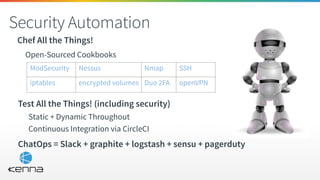
This document discusses applying security automation principles through a SecDevOps approach. It begins by highlighting lessons from other companies that deployed features in a disabled state using feature flags and integrated security testing in continuous integration. The document then outlines how Kenna applies SecDevOps principles through automation, with examples like using Chef for configuration management and testing security at each code check. It also presents a use case where Kenna loads security scanning results from various tools into its platform via API to enable continuous security testing.


























![Mix It Together
Parse Some XML
$ cat nvdcve-2.0-2014.xml | ruby -e 'require "ox"; p
Ox.parse(ARGF.read).nvd.locate("entry").select {|x| x.locate("*/
vuln:product/*").member? "cpe:/a:oracle:mysql:5.5.26" }.map(&:id)’
["CVE-2014-0384", "CVE-2014-0386", "CVE-AWW-YEAH",...]
What was that?
• We have mysql 5.5.26 installed
• Searching for it’s most specific CPE locator
• We found that there are a bunch of Vulnerabilities for it from 2014](https://image.slidesharecdn.com/edbellissecurityascode-does15-151029172326-lva1-app6891/85/Security-as-Code-DOES15-30-320.jpg)






