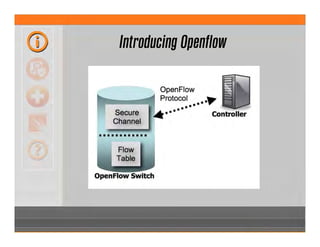
This document summarizes a presentation on abusing software defined networks. It discusses how SDNs separate the control plane from the data plane and use controllers to program switches. While SDNs solve many network problems, the presentation outlines several security weaknesses in SDN protocols and controllers like Floodlight and Opendaylight that could allow attackers to gain unauthorized access, intercept traffic, or launch denial of service attacks. It demonstrates exploits against real networks and advocates for securing SDN through encryption, authentication, access control, and developing security capabilities within SDN controllers.