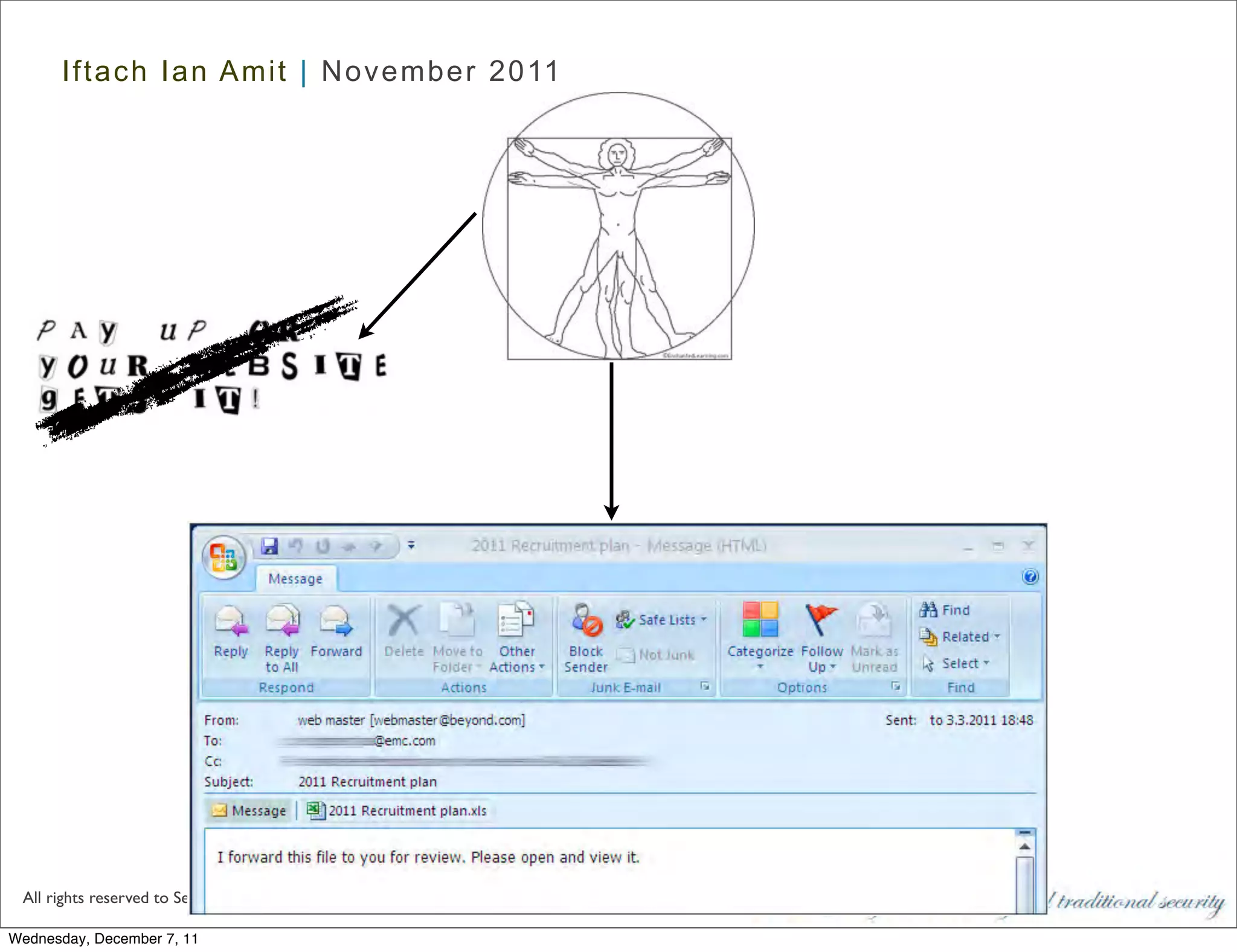
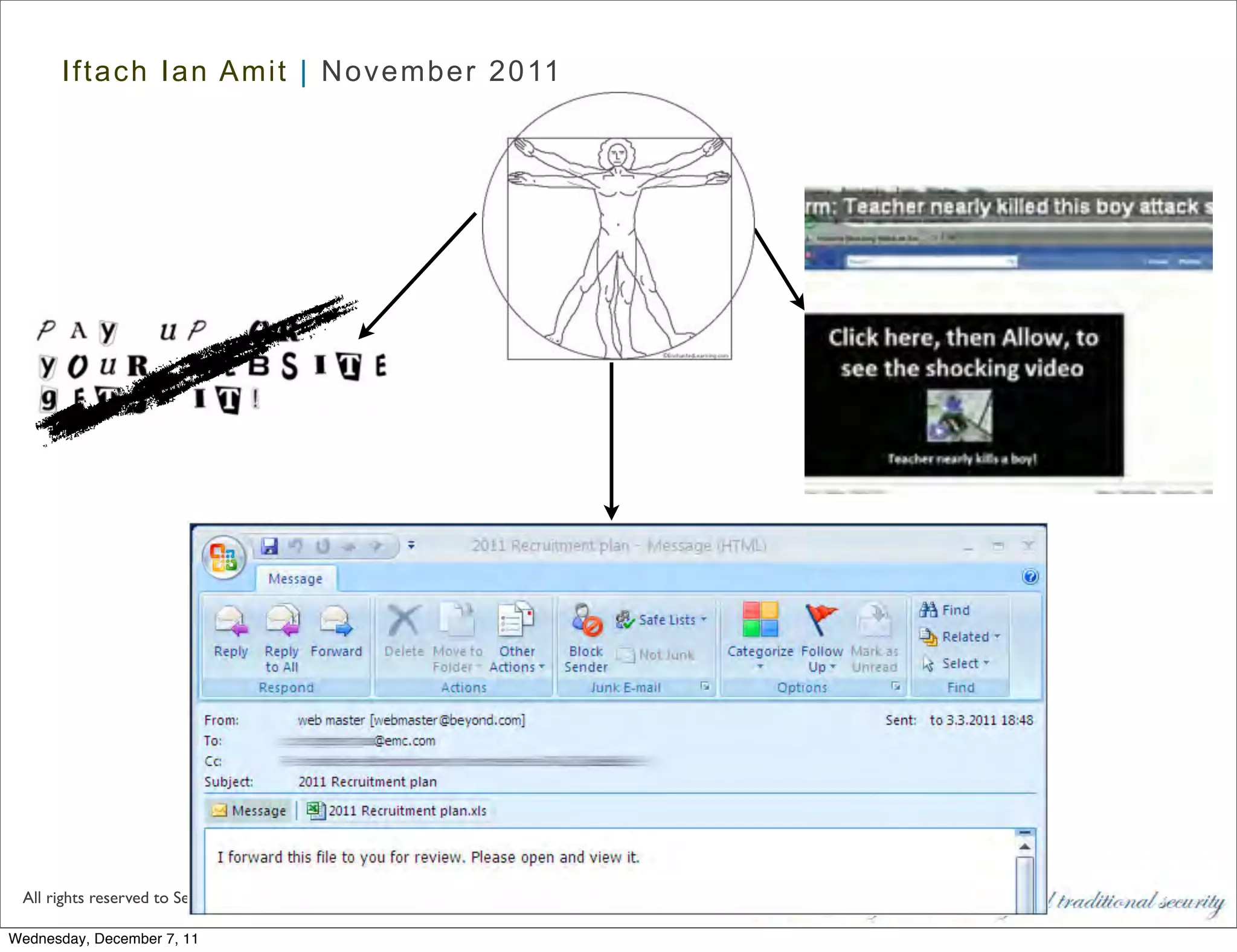
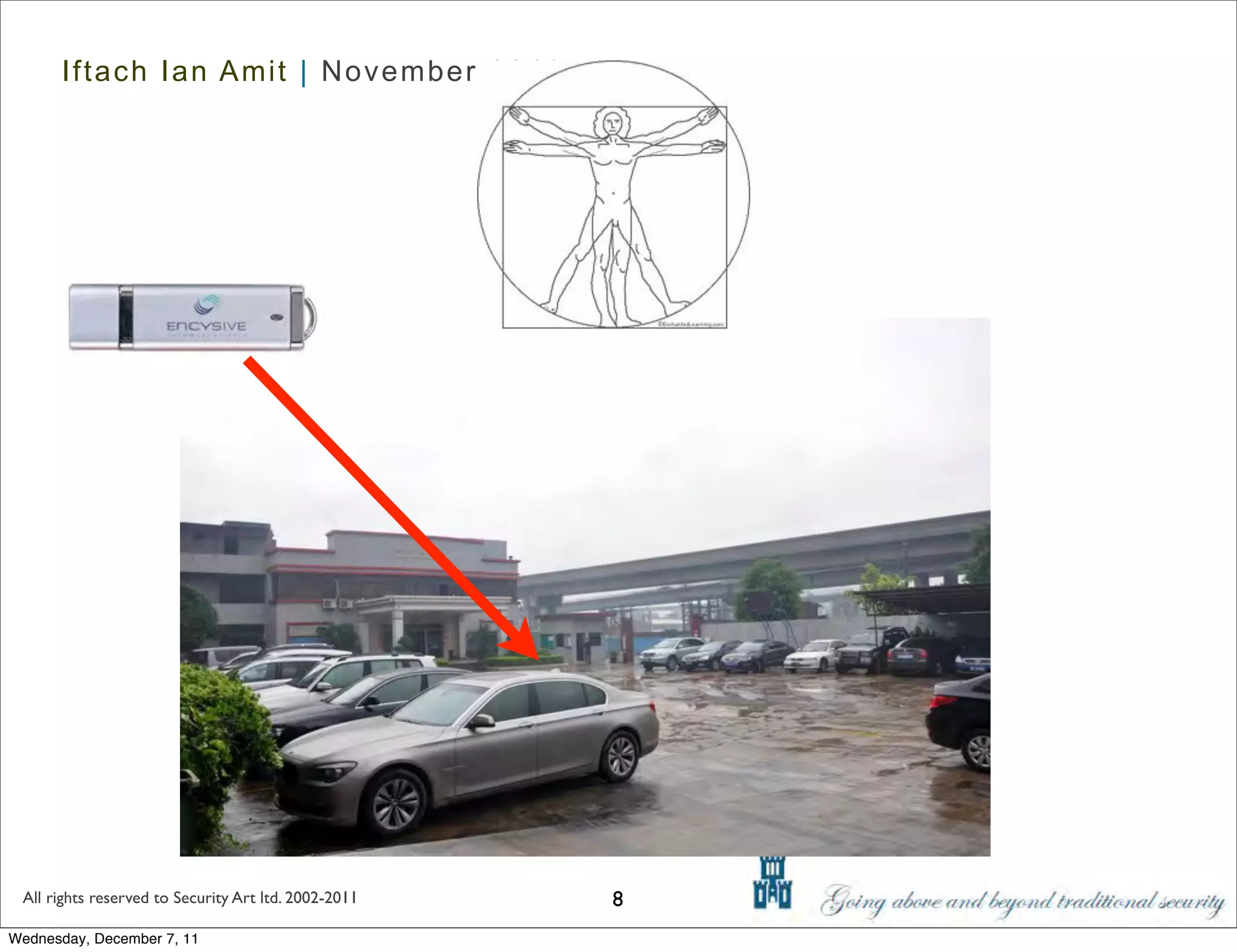
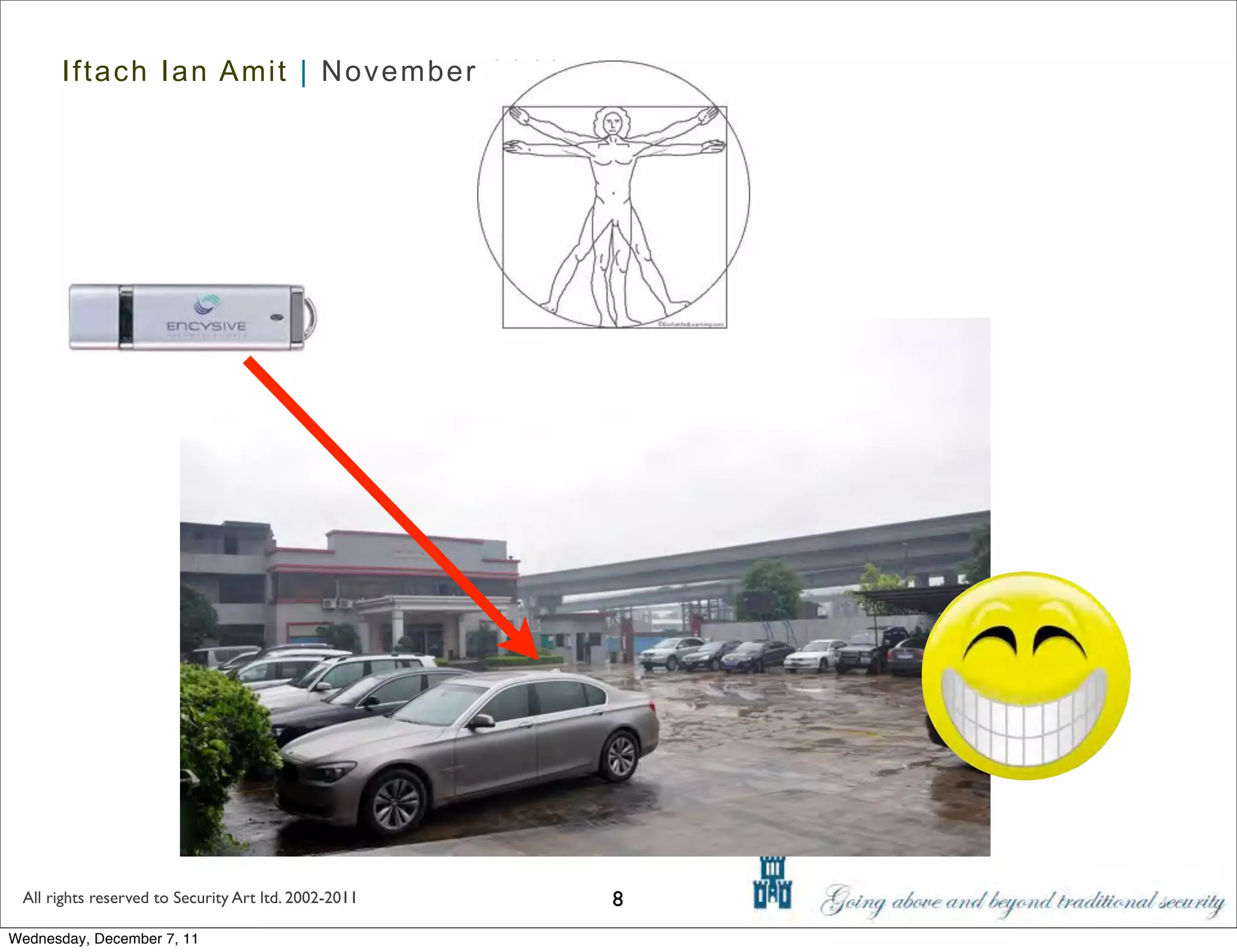
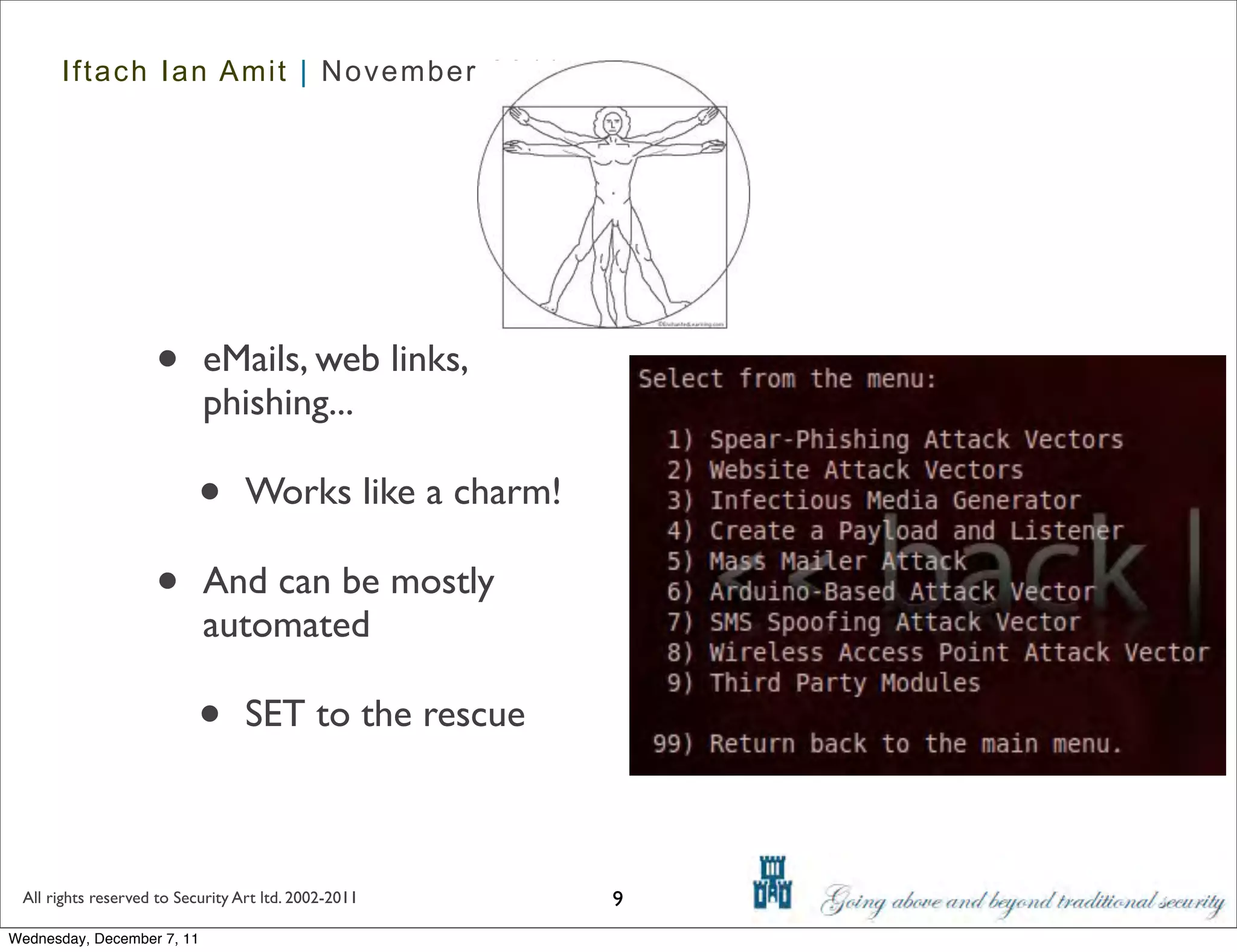
