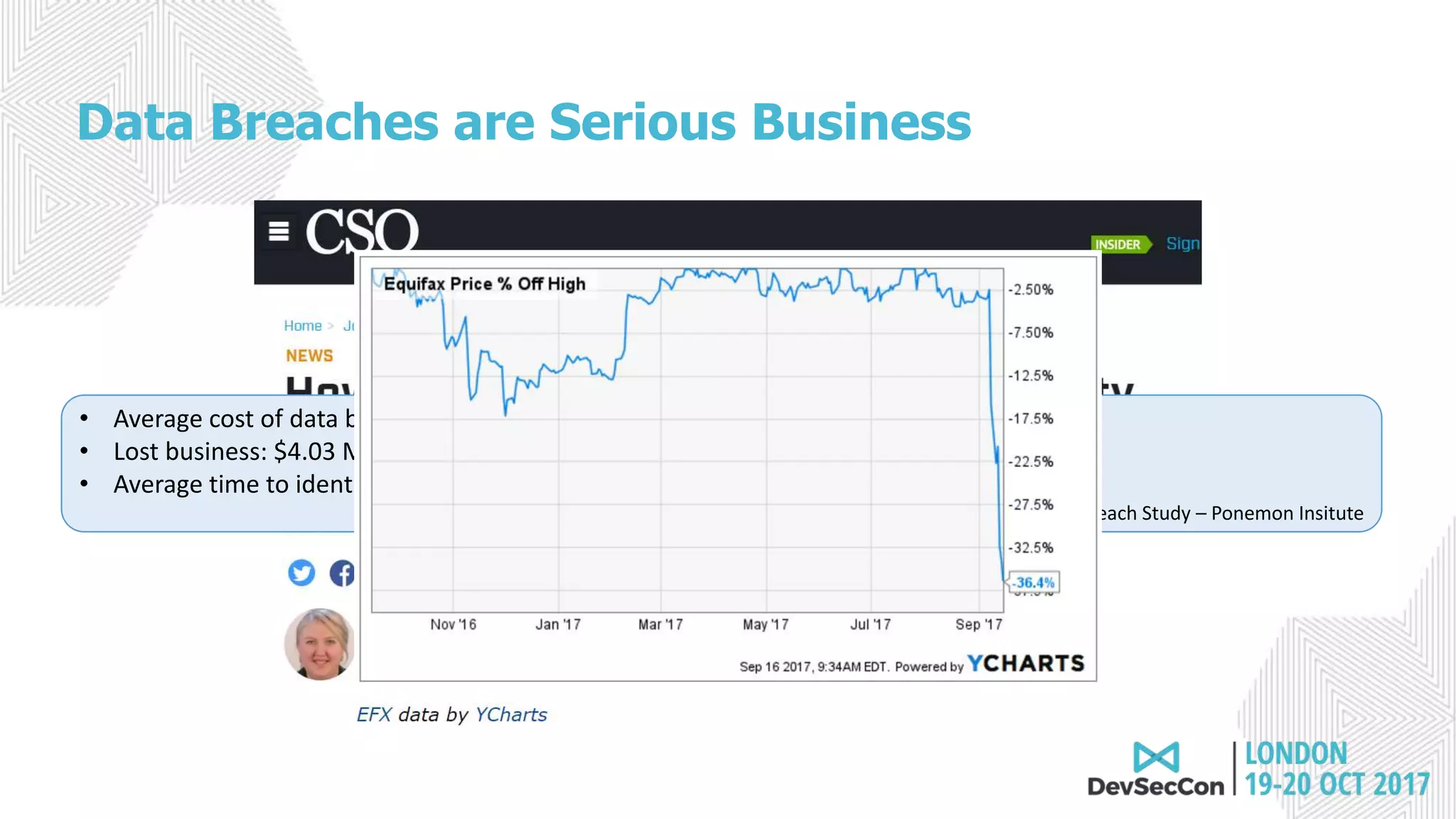
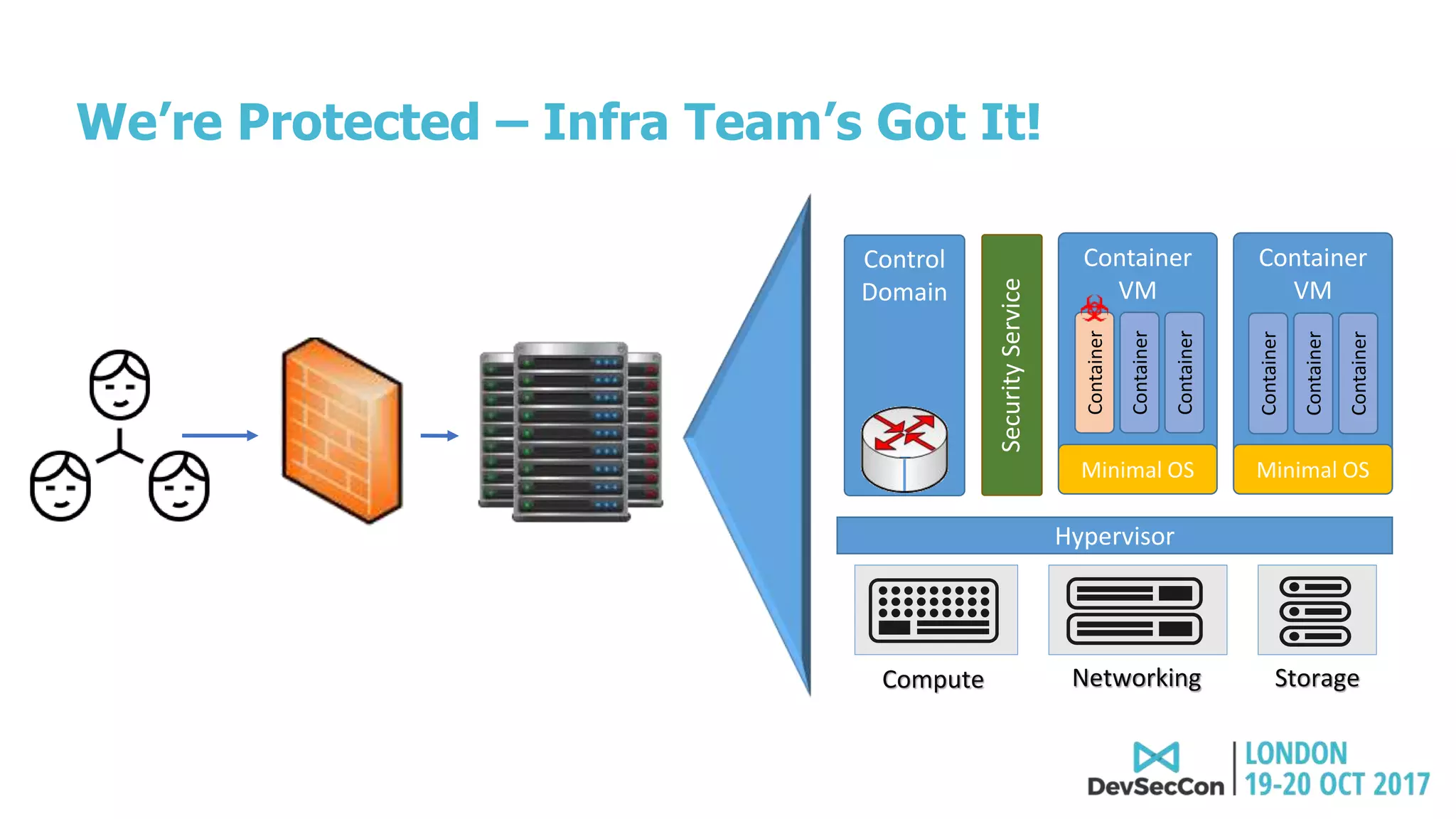
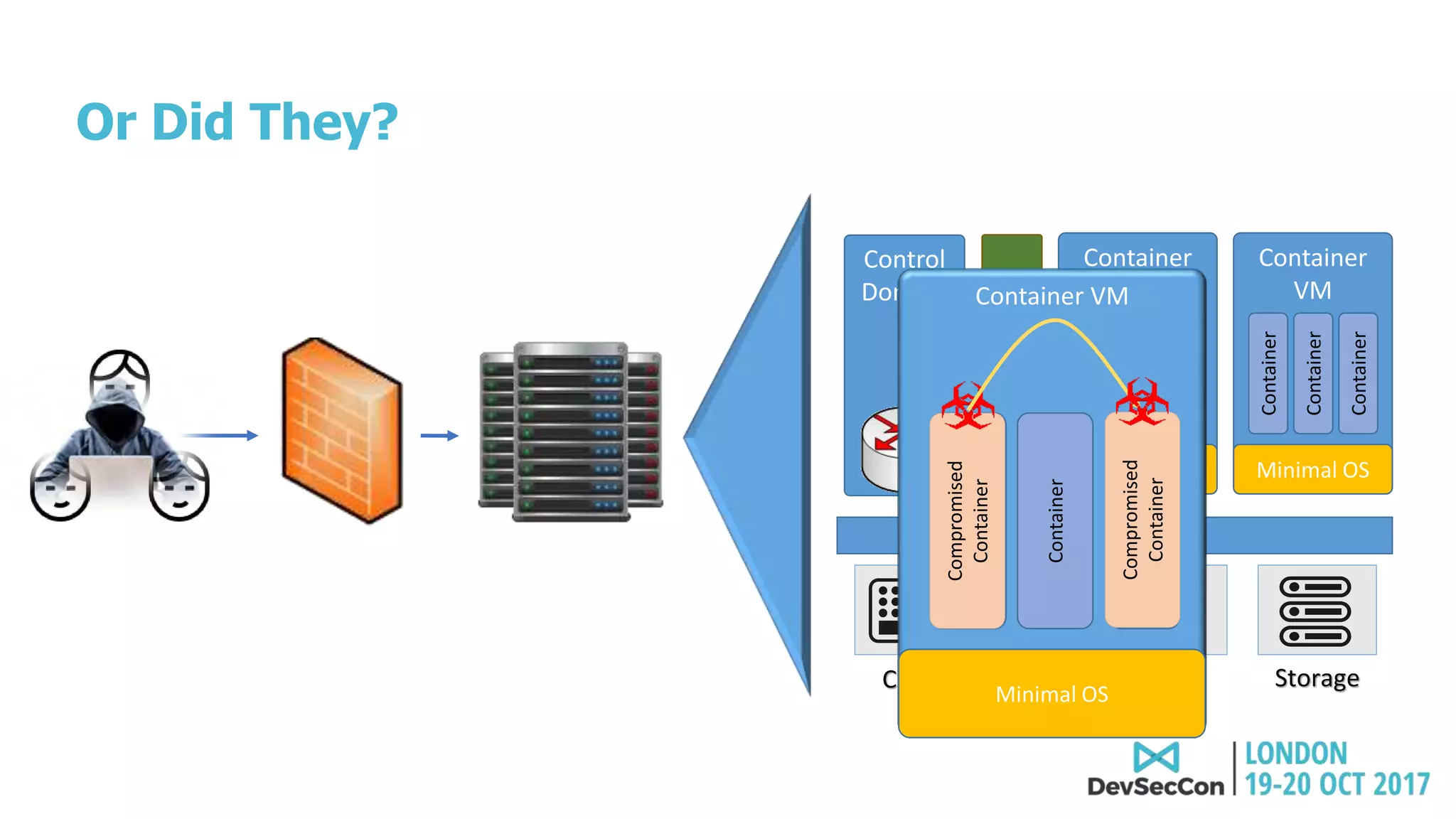
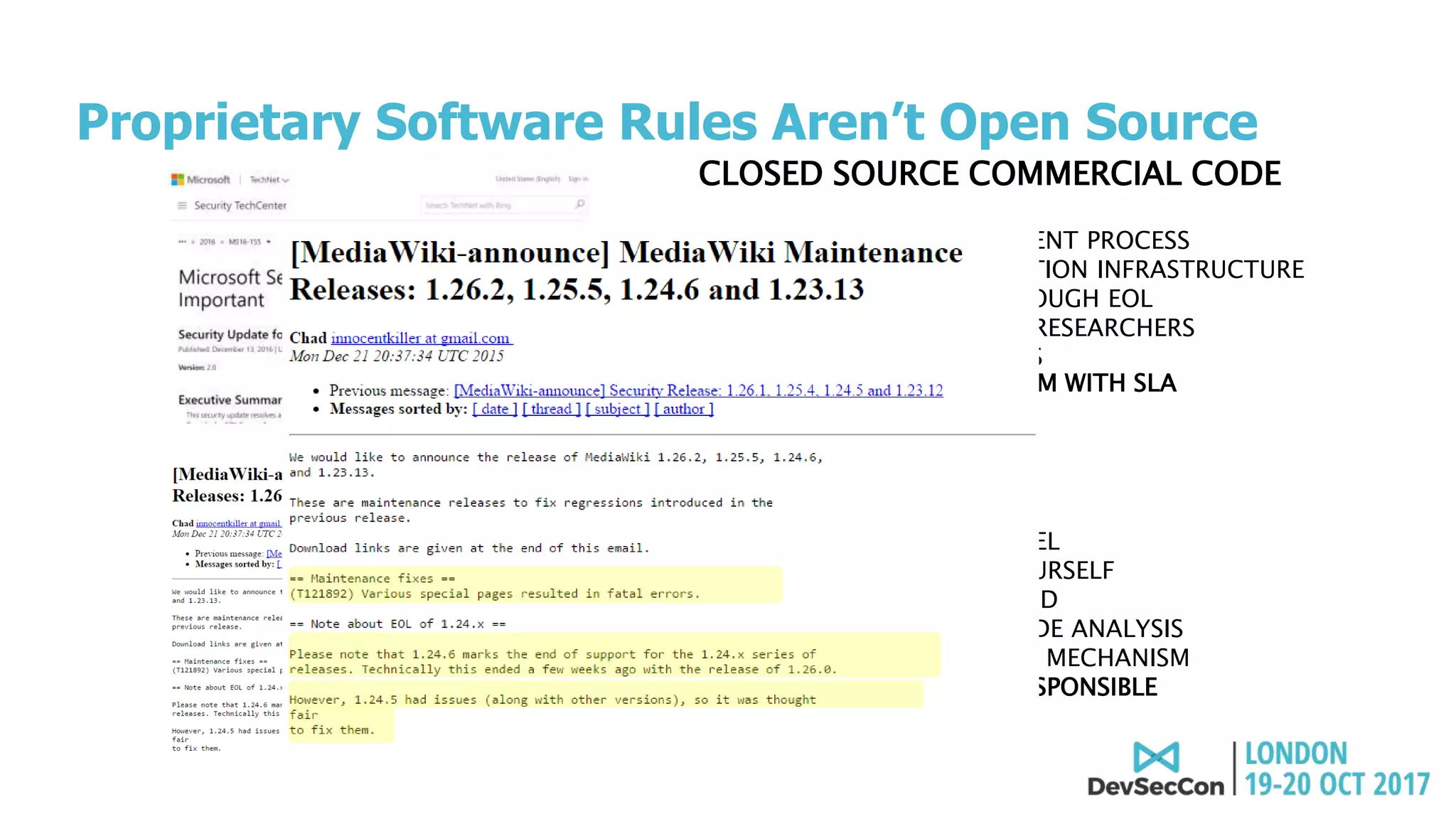
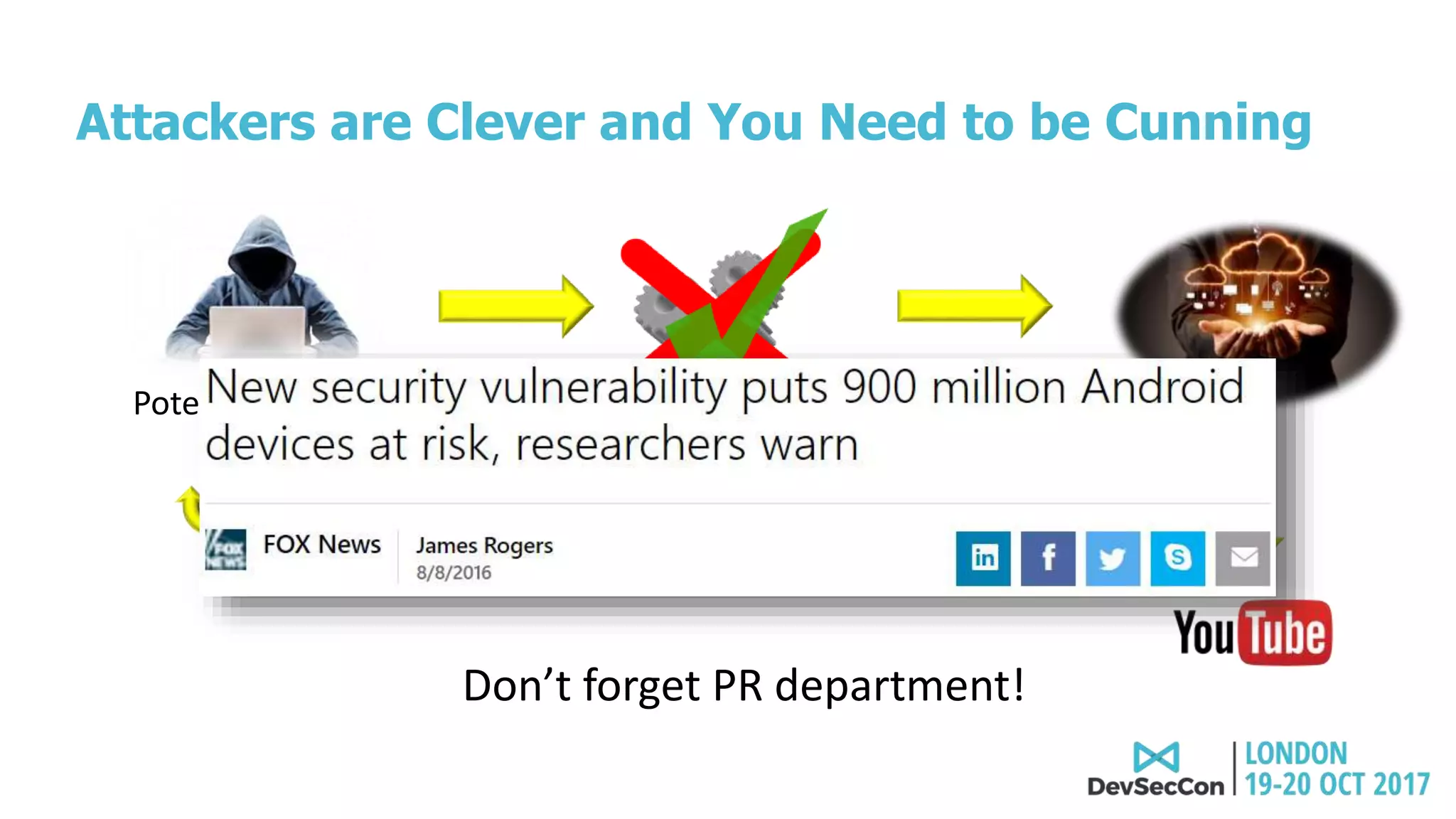
