This document discusses using machine learning algorithms to detect credit card fraud. It begins with an abstract that introduces credit card fraud as an increasing problem and machine learning as a solution. The introduction provides more background on credit card fraud and detection methods. It then discusses several machine learning algorithms that can be used for credit card fraud detection, including logistic regression, decision trees, random forests, and XGBoost. It concludes that hybrid models combining individual algorithms performed best on a publicly available credit card dataset, with the highest Matthews correlation coefficient of 0.823. References are provided on related work in credit card fraud detection techniques.

![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 04 | Apr 2022 www.irjet.net p-ISSN: 2395-0072
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 2669
Certified is characterized as any wilful or purposeful
demonstration of denying one more of proprietorship or
cash through wiliness, double dealing, or other uncalled
for implies When application extortion happens,
fraudsters apply for another card from the bank or give it
to organizations that utilization misleading or other data.
A client can record various applications with a solitary
common of portrays, or an alternate client with
comparable depicts.
1.2 Credit Card Fraud Detection
Fraud detection is a set of activities that are taken to
prevent money or property from being obtained through
false pretences. Fraud can be committed in different
ways and in many industries. The majority of detection
methods combine a variety of fraud detection datasets
to form a connected overview of both valid and non-
valid payment data to make a decision. This decision
must consider IP address, geo-location, device
identification, “BIN” data, global latitude/longitude,
historic transaction patterns, and the actual transaction
information. In practice, this means that merchants and
issuers deploy analytically based responses that use
internal and external data to apply a set of business
rules or analytical algorithms to detect fraud. Credit
Card Fraud Detection with Machine Learning is a
process of data investigation by a Data Science team and
the development of a model that will provide the best
results in revealing and preventing fraudulent
transactions. This is achieved through bringing together
all meaningful features of card users’ transactions, such
as Date, User Zone, Product Category, Amount, Provider,
Client’s Behavioural Patterns, etc. The information is
then run through a subtly trained model that finds
patterns and rules so that it can classify whether a
transaction is fraudulent or is legitimate. All big banks
like Chase use fraud monitoring and detection systems.
The Techniques of Credit Card Fraud and Prevention.
Associations and banks to utilize them propose great
security arrangements. To resolve these issues, yet at the
same fraudsters unpretentious methods develop after
some time. Therefore, it is basic to further developing
recognition and counteraction techniques. Fraud location
and avoidance's essential objective is to differentiate
between genuine and false exchanges and to forestall fake
movement. At the point when the framework neglects to
identify and forestall fake exercises, extortion discovery
dominates. In managed extortion discovery frameworks,
new exchanges are named false or certified in view of
attributes of misleading and real exercises, while
anomalies exchanges are recognized as forthcoming false
exchanges in solo extortion location frameworks.
Various techniques for credit card fraud detection
In data mining there are various methods for
distinguishing the credit card fraud detection. In this
Survey paper we talk about some most helpful methods.
• Hidden Markov Model
• K-Means Clustering
• Genetic Algorithm
• Neural Network
• Decision Tree
2. Literature Review
Existing Credit Fraud Detection Techniques
In order to detect credit fraud in the data-rich areas of
insurance, credit cards, and telecommunications, this
subsection focuses on the analysis of some reliable data
mining methods applied specifically to the data-rich areas
of insurance, credit cards, and telecommunications credit
fraud detection.To incorporate a few of them Each
approach and its applications are given a brief description.
The study compares Bayesian Belief Networks (BBN) to
Artificial Neural Networks (ANN).
In credit fraud detection, the STAGE algorithm for BBNs
and the BP algorithm for ANNs are used.The results reveal
that BBNs are more accurate and faster to train, but they
are slower when they are deployed.As in equation [1], but
applied to fresh instances. Credit card data from the real
world was used, but the number of cards used was small.
A New Method of Detecting Credit Fraud
First, the Internet platform may establish users,
environment, and behaviour using its own user data,
environmental data, and behaviour data, as well as
bioprobe technology obtained from user behaviour
Rank Category #of Reports
1 Internet Services 62,942
2 Credit Cards 51,129
3 Healthcare 47,410
4 Television and Electronic
Media
38,336
5 Foreign Money Offers and
Counterfeit Check Scams
27,443
6 Computer Equipment and
Software
18,350
7 Investment-Related 14,884](https://image.slidesharecdn.com/irjet-v9i4314-220927120457-408c9aa2/85/Credit-Card-Fraud-Detection-System-Using-Machine-Learning-Algorithm-2-320.jpg)
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 04 | Apr 2022 www.irjet.net p-ISSN: 2395-0072
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 2670
data.Behaviour pictures based on the user, environment,
and relationship network behaviour, such as in[2]
equation The detection of cheating activity is
accomplished through the use of a machine learning
system.Real-time detection of problematic spots in the
relationship network.
