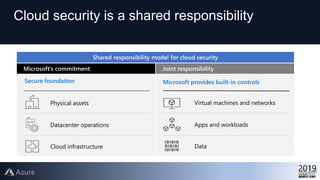
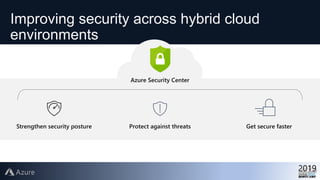
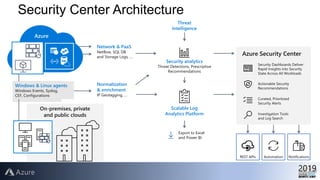
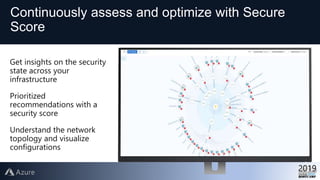
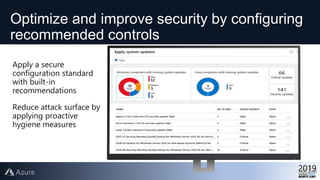
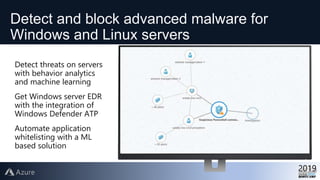
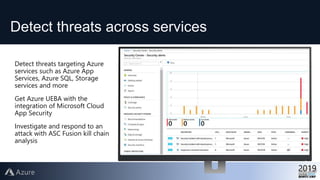
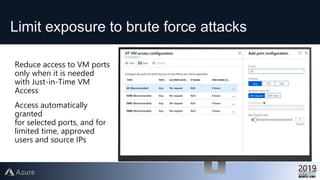
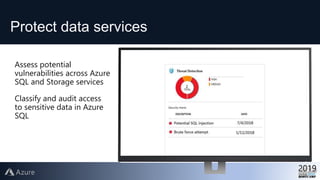
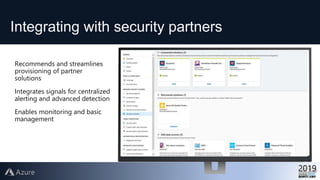
This document provides an overview of Azure Security Center, which is a service that helps secure hybrid cloud environments. It discusses how Azure Security Center provides improved security across Azure subscriptions by delivering security recommendations, dashboards to monitor security state, and APIs to integrate with other security tools. The presentation includes an agenda that covers why cloud security is needed, how Azure Security Center addresses security as a shared responsibility, and demonstrations of its key capabilities like threat detection, secure score assessments, and recommendations for configuring security controls.