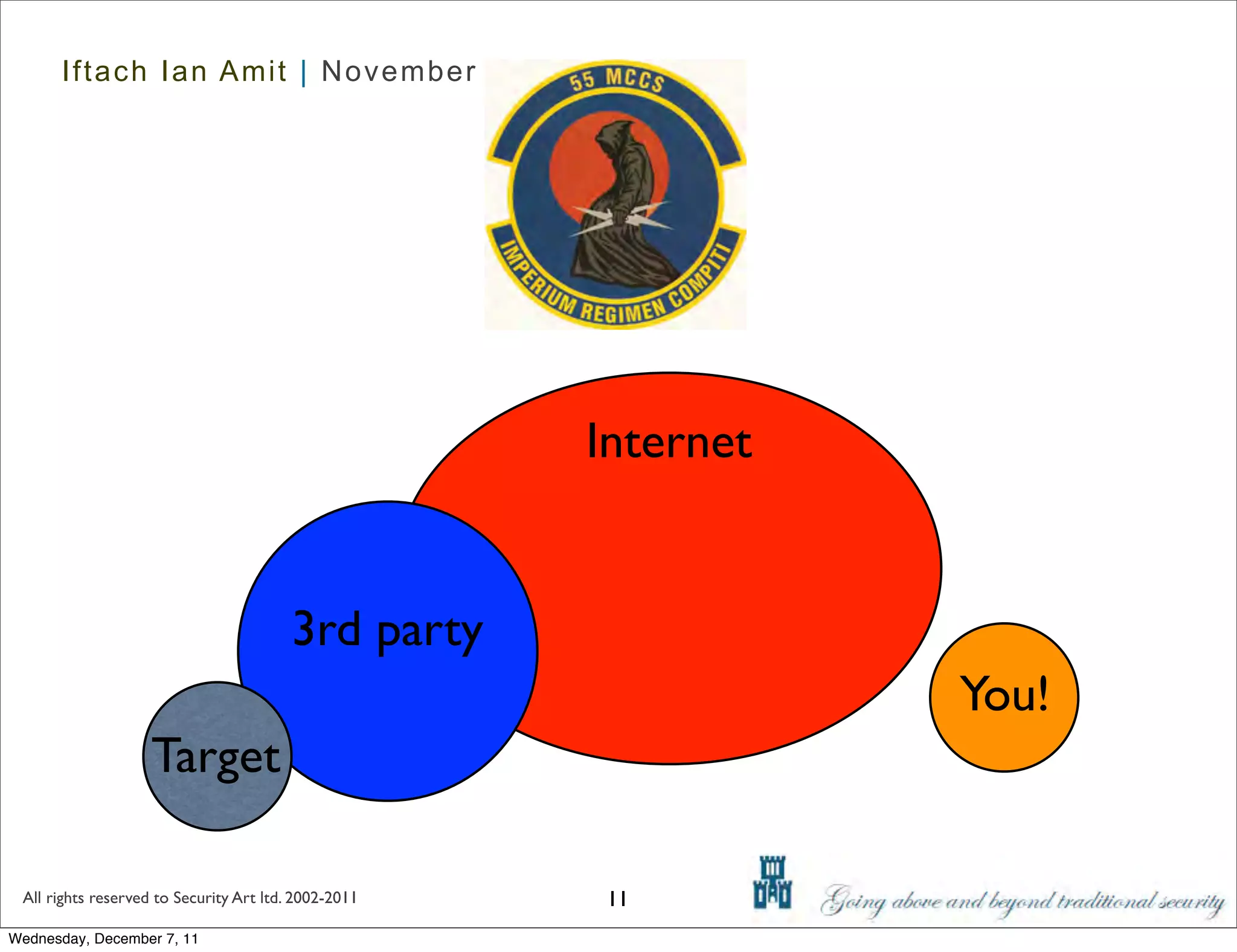
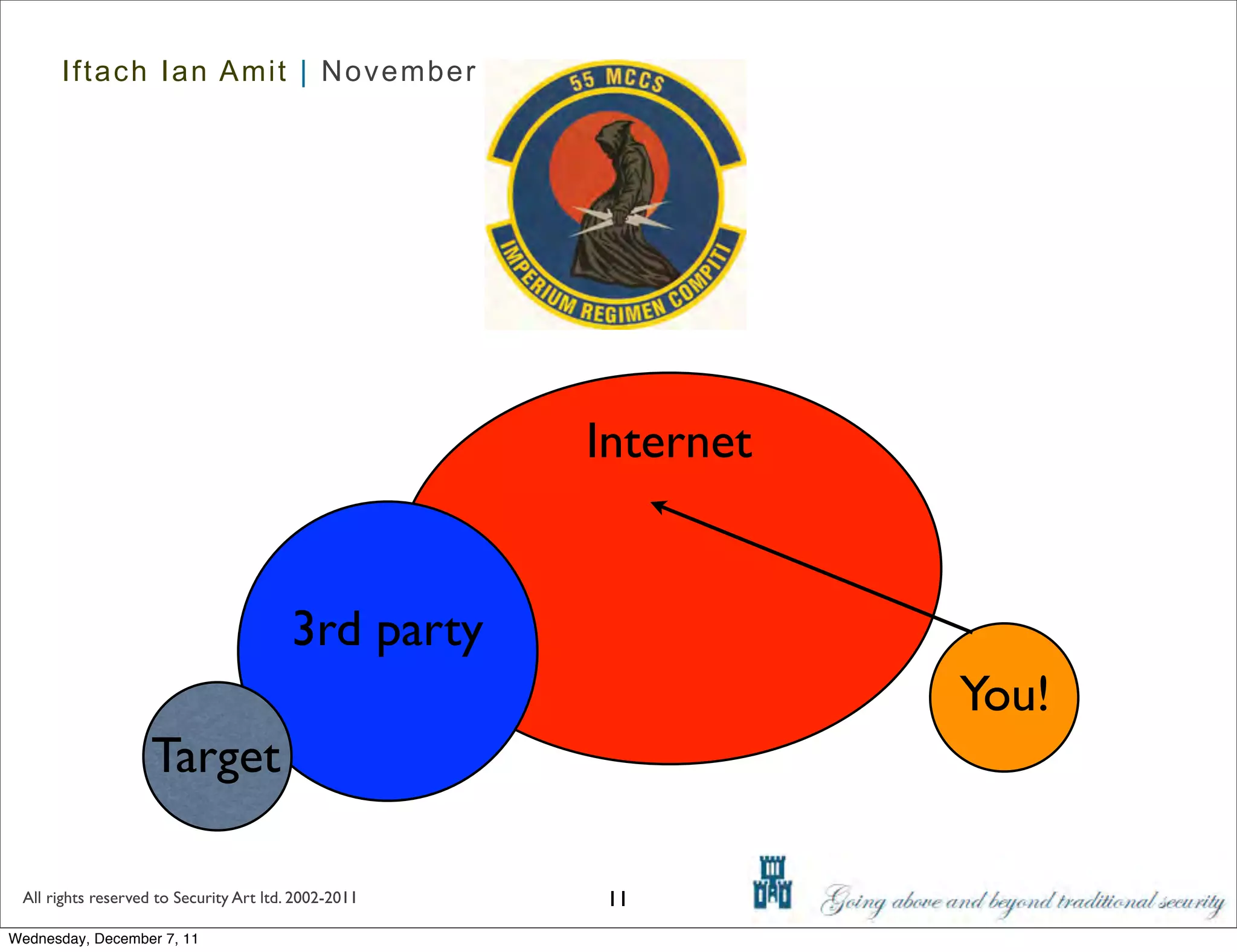
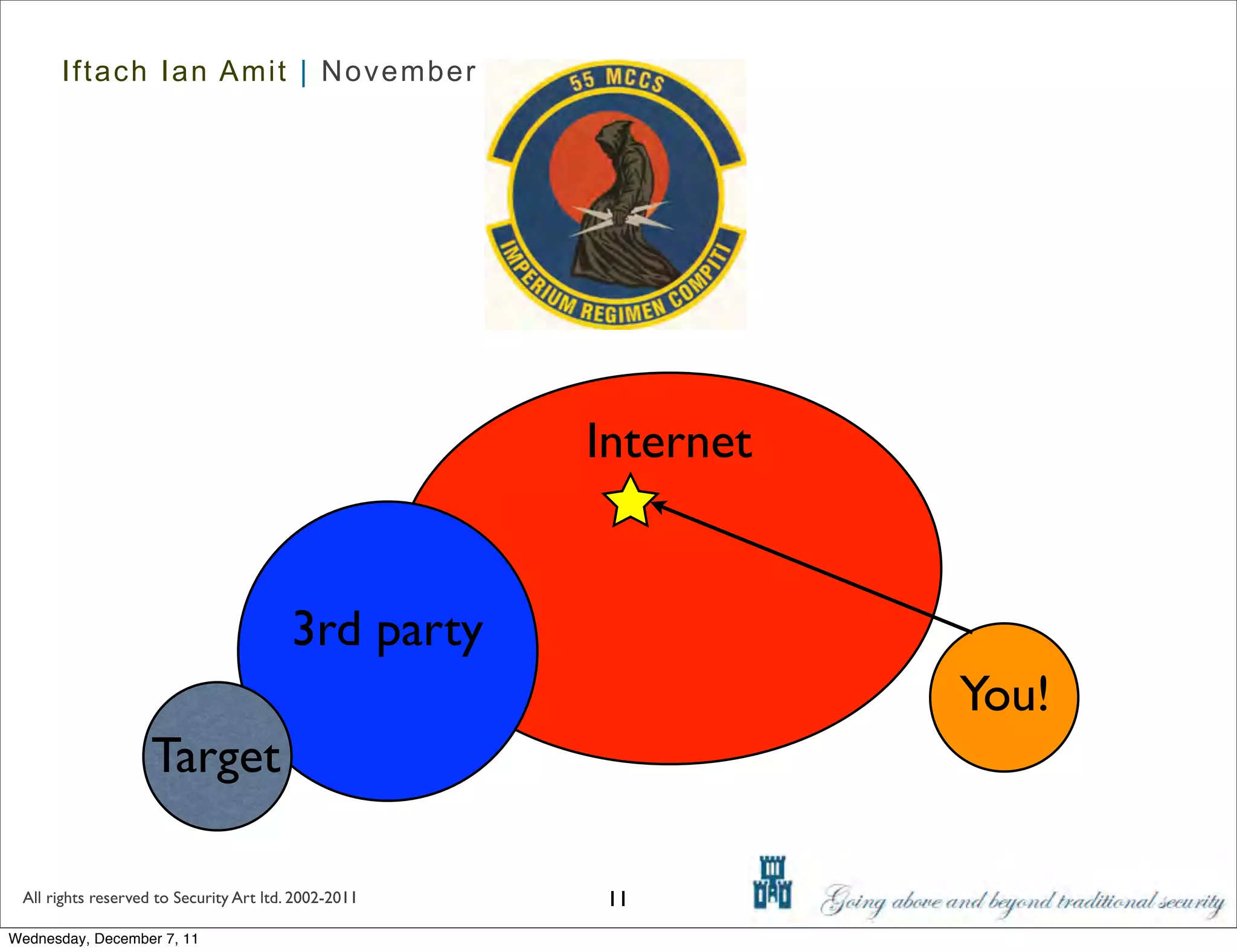
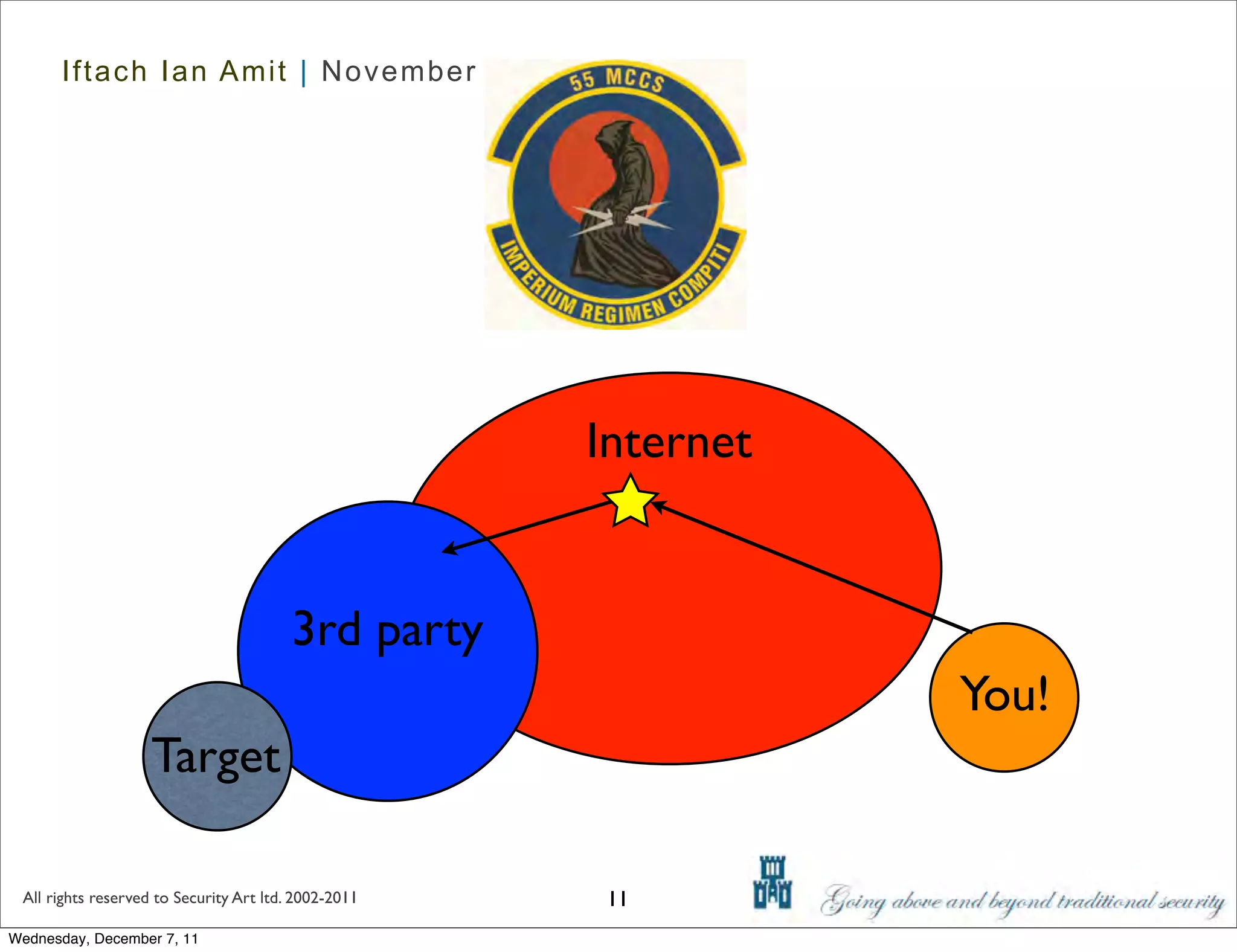
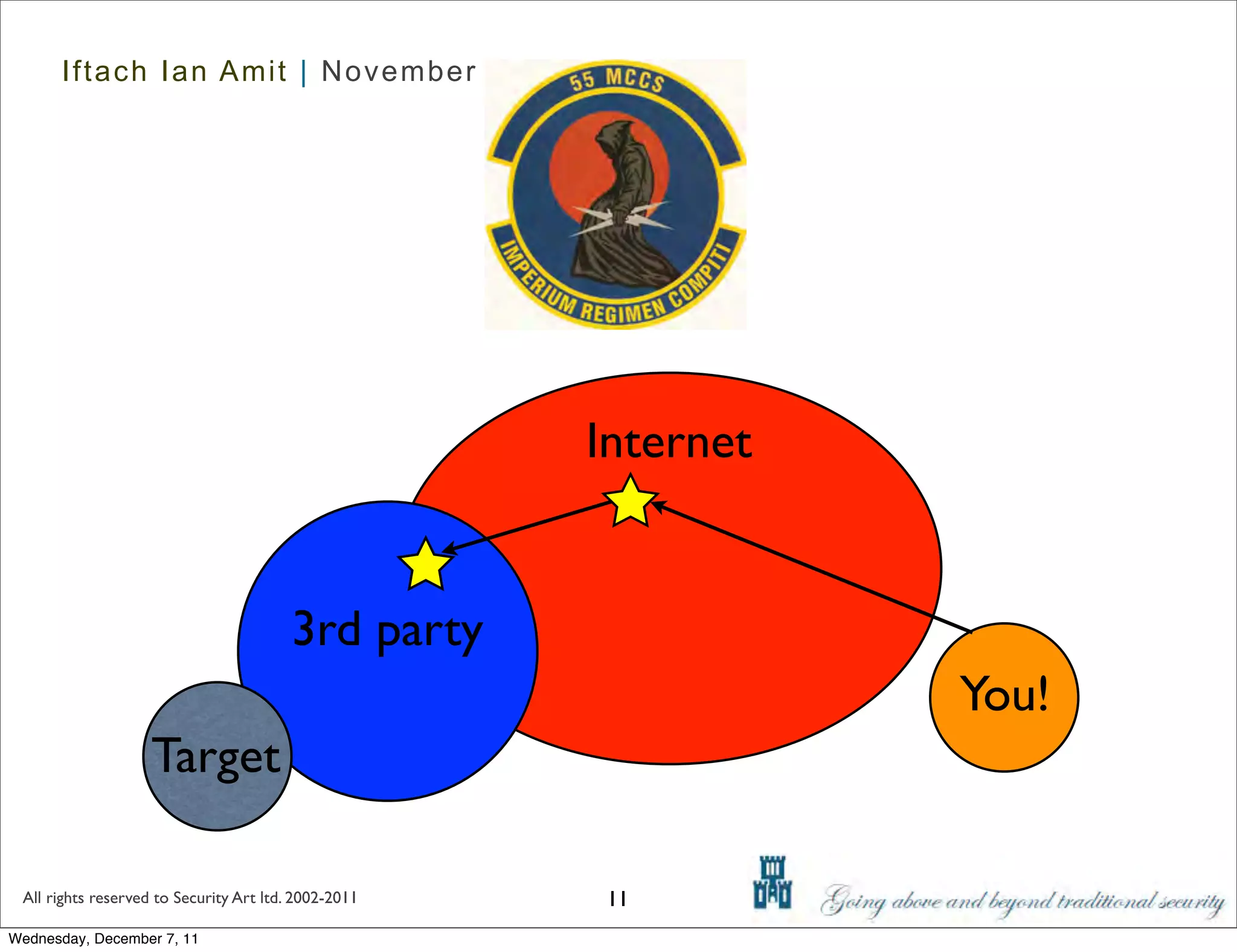
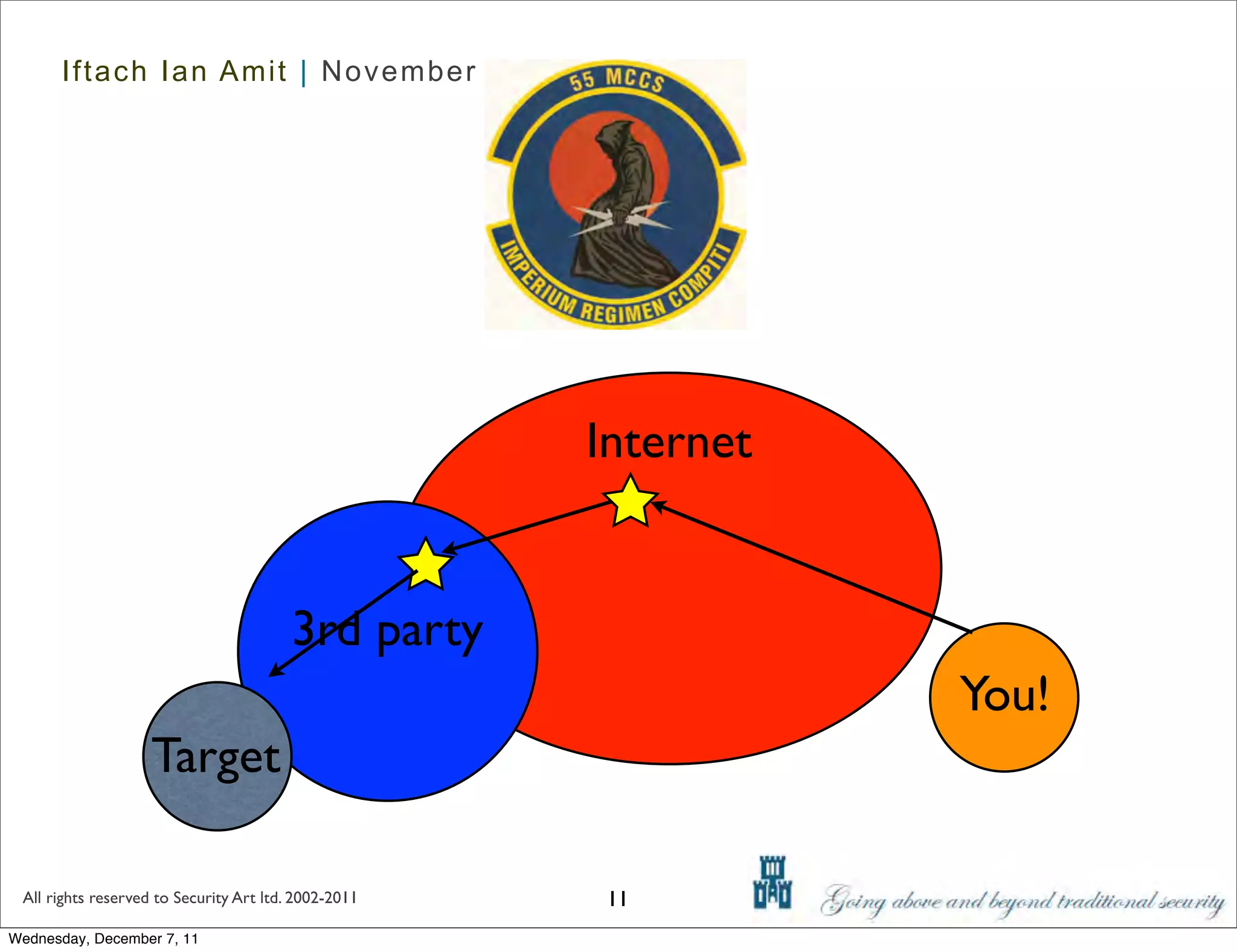
