1) End user computing is an increasing phenomenon where end users such as managers and knowledge workers develop their own applications to meet information needs, as IT departments are often unresponsive.
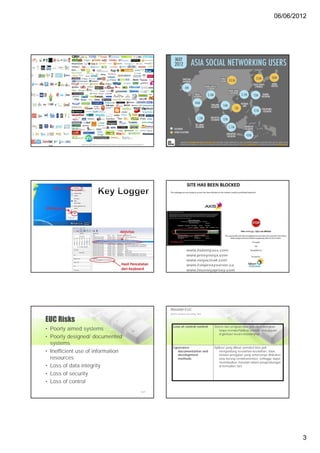
2) This gives rise to both benefits like more responsive systems and risks like redundant resources, poor system design, and security issues.
3) The CIO role is important to manage information resources, build partnerships, improve processes, and provide reliable services while communicating in business terms.