Embed presentation
Download to read offline



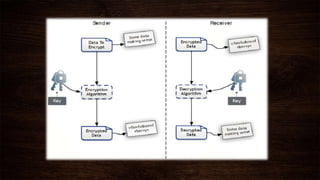

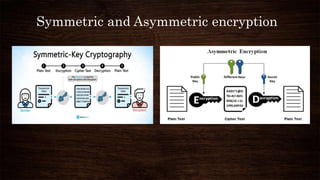
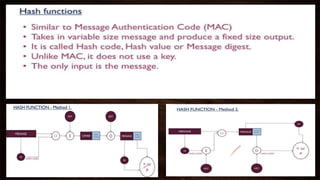

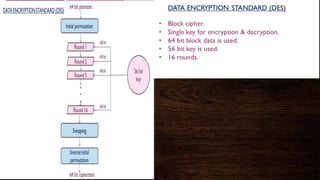
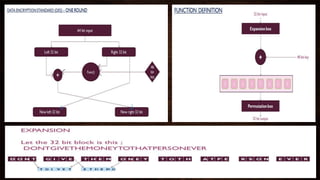
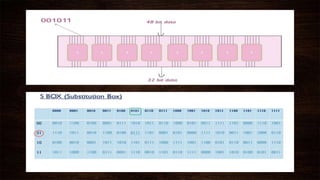

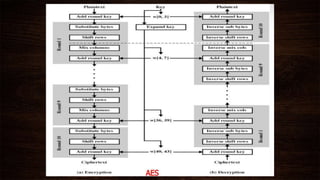
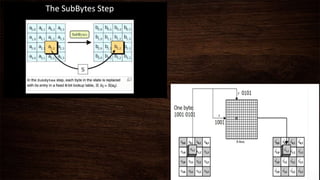
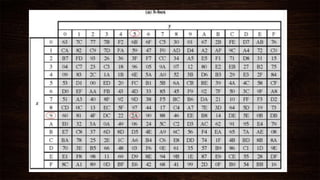
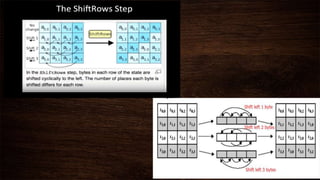
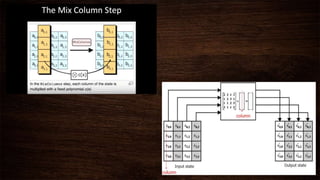
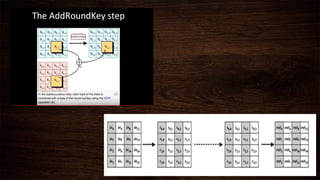
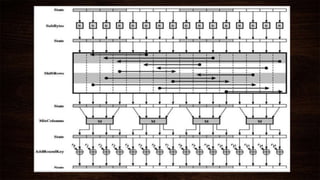
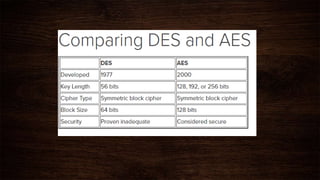

Cryptography is a method of protecting information through codes and involves encryption and decryption processes. Encryption encodes messages into cipher text using a key, while decryption decodes cipher text back into the original plain text. There are two main types of encryption - symmetric which uses the same key for encryption and decryption, and asymmetric which uses different public and private keys. Common encryption algorithms include the Advanced Encryption Standard (AES).




















