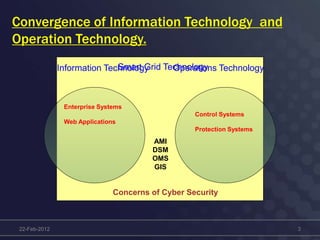
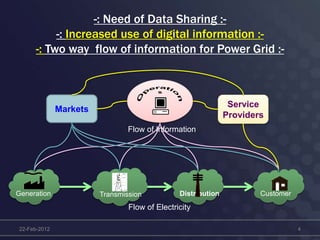
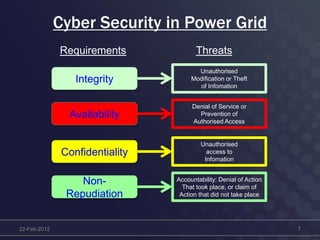
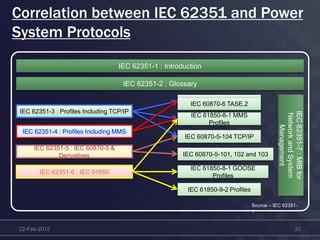
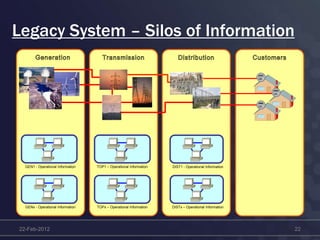
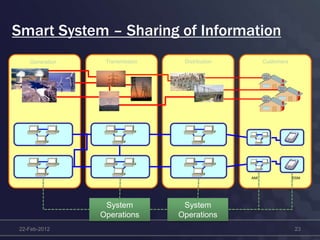
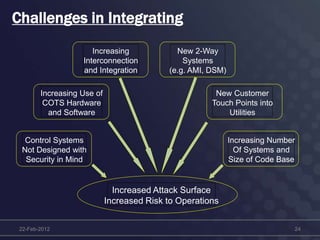
This document discusses cyber security concerns regarding smart grid technology integration. It outlines how increased data sharing and connectivity between new and legacy systems introduces new cyber vulnerabilities. It then summarizes existing cyber security standards from organizations like ISO, NERC, and IEC that can provide frameworks for addressing these vulnerabilities. Finally, it notes challenges integrating new technologies with legacy systems and the need for a strategic roadmap to help guide secure technology adoption.