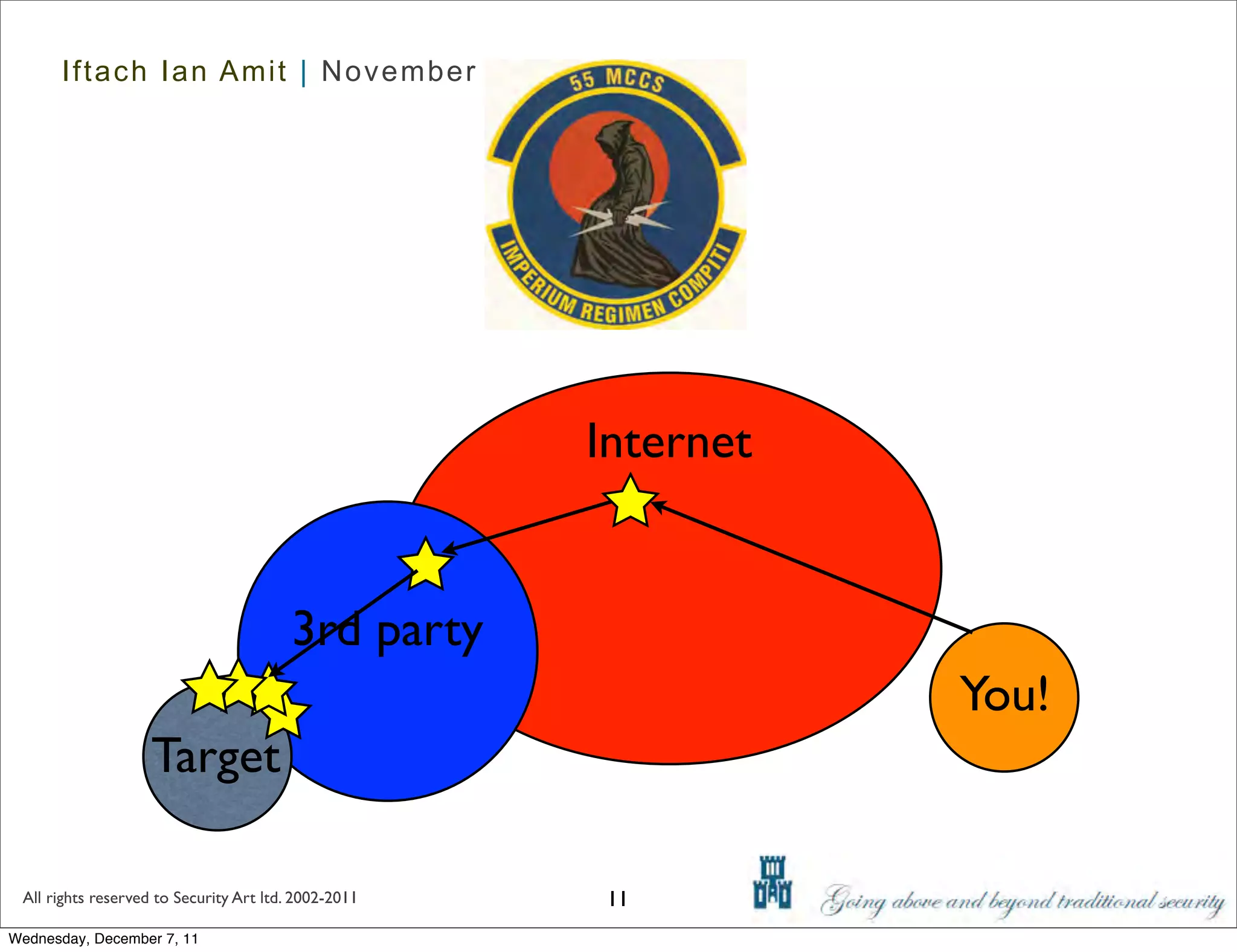
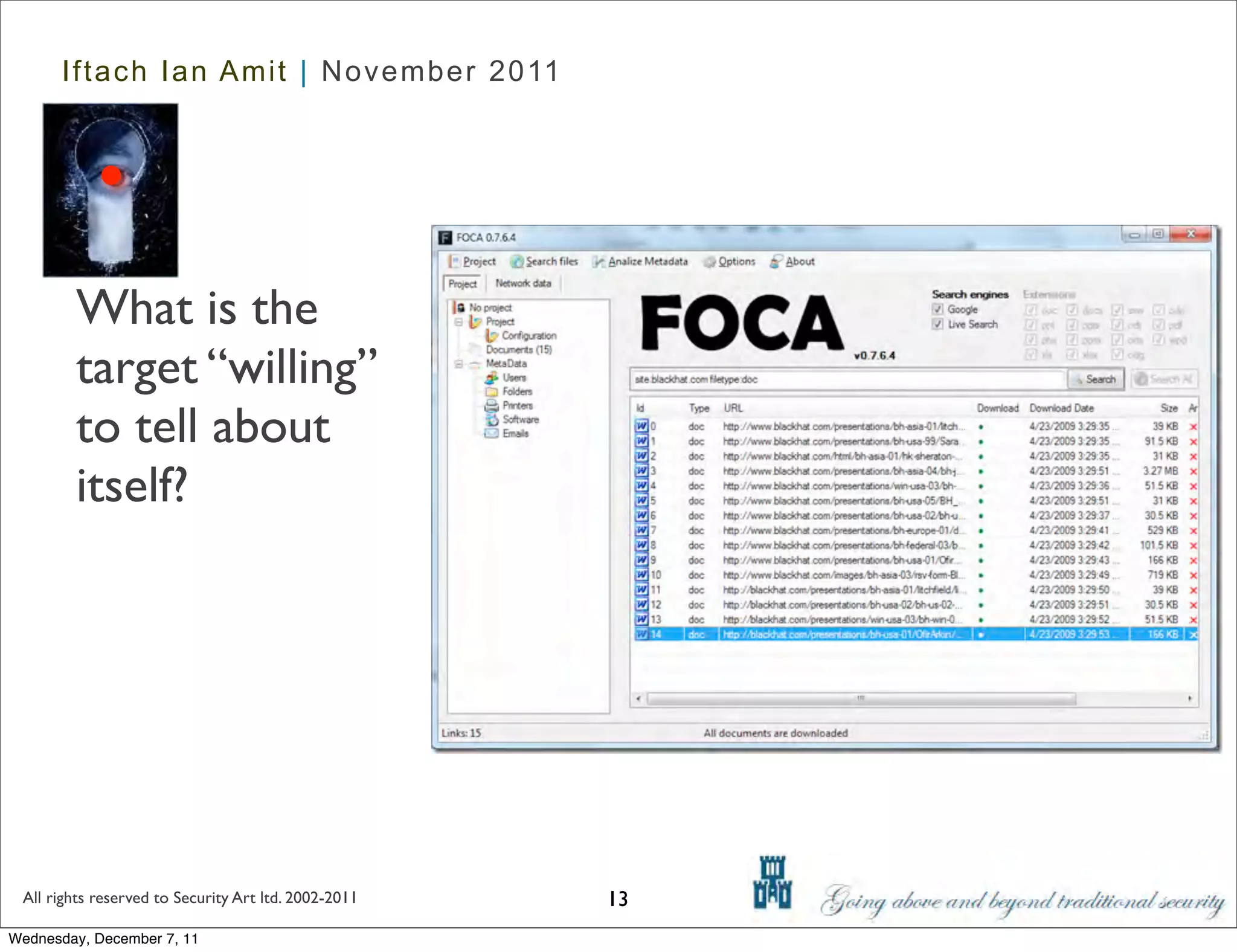
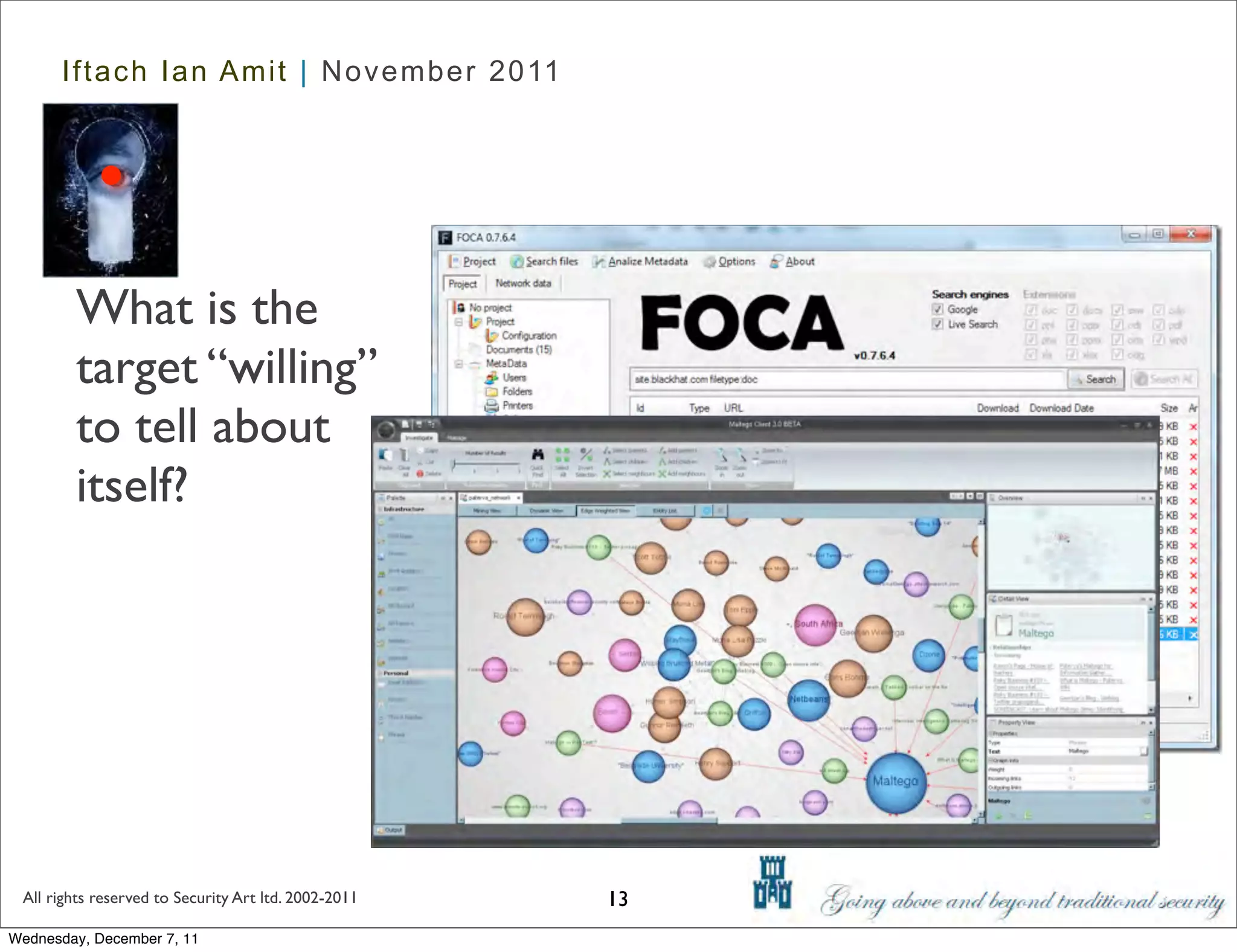
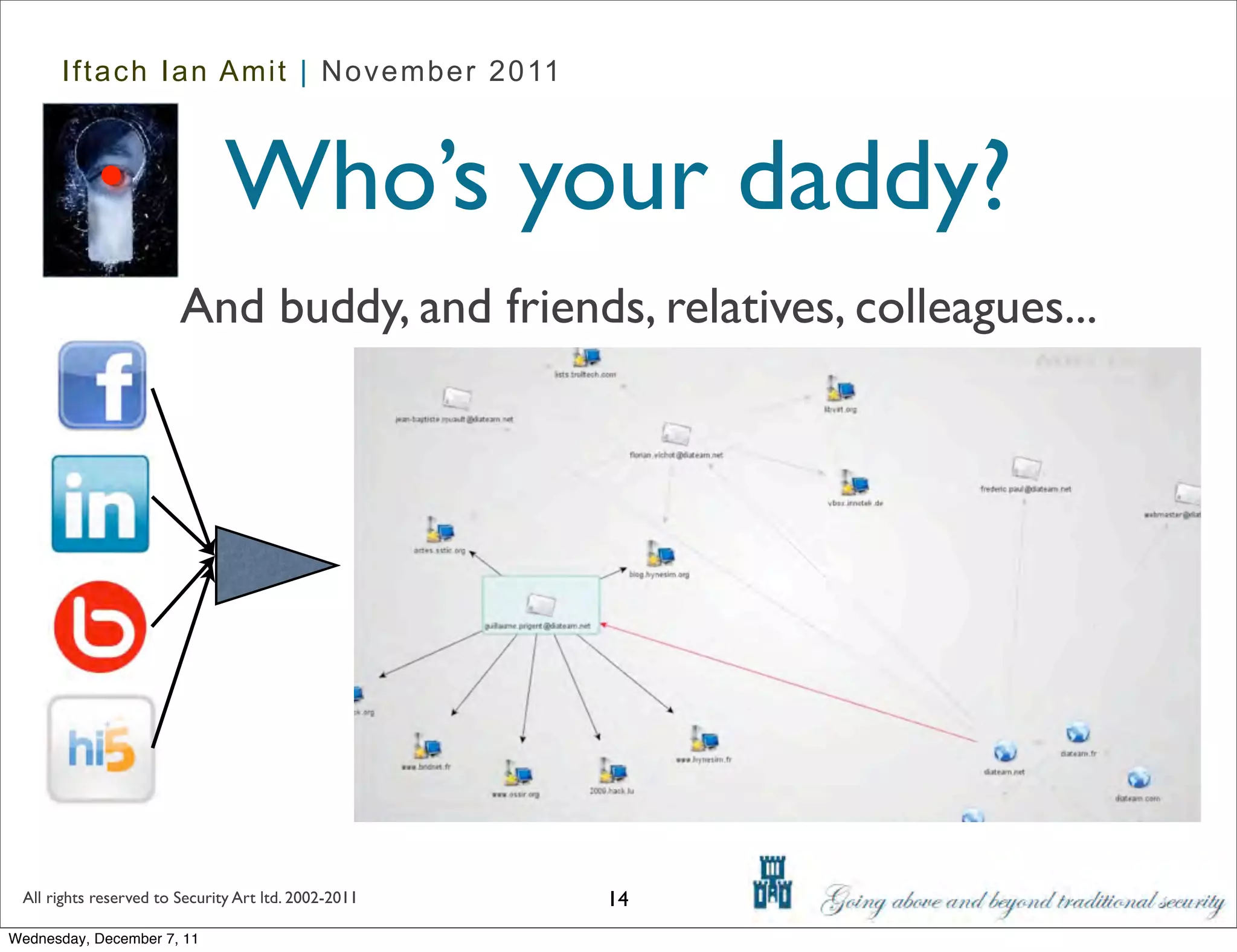
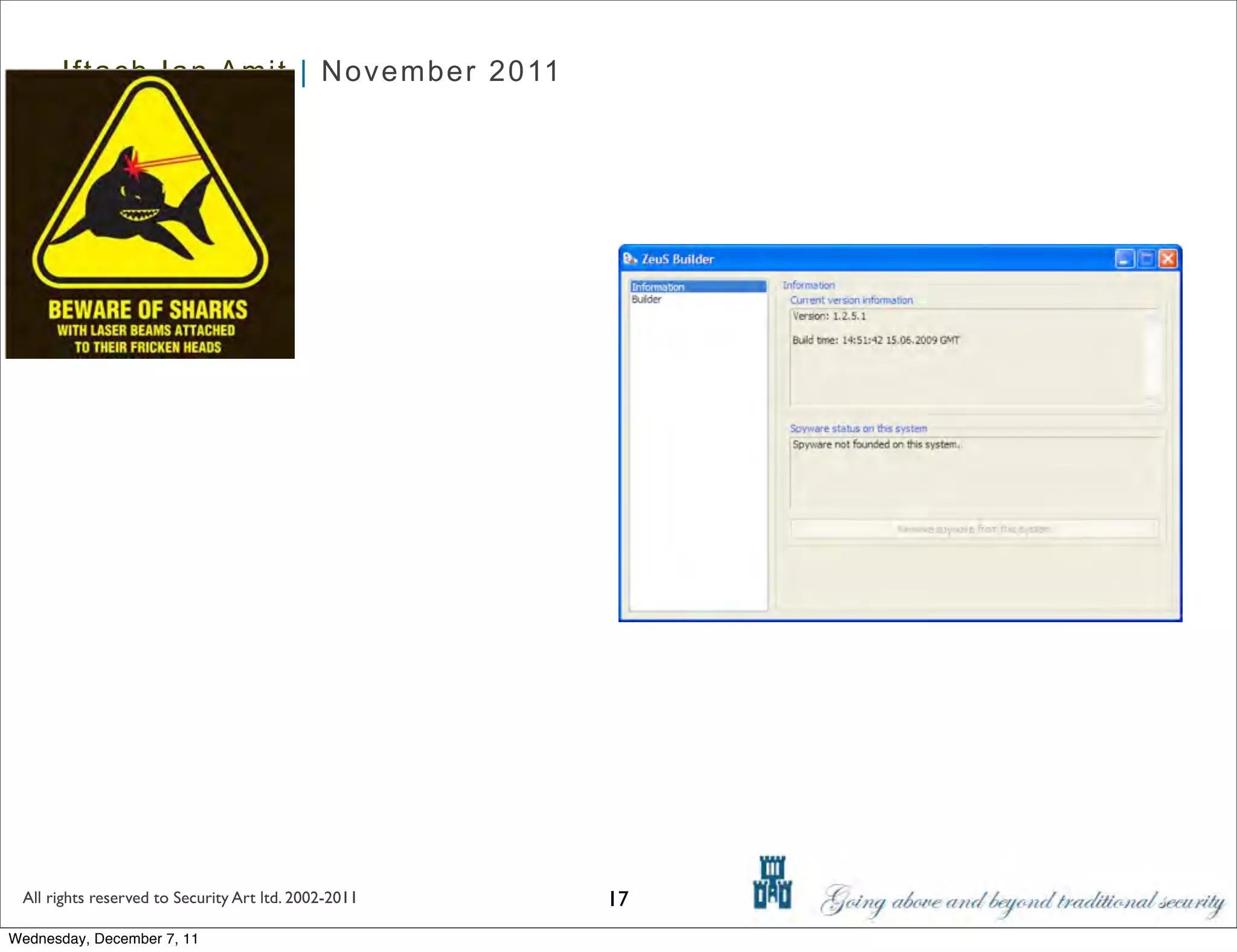
