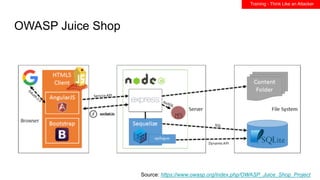
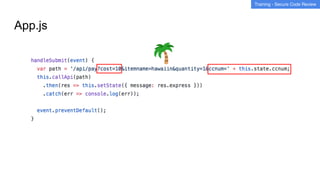
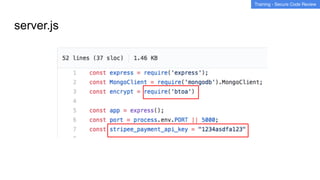
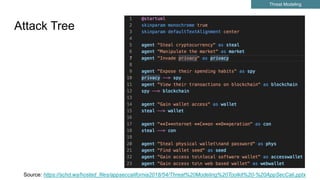
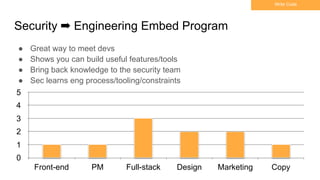
This document summarizes best practices for building an application security program at a startup. It recommends getting organizational buy-in, building a security team by networking and attending events, and shifting security left by training developers. It also discusses implementing threat modeling, carefully vetting security vendors, embedding security engineers with developer teams, and continuing to improve processes over time. The overall message is that security is a collaborative effort involving the whole company.
![Year[0]
AppSec at a Startup](https://image.slidesharecdn.com/yearzero-181025030223/85/Year-Zero-1-320.jpg)