1. Jason Chan, an engineering director at Netflix, gave a presentation about product security approaches at Netflix.
2. Netflix has an agile development culture with over 200 daily production pushes across 1000+ supported devices in 40 countries. This results in a need for security approaches that can handle Netflix's scale and speed.
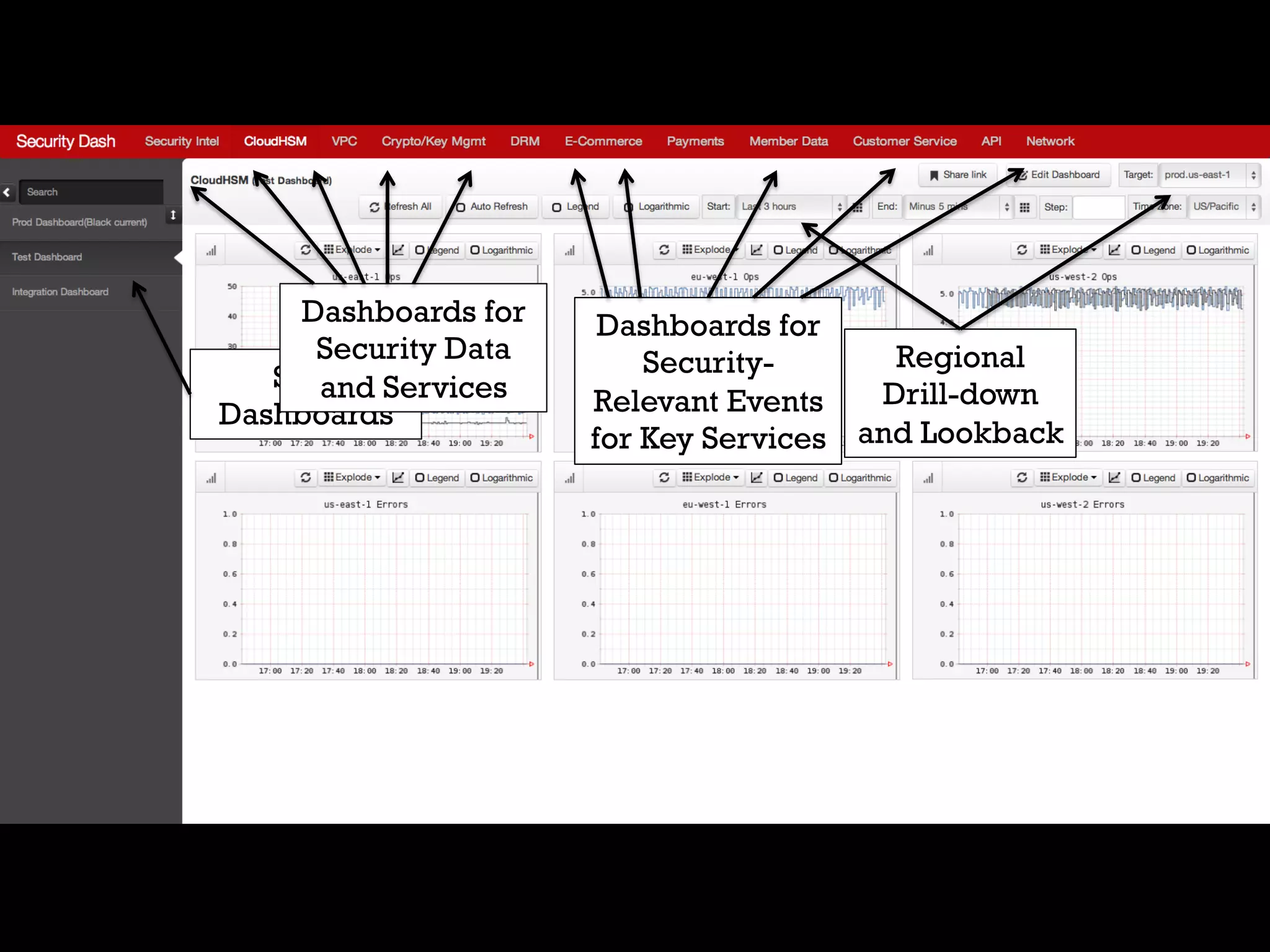
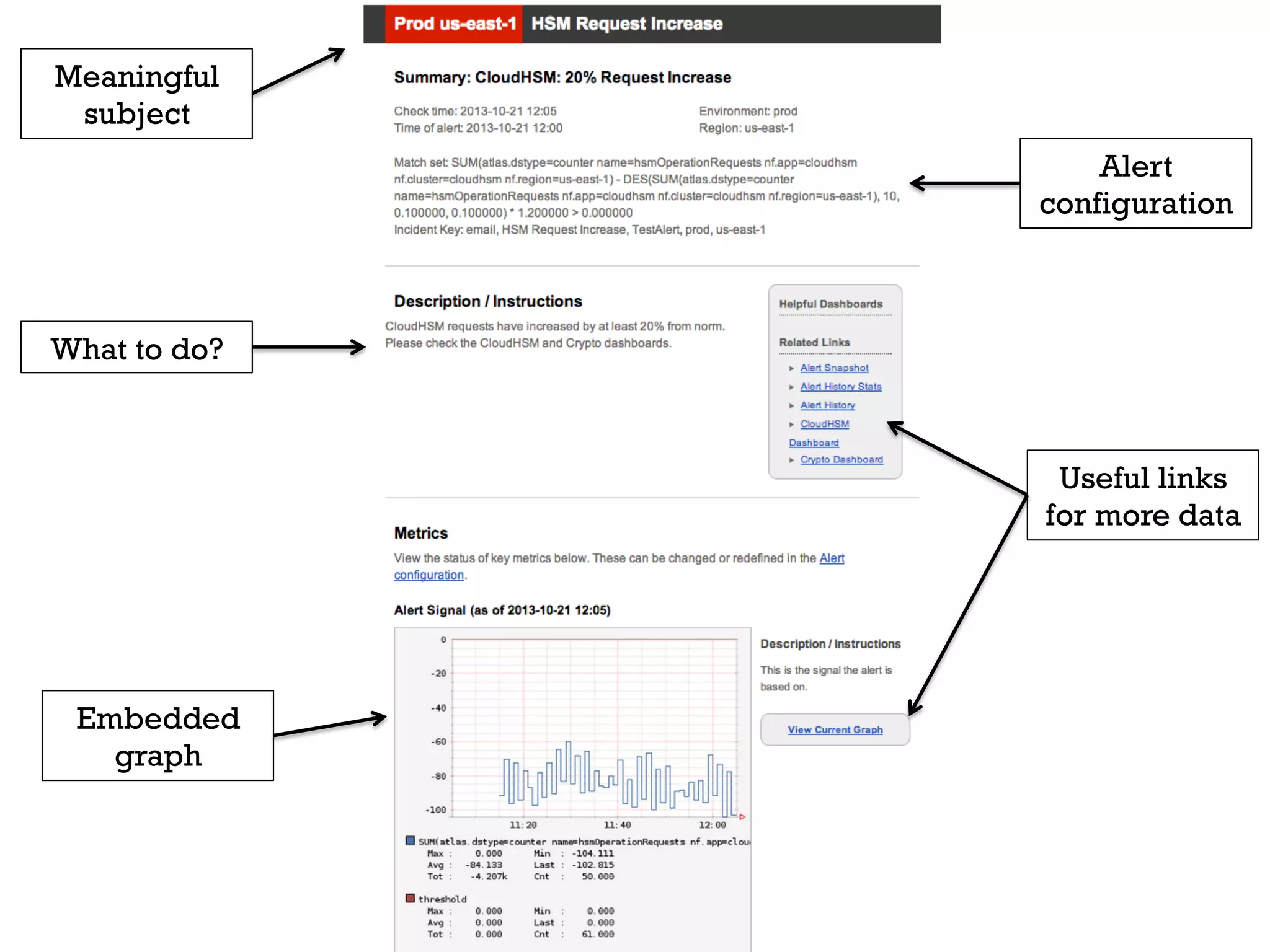
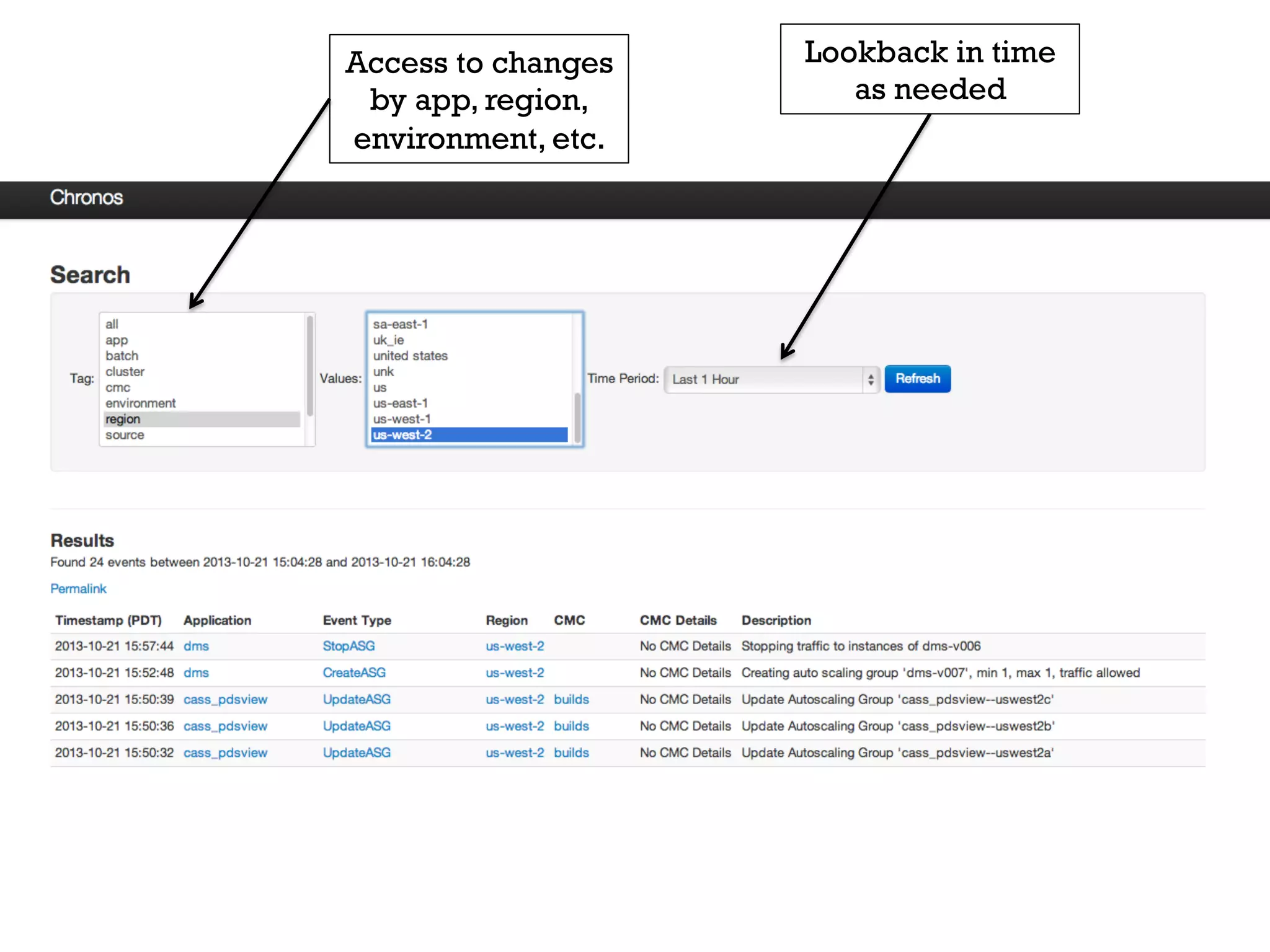
