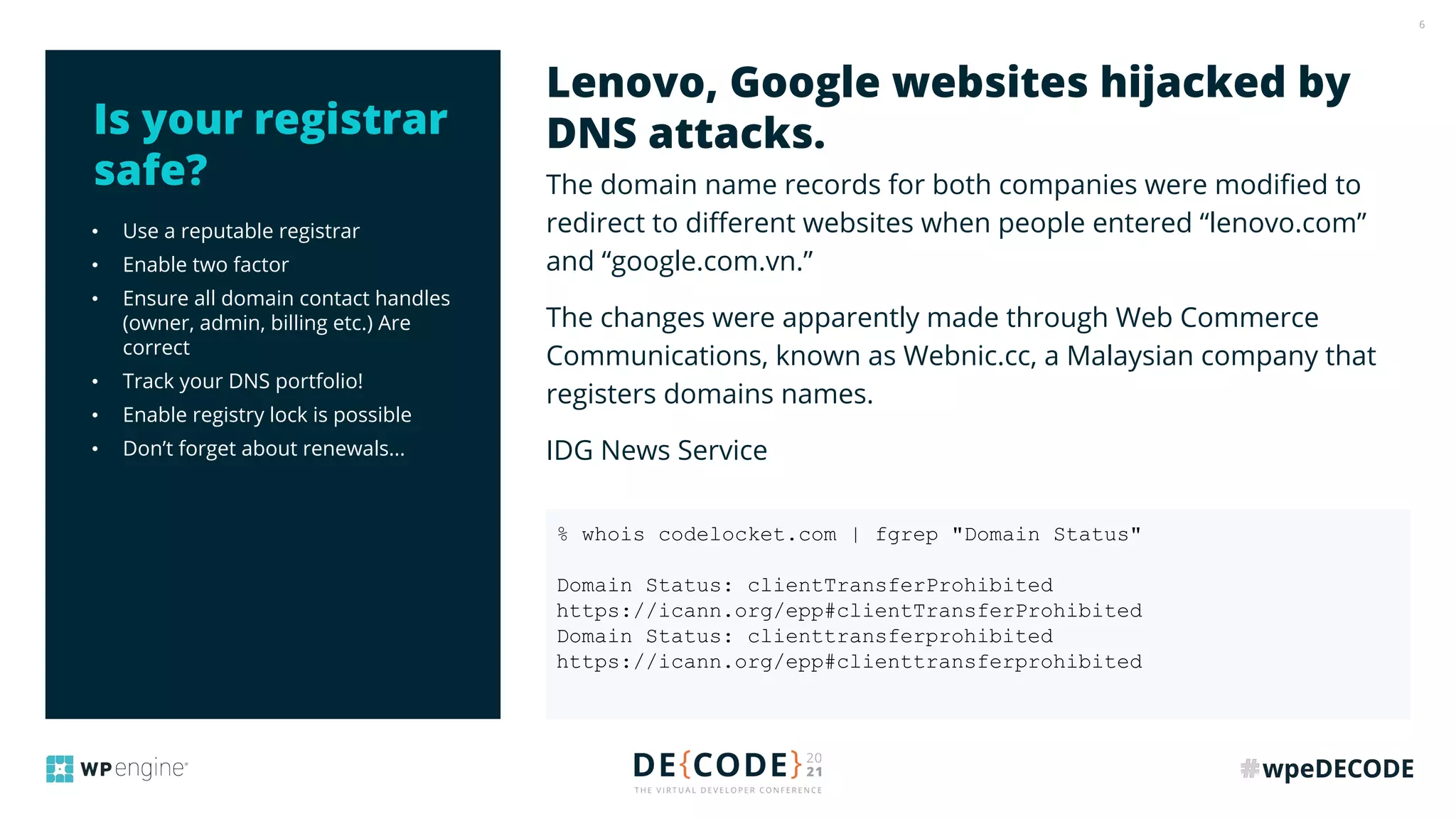
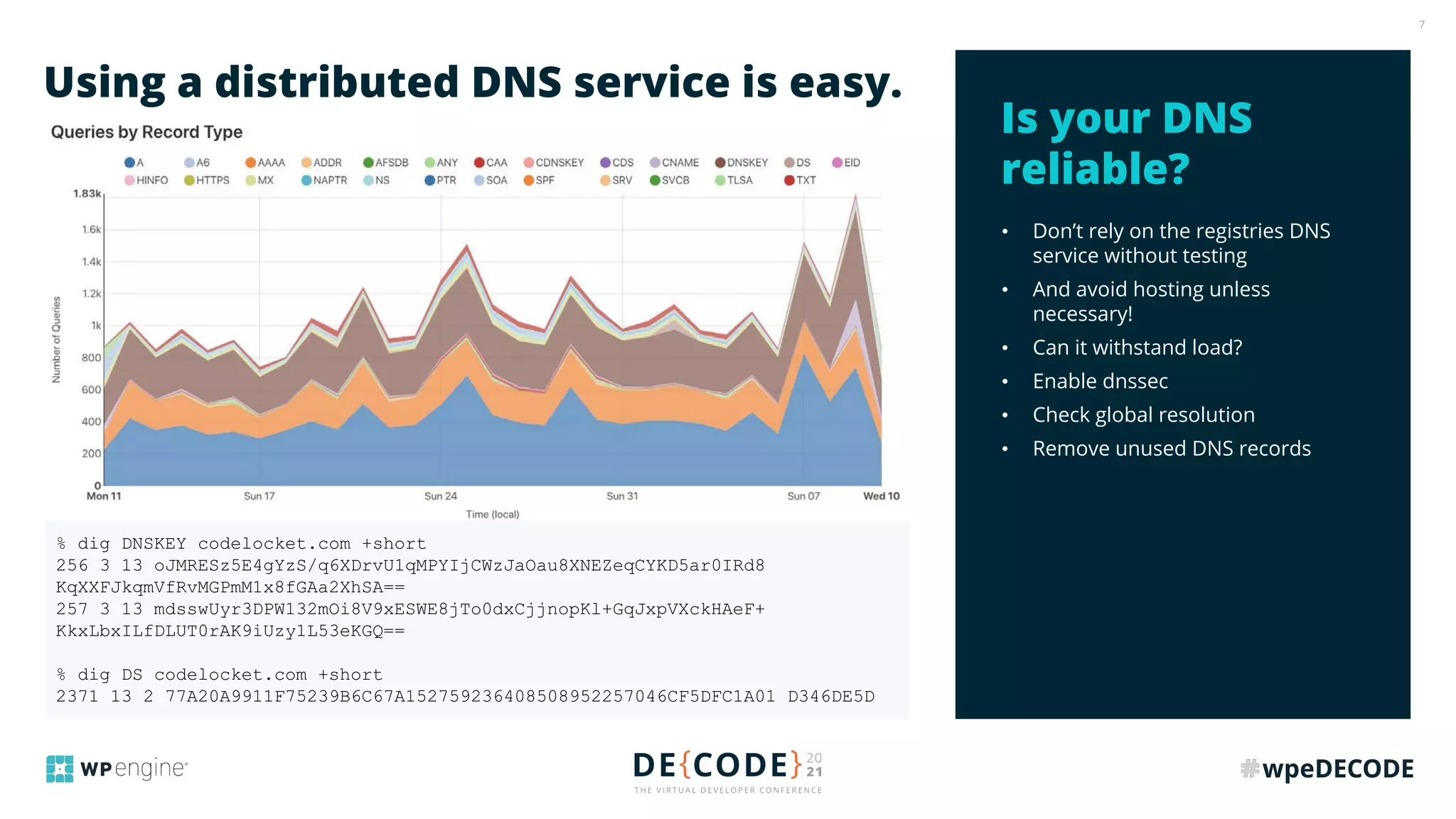
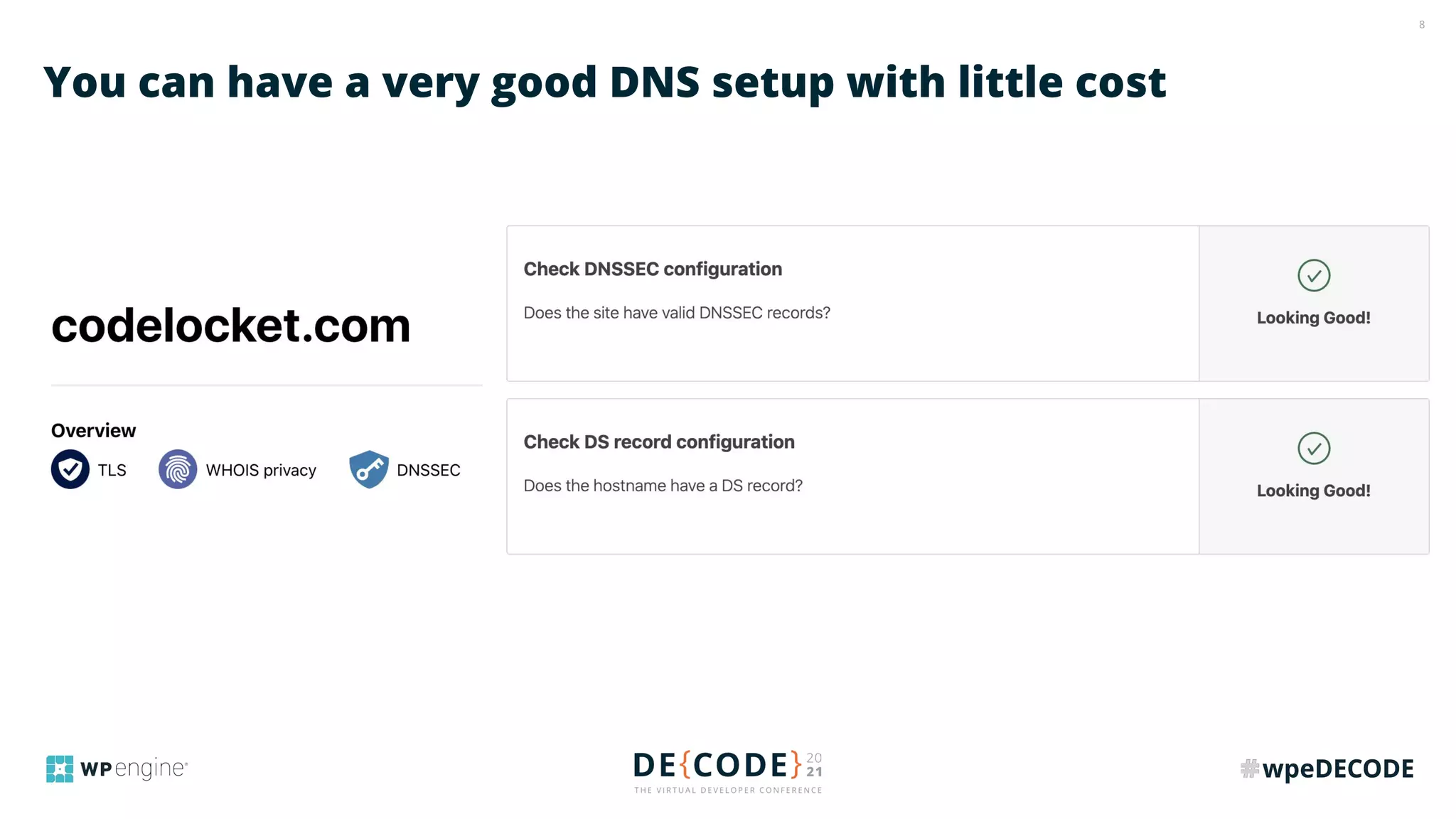
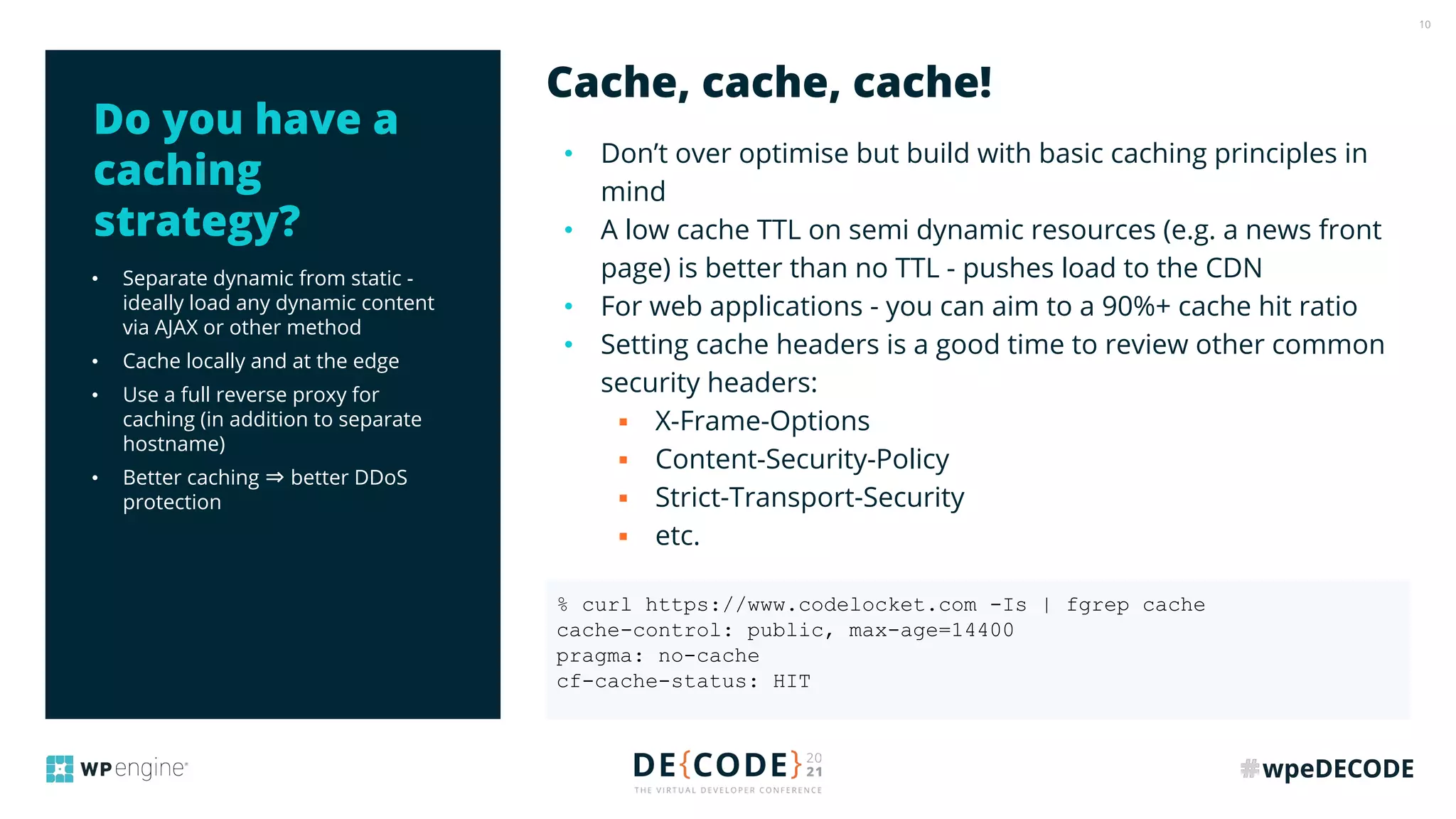
