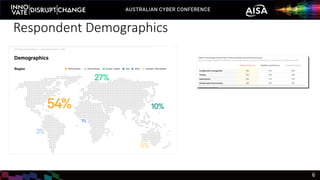
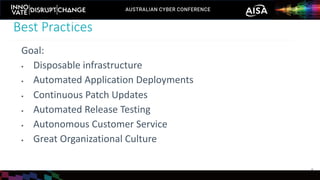
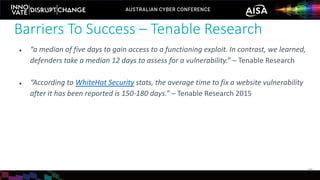
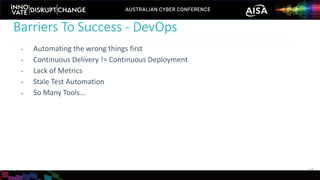
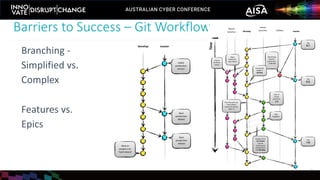
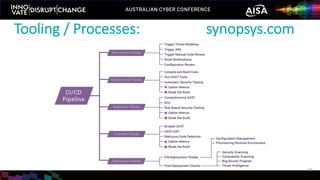
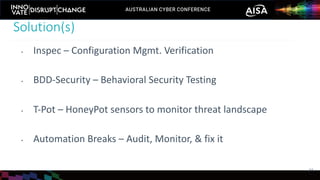
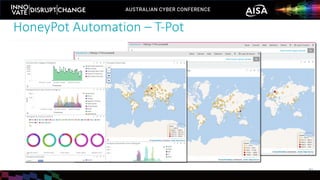
The document outlines the rise of SecDevOps, emphasizing its role in enhancing security and operational practices in software development. It presents research findings on the benefits and performance improvements related to the adoption of SecDevOps methodologies while also highlighting barriers to success in terms of vulnerability remediation and organizational challenges. Best practices and tooling solutions are recommended to foster a proactive security culture and streamline processes.