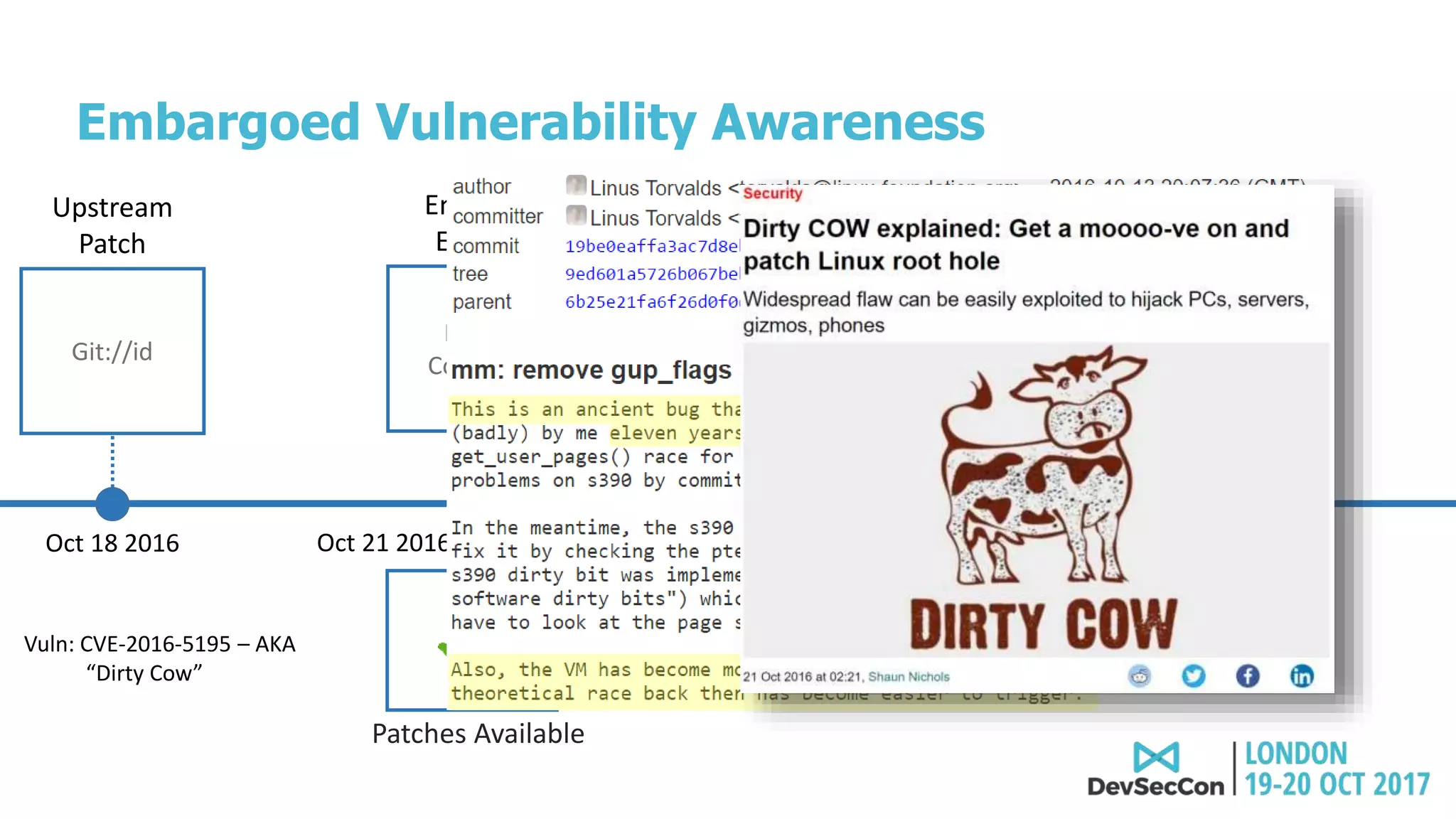
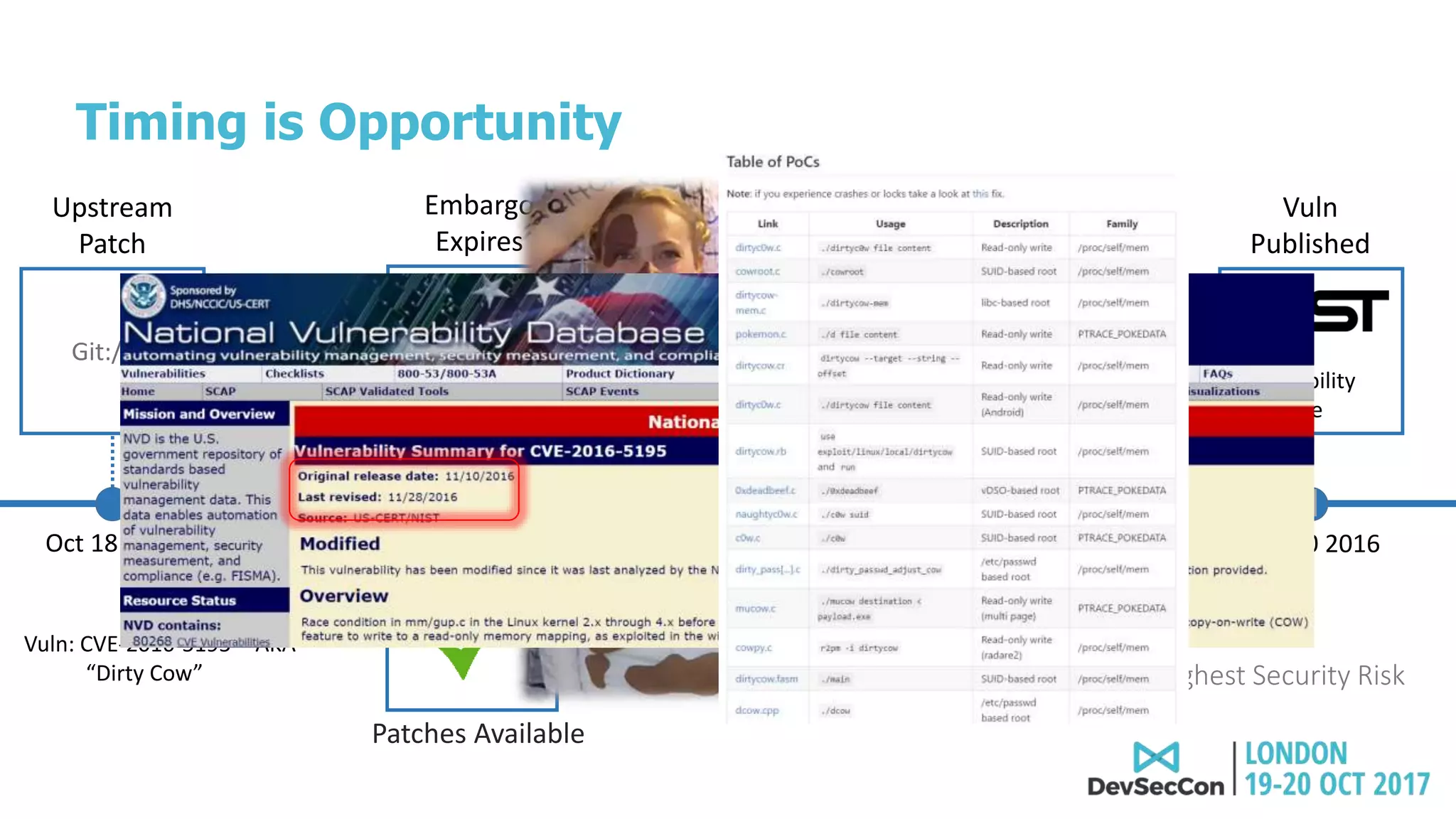
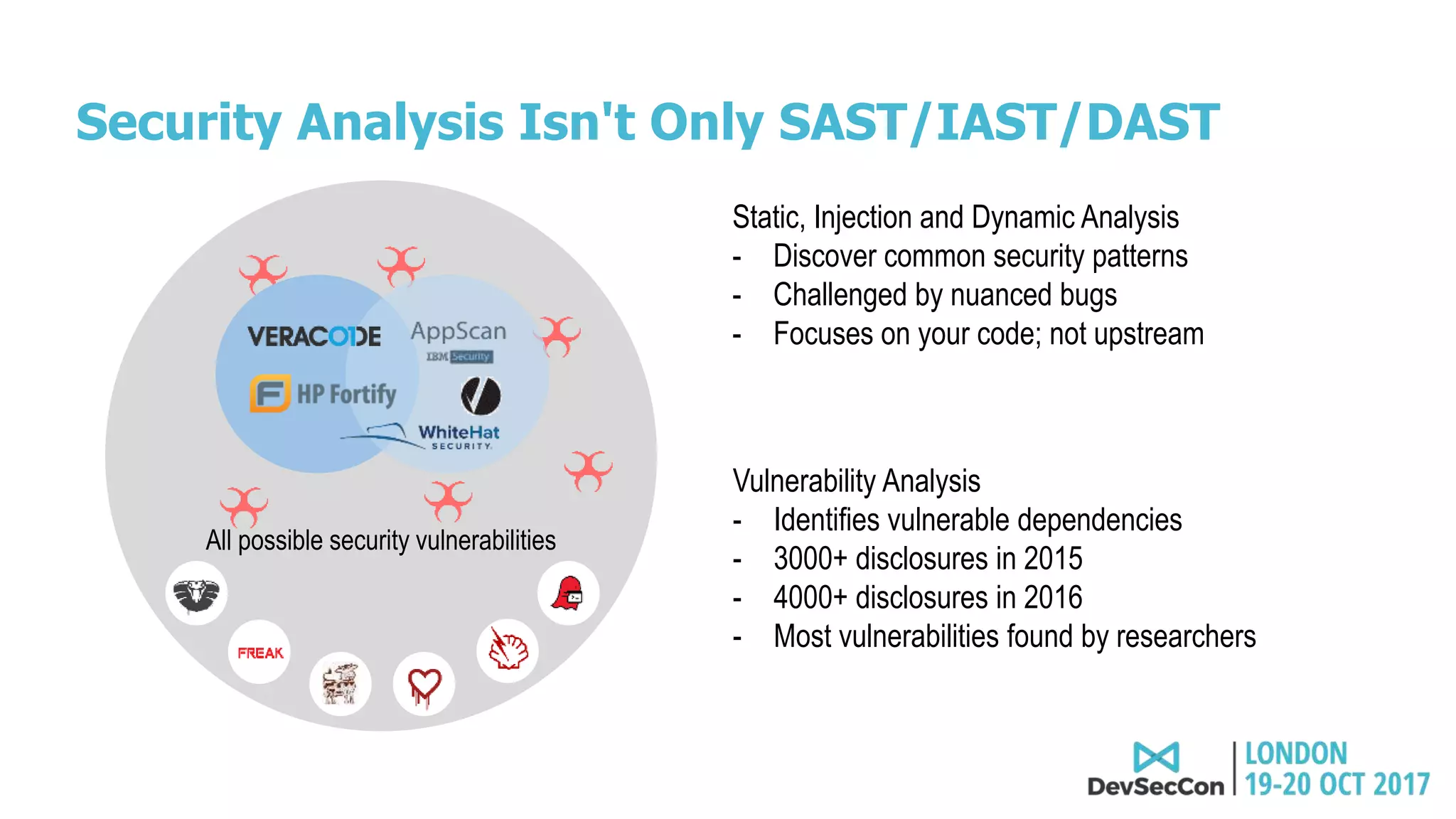
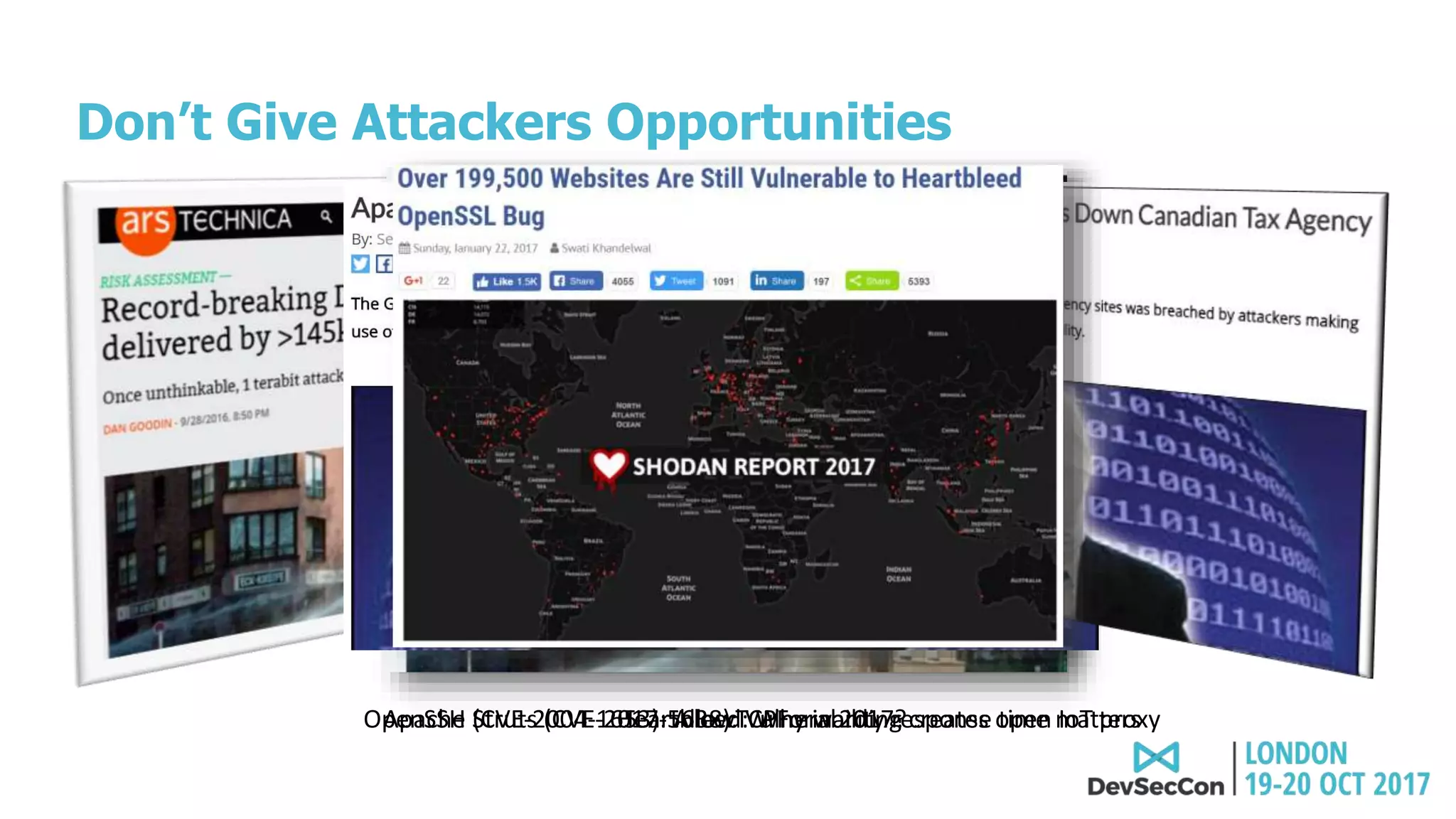