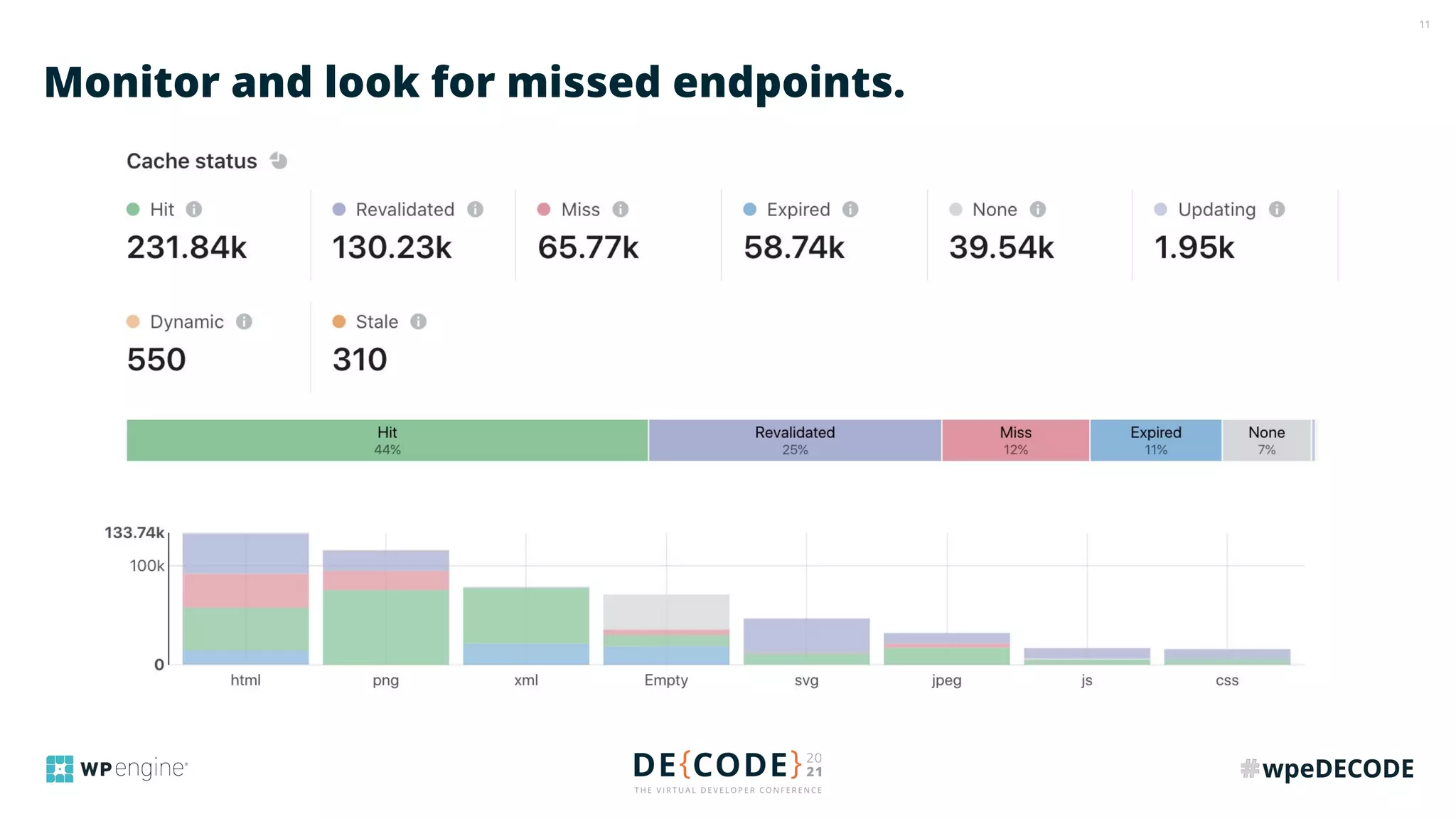
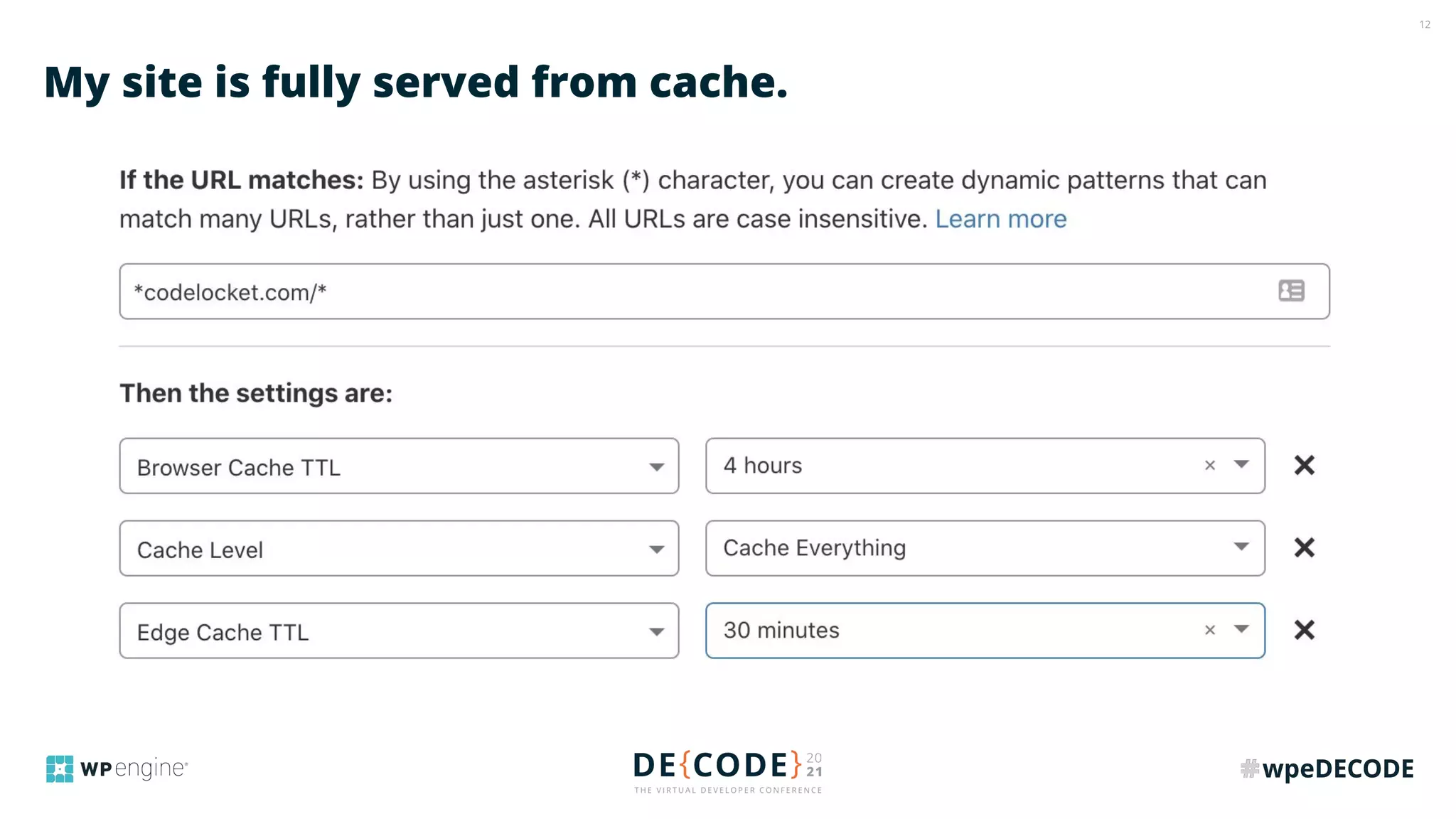
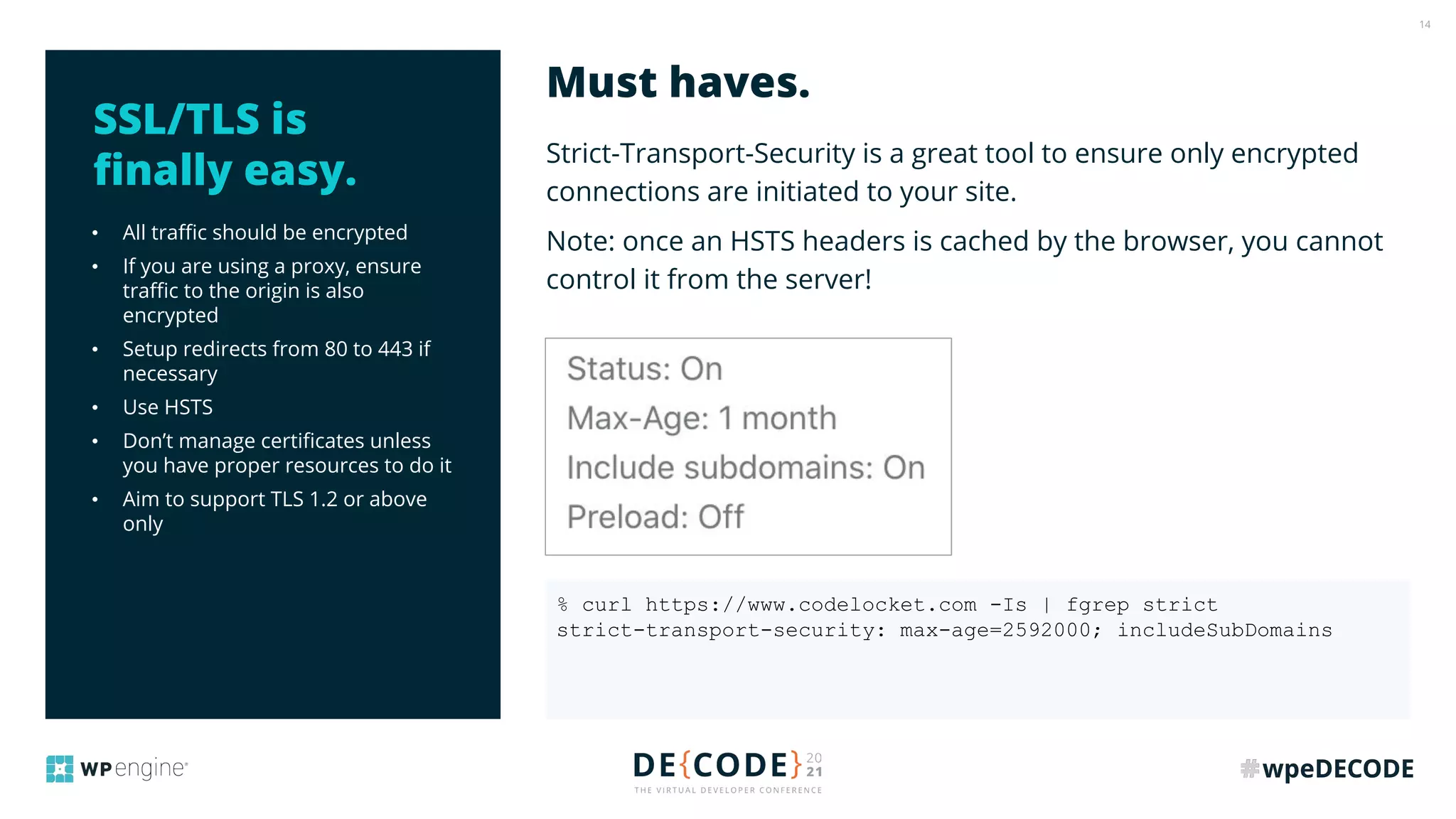
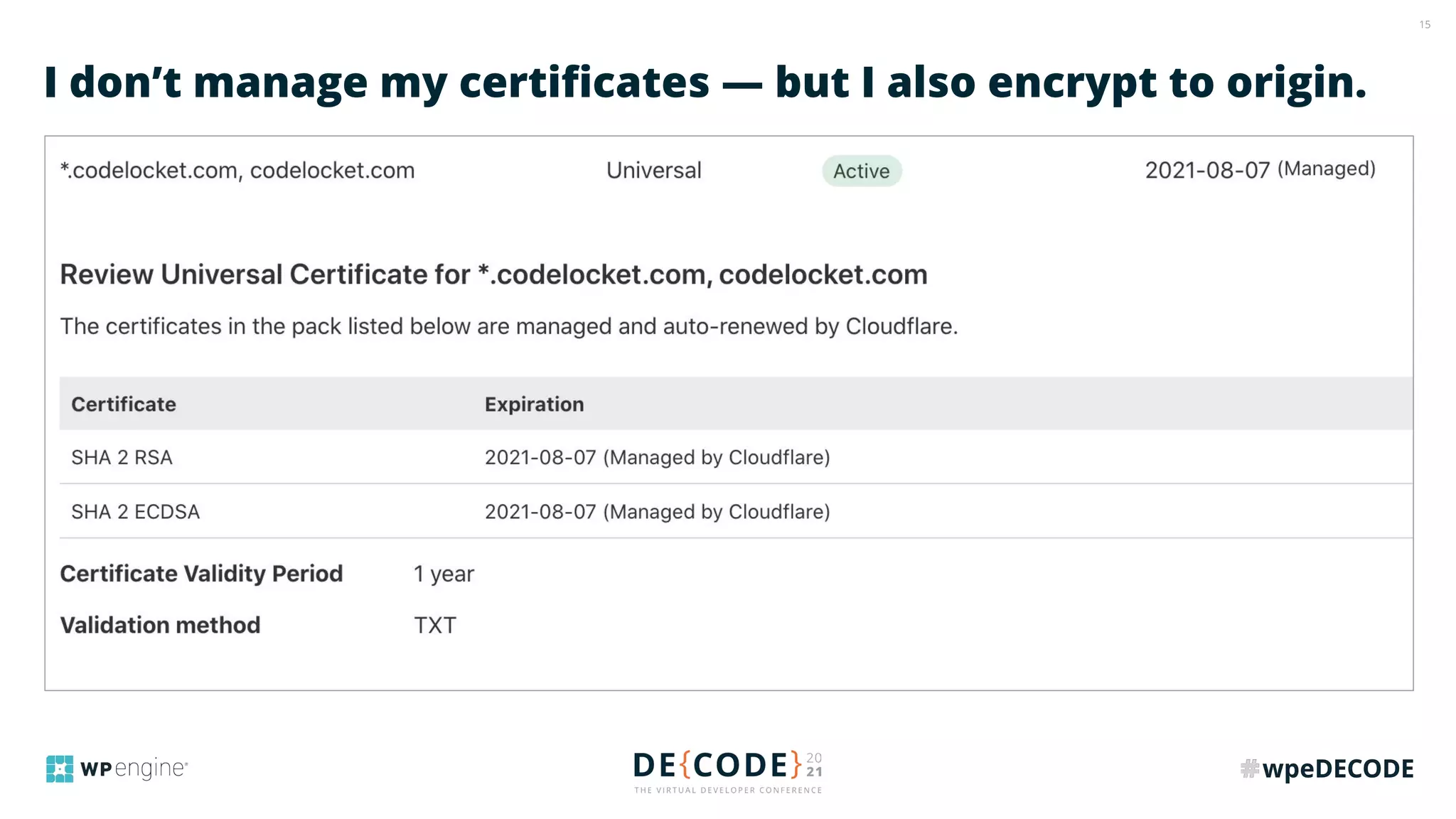
