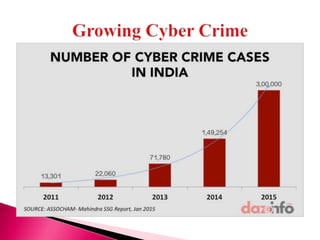
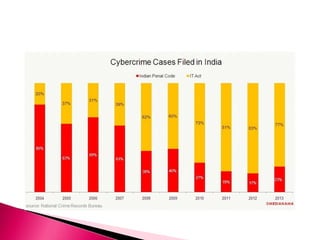
The document discusses various forms of cyber crime, categorizing them as using computers as targets or weapons, with specific examples such as hacking, data theft, and cyber terrorism. It highlights the implications for national security and emphasizes the need for cyber security measures, including antivirus software and firewalls, as well as the importance of adhering to cyber ethics and laws. The document concludes that while Indian laws on cyber crime are comprehensive, ongoing education and enforcement are necessary to combat evolving threats.