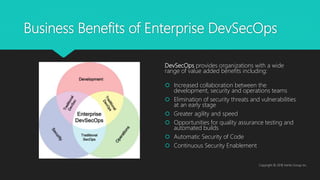
The document discusses the importance of transitioning from DevOps to DevSecOps by integrating security into the development lifecycle to enhance software security and reduce vulnerabilities. Key components include continuous monitoring, assessment of security measures, analysis of code vulnerabilities, and fostering collaboration between development and security teams. Adopting a DevSecOps strategy not only mitigates risks but also accelerates time to market and improves overall operational efficiency.