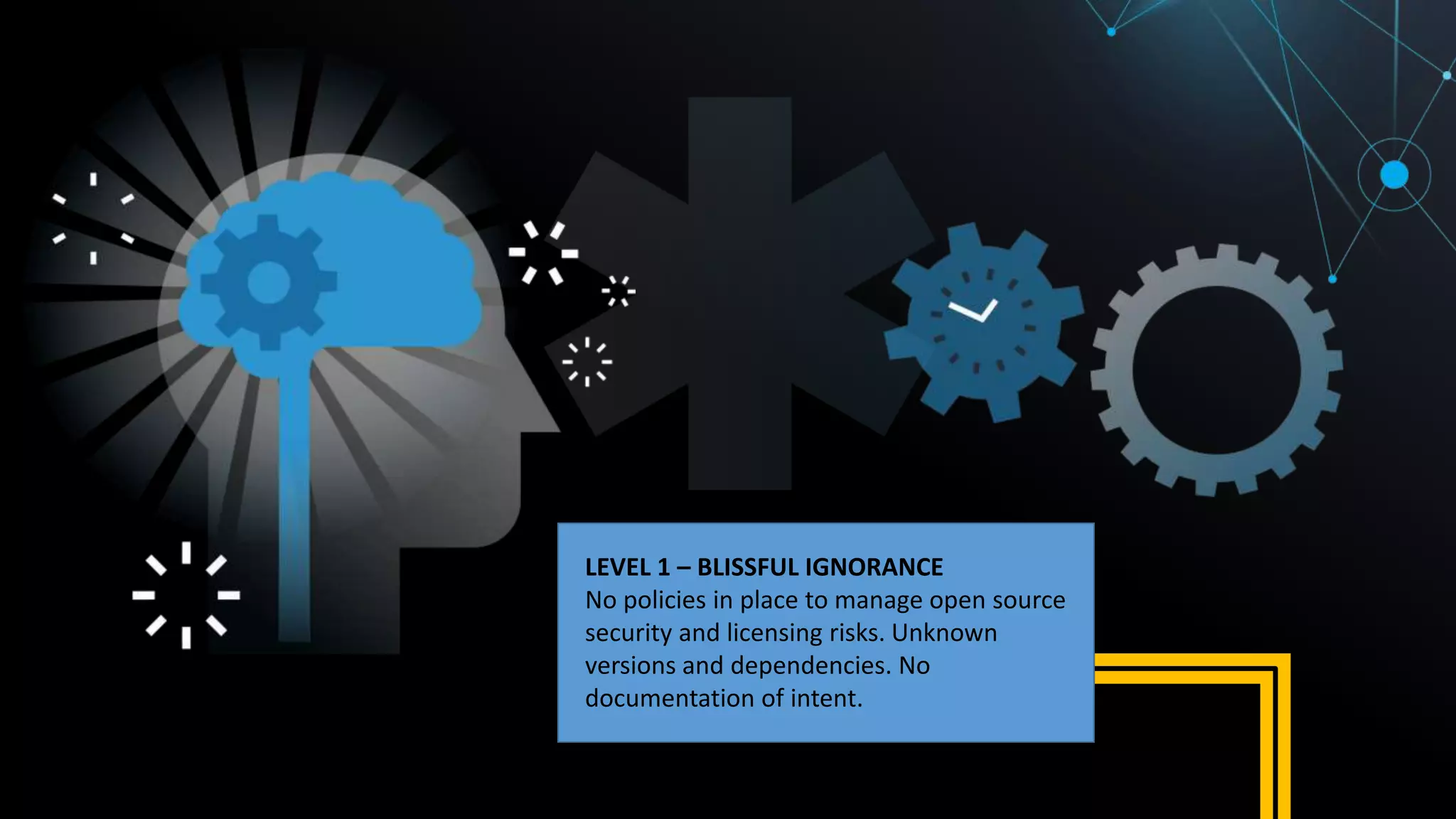
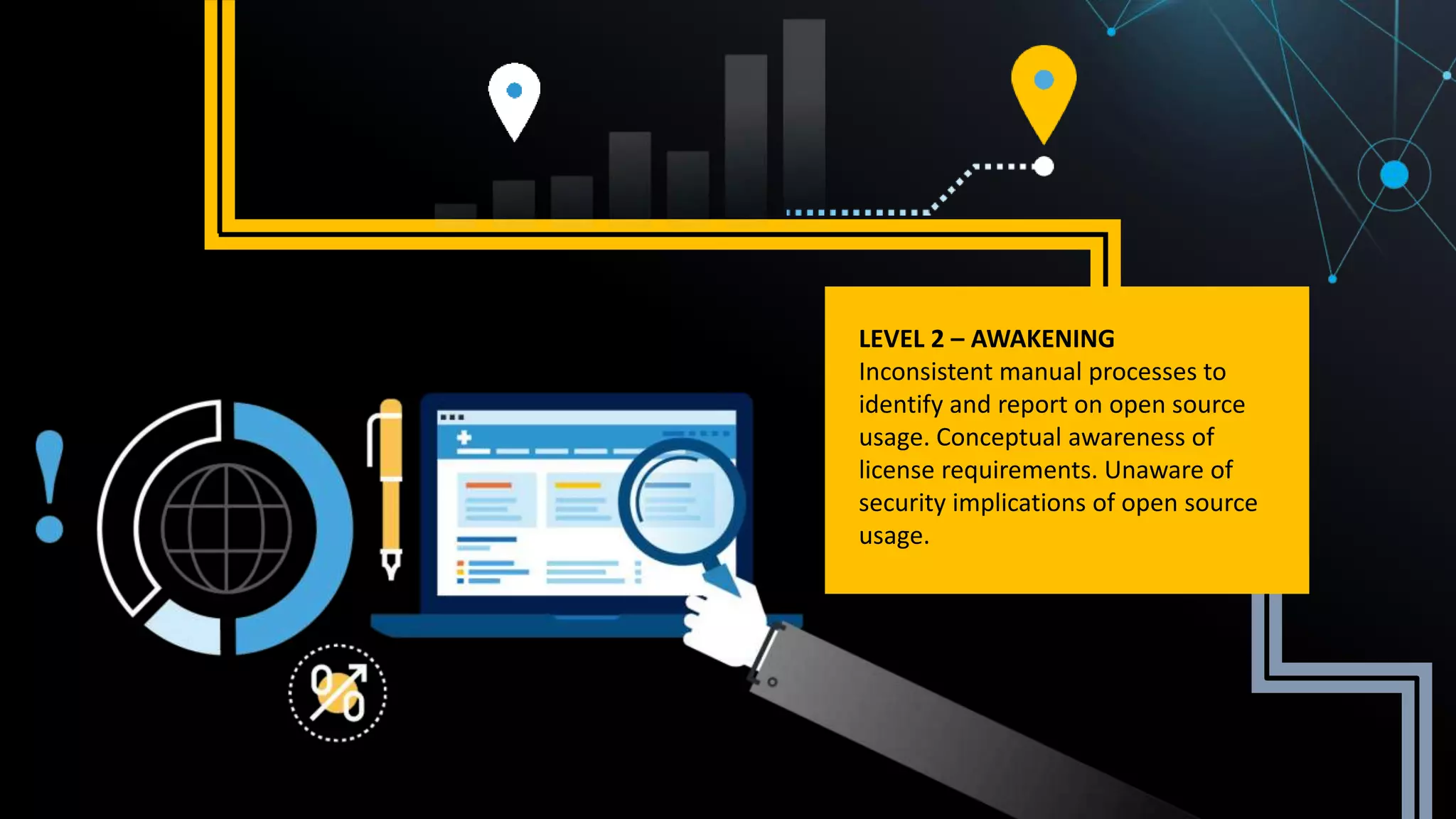
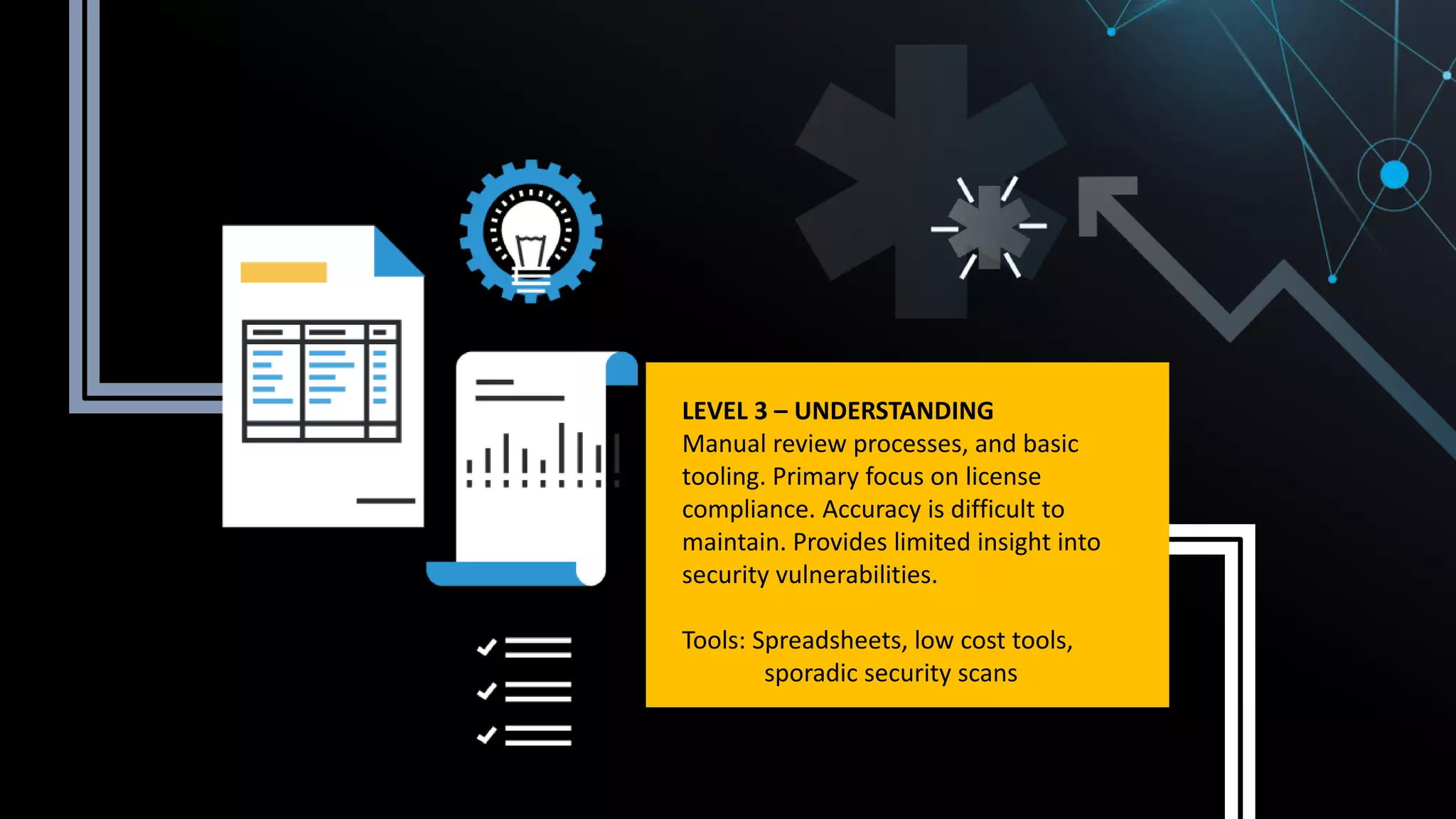
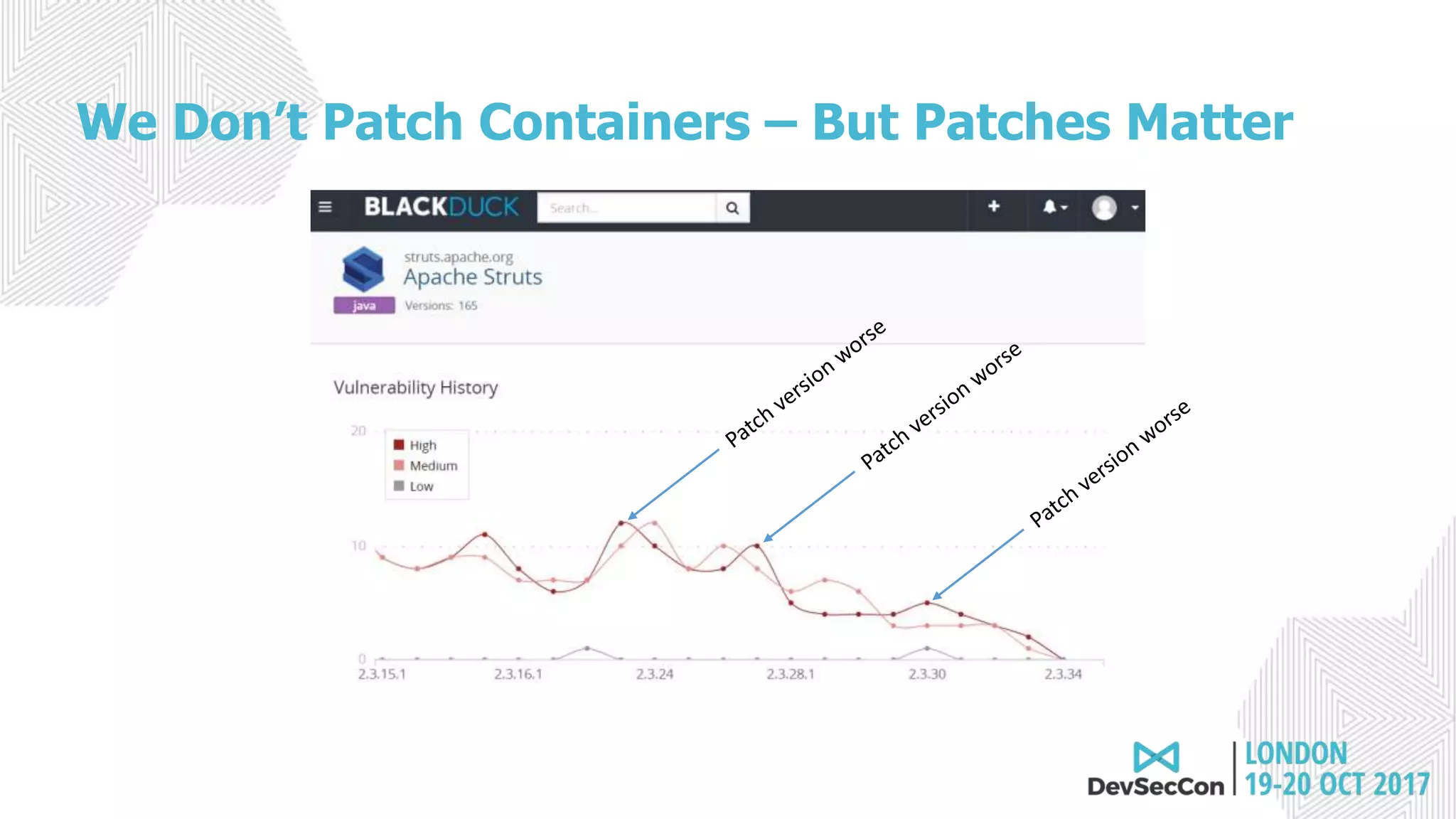
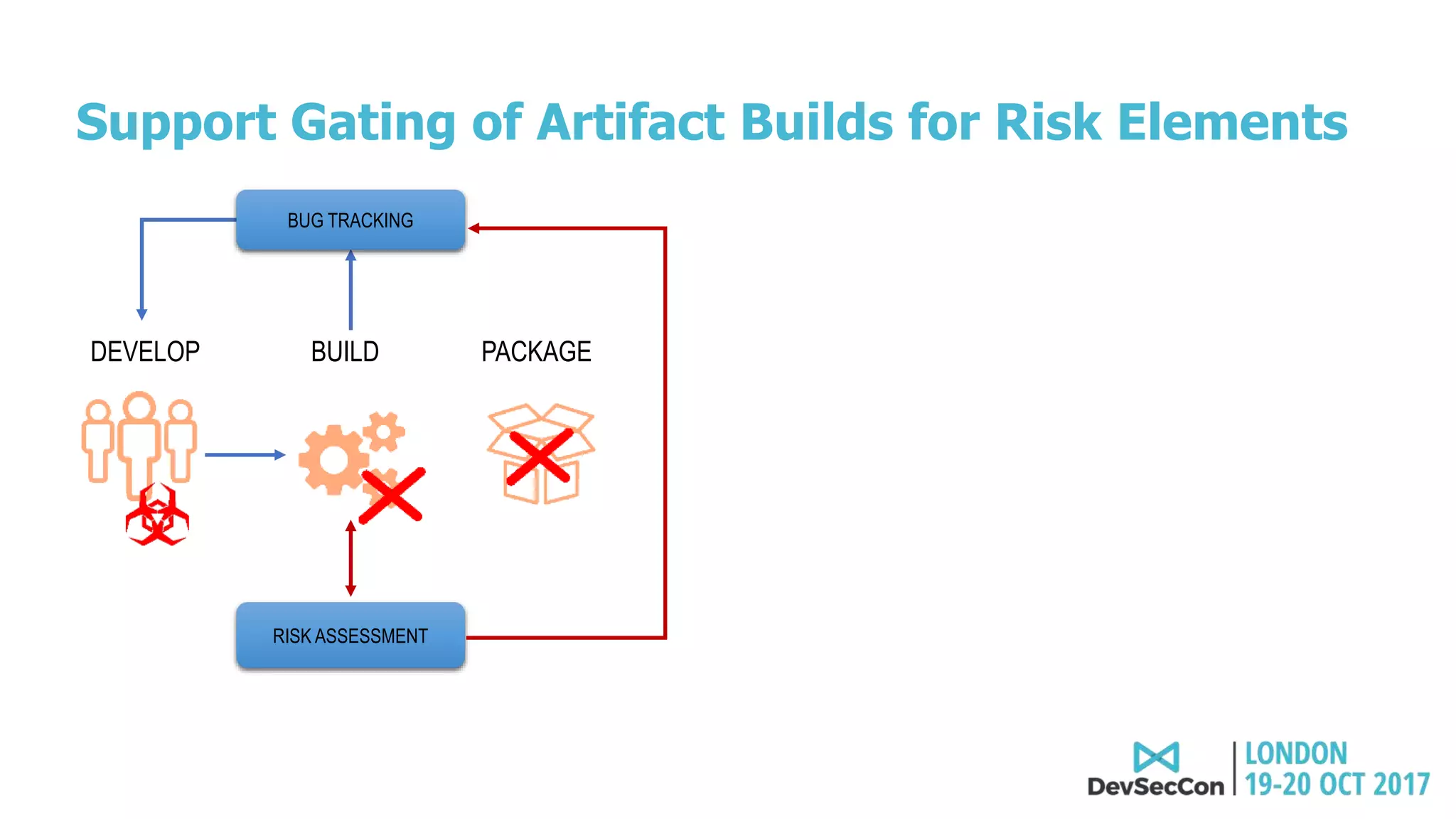
