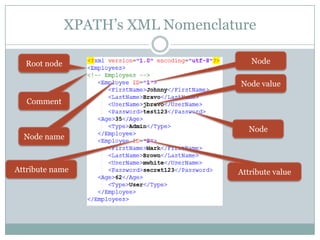
This document provides information about a 2-day training course on exploiting injection flaws. It discusses the agenda which includes hands-on exercises covering SQL injection, LDAP injection, ORM injection, XPath injection and combining XXE and XPath. The trainer, Sumit Siddharth, is an expert in application and database security with over 8 years experience who has spoken at several security conferences. The course aims to help attendees think outside the box to find issues that tools may miss through practical CTF exercises.



![Encoding/Decoding User Input
Base64 decoding user input
Hex decoding user input
Real world examples
WordPress Admin-Ajax.php unauthenticated SQL injection
PHP-Nuke auth.php
$cookie=explode(„;‟, urldecode(empty($_POST[„cookie‟])))
$admin=base64_decode($admin)](https://image.slidesharecdn.com/injectionflawteaser-130624030024-phpapp01/85/Injection-flaw-teaser-8-320.jpg)