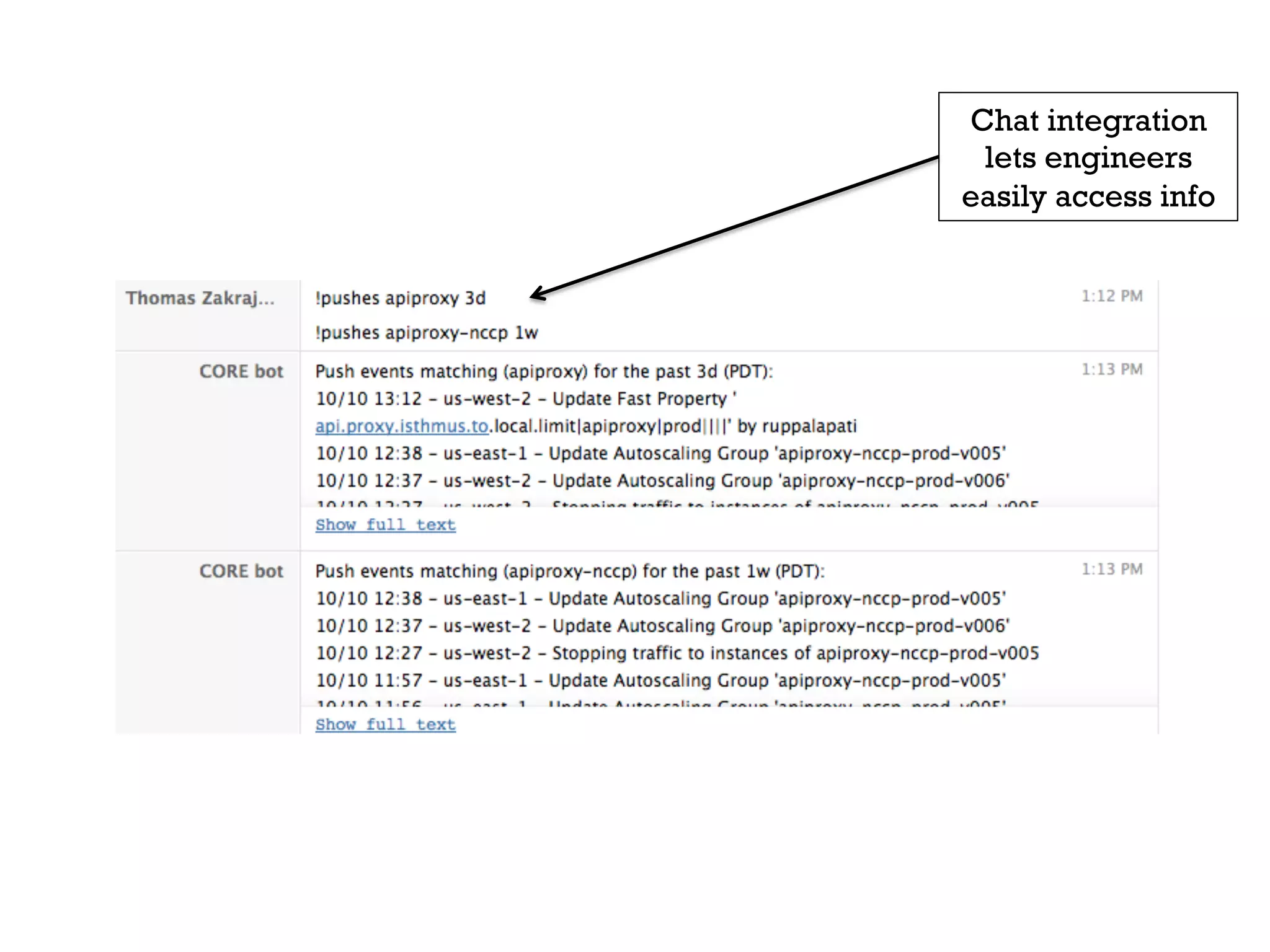
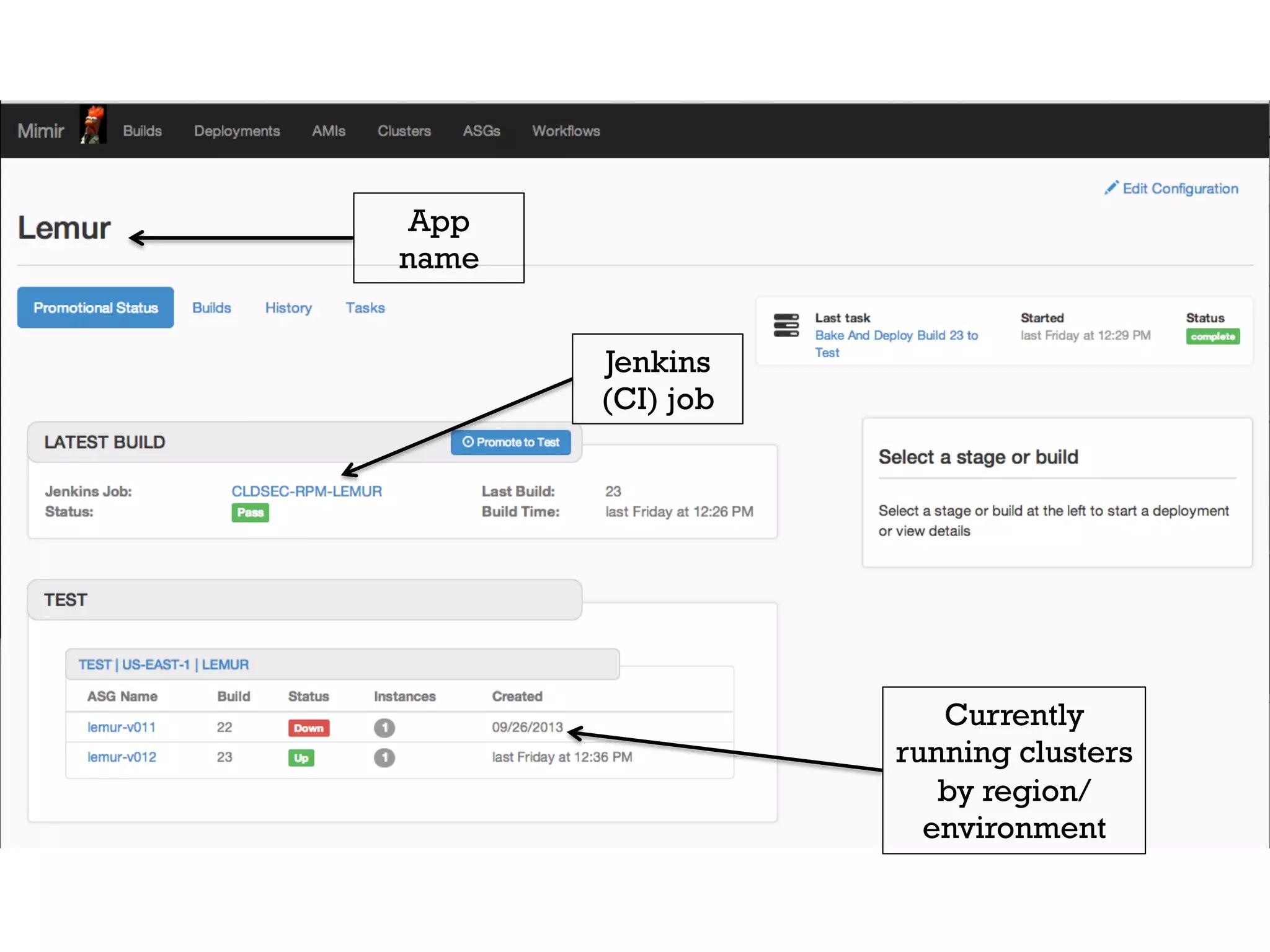
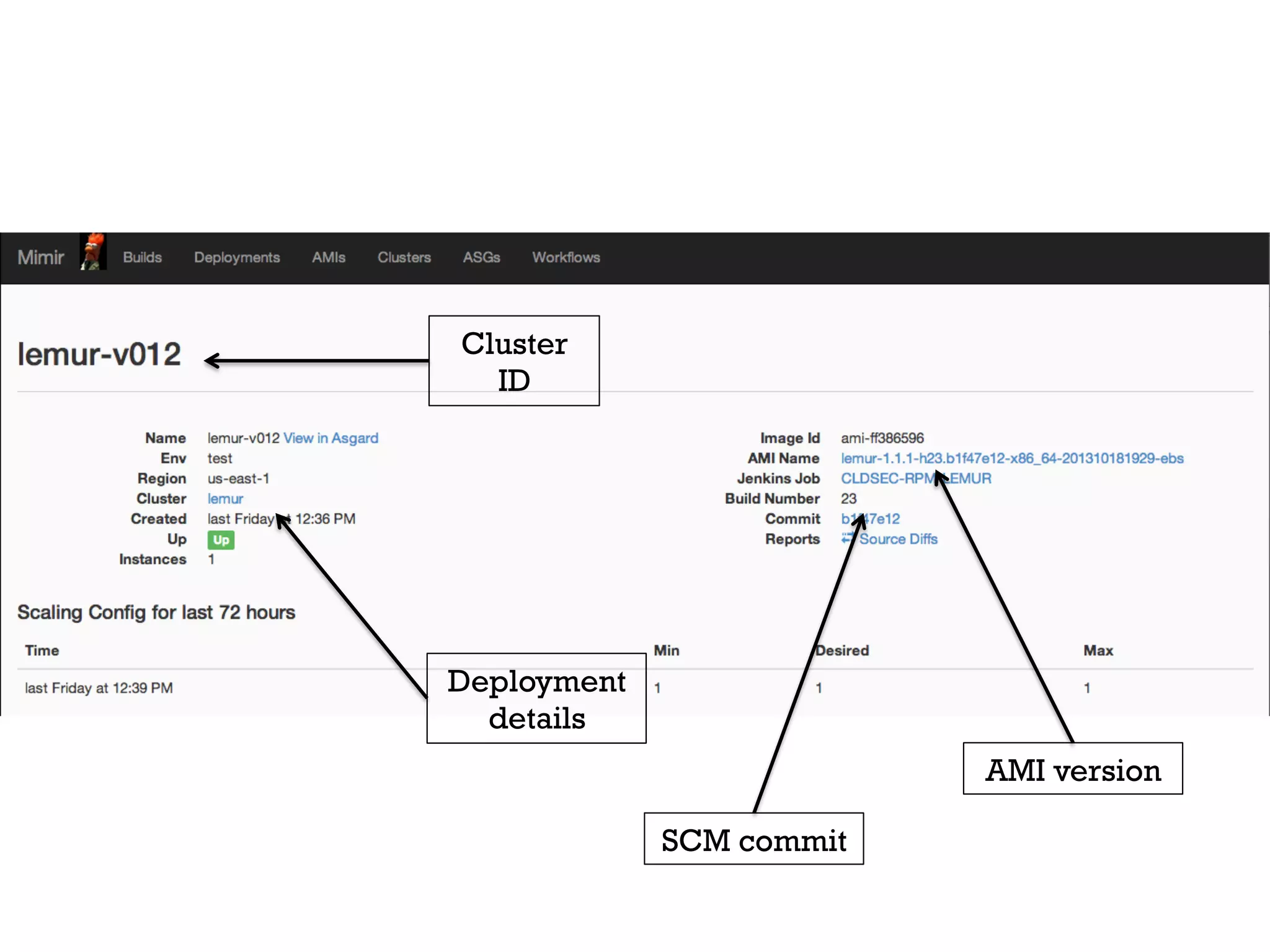
