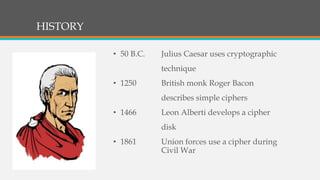
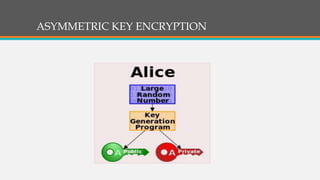
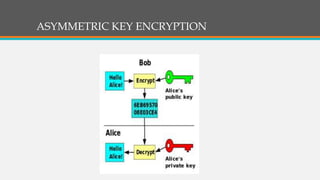
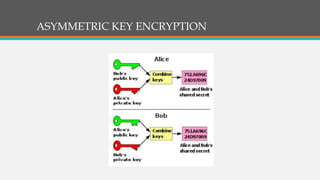
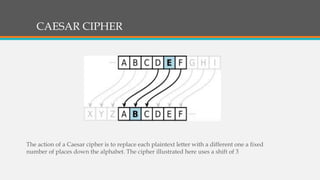
Cryptography involves techniques for securing communication and information. It uses ciphers and encryption algorithms to convert plain text into encrypted ciphertext. There are two main types of encryption: symmetric key encryption which uses a shared secret key for encryption and decryption, and asymmetric (public key) encryption which uses separate public and private keys. Cryptography is used for secure communication over the internet, wireless networks, and to encrypt files and content. Common ciphers include the Caesar cipher which shifts each letter by a fixed number of positions. Ciphers can be attacked using statistical analysis of letter frequencies or brute force methods to decrypt the ciphertext without the key.