The document discusses the implementation of decimation in time-radix-2 FFT algorithms for signal processing in the encrypted domain. It covers the history and development of FFT algorithms, their computational efficiency, and how they can be applied to encrypted signals to maintain security and performance. Additionally, it highlights the benefits and challenges of performing operations on encrypted data using homomorphic encryption techniques.





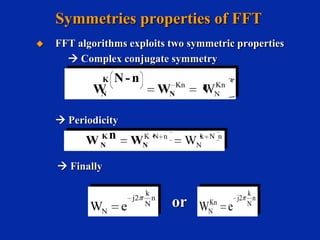



![2 point Butterfly
Example if N=8 the even number[0,2,4,8]
odd number[0.3.5.7]
X(0)
X(1)
x(0)
x(2)
TFD N/2
•N/2(N/2-1) complex ‘+’ for each
N/2 DFT.
•(N/2)2 complex ‘ ’ for each
DFT.
x(N-2)
X(N/2-1)
W0
W1
x(1)
x(3)
We need:
-
X(N/2)
X(N/2+1)
•N/2 complex ‘ ’ at the input of
the butterflies.
•N complex ‘+’ for the butterflies.
•Grand total:
N2/2 complex ‘+’
TFD N/2
N/2(N/2+1) complex ‘ ’
WN/2-1
x(N-1)
N
2
2
-
X(N-1)
.2.......... .......... ......
N](https://image.slidesharecdn.com/dit-radix-2-fftinsped-131211130402-phpapp01/85/DIT-Radix-2-FFT-in-SPED-10-320.jpg)









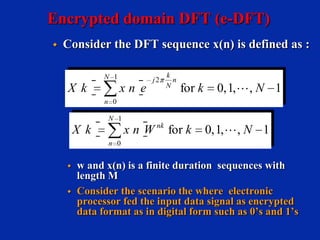
![Encrypted domain DFT (e-DFT)
Encrypted input data signal in the form
of digital 0’s and 1’s in the form of
equation
E(X)=(E[x(0)],E[x(1)],…..E[x(N-1)]
in order to make possible linear
computation for encrypted input signal
use homographic technique of Additive
that is represented by
E(x + y) = E(x)
. E(y)](https://image.slidesharecdn.com/dit-radix-2-fftinsped-131211130402-phpapp01/85/DIT-Radix-2-FFT-in-SPED-24-320.jpg)