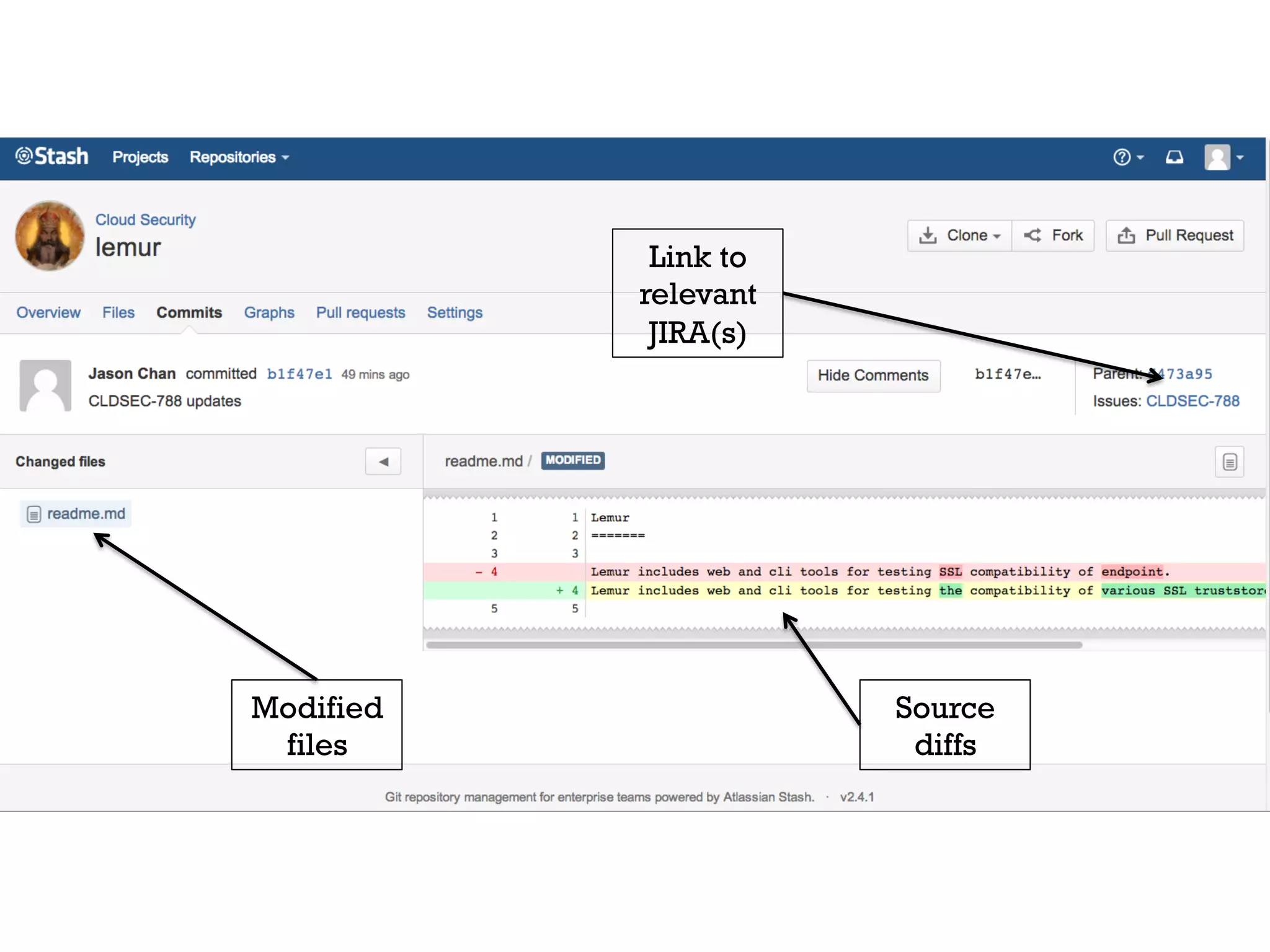
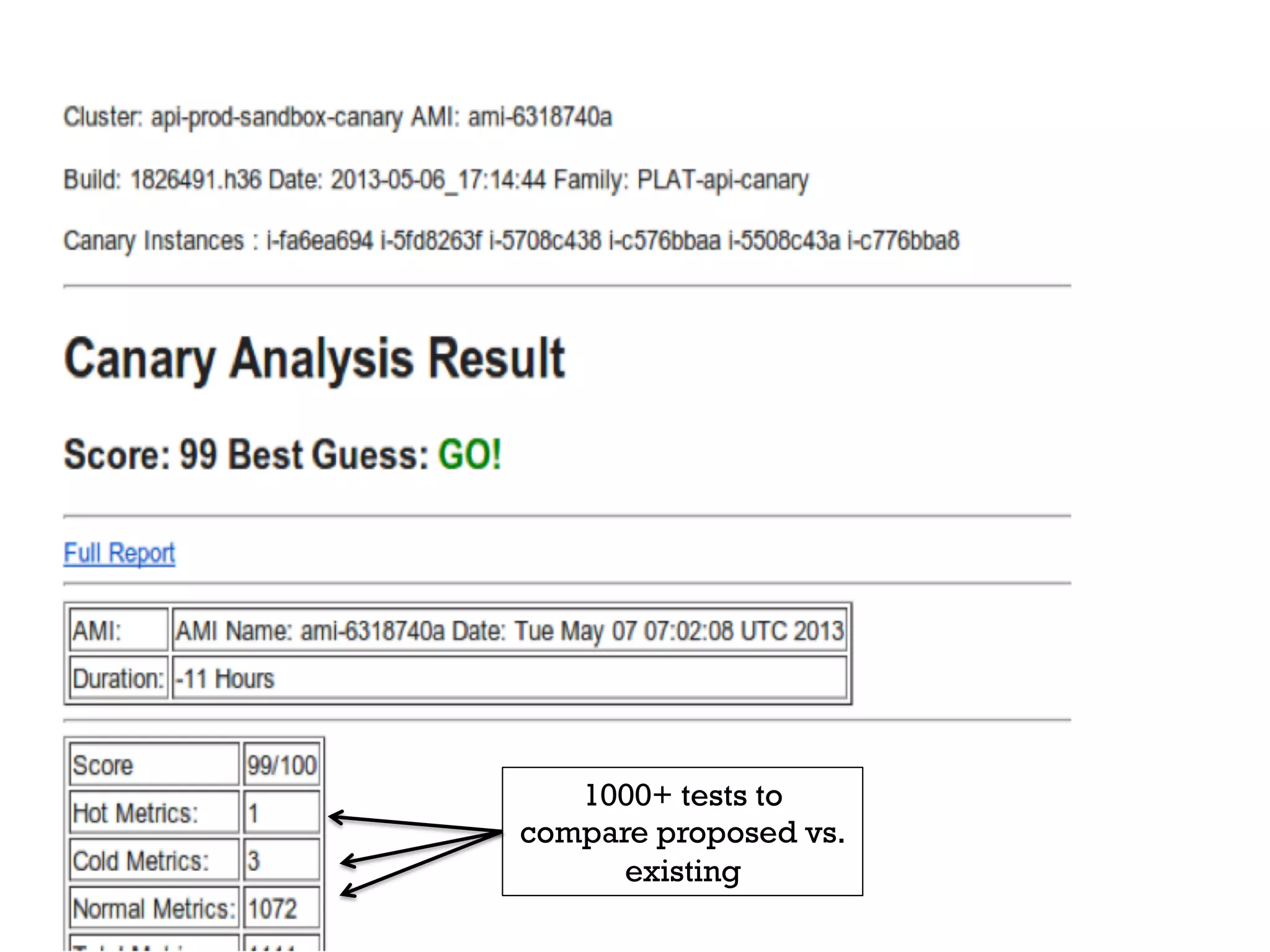
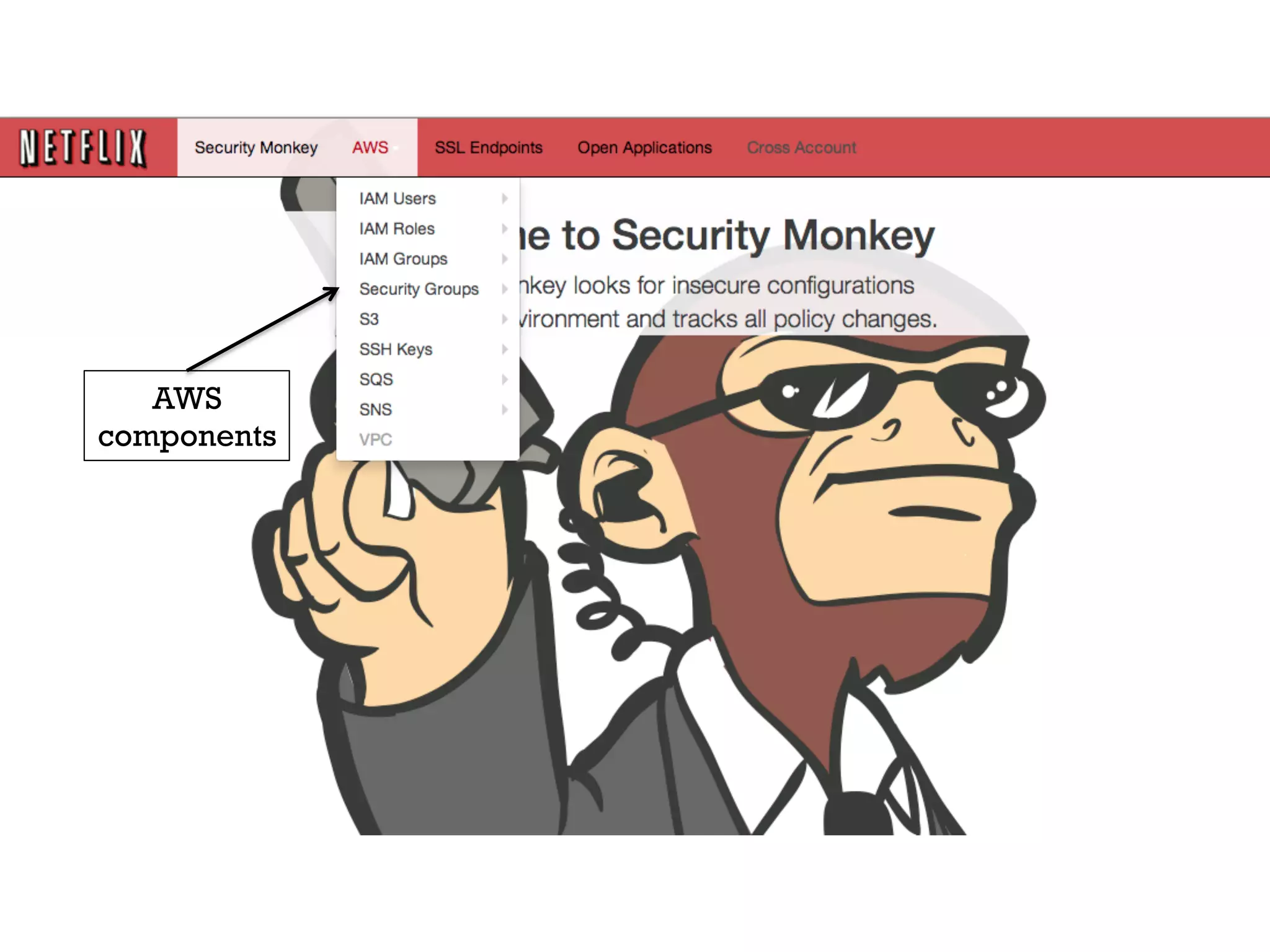