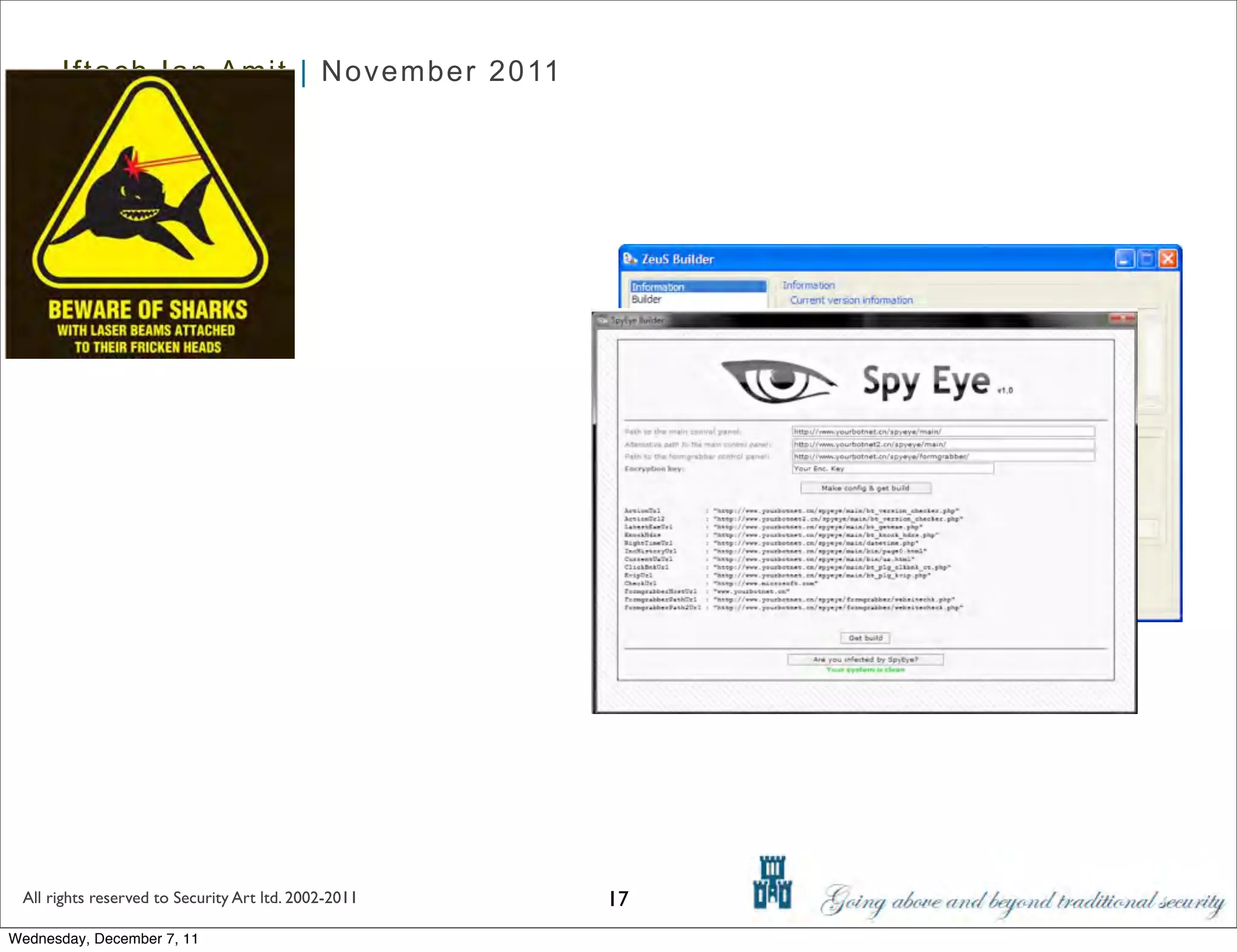
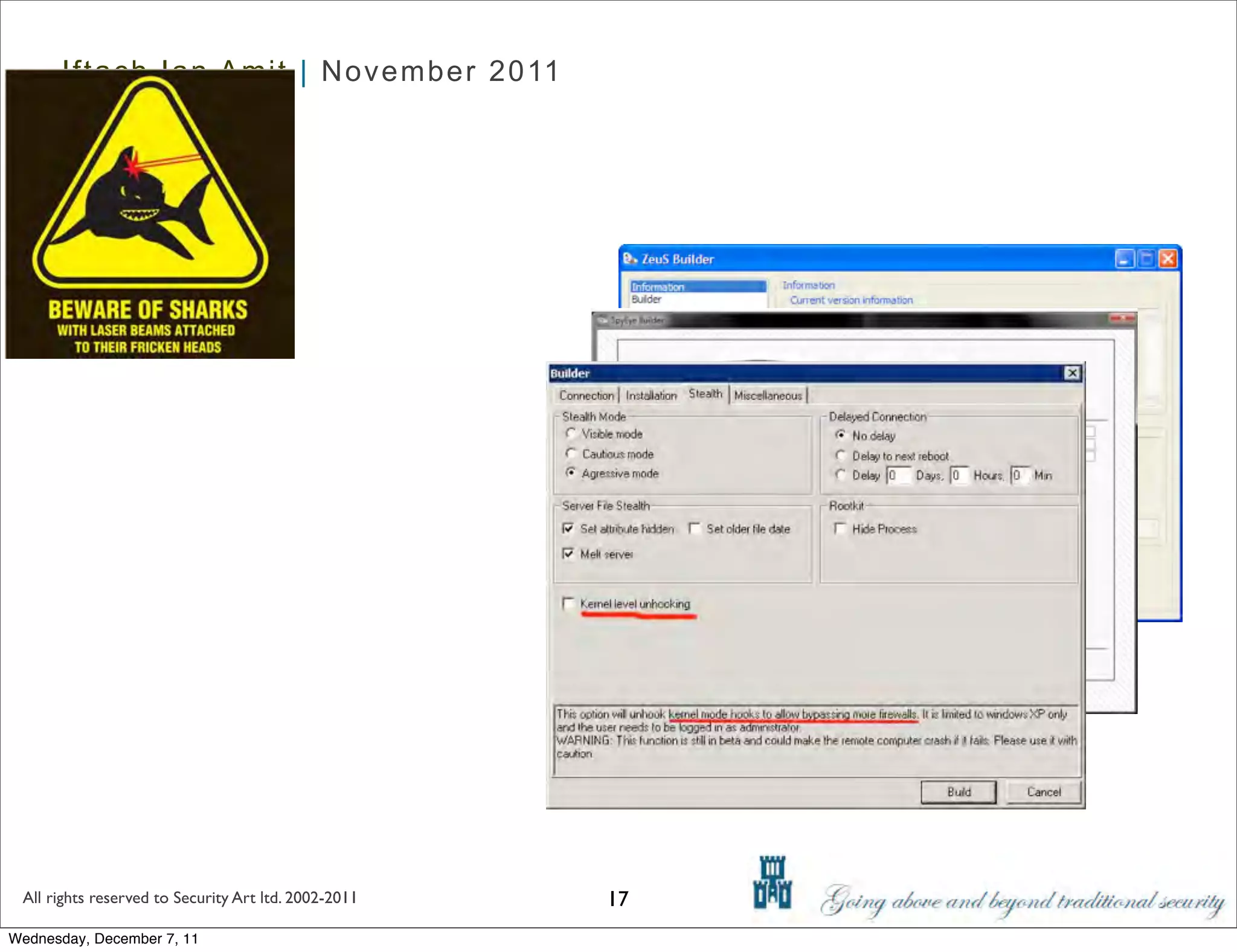
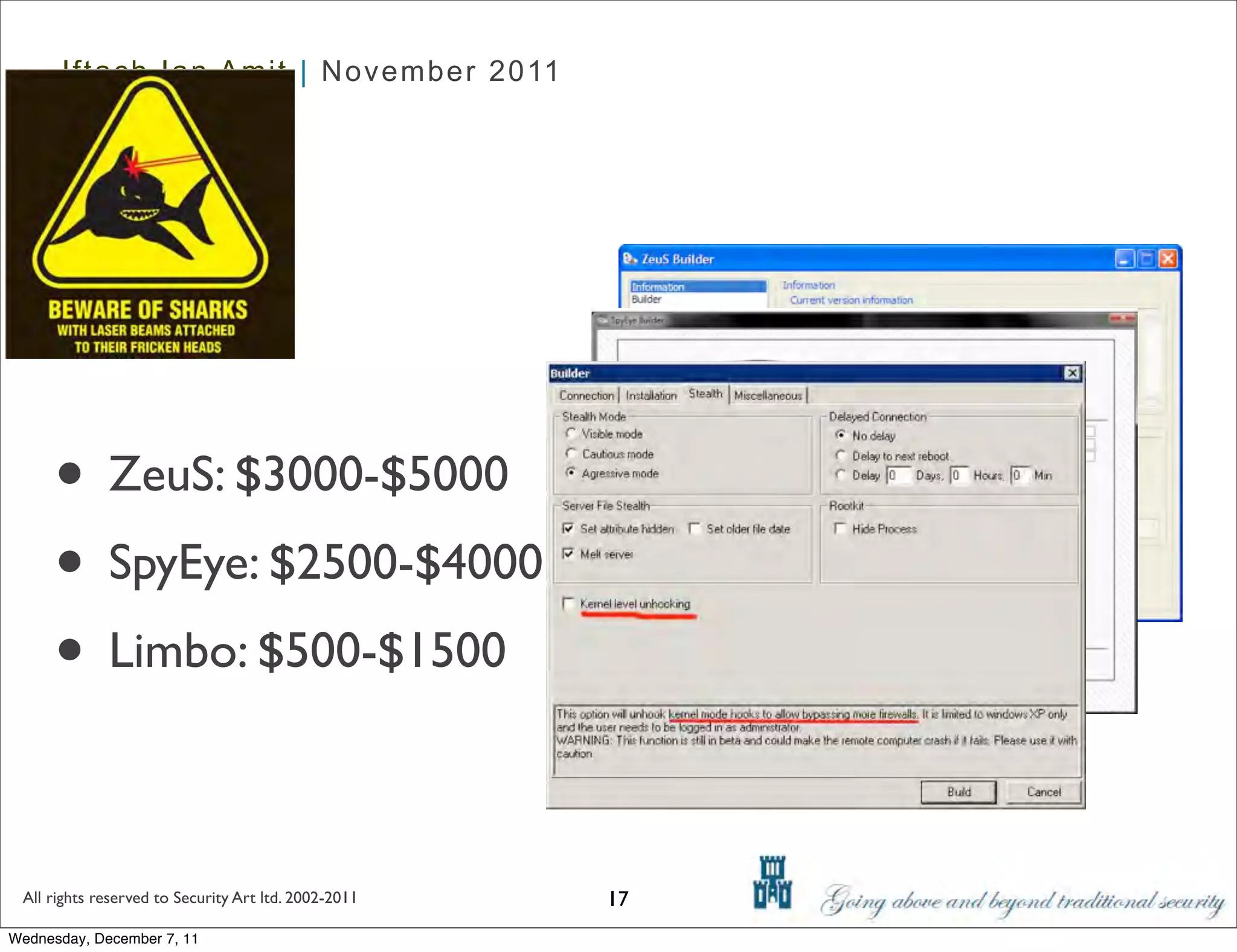
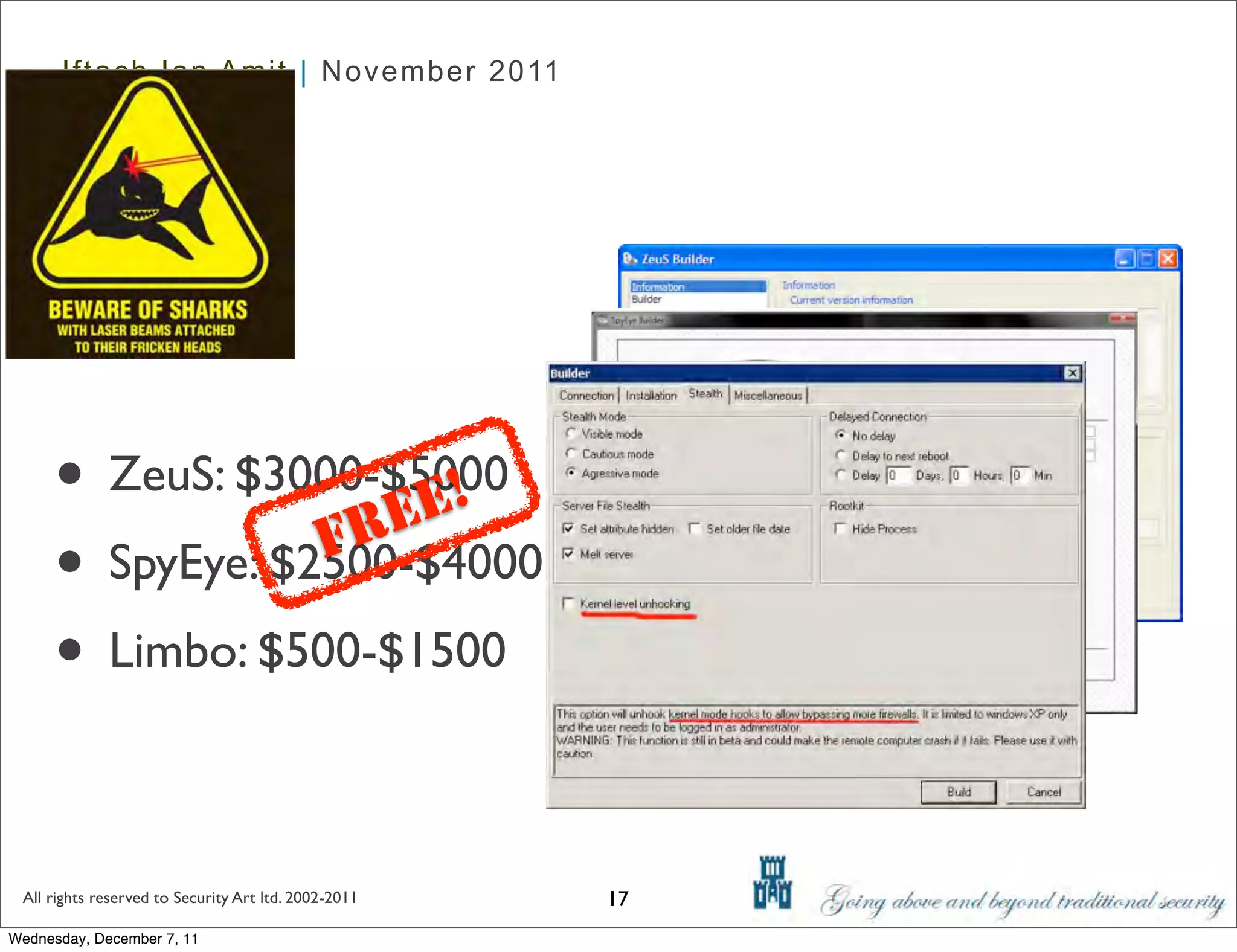
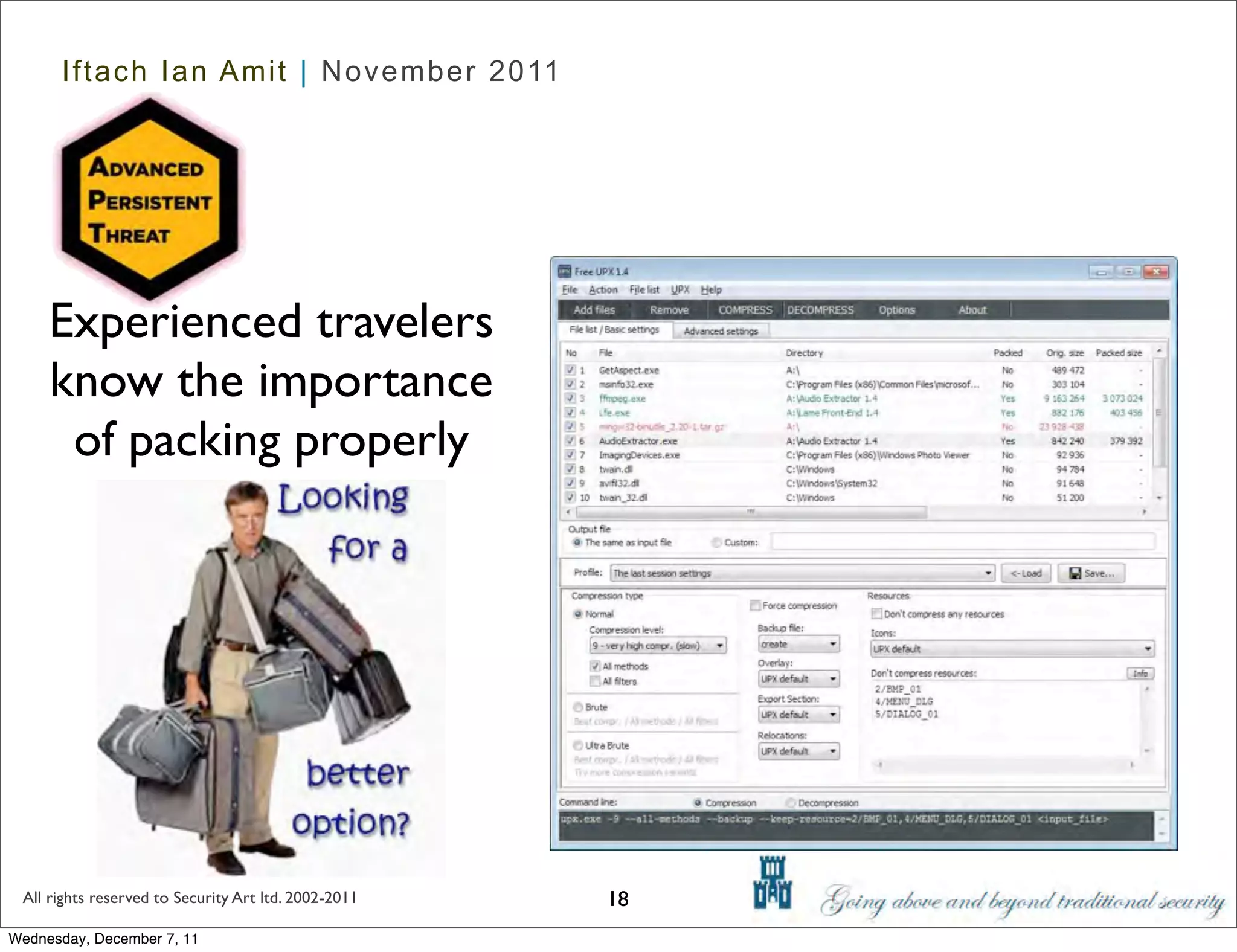
