Embed presentation
Download as PDF, PPTX



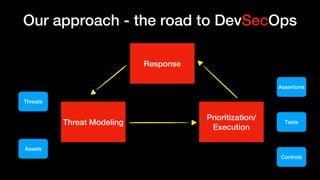
![Threat Modeling
• STRIDE? DREAD?
• MITRE ATT&CK Framework [1]
• CAPEC [2]
https://attack.mitre.org/wiki/Main_Page
https://capec.mitre.org/
What are you
protecting?
What’s the value
of it?
Who/what are you
protecting it from?
Threats
Assets
Controls
Assertions
Tests](https://image.slidesharecdn.com/devsecops-cmpr-181001131629/85/Devsecops-at-Cimpress-5-320.jpg)





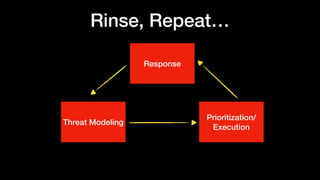

This document discusses DevSecOps at Cimpress, an online printing company. It outlines some of the challenges of their worldwide and decentralized operations with varying technology stacks. Their approach involves threat modeling to identify threats, assets, and controls. They create security assertions based on the threat model and assure test case coverage. The focus is on integrating security into development in a way that is not burdensome to developers. The expected deliverables include automated unit test coverage and tool scans to address the threat model.




![Threat Modeling
• STRIDE? DREAD?
• MITRE ATT&CK Framework [1]
• CAPEC [2]
https://attack.mitre.org/wiki/Main_Page
https://capec.mitre.org/
What are you
protecting?
What’s the value
of it?
Who/what are you
protecting it from?
Threats
Assets
Controls
Assertions
Tests](https://image.slidesharecdn.com/devsecops-cmpr-181001131629/85/Devsecops-at-Cimpress-5-320.jpg)






