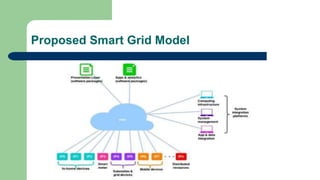
This document discusses cyber security in smart grid systems. It begins by defining smart grids as power grids that use digital technology to improve reliability, security and efficiency. It then discusses why smart grids are needed to address challenges like increasing power production while reducing carbon footprint. The document outlines some key cyber security risks in smart grids like denial of service attacks and malware. It also describes some common security requirements like availability, integrity and confidentiality. Finally, it proposes some solutions to smart grid cyber security like network security protocols, data security methods, key management and secure communication architectures.























![References
[1] Salsabeel, Fatma, Raafat (2015) ‘Smart grid cyber security: challenges and solutions’
[2] Y.Yang, Tim Littler, S.Sezer, H.F.Wang (2015) ‘impact of cyber security issues on smart
grid’
[3] Danda, Chandra (2015) ‘cyber security for smart grid system: status, challenges and
perspectives’
[4] Sharmin, Rabeya (2015) ‘An analysis of smart gridcommunication infrastructure & cyber
security in smart grid’
[5] Ye yan, Yi qian, Hamid and David (2012) ‘A survey on cyber security for smart grid
communication’
[6] Adam, Aditya, Siddharth, Manimaran (2013) ‘Cyber physical security testbeds: architecture,
application’
[7] A.David (2014) ‘Bio inspired cyber security for the smart grid’](https://image.slidesharecdn.com/smartgridsystem-170406155833/85/Cyber-security-in-Smart-grid-system-30-320.jpg)
