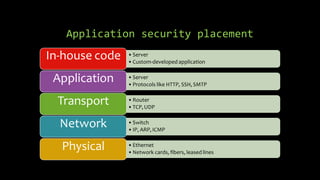
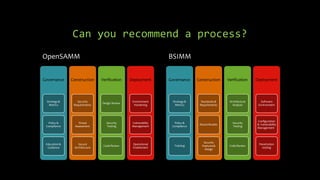
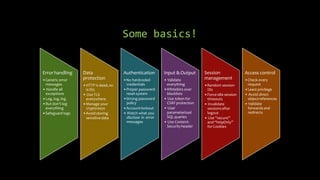
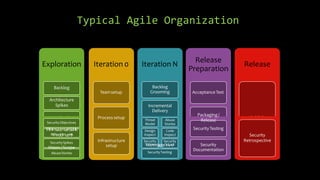
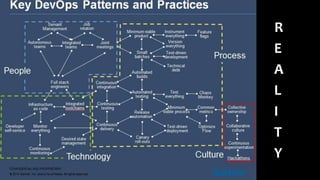
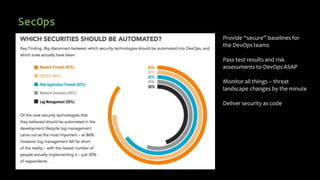
Dimitrios Stergiou discusses application security approaches, highlighting ineffective strategies like bolt-on security and extreme security measures, while advocating for a balanced process aligned with agile frameworks. He emphasizes the importance of integrating security throughout the software development lifecycle and leveraging governance models such as OWASP and BSIMM. The conclusion stresses that while there is no absolute truth in application security, consensus exists on core practices necessary to manage risk and ensure a secure environment.