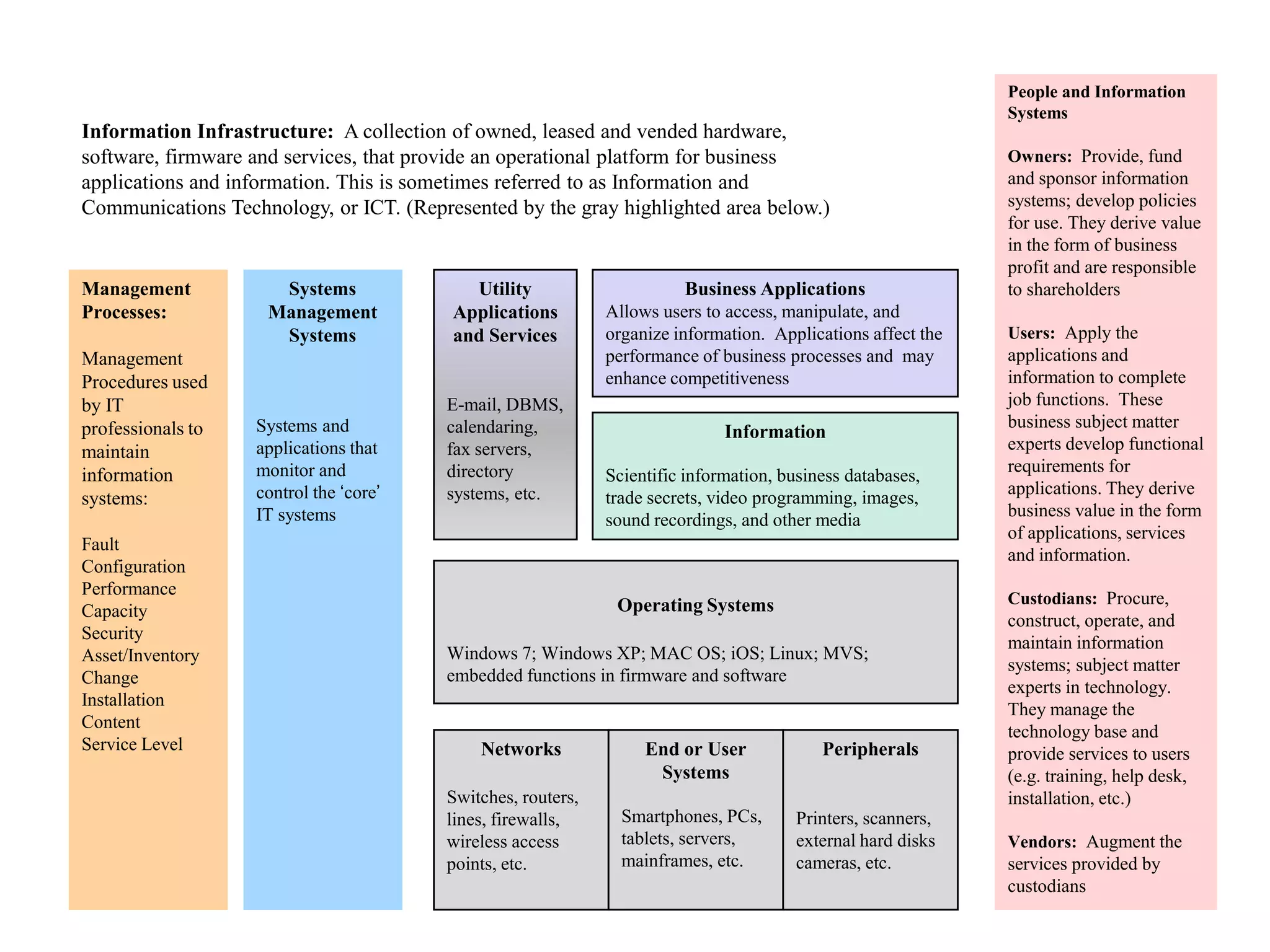
People and systems work together to manage information infrastructure. Owners provide funding and set policies while users access applications to complete work. Custodians maintain systems and manage technology while vendors supplement their services. Together these roles ensure information infrastructure supports business operations.