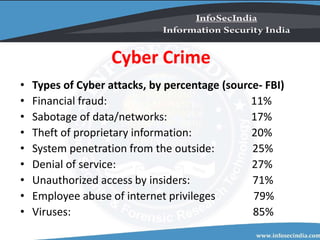
The document discusses cybercrime, defining it as crimes committed via computers and the internet, and categorizes it by types including hacking, child pornography, denial of service attacks, and software piracy. It provides statistics on various cyber attacks and their prevalence, highlighting issues like financial fraud and unauthorized access. Additionally, it offers cybersecurity tips to mitigate risks, emphasizing the importance of antivirus software and maintaining security settings.