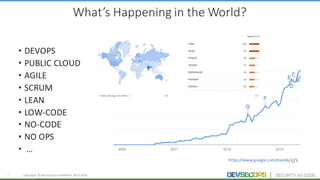
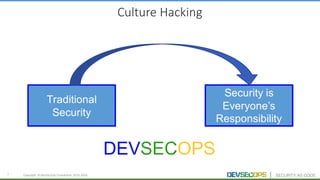
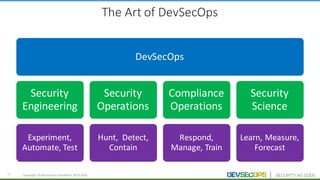
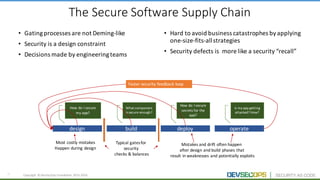
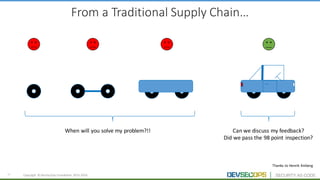
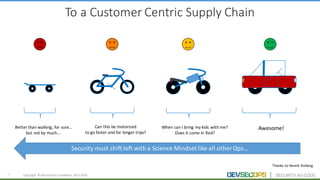
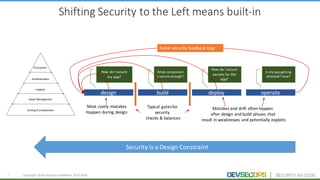
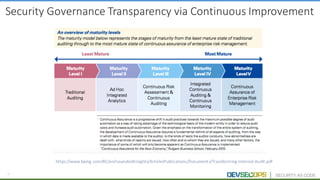
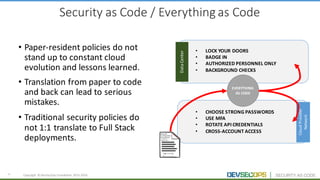
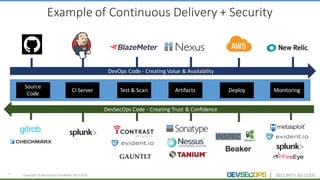
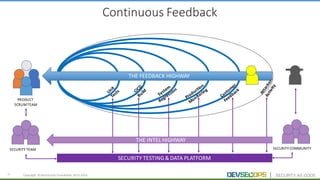
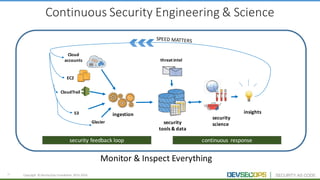
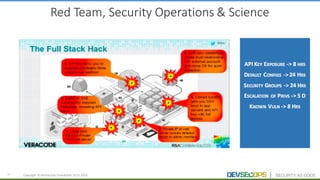
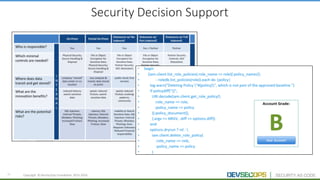
The document discusses the concepts of DevSecOps, which aims to integrate security practices into software development processes from the beginning. It notes trends in DevOps, cloud computing, and agile development that have led to this approach. DevSecOps seeks to shift security "left" so that it is designed into applications from the start rather than treated as an afterthought. This is achieved through continuous feedback between developers and security teams to build security into applications and infrastructure through automated testing and monitoring.