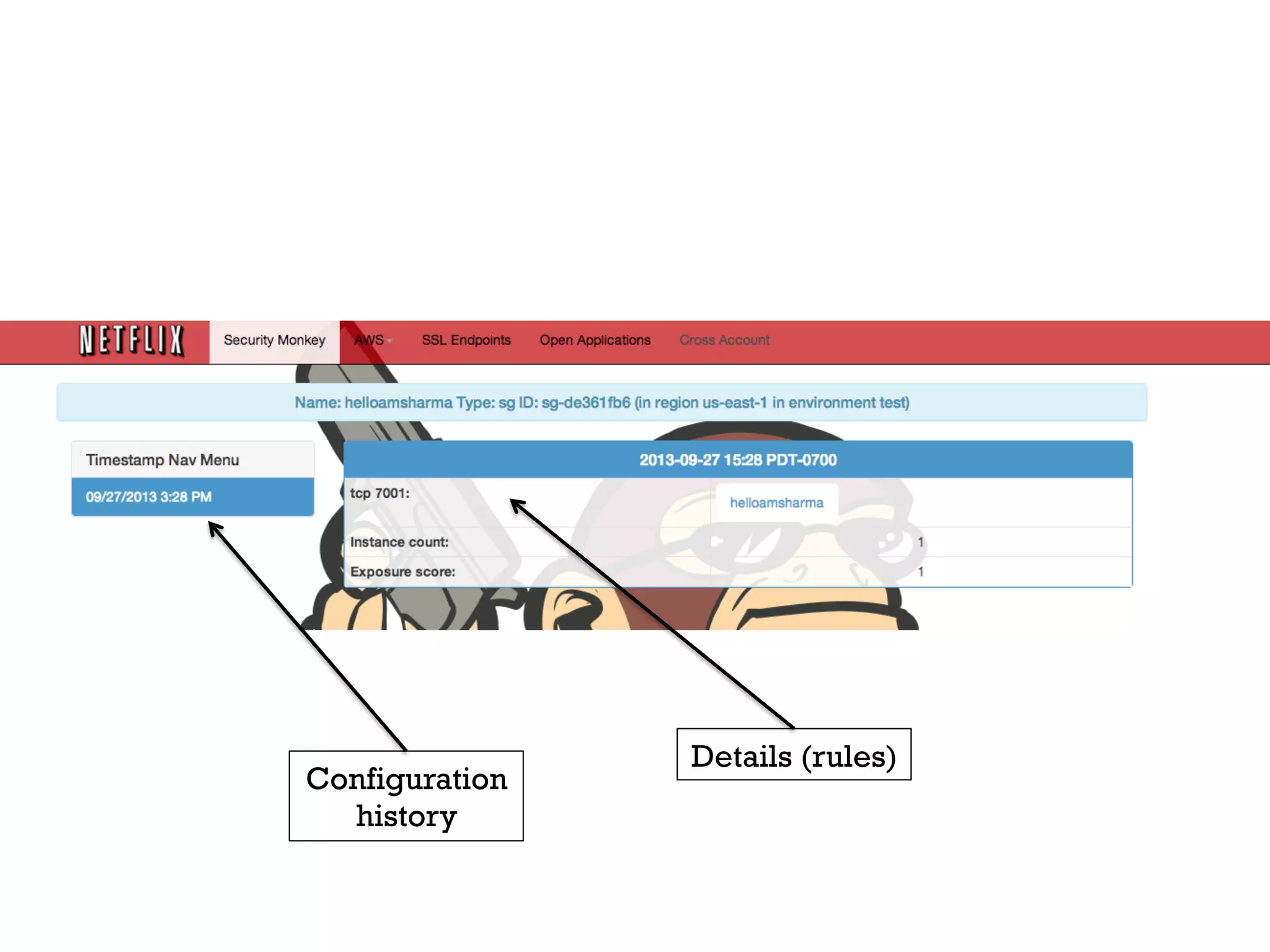
3. Netflix employs approaches like visibility into security-related data, automation through over 1000 tests, and an immutable server pattern to enable security in their fast-paced, cloud-based environment.