Second, according to the various sorts of cheating and
danger levels, passwords are used.
User behaviour can be verified using up and down text
messages, voice, visual verification code, and other
methods.Features a risk decision-making engine that
works in real time At the same time, Internet corporations
can make use of their existing infrastructure.
Imbalance of Classes
Because the credit fraud monitoring fraud sample
percentage is modest in the real world, credit fraud
monitoring is a classic class imbalance problem in
machine learning. The term "class-imbalance" refers to the
fact that there is a disparity between the classes.The
training sets utilised in the training classifier have an
unequal distribution. A two-classification system, for
example.1000 training samples are an issue, and the more
positive and negative classes there are, the better.
If the positive class samples have 995 and the negative
class samples just 5, it suggests the samples are
similarFrom the perspective of the model's training
process, if the sample size of a class is relatively tiny, the
"information" offered by this category is insufficient, and
the model does not learn how to discriminate a few
classes. Consider the following examples of extremes: 999
out of 1000 training samples.One was positive and the
other was negative. During training, the model was
partitioned at the conclusion of each iteration.all of the
samples into positive groupings, and despite the fact that
the negative category was incorrectly classified, the harm
was done.With accuracy already at 99.9%, the difference
was minimal.
3. Machine Learning Algorithm
3.1 Logistic Regression
Logistic regression is a supervised learning algorithm
which is mostly used for binary classification problems.
Although “regression” contradicts with “classification”, the
focus here is on the word “logistic” referring to logistic
function which does the classification task in this
algorithm. Logistic regression is a simple yet very effective
classification algorithm so it is commonly used for many
binary classification tasks. Customer churn, spam email,
website or ad click predictions are some examples of the
areas where logistic regression offers a powerful solution.
3.2 Decision Tree
A decision tree builds upon interactively asking questions
to partition data.Decision tree algorithm usually does not
require to normalize or scale features. It is also suitable to
work on a mixture of feature data types (continuous,
categorical, binary). On the negative side, it is prone to
overfitting and needs to be ensembled in order to
generalize well.
3.3 Random Forest
Random forest is an ensemble of many decision trees.
Random forests are built using a method called bagging in
which decision trees are used as parallel estimators. If used
for a classification problem, the result is based on majority
vote of the results received from each decision tree. For
regression, the prediction of a leaf node is the mean value
of the target values in that leaf. Random forest regression
takes mean value of the results from decision
trees.Random forests reduce the risk of overfitting and
accuracy is much higher than a single decision tree.
Furthermore, decision trees in a random forest run in
parallel so that the time does not become a bottleneck.
3.4 XG Boost
XGBoost, which stands for Extreme Gradient Boosting, is a
scalable, distributed gradient-boosted decision tree
(GBDT) machine learning library. It provides parallel tree
boosting and is the leading machine learning library for
regression, classification, and ranking problems.It’s vital to
an understanding of XGBoost to first grasp the machine
learning concepts and algorithms that XGBoost builds
upon: supervised machine learning, decision trees,
ensemble learning, and gradient boosting.Supervised
machine learning uses algorithms to train a model to find
patterns in a dataset with labels and features and then
uses the trained model to predict the labels on a new
dataset’s features.
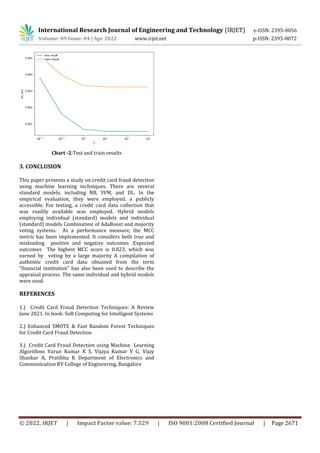
Chart -1: distribution of classes with time](https://image.slidesharecdn.com/irjet-v9i4314-220927120457-408c9aa2/85/Credit-Card-Fraud-Detection-System-Using-Machine-Learning-Algorithm-3-320.jpg)