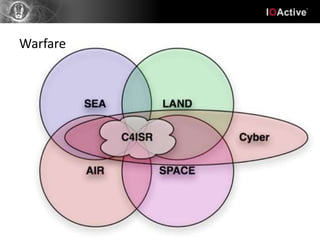
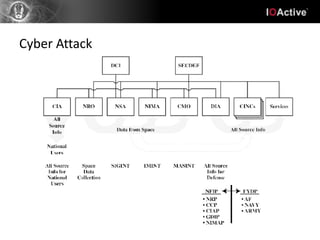
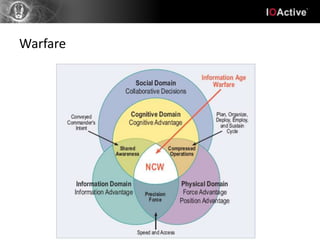
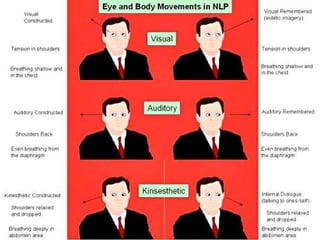
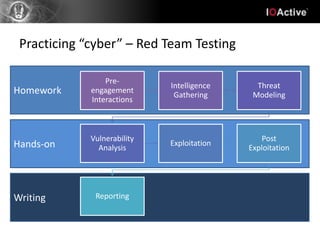
Hacking involves a single target and shallow attacks using common tools and techniques, motivated by financial or political goals. Cyber attacks are part of cyber warfare involving strategic targets across physical, social, intelligence and electronic domains using custom tools in a coordinated campaign. Cyber defenses require a strategic defense in depth approach across all domains with awareness training, unlike typical IT security products. Hacking is an individual battle while cyber attacks are part of a larger warfare strategy.