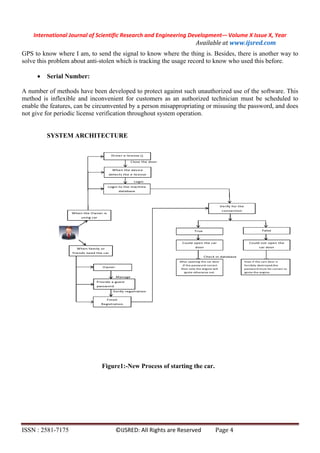
This document summarizes a research paper on a device verification and safety system for cars using RFID tags. The system uses an RFID tag and reader to identify unauthorized access to the car. A microcontroller uses an ID and password entered by the person in the car to control the engine starting. A GPS system helps the owner locate a stolen car by tracking its location. The system is built with an ATmega16 controller and uses SMS messaging to transmit intruder data and alerts to the owner. It aims to merge vehicle security, tracking, and remote control capabilities.



![International Journal of Scientific Research and Engineering Development-– Volume X Issue X, Year
Available at www.ijsred.com
ISSN : 2581-7175 ©IJSRED: All Rights are Reserved Page 5
IV.CONCLUSION
Hence this system efficiently prevents car theft using RFID and SMS gateway technology. And even if the
thief manages to steal the car, the owner or police can easily track the vehicle and can also identify the
thief by using SMS gateway. This device will relieve the police pressure of searching the stolen vehicle to
reduce the rate of car theft. The sensors, the RFID and the password need to be correct to ignite the engine
which will be sufficient to prevent the theft of the car in most cases. The system may be further upgraded
by adding a module that authenticates the owner using his/her ID Password.
ACKNOWLEDGMENT
We would like to express our deepest gratitude to our guide Prof.Milind Bhandare, project Coordinator
Prof.Prashant Kale, and HOD Dr.(Prof). Nilesh Wankhede, Department of Computer Engineering, Late
G.N. Sapkal college of engineering, for guidance and advice that helped us to improve to present the paper
with their full efforts in guiding us in achieving the goal and also giving valuable suggestions to improve
the paper.
REFERENCES
[1] Bajaj, S., Bradescu, R. A., Burstein, J., M'raihi, D., & Popp, N. (2011). System and method for website authentication using shared secret.
[2] The Future Of Energy. Chacon, A. W. (1996). Vehicle anti-theft system: Google Patents.
[3] Gerla, M., Lee, E.-K., Pau, G., & Lee, U. (2014). Internet of vehicles:From intelligent mesh to autonomous cars and vehicular clouds.
[4] Gogoro. (2017). The Future Of Energy.
[5] Hou, X., Li, Y., Chen, M., Wu, D., Jin, D., & Chen, S. (2016). Vehicular fog computing: A viewpoint of vehicles as infrastructures. IEEE Transactions on
Vehicle Technology, 65(6), 3860-3873.
[6] Jia, X., Feng, Q., Fan, Q. (2012). RFID technology and its approach in Internet of Things (IoT). Paper presented at the Consumer Electronics,
Communications and Networks (CECNet), 2012 2nd International Conference on.
[7] Liu, J. K., Au, M. H., Susilo, W., & Zhou, J. (2012). Enhancing location privacy for electric vehicles. Paper presented at the European Symposium on
Research in Computer Security.
[8] Peng, S.-L., Lee, G.-L., Klette, R., & Hsu, C.-H. (2017). Internet of Vehicles. Technology and Services for Smart Cities: 4th International Conference, Iov
2017.
[9] Serkowski, R. J., & Walker, W. T. (2007). License file serial number tracking: Google Patents](https://image.slidesharecdn.com/ijsred-v2i6p4-200210182158/85/Device-Verification-and-SafetyUsing-RFID-Tag-5-320.jpg)