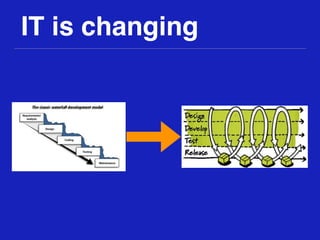
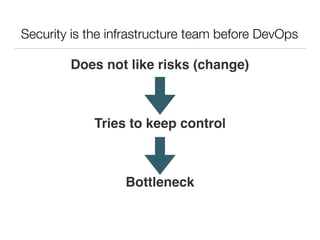
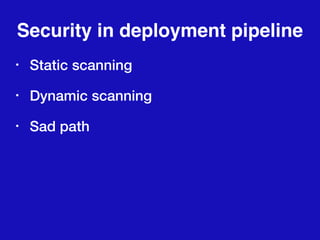
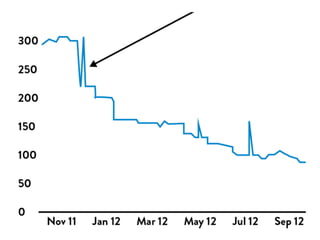
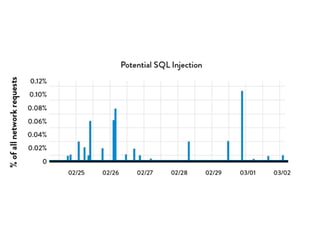
This document discusses integrating DevOps and security by bringing development, operations, QA, and security teams together. It outlines where security currently stands, emphasizing the need to change from a "rugged" security model that acts as a bottleneck. The document proposes tactics to scale security through empathy, automation, and feedback loops. Specific tactics include integrating security into defect tracking, preventative controls, deployment pipelines, monitoring, and emphasizing that security says "we could do it this way" rather than only saying no. The overall goal is to improve security while making work easier.