Embed presentation
Download to read offline

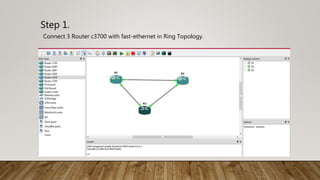
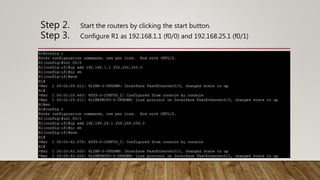
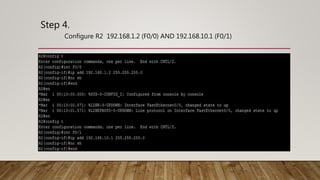
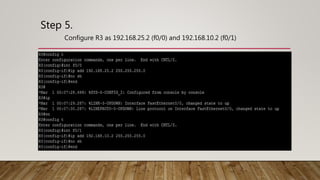
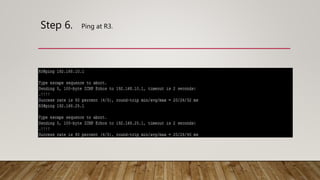
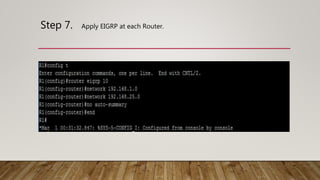
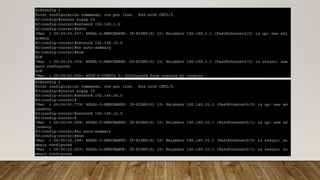

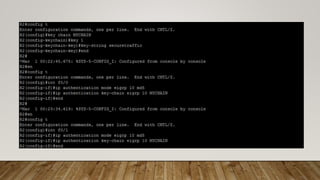
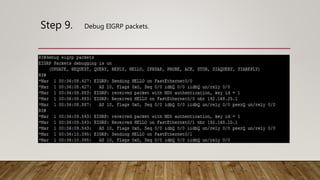


The document outlines the steps to implement EIGRP with MD5 authentication using GNS3, including configuring three routers in a ring topology. It details IP address assignments, commands to apply EIGRP and MD5, and concludes with successful implementation. Debugging EIGRP packets is also suggested as part of the process.