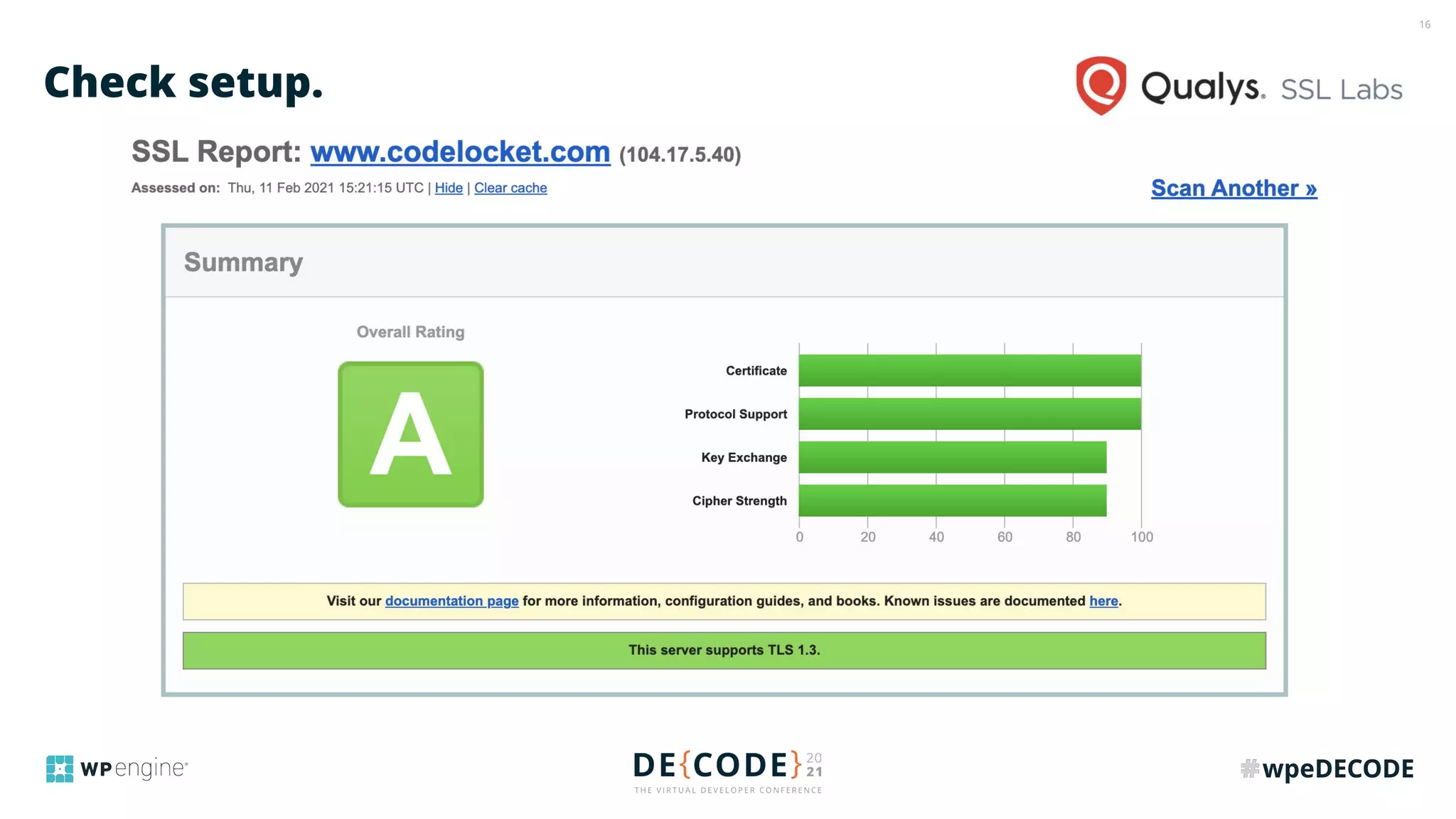
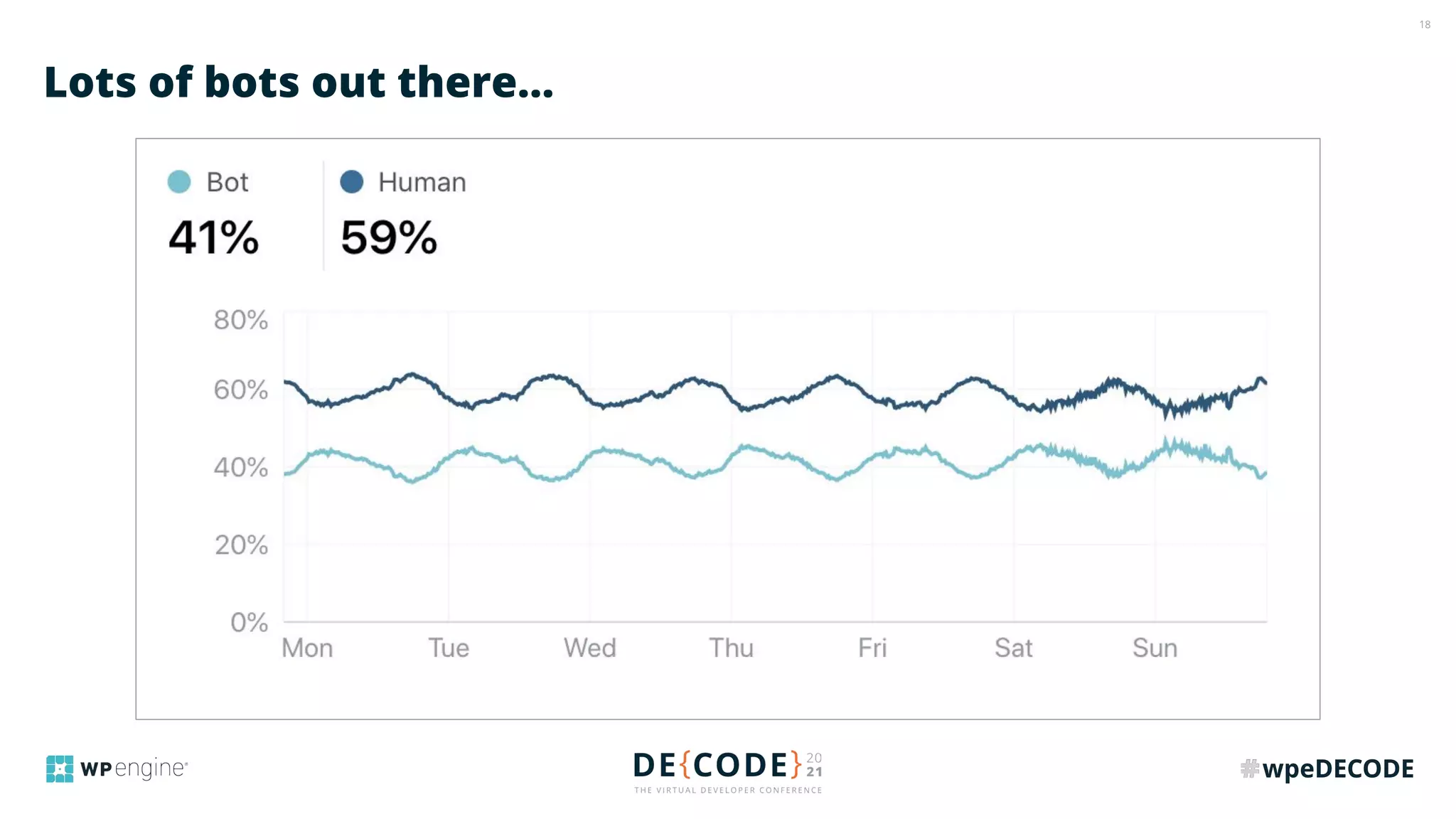
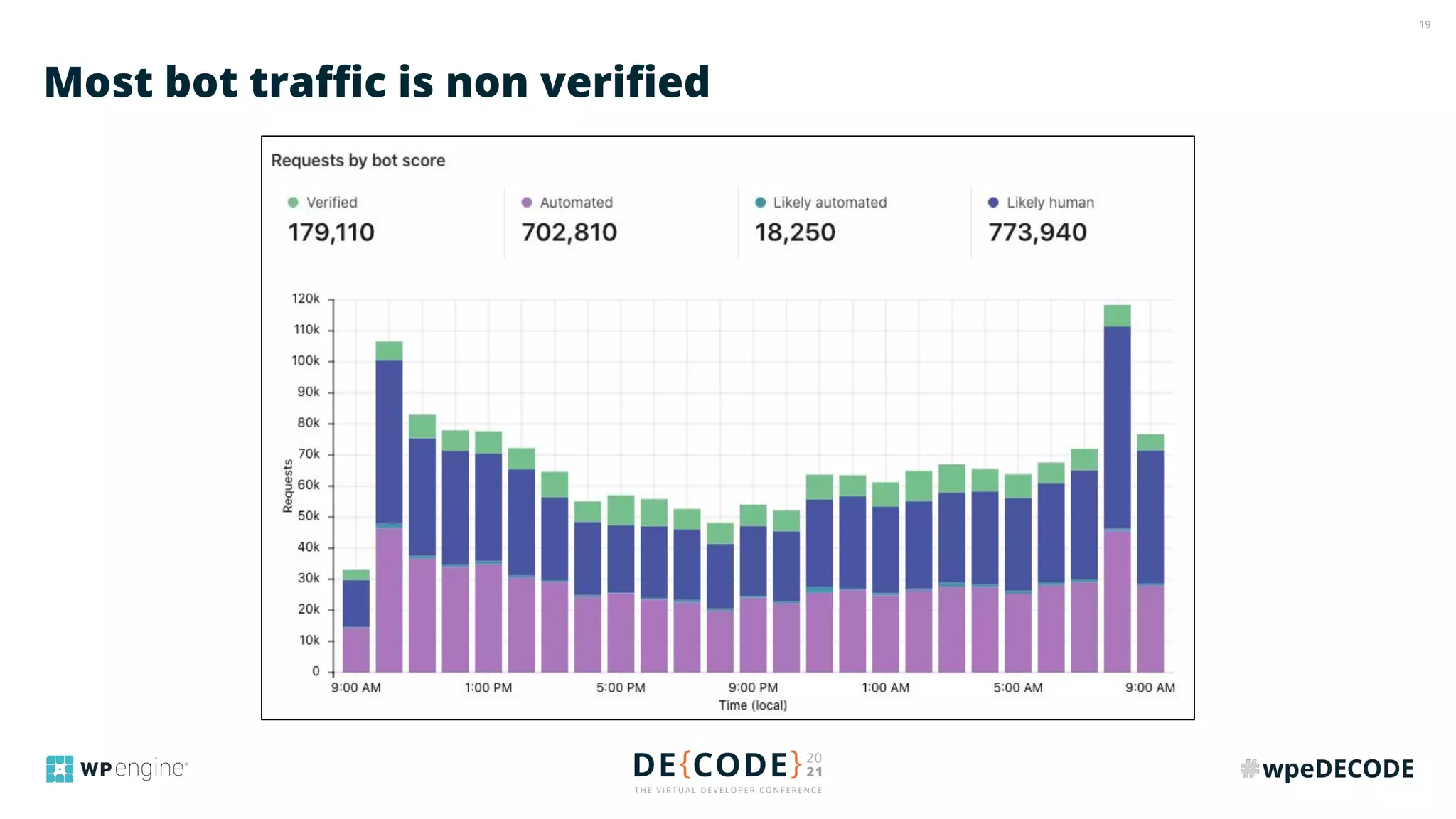
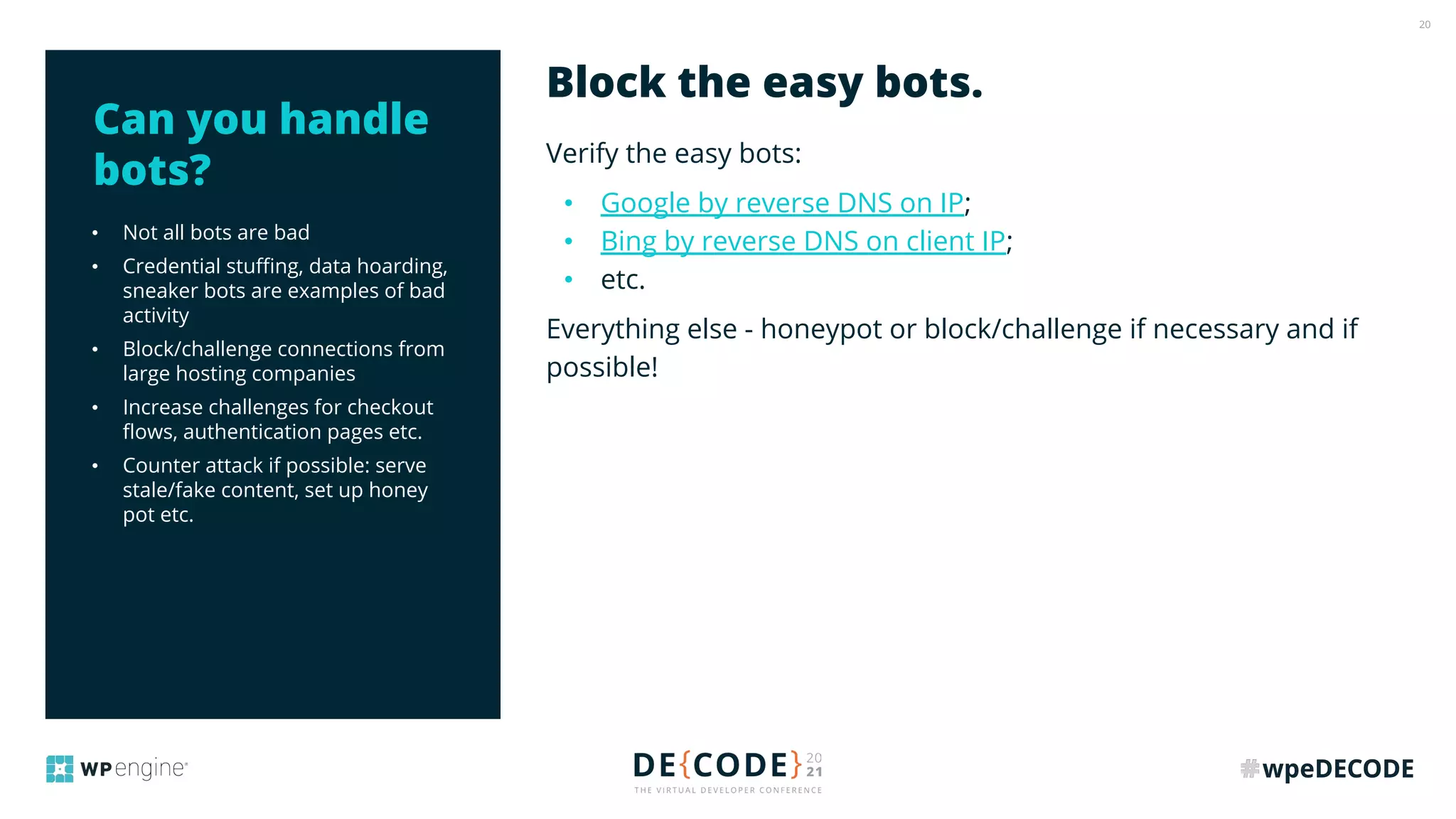
