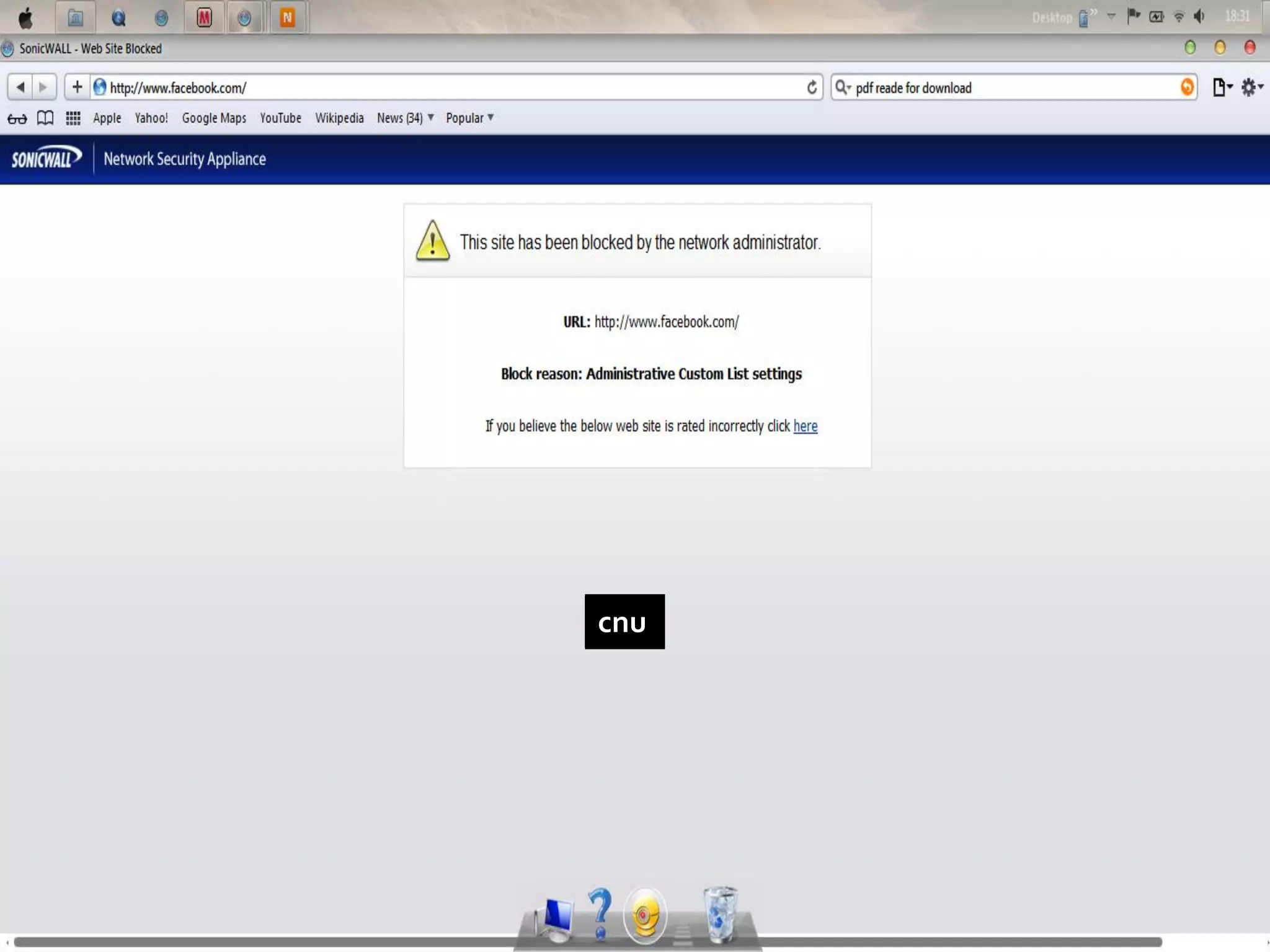
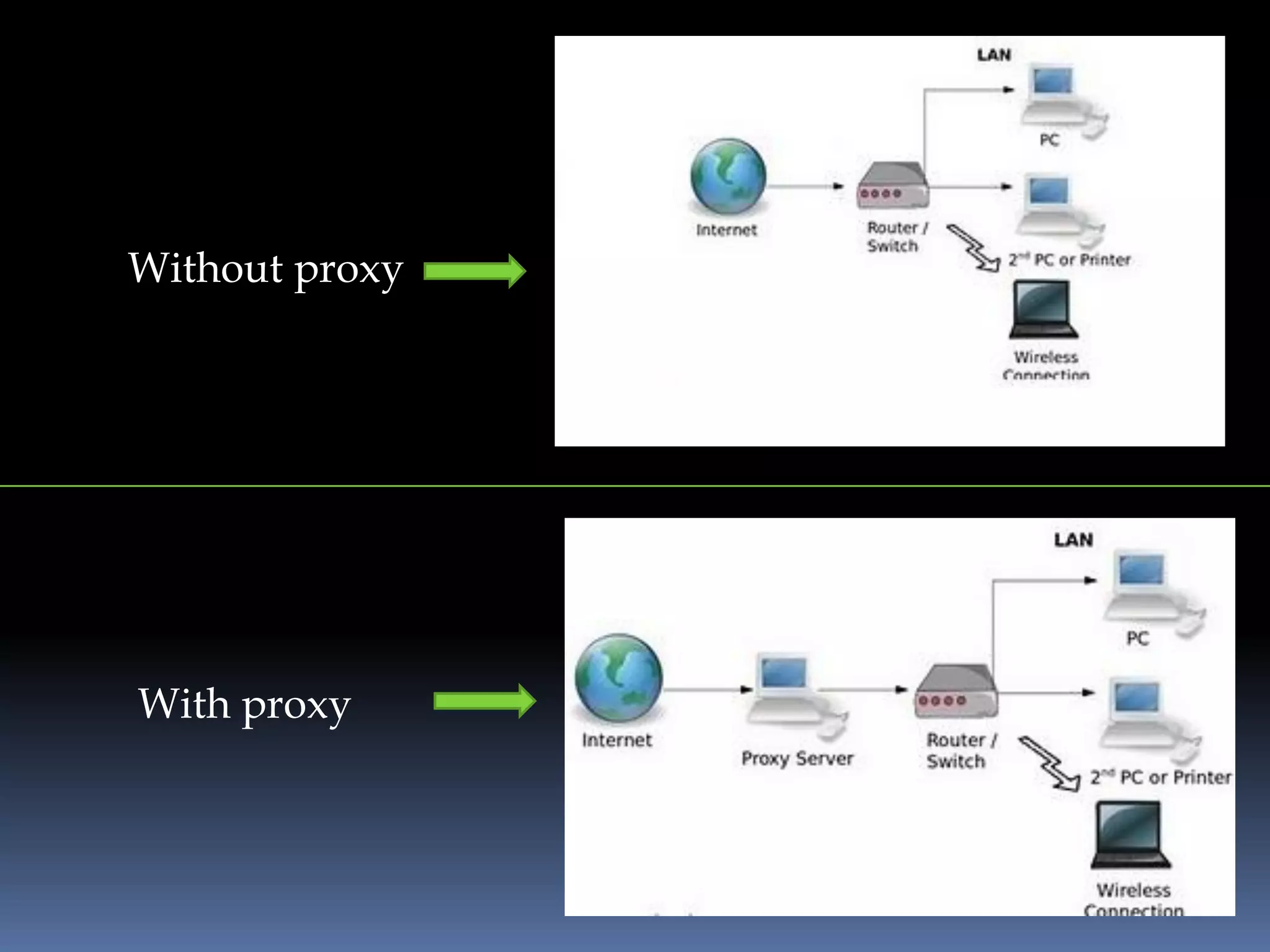
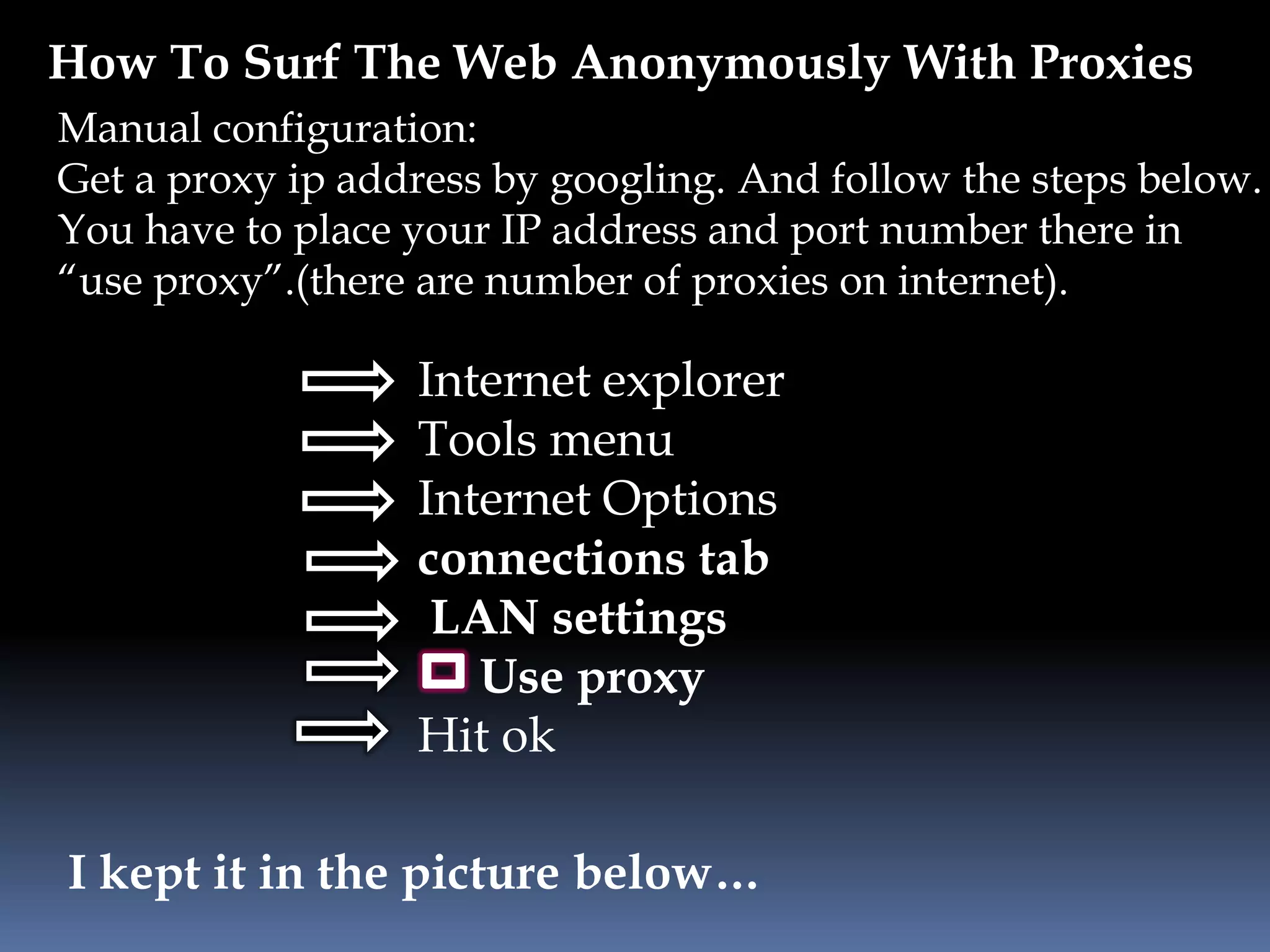