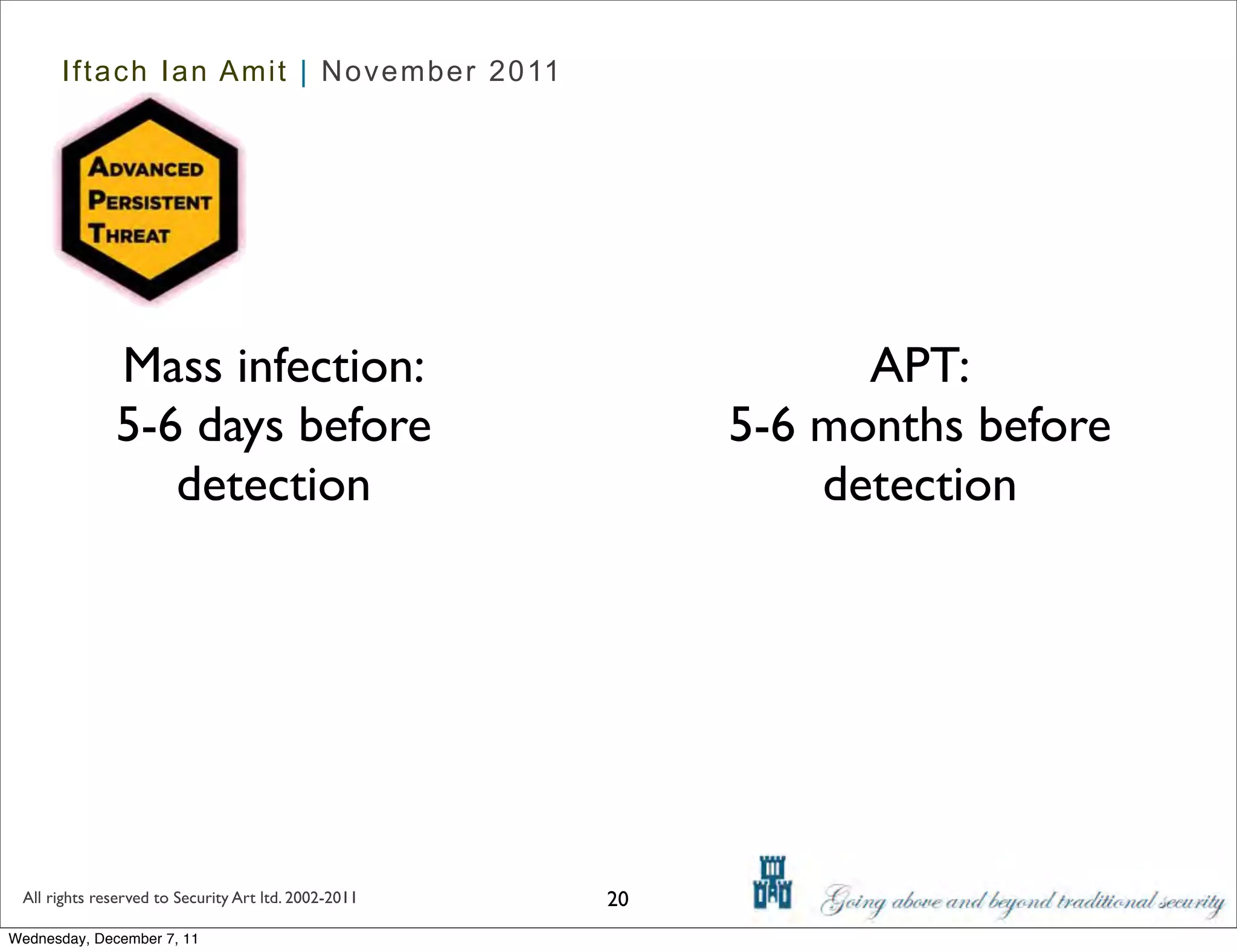
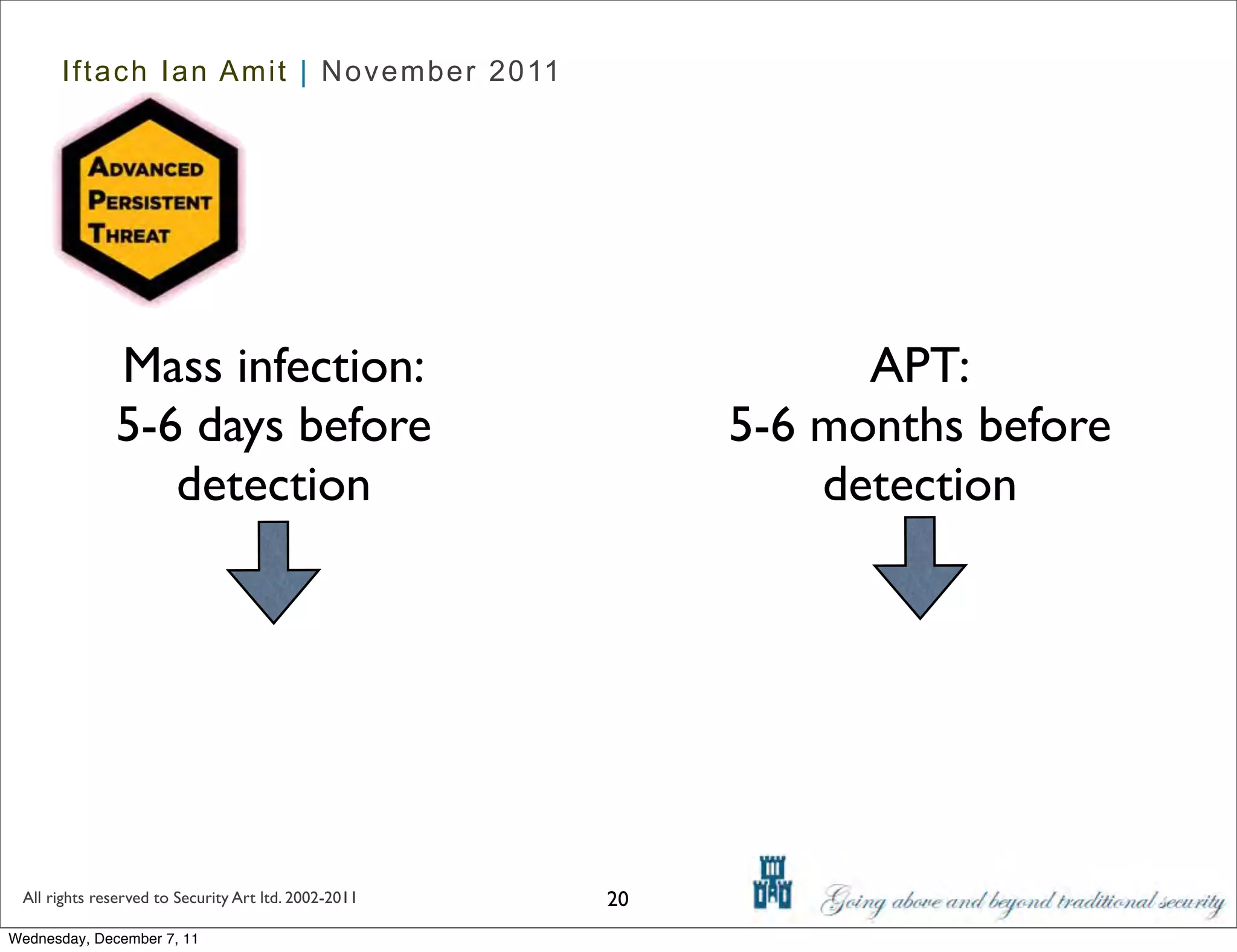
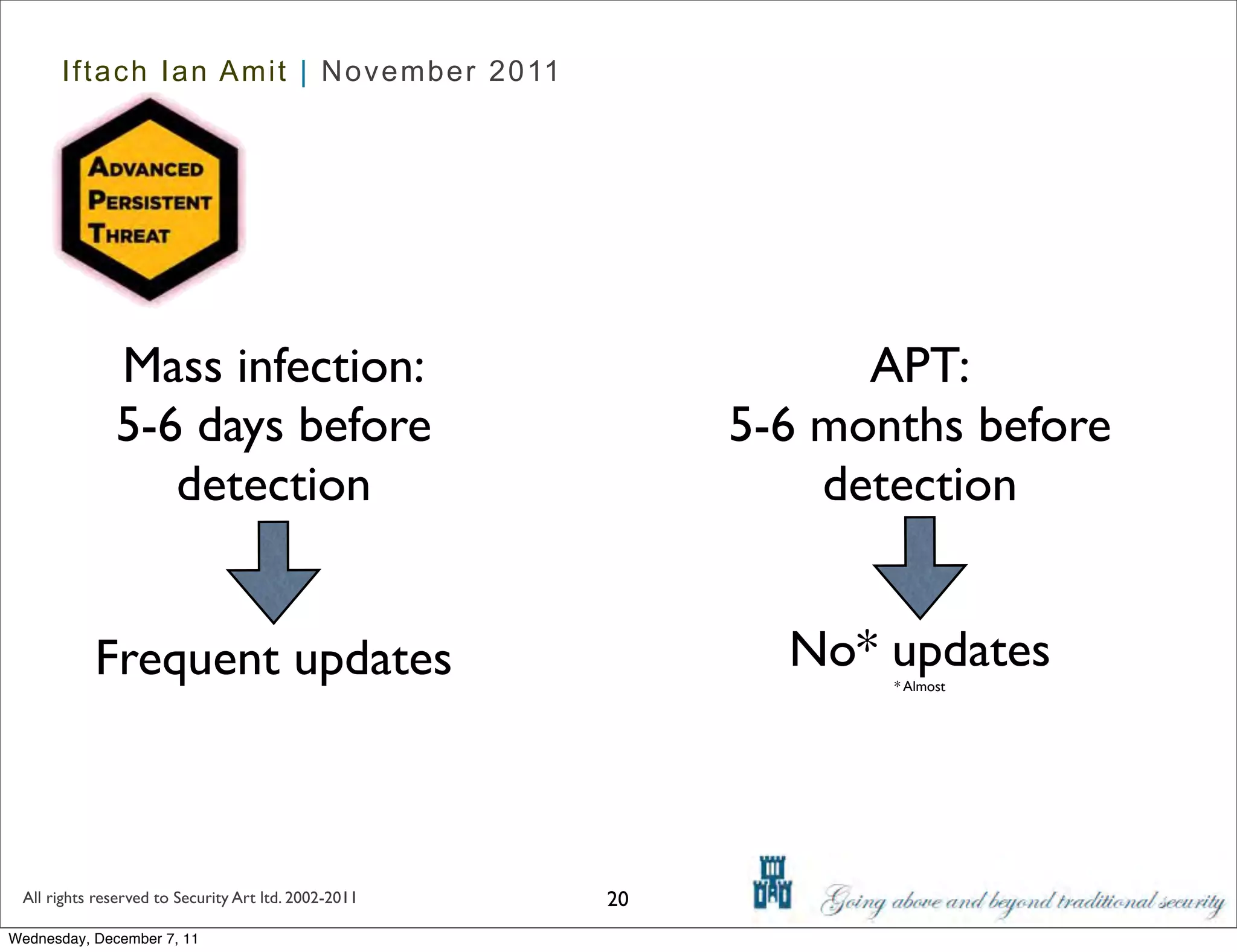
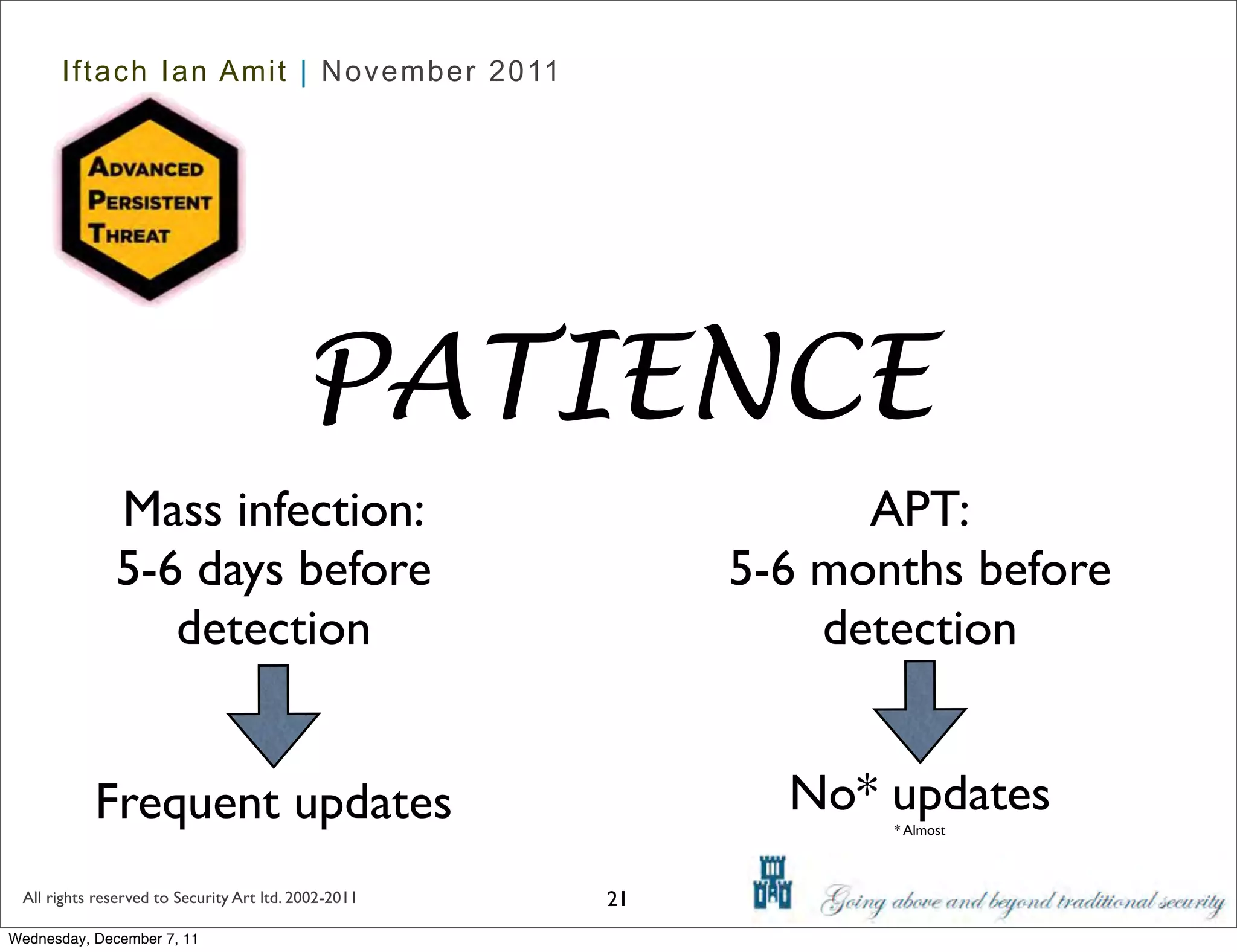
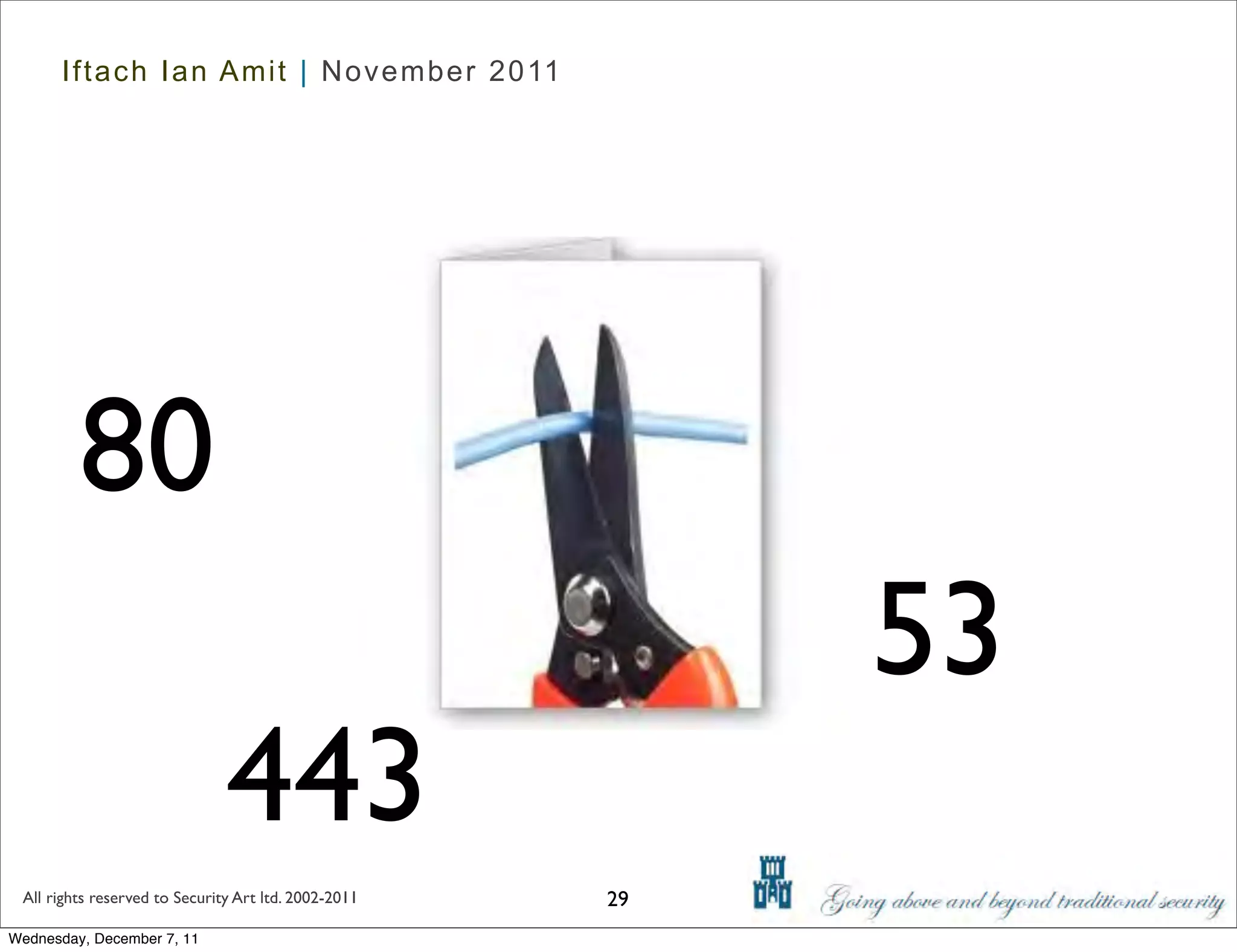