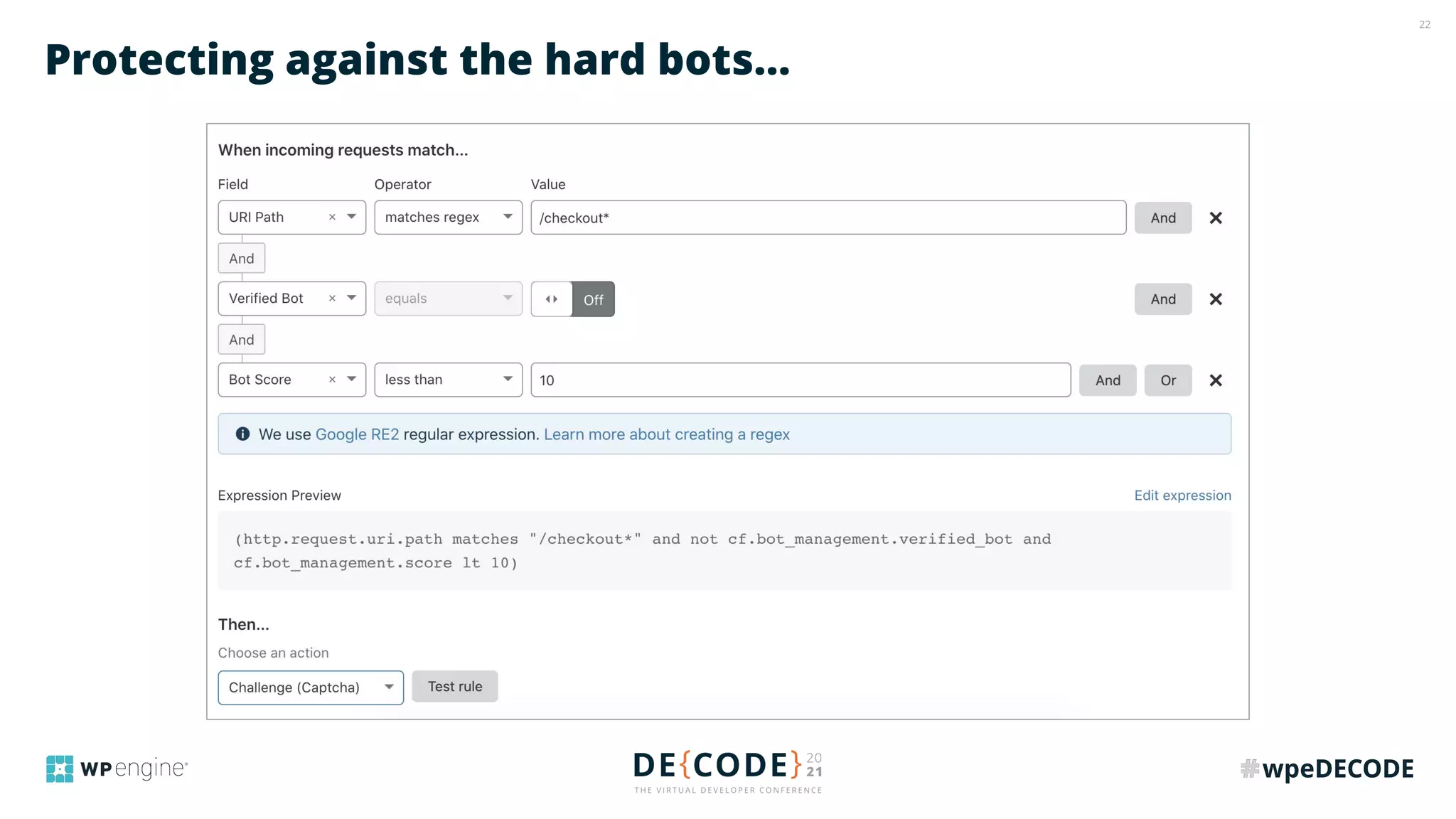
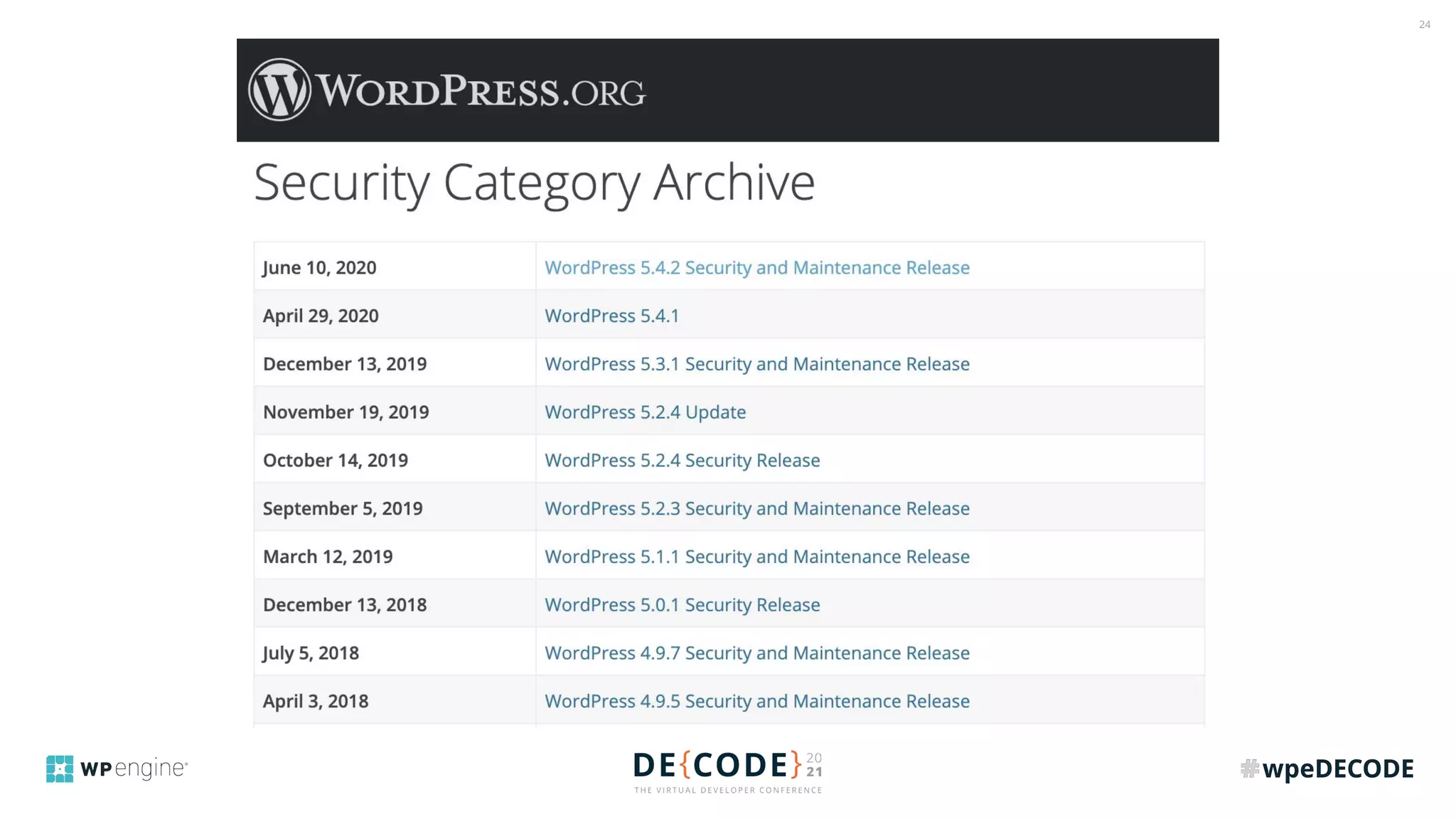
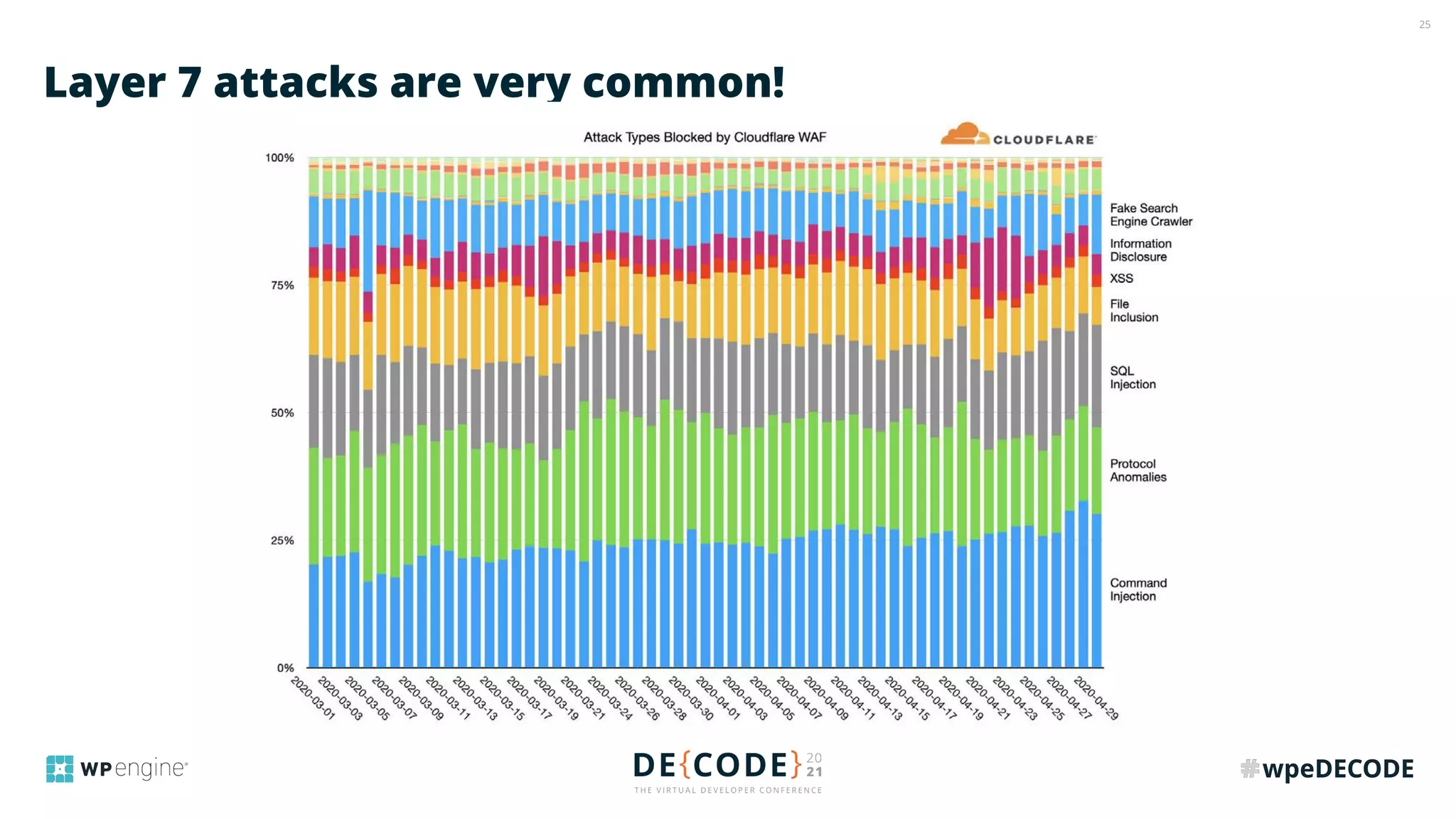
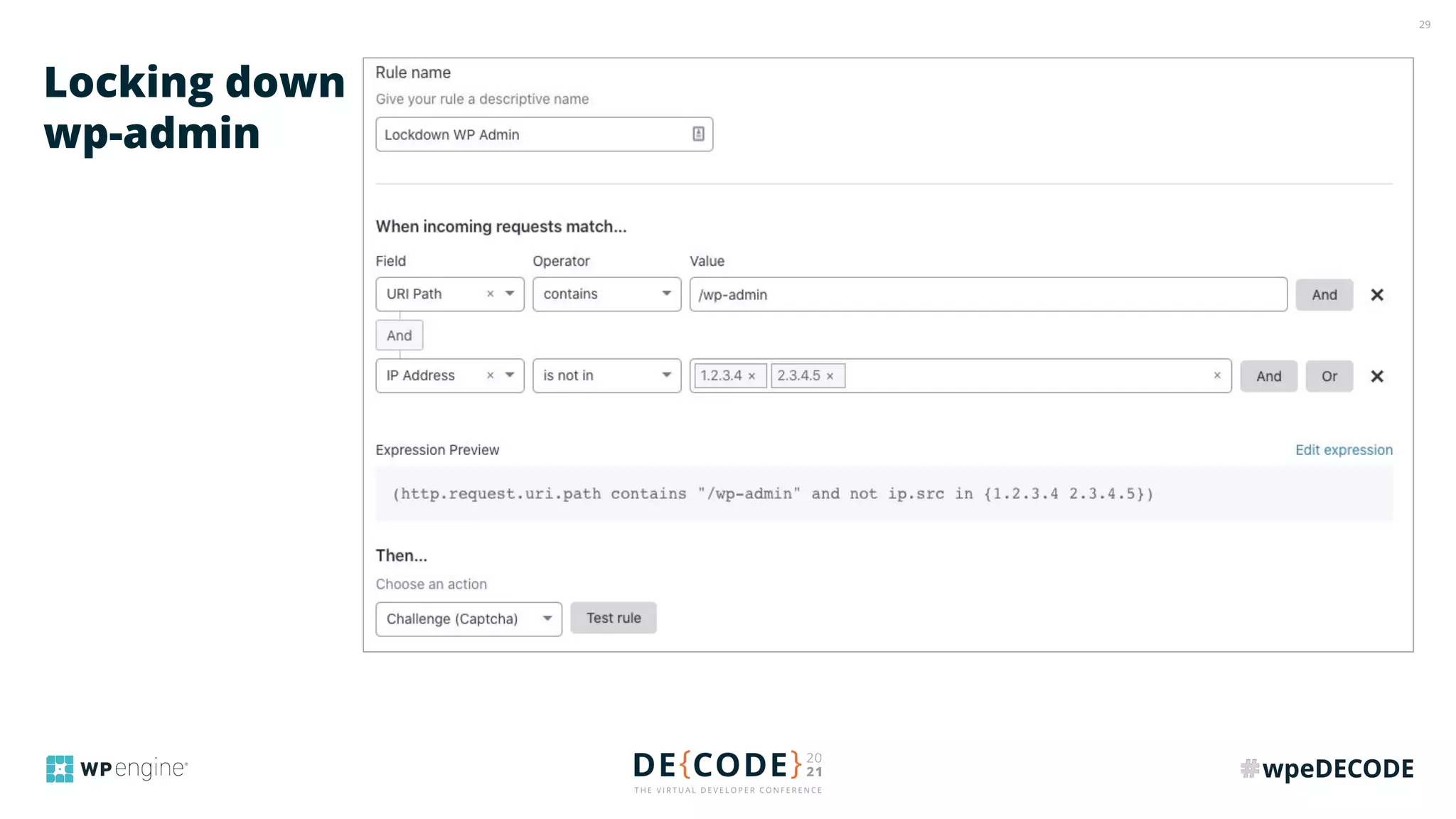
