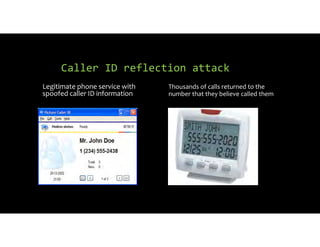
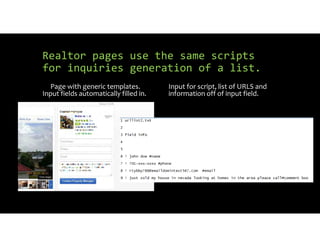
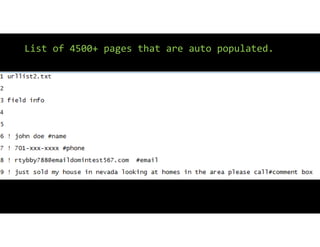
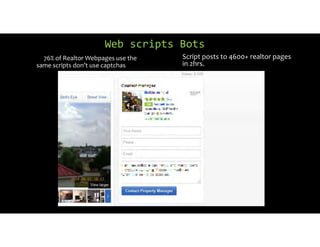
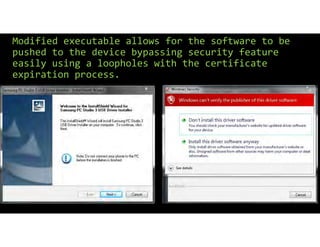
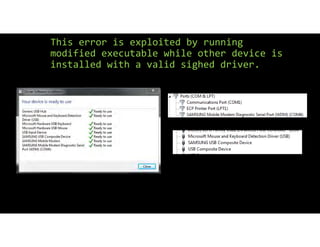
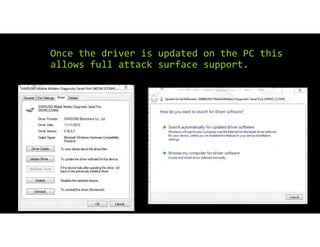
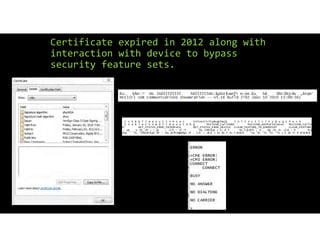
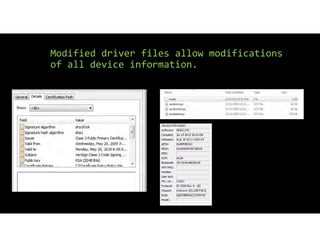
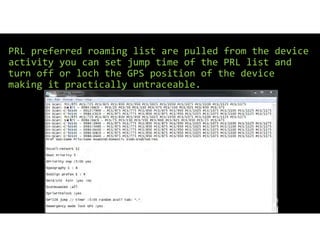
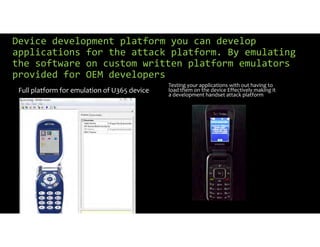
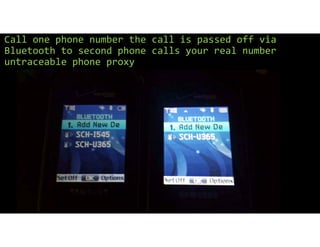
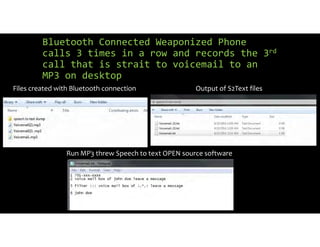
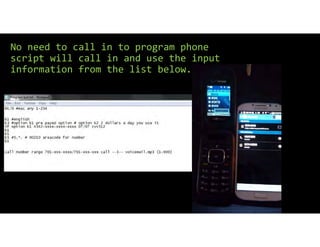
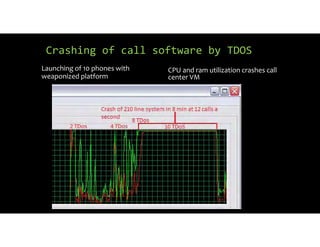
The document discusses using inexpensive prepaid phones to conduct telephony denial-of-service (TDoS) attacks. It describes how the phones can be modified by unlocking their bootloaders and flashing them with custom firmware, allowing them to make thousands of spoofed calls in order to crash a target organization's phone system. The document shows how a kit with multiple modified phones, solar chargers, and other basic equipment could be used to conduct sustained TDoS attacks for around $21.