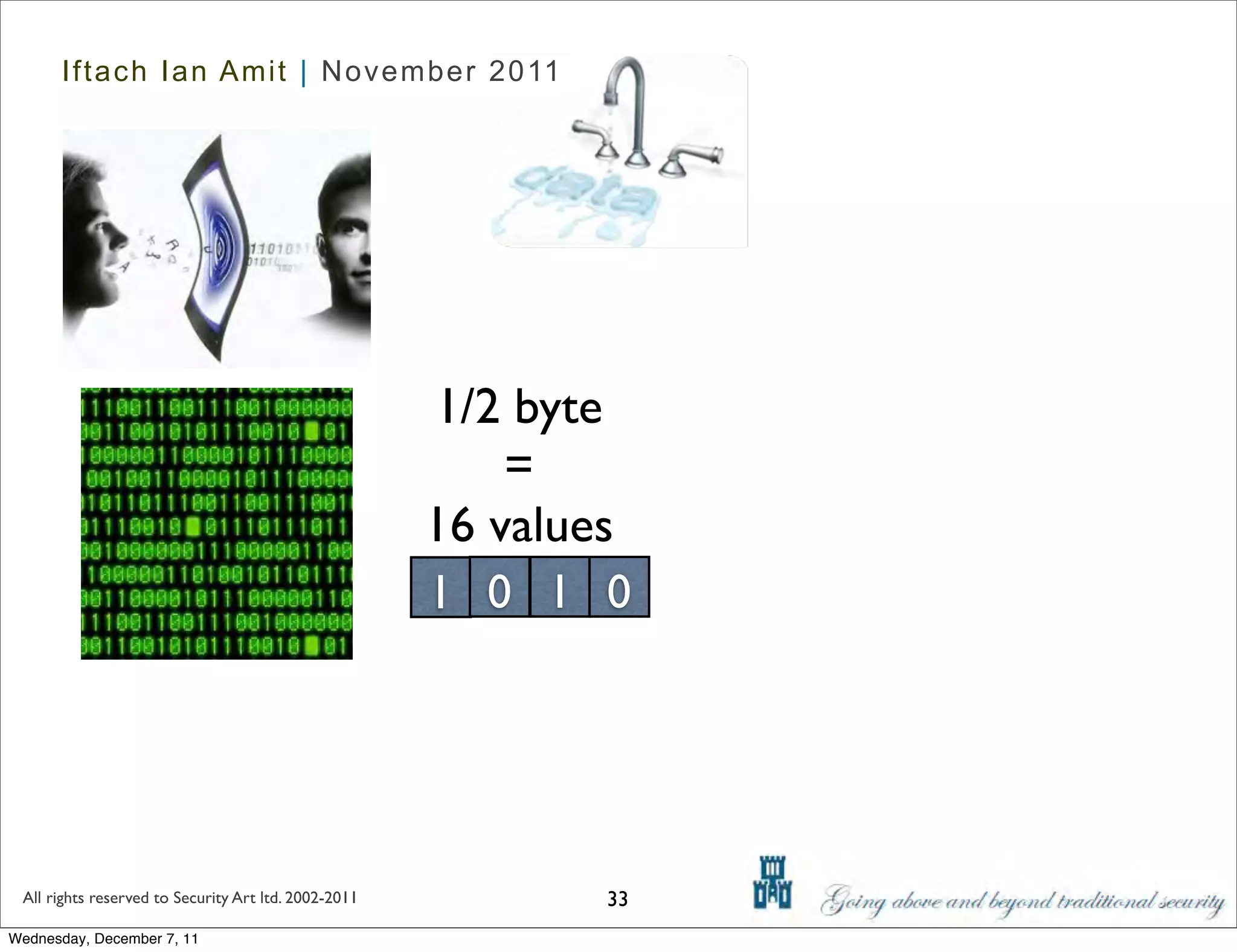
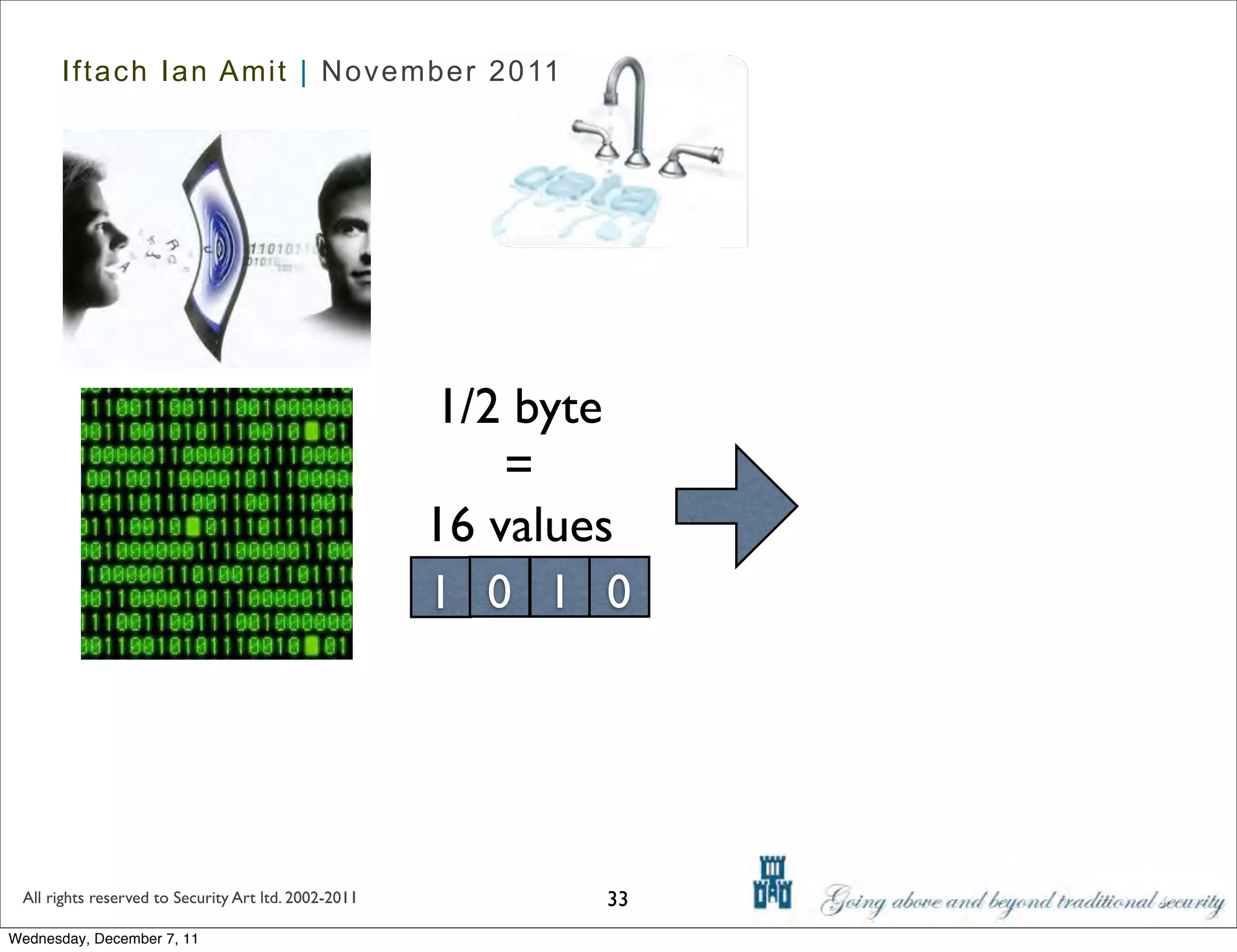
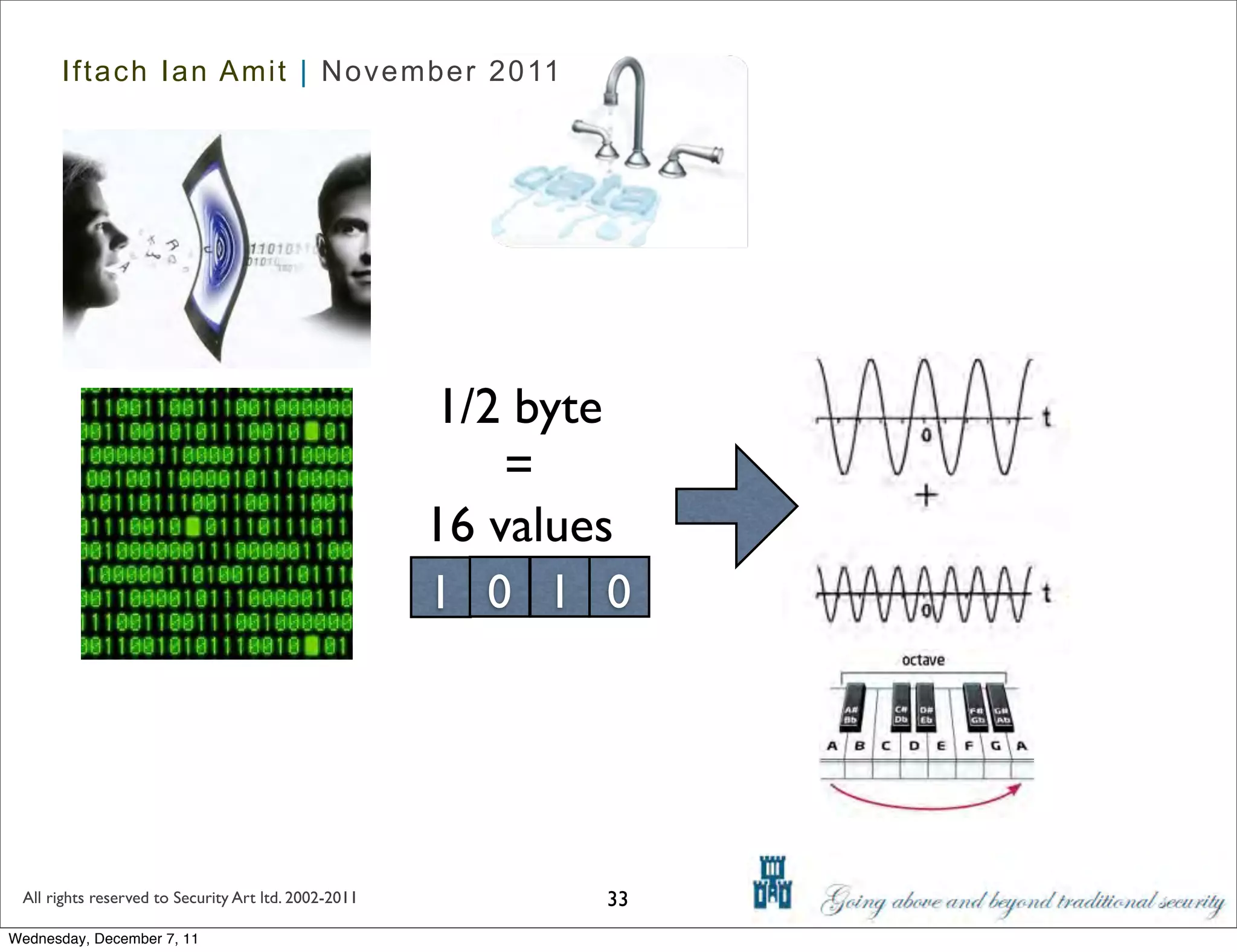
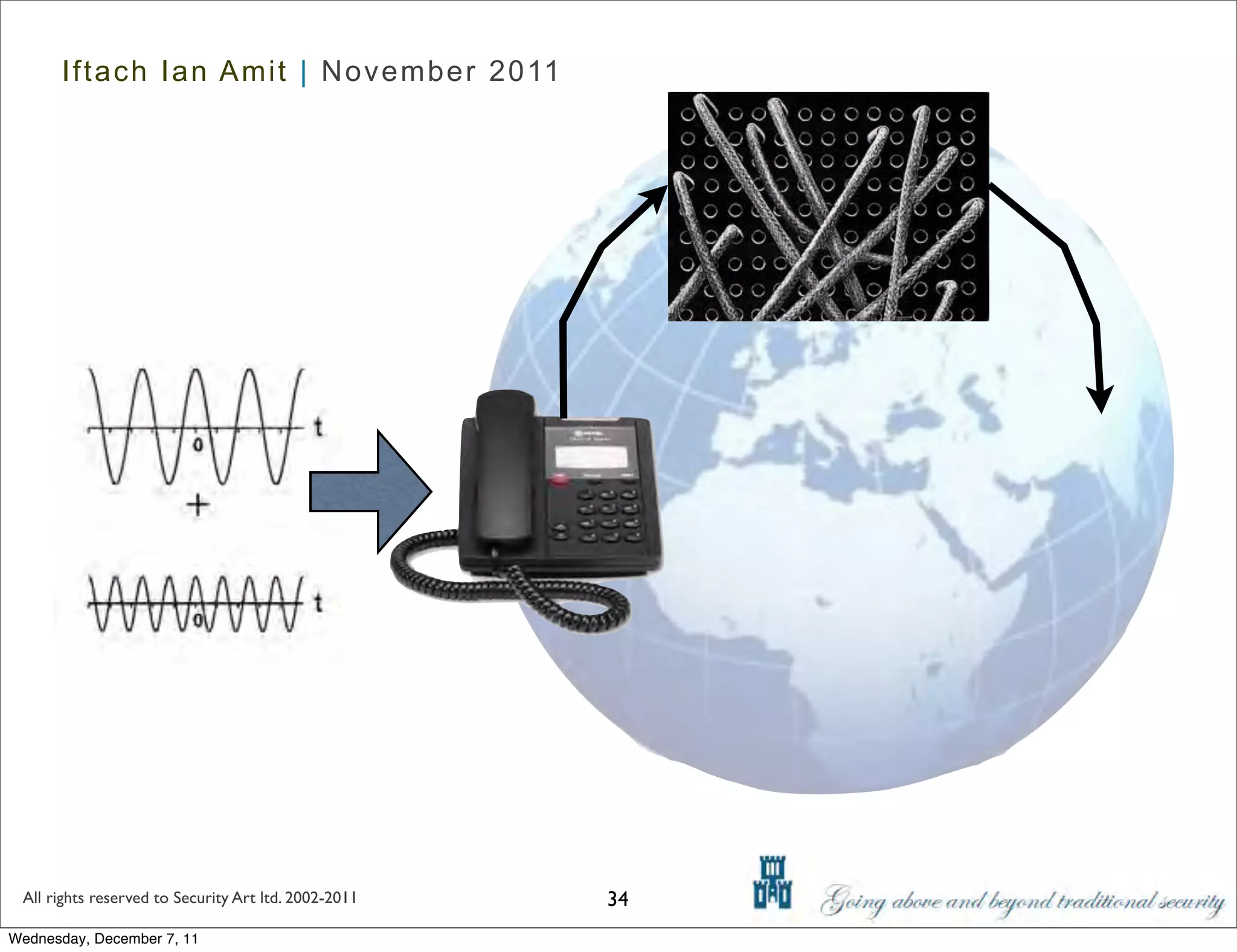
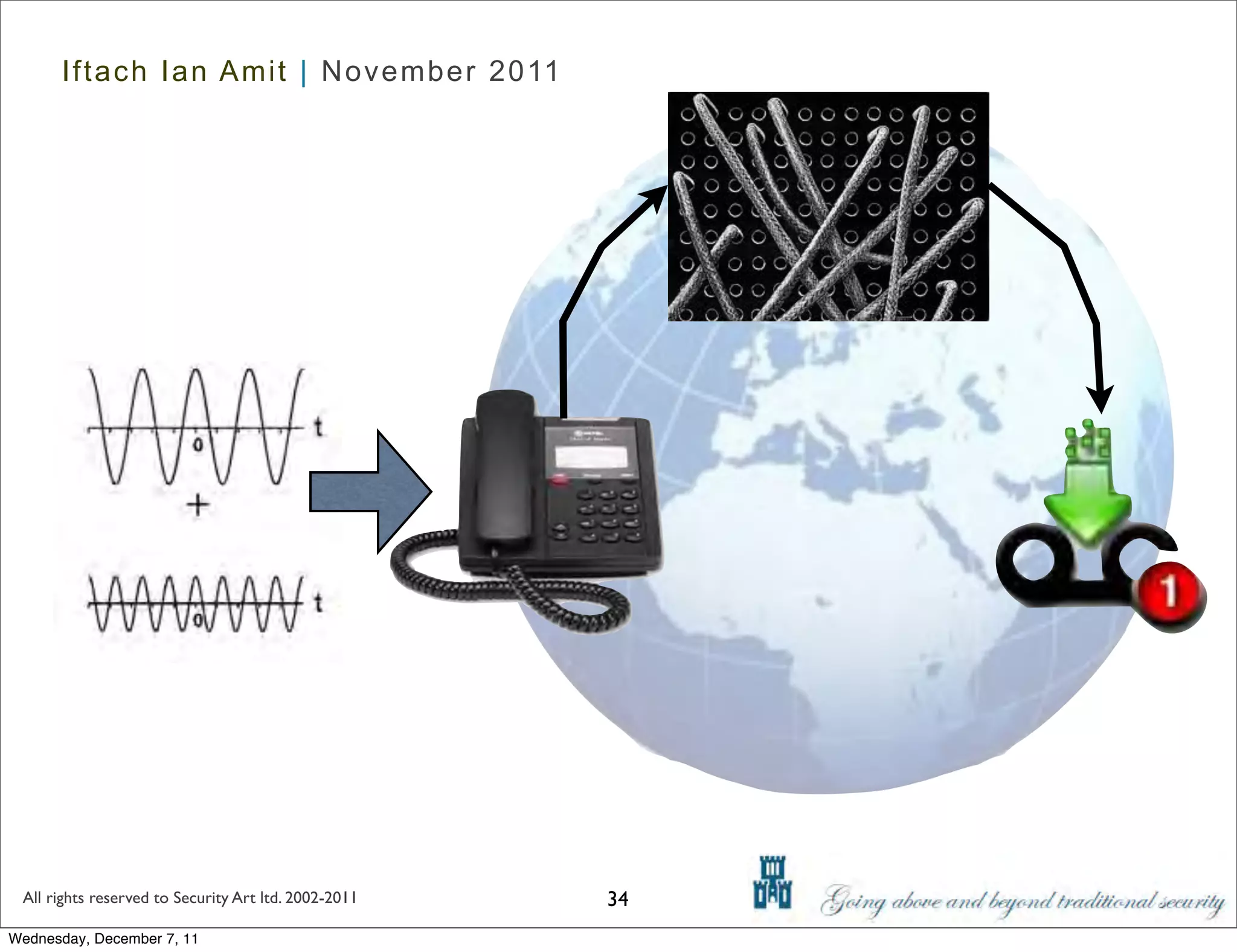
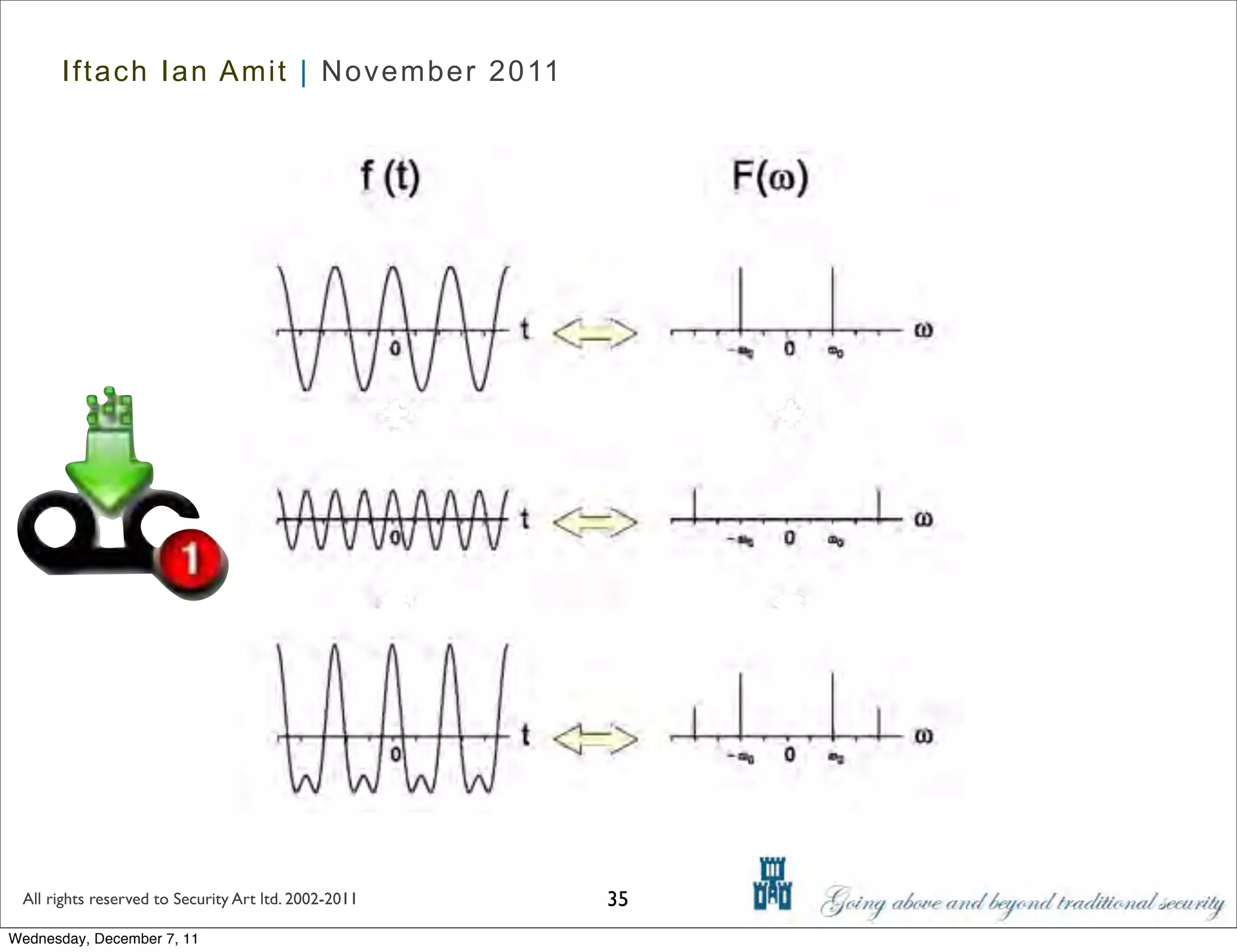
