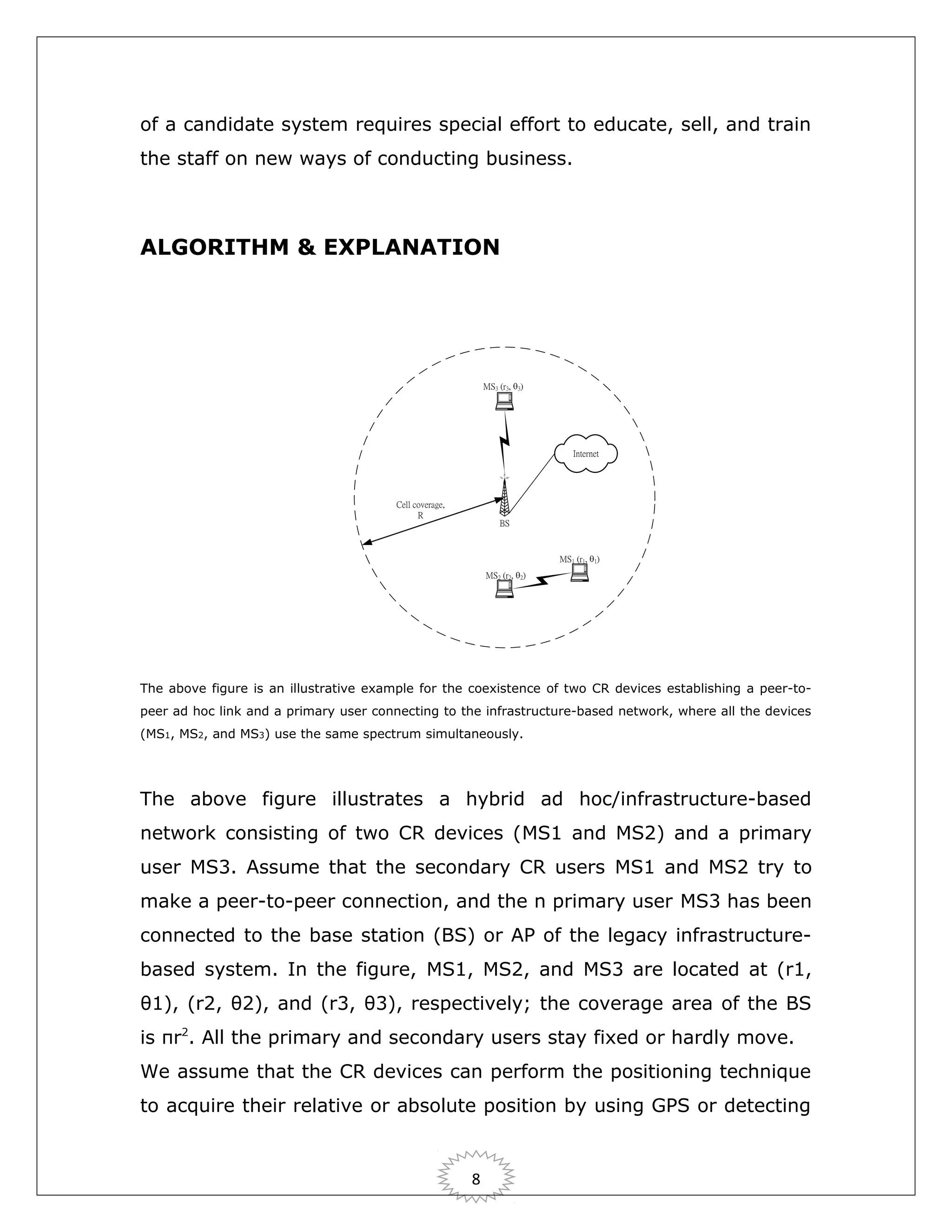
This document proposes a system that allows cognitive radio (CR) devices to establish peer-to-peer ad hoc networks that overlay existing infrastructure-based wireless networks. By utilizing location awareness, CR devices can identify regions where concurrent transmissions on the same frequency band are possible between the ad hoc and infrastructure-based networks. An analytical model is developed based on CSMA/CA to compute the probability of concurrent transmissions. The results show the frequency band of the legacy system can be reused up to 45% by the overlaying cognitive ad hoc network when CR users have location information.