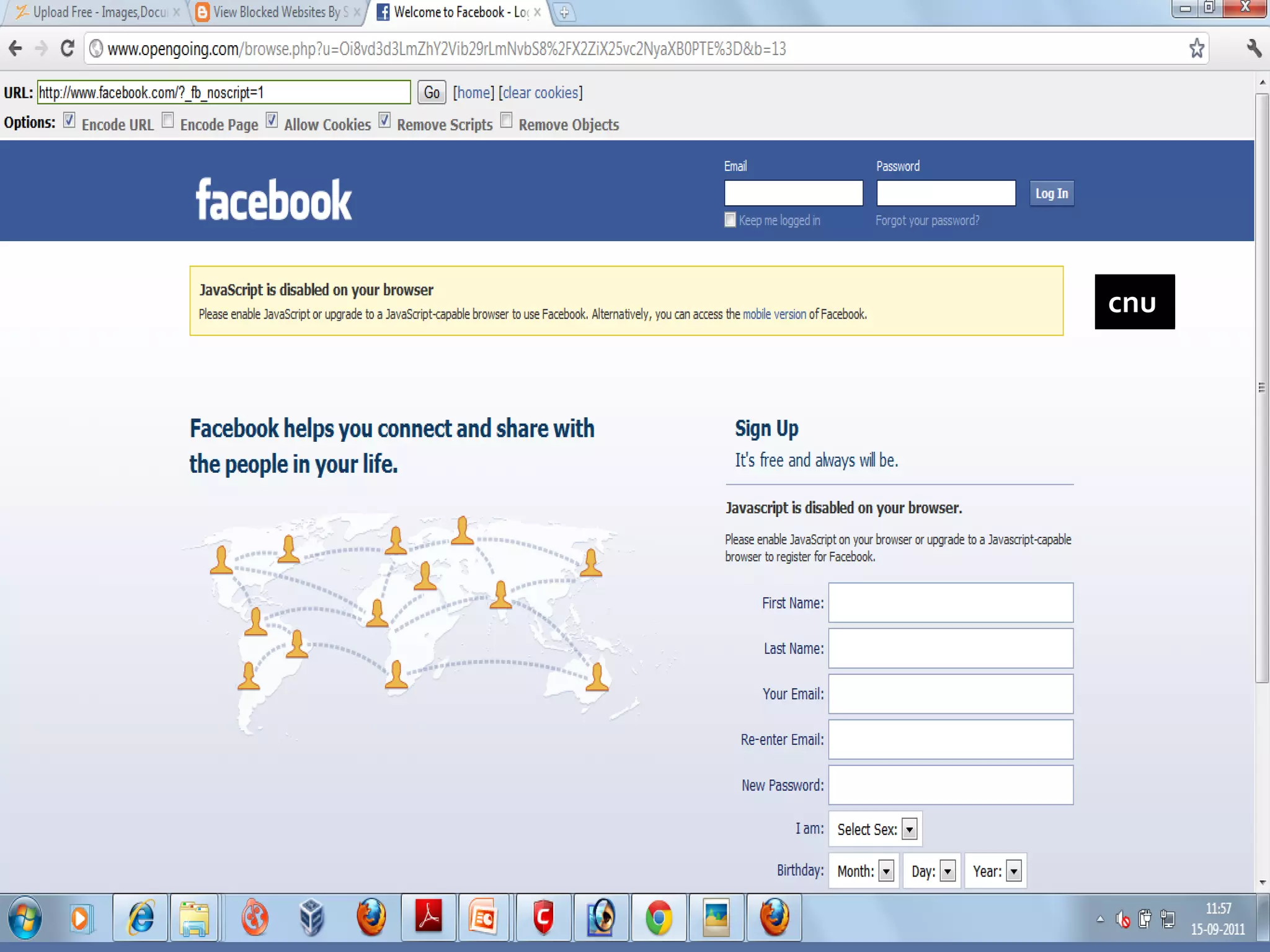
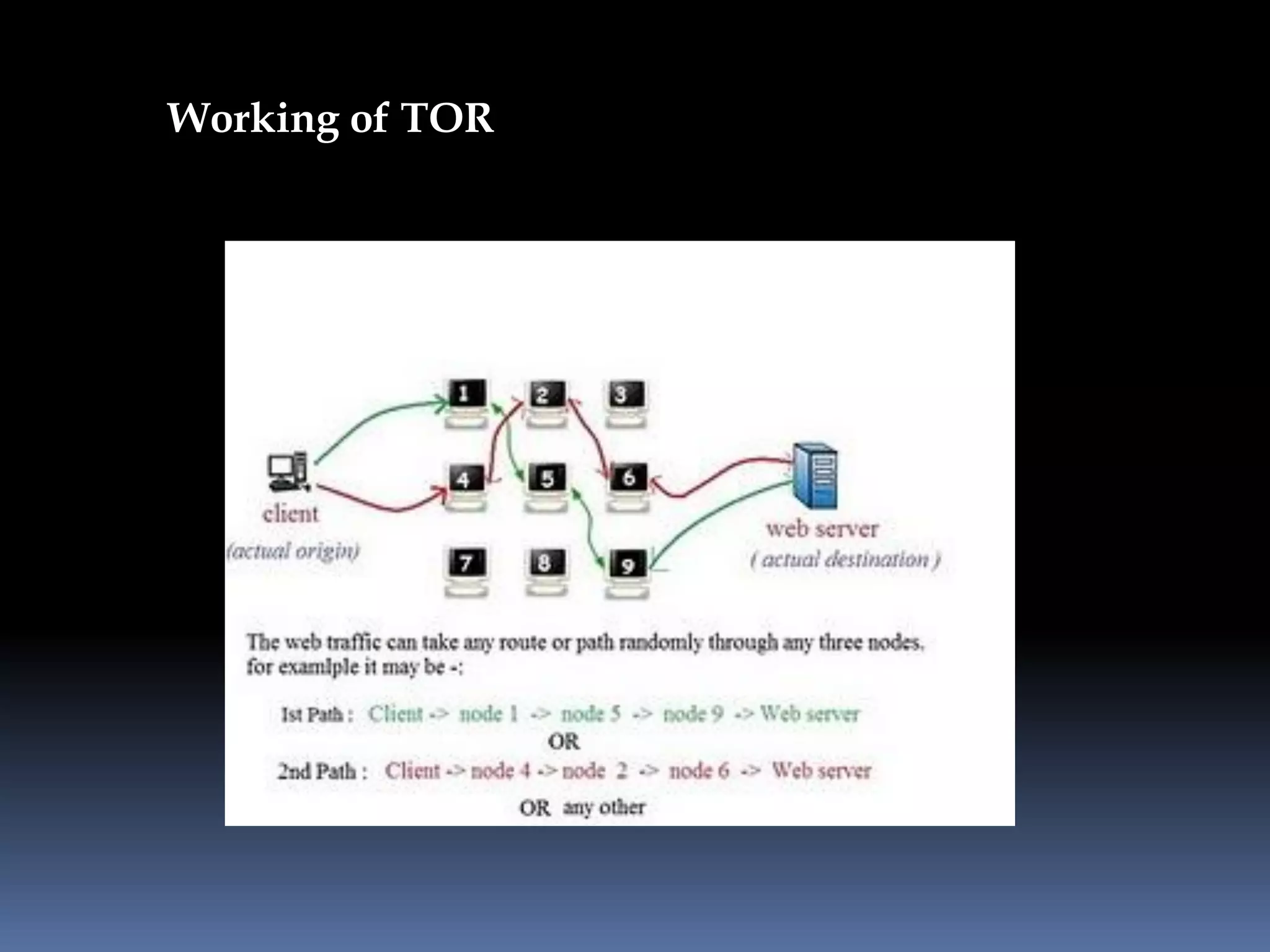
