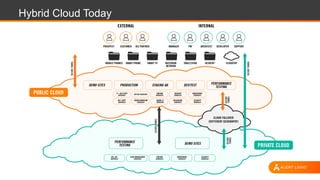
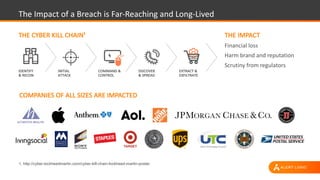
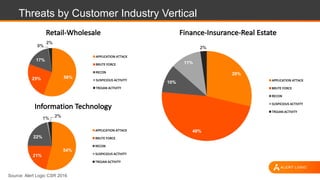
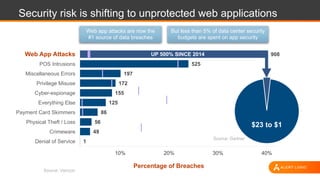
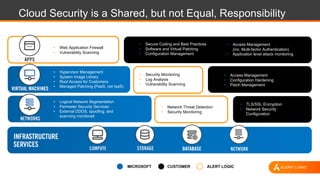
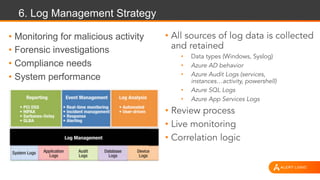
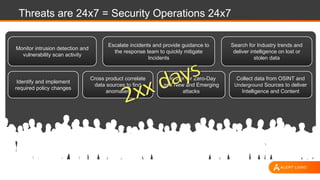
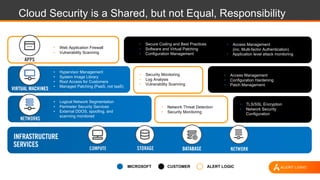
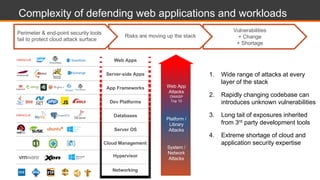
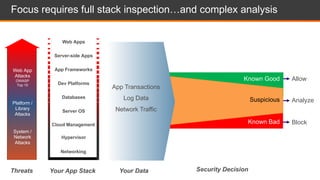
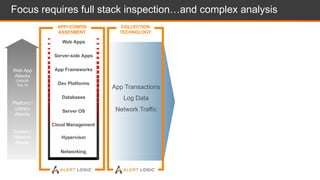
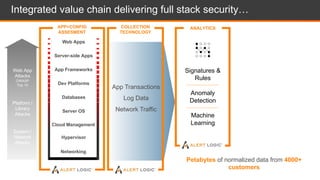
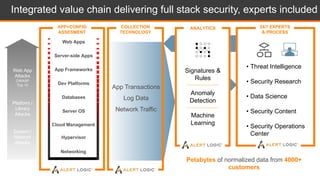
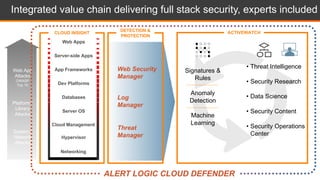
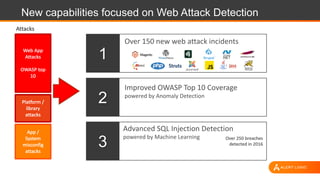
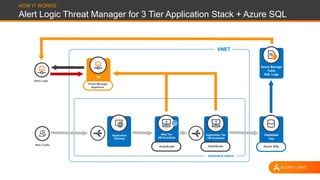
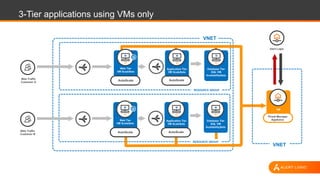
The document discusses shared security responsibilities in Azure, emphasizing that while Microsoft secures much of the infrastructure, customers must manage security for their applications and data. It outlines various security best practices, threats such as web application attacks, and the shifting risk landscape. Additionally, it provides a comprehensive set of recommendations for securing cloud workloads, including understanding the shared responsibility model, adopting patch management, and regularly reviewing logs.