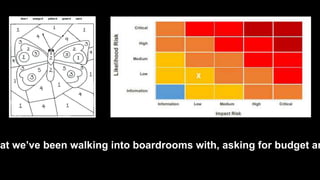
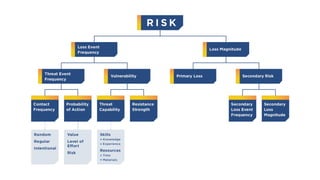
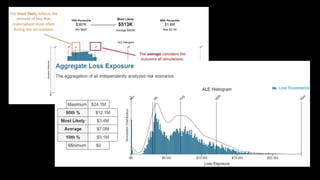
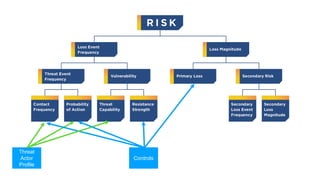
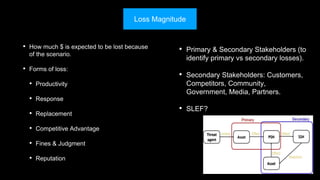
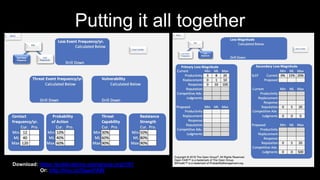
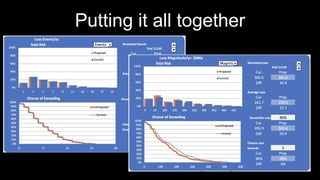
The document outlines the fundamentals of quantitative risk analysis, addressing key concepts like assets, threats, vulnerabilities, and risk definitions. It presents a structured approach for assessing risk scenarios, particularly in the context of cybersecurity, emphasizing the importance of threat actor profiles and the effectiveness of controls. It advises organizations to adapt frameworks to their specific needs while integrating both quantitative and qualitative assessment methods.