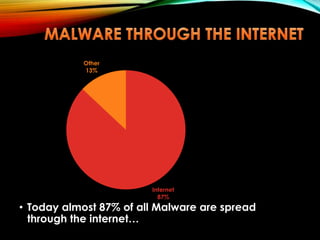
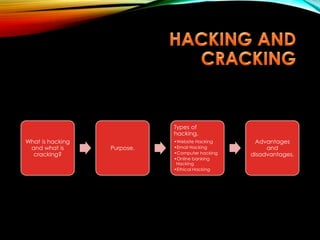
This document discusses various common security risks and threats to computers and networks. It covers topics like malware, viruses, spam, spoofing, phishing, botnets, worms, Trojans, backdoors, blended threats, denial of service attacks, and physical threats like hardware theft and vandalism. It also discusses prevention, detection and removal strategies for many of these threats. Passwords, antivirus software, firewalls and regular backups are recommended for protection. The document provides examples of weak versus strong passwords. It cautions that most malware is spread through the internet.