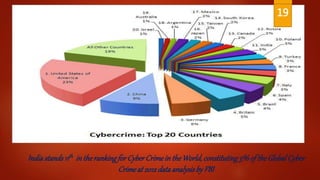
Cybercrime is on the rise globally and in India. India ranks 11th in the world for cybercrime, constituting 3% of global cybercrime. Common cybercrimes in India include denial of service attacks, website defacement, spam, computer viruses, pornography, cyber squatting, cyber stalking, and phishing. While Indian laws against cybercrime are well-drafted, enforcement has been lacking, with few arrests compared to the number of reported cases. Increased internet and technology use in India has contributed to higher cybercrime rates in recent years. Stronger enforcement is needed to curb the growth of cybercrimes in India.







![IndianCrimeScene
The major Cyber Crimes reported, in India, are
Denial of Services, Defacement of Websites, Spam, Computer
Virus and Worms, Pornography, Cyber Squatting, Cyber
Stalking and Phishing.
Given the fact that nearly $ 120 million worth of Mobiles are
being lost or stolen in the country every year, the users have to
protect Information, Contact details and Telephone numbers
as these could be misused. Nearly 69 per cent of information
theft is carried out by current and ex-employees and 31 per cent
by hackers. India has to go a long way in protecting the vital
information.
[3 The Hindu, Saturday, Oct 27, 2007].
10](https://image.slidesharecdn.com/cybercrime-160724163552/85/Cyber-crime-10-320.jpg)