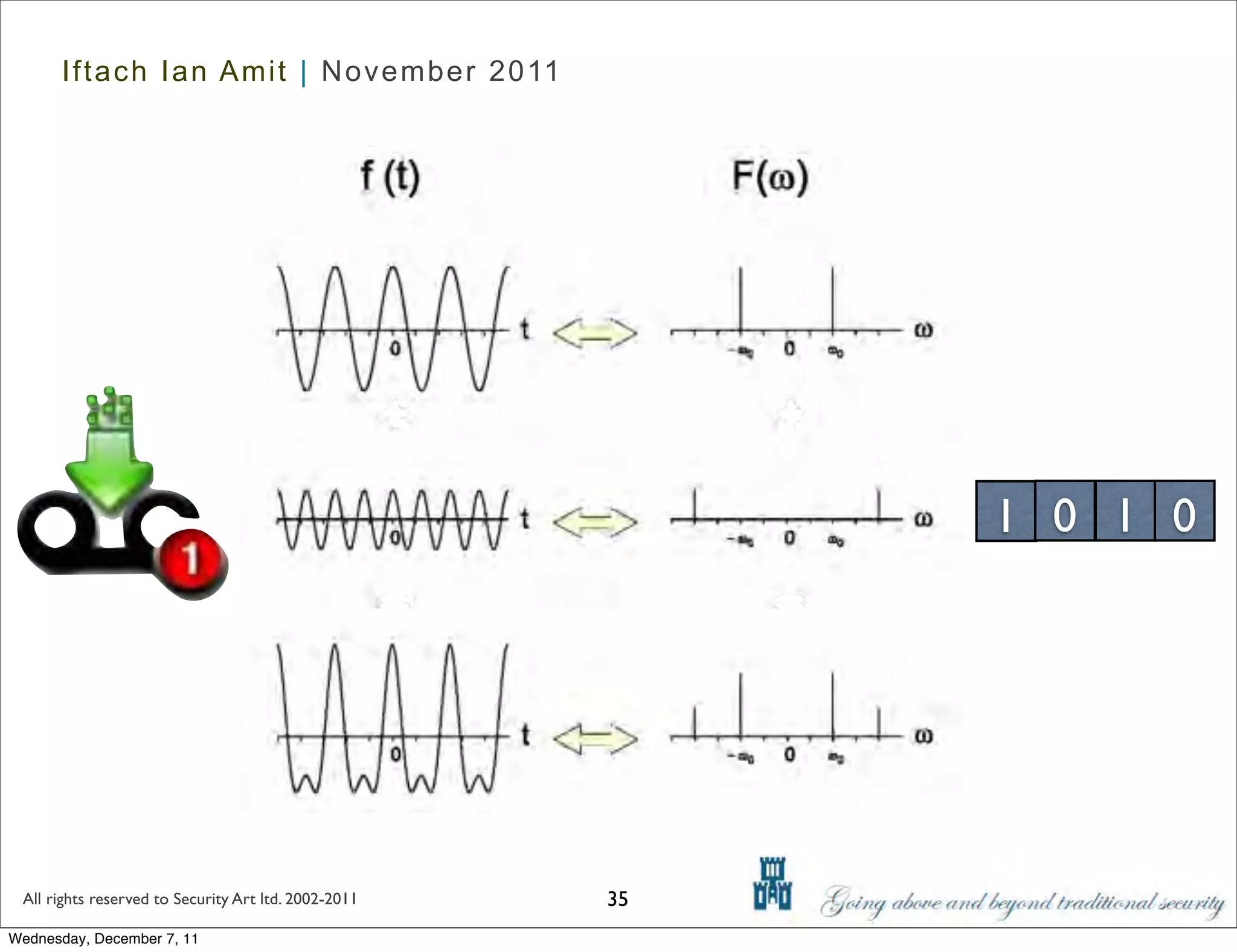
The document discusses advanced data exfiltration techniques, highlighting various methods such as emails, web links, and phishing. It emphasizes the importance of choosing targets wisely and understanding the target's willingness to share information. Additionally, it mentions different malware options with associated costs and the timeline for mass infection detection.