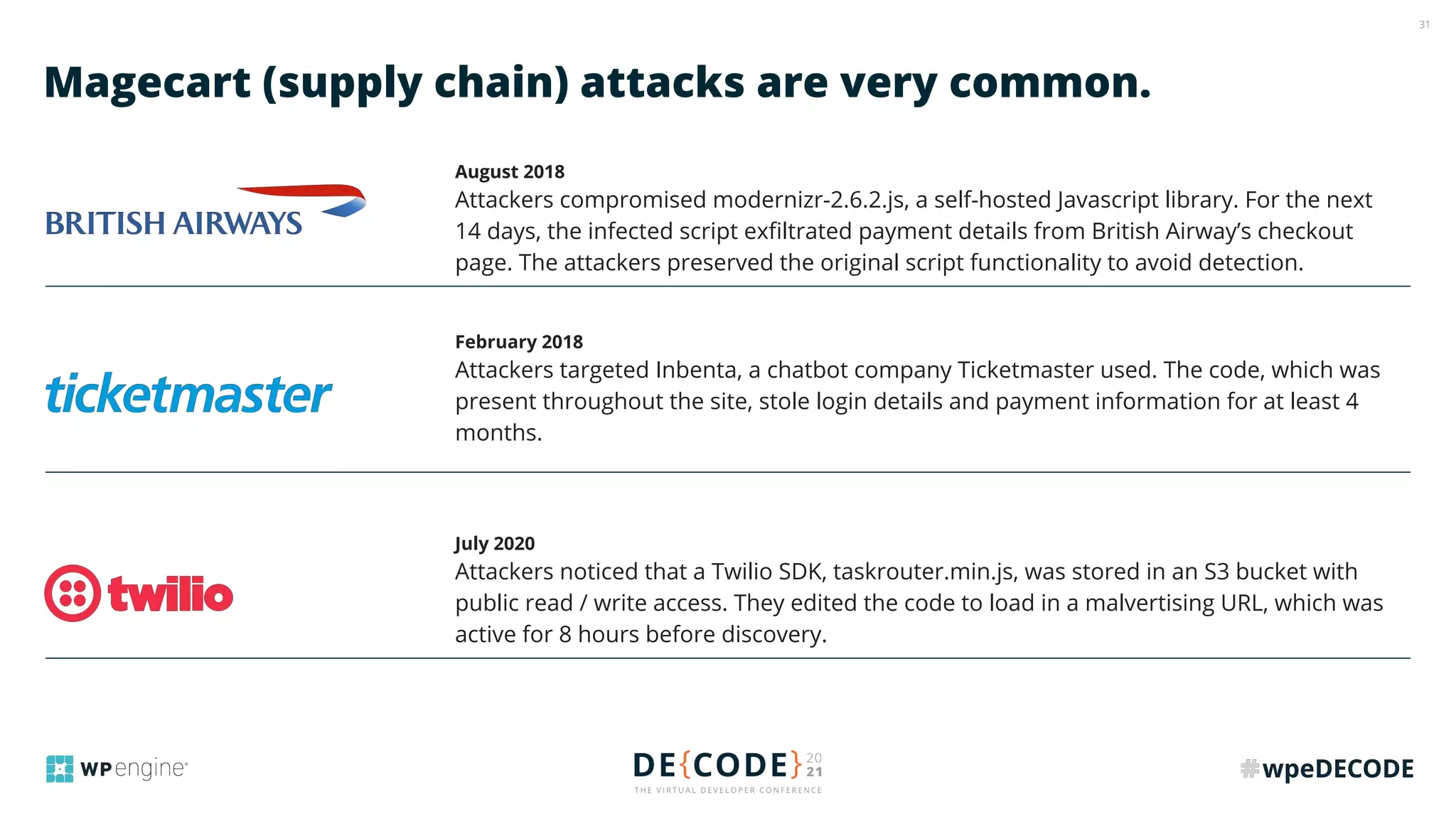
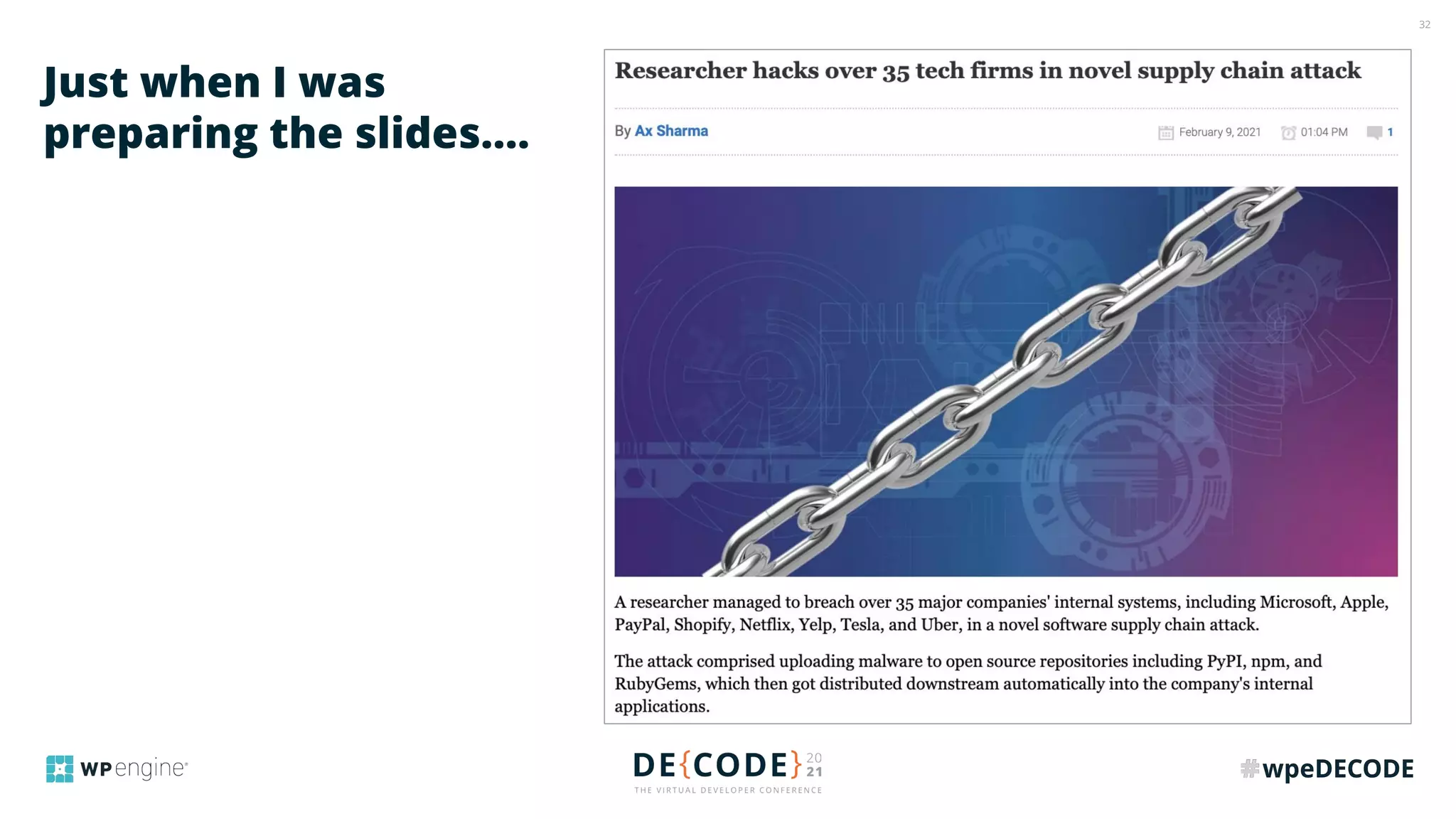
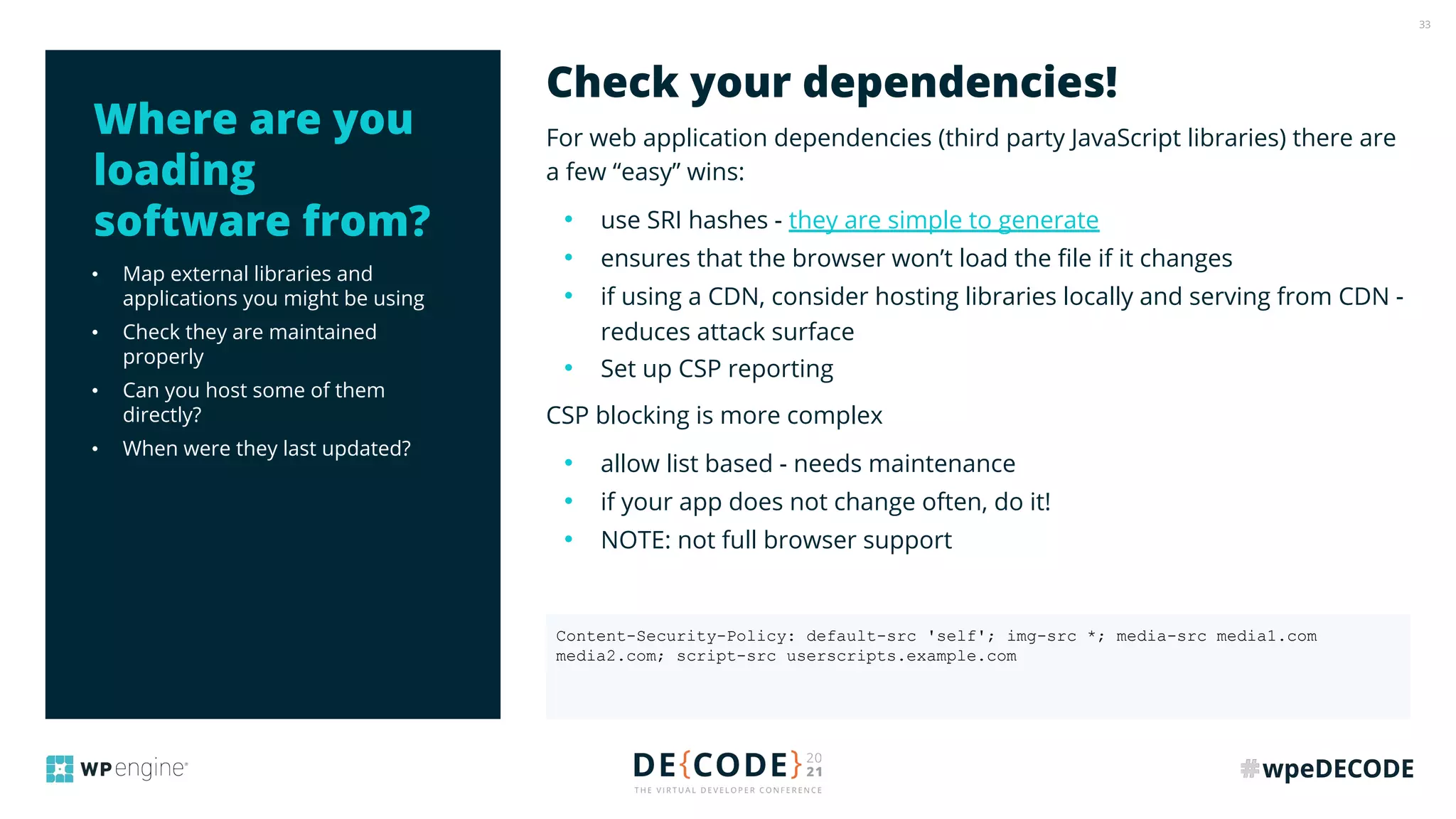
The document outlines key practices for securing websites, focusing on DNS security, reducing application load, encrypting traffic, detecting automated traffic, and managing vulnerabilities. It emphasizes the importance of using reputable services, enabling two-factor authentication, and regularly updating software while also addressing the significance of proper traffic encryption and bot management. The document also provides actionable strategies such as caching, setting security headers, and monitoring external libraries to mitigate risks effectively.