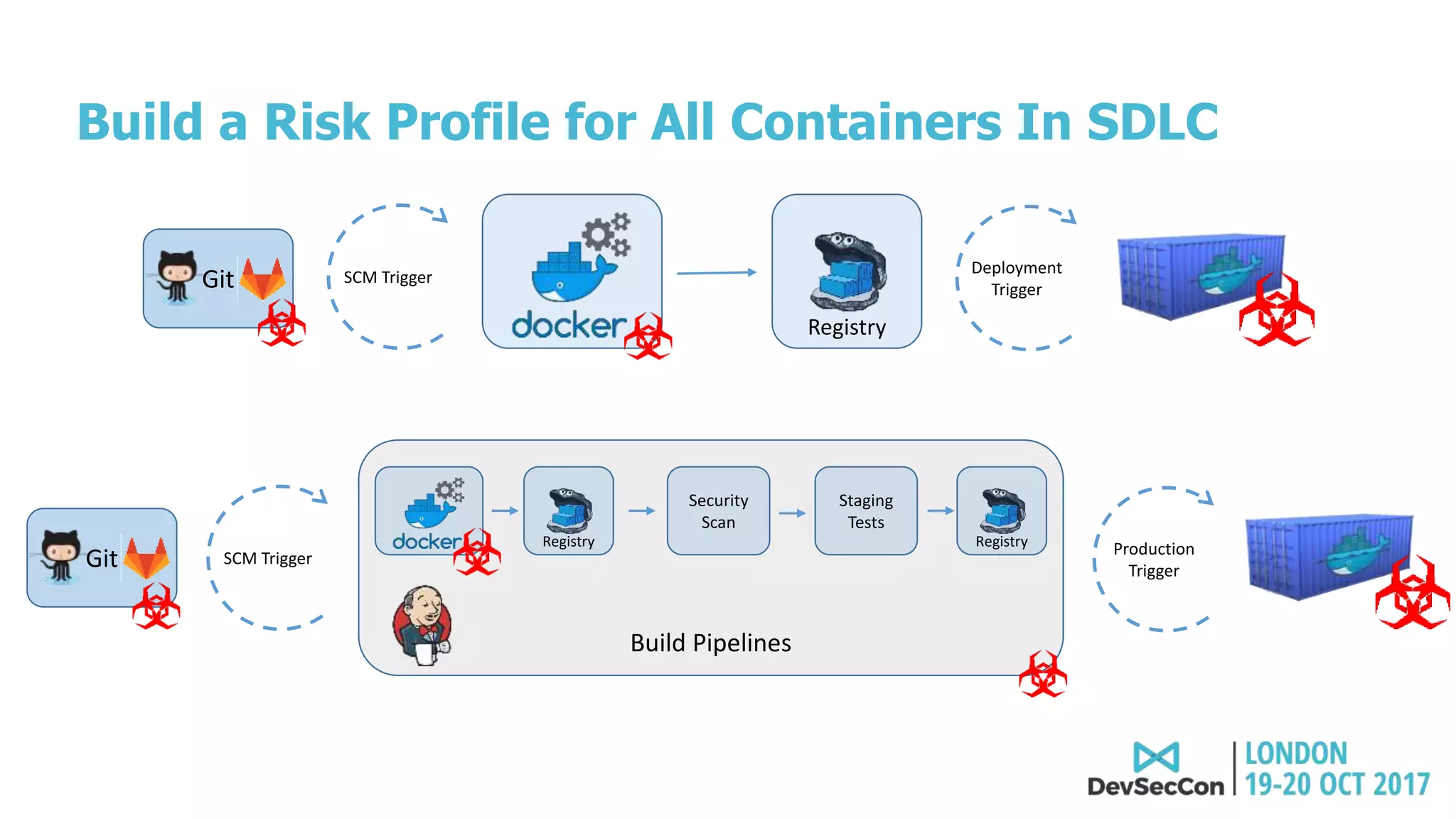
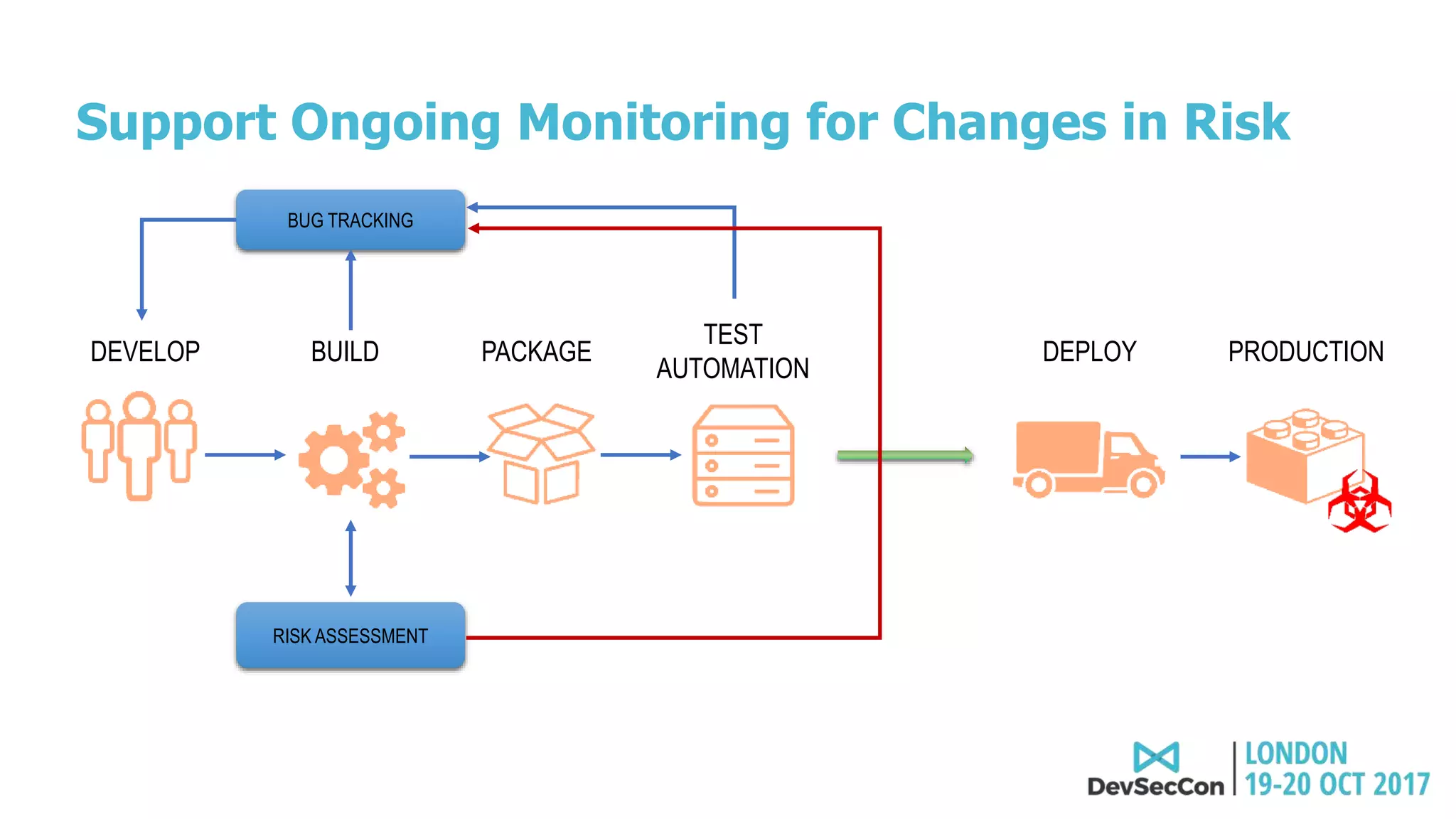
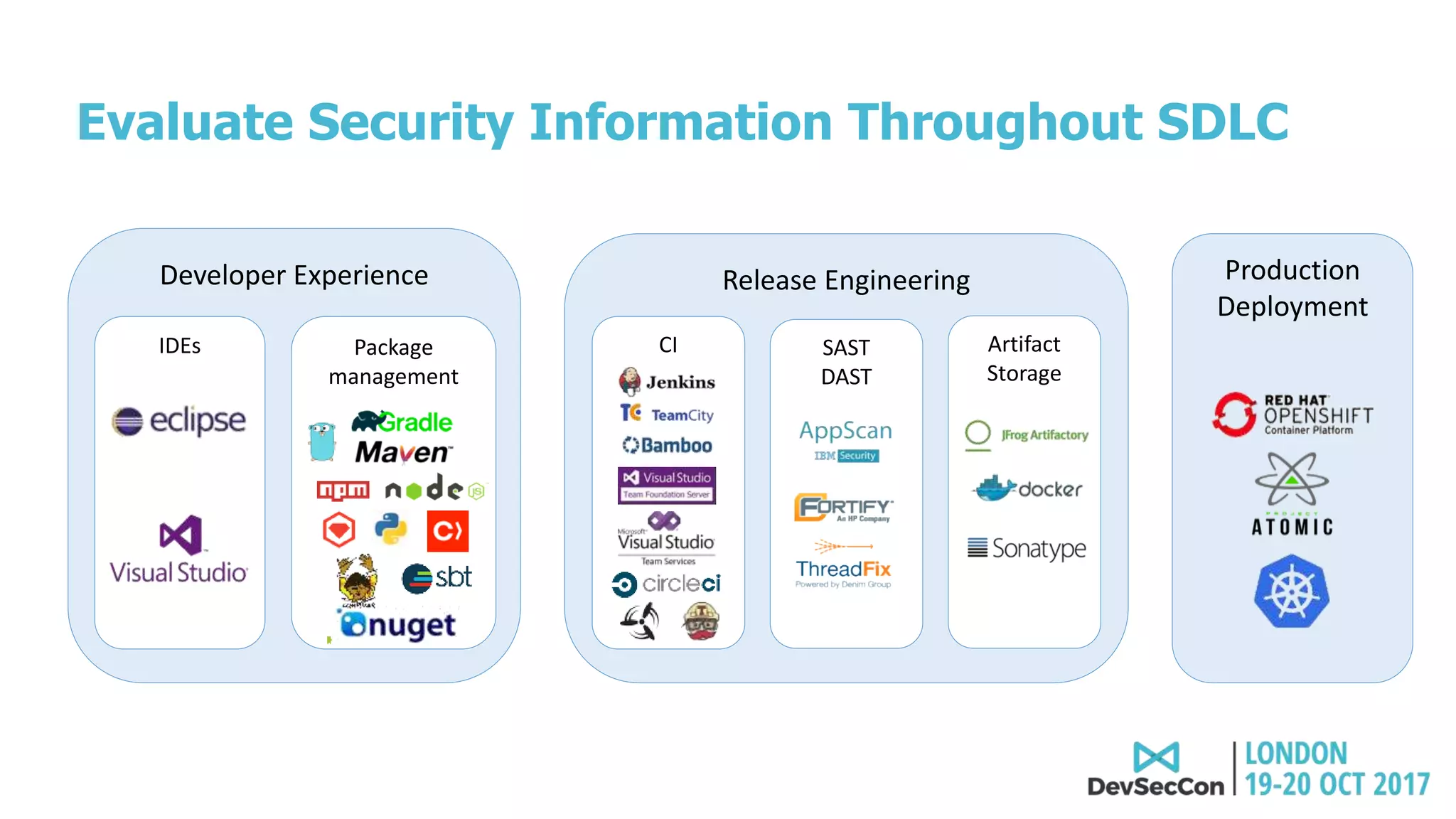
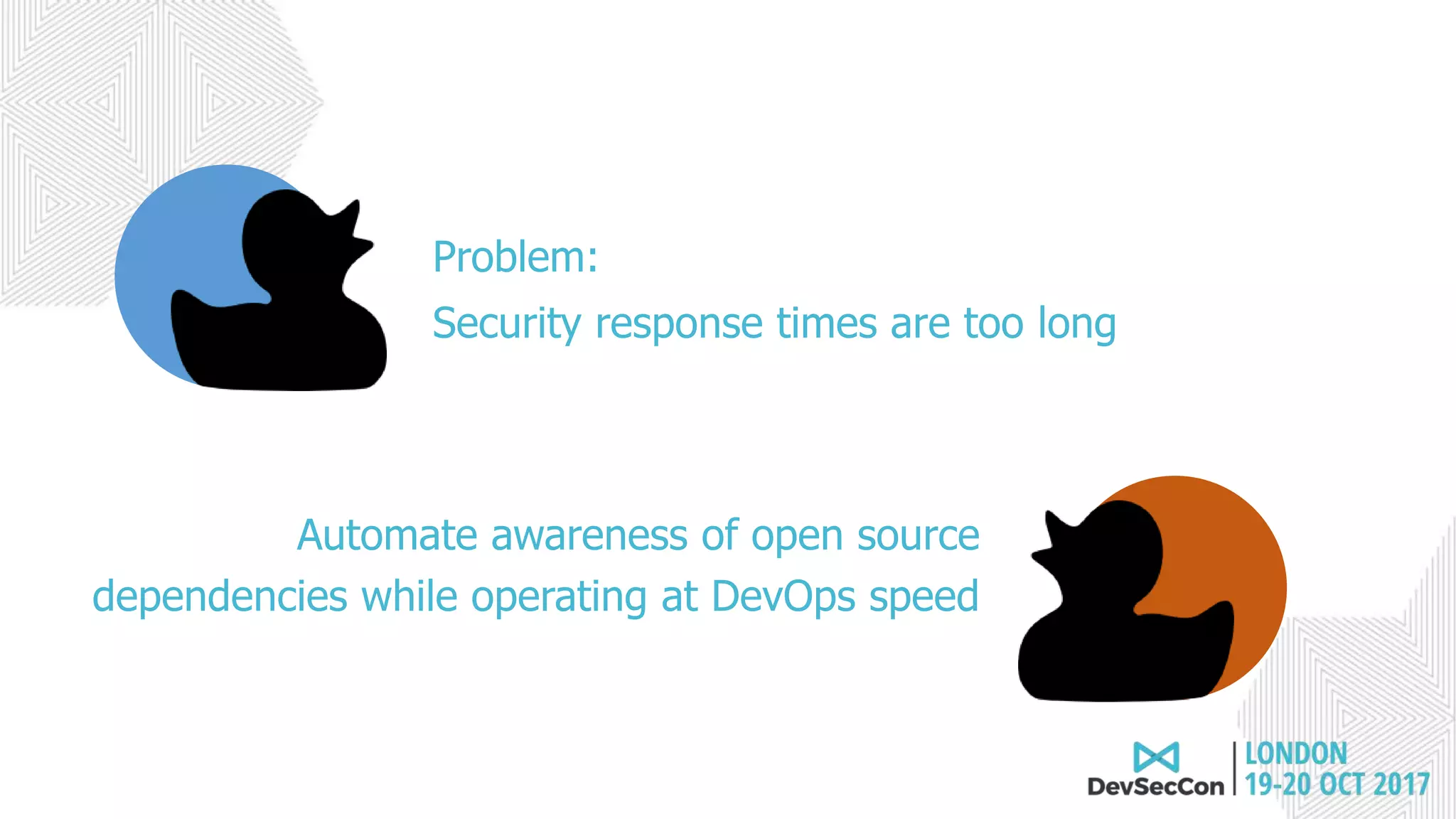
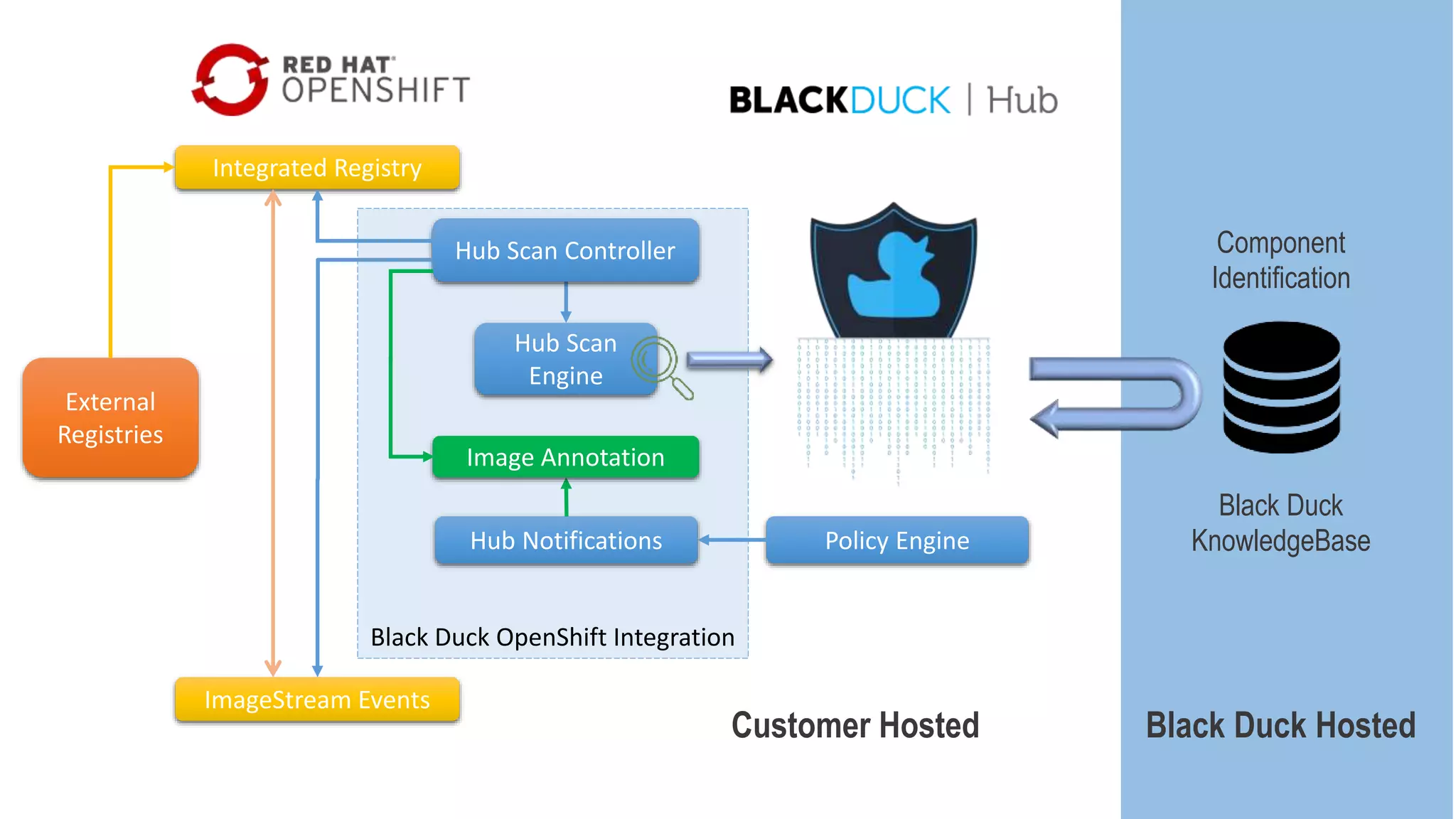
