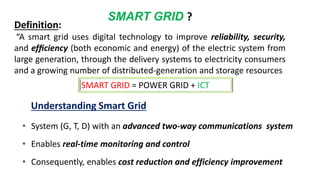
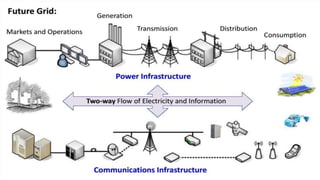
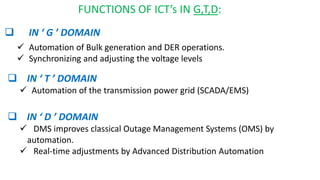
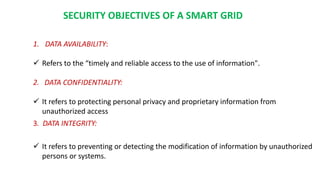
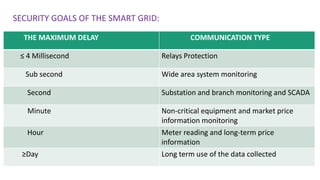
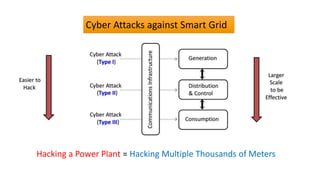
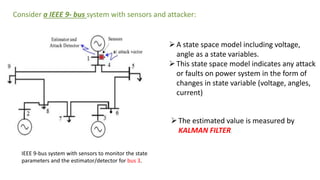
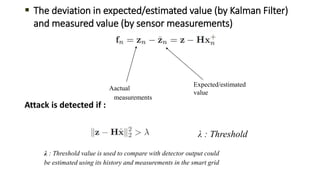
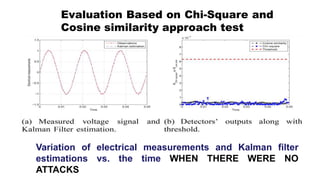
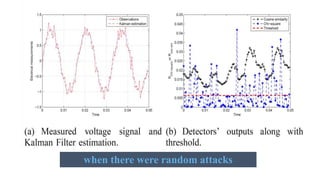
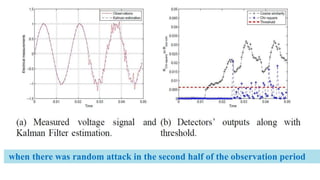
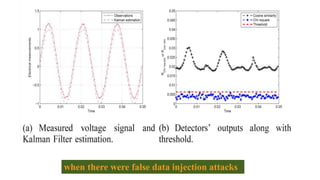
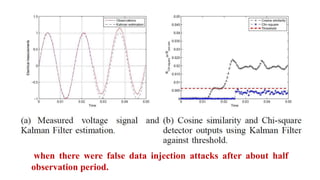
This document discusses cyber security issues in smart grids. It begins with an introduction to smart grids and their reliance on information and communication technologies. It then discusses three key security objectives for smart grids: data availability, confidentiality, and integrity. Several types of cyber attacks on smart grids are described, including denial-of-service attacks, random attacks, and false data injection attacks. The document concludes by evaluating techniques for detecting attacks, such as using chi-square tests and cosine similarity matching to compare expected and measured smart grid data.