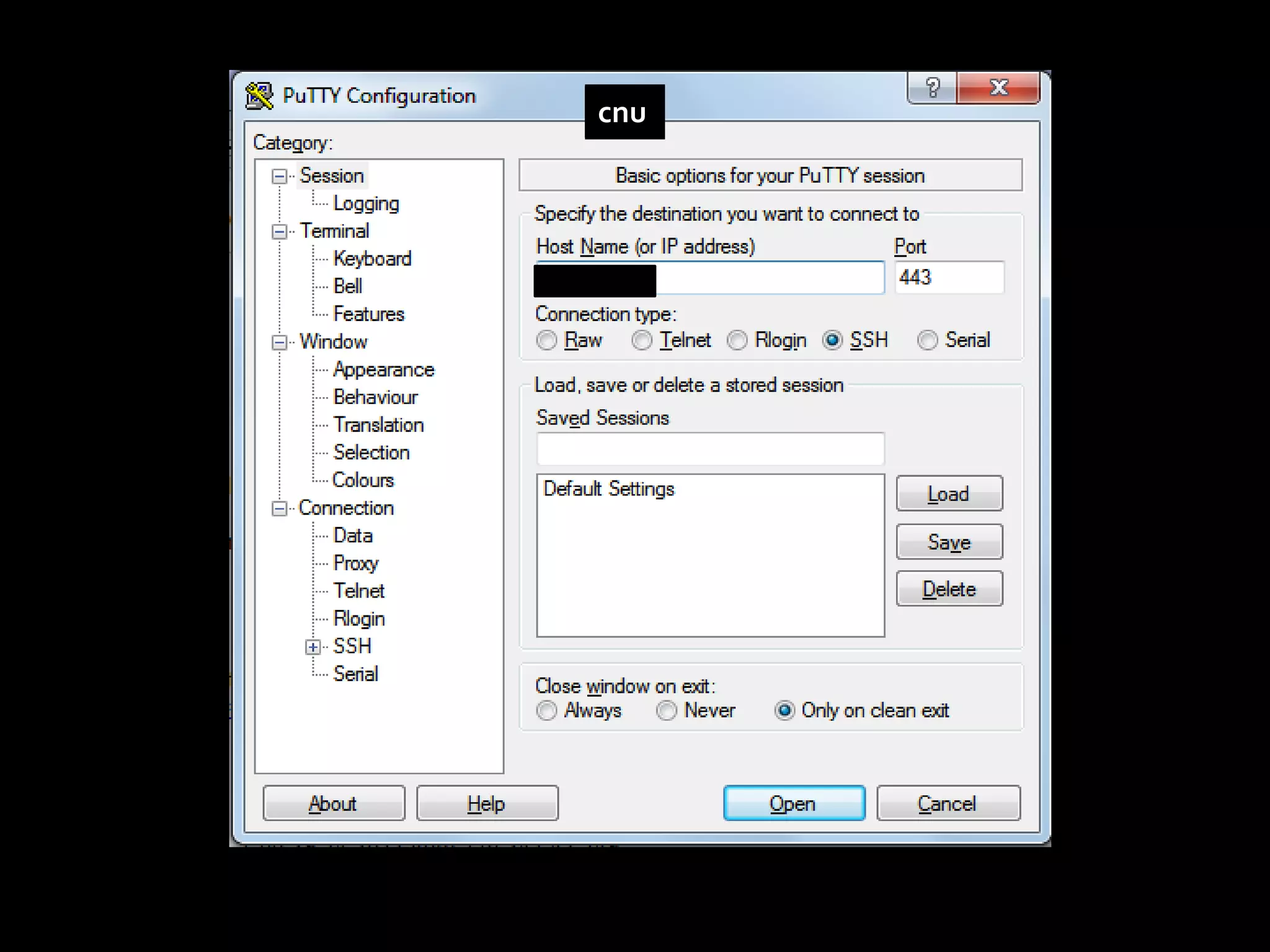
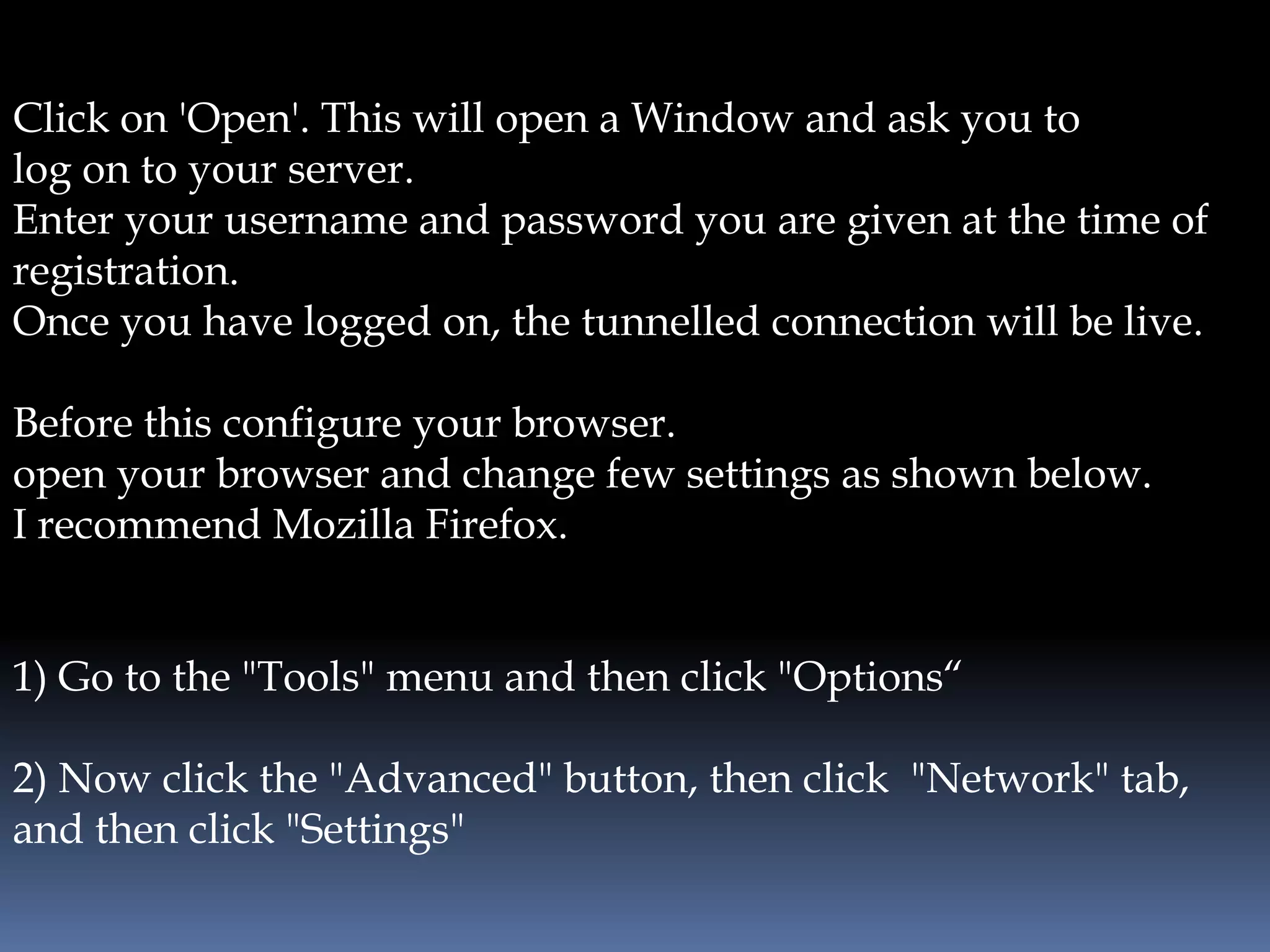
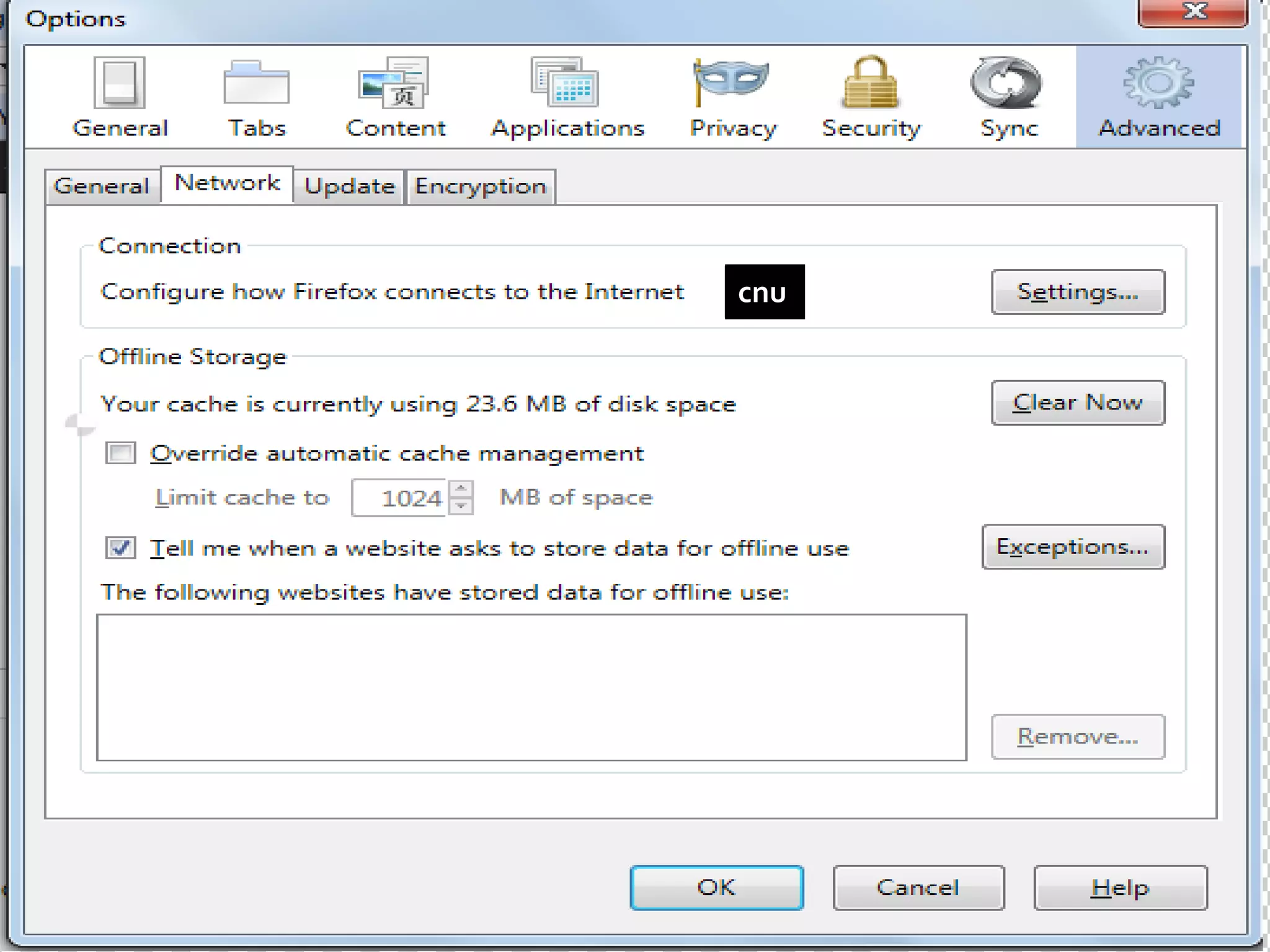
This document provides instructions for accessing blocked websites like Facebook in college networks by using different methods to bypass firewalls and proxies. It explains how to use secure connections, proxy servers, the Tor network and VPNs to anonymously access blocked sites. It also describes setting up an SSH tunnel using PuTTY to create an encrypted tunnel for forwarding requests and browsing privately. Screenshots demonstrate successfully opening Facebook after configuring these techniques on the author's college network.