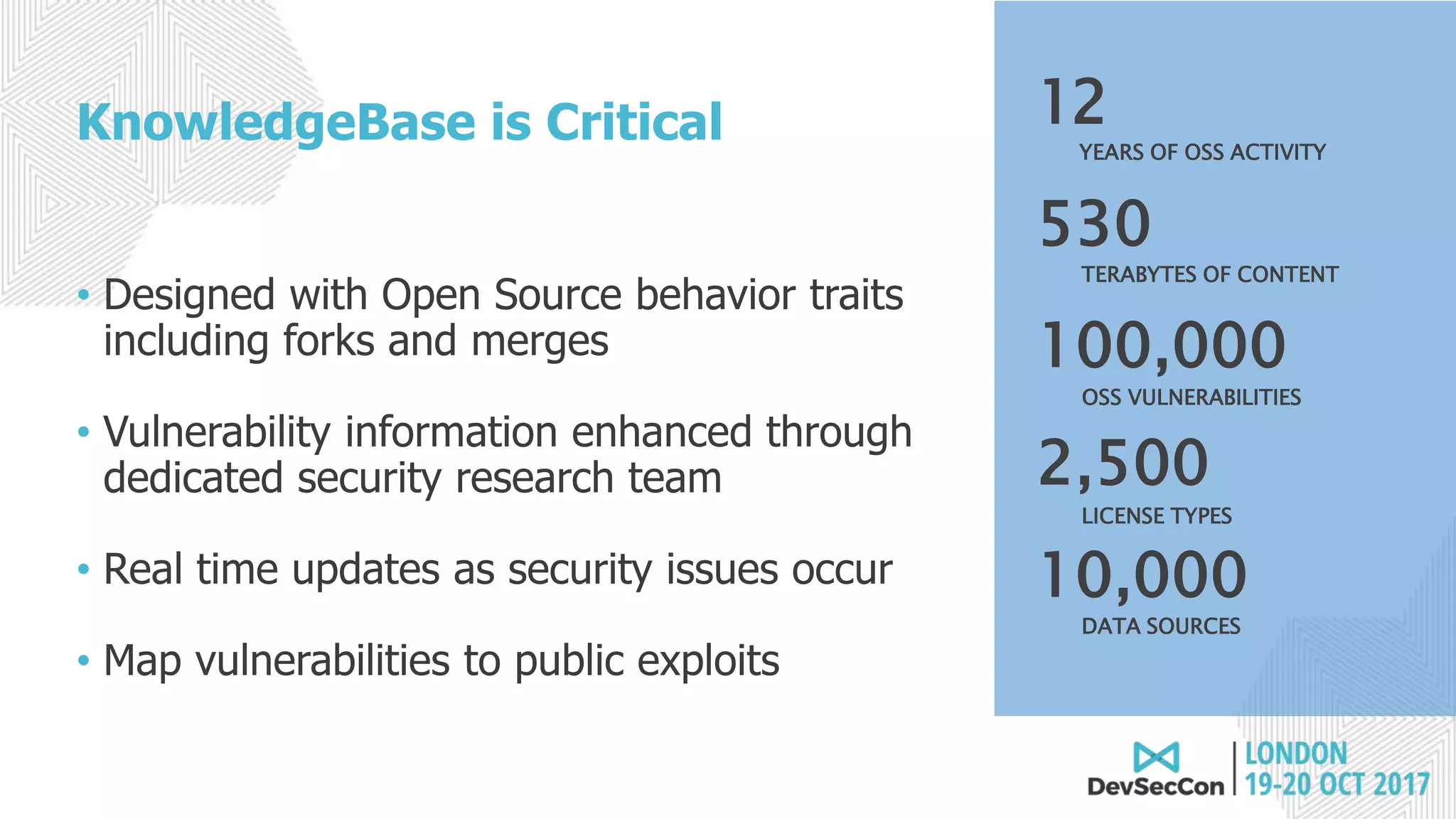
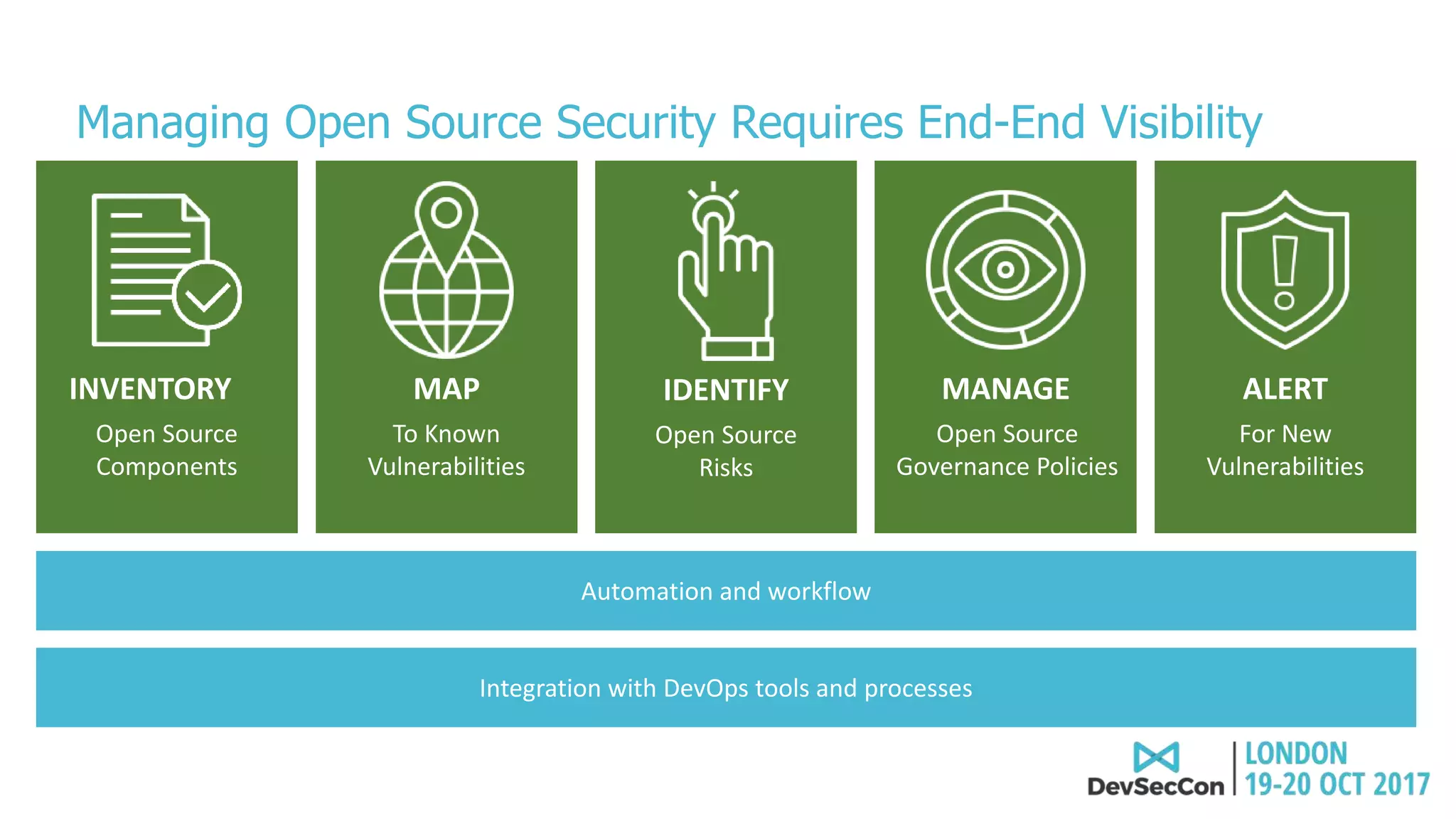
This document summarizes Tim Mackey's presentation at DevSecCon. It discusses the importance of security driven development practices like using trusted components, continuous integration processes that include security testing, and digitally signing container images. It warns that while infrastructure teams aim to provide security, vulnerabilities can still exist, and advocates continually evaluating the trust of components used. The document predicts disclosure of security issues will increase and outlines penalties for data breaches under new regulations like GDPR. It emphasizes automating awareness of open source dependencies to keep pace with DevOps.