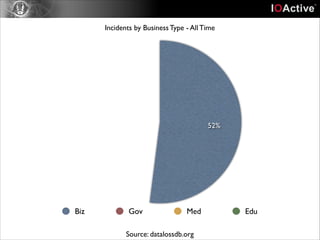
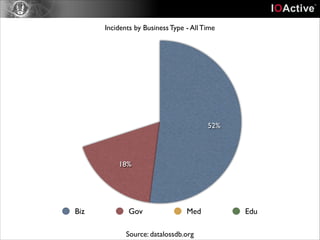
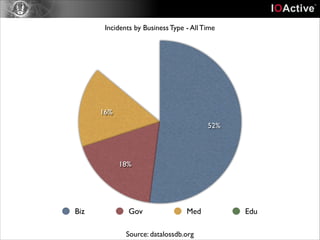
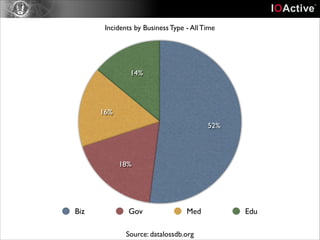
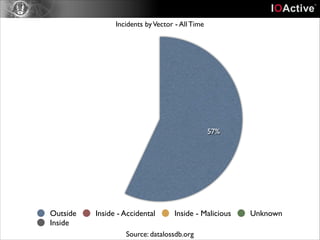
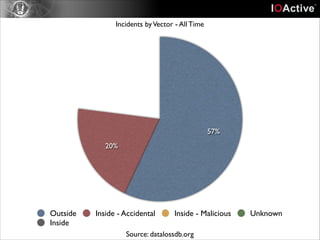
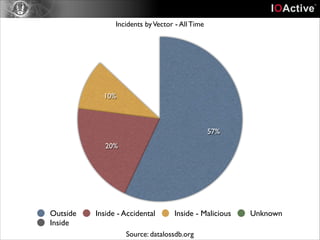
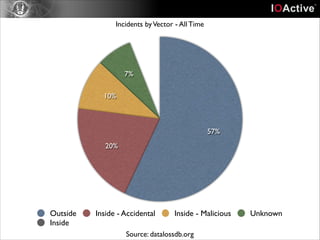
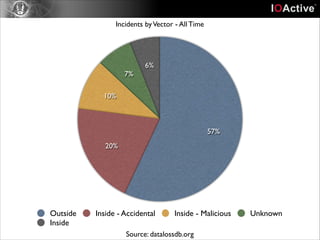
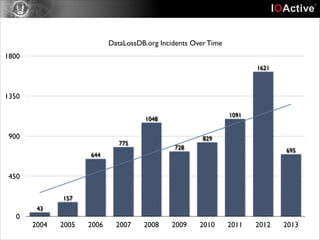
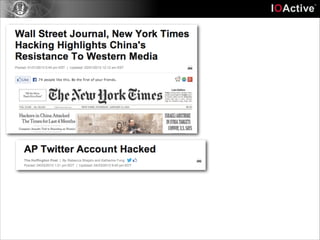
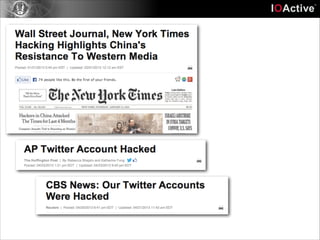
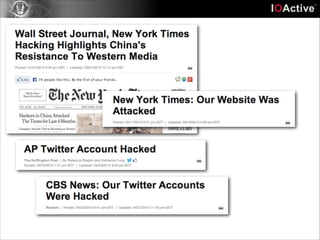
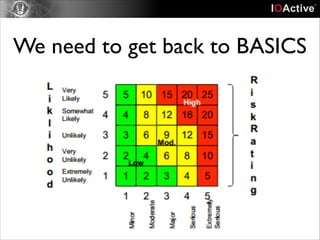
This document discusses cyber security risks and incidents over time. It notes that 52% of all incidents are from businesses, with government, medical, and education each accounting for around 15-20% of incidents. The majority (57%) of incidents are caused by outside actors, while 20% are from insider threats and 10% are accidental insider incidents. The number of reported data loss incidents has increased significantly over time from just over 100 in 2004 to over 1600 in 2013. The document advocates returning to basic risk management practices, including prioritizing remediation based on risk, impact, costs, and addressing the most critical gaps in assets, processes, technologies and threats based on priority. It warns against overspending on products and focusing