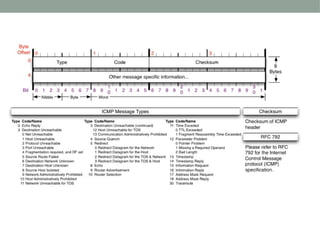
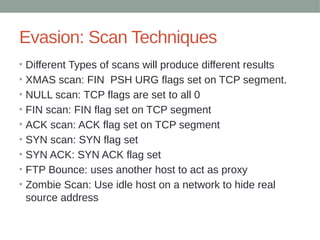
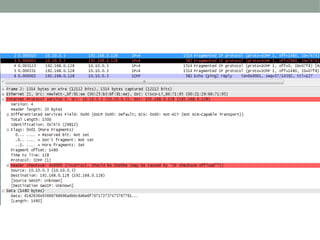
This document discusses techniques used to evade detection from enterprise security systems. It covers common security technologies like firewalls, IDS, IPS and how attackers can bypass them. Specific evasion techniques discussed include modifying packet headers, fragmentation, source routing and using tunnels through other compromised systems. The goal is to introduce common concepts but the document is not intended to be comprehensive.






































![Snort Example Signatures
•# jwalker
•alert tcp $EXTERNAL_NET $HTTP_PORTS -> $HOME_NET any (msg:"ET WORM AirOS admin.cgi/css Exploit Attempt";
flow:established,to_server; content:"POST"; http_method; content:"/admin.cgi/"; http_uri; fast_pattern:only; content:".css HTTP/1.";
http_raw_header; content:"Content-Type|3A| multipart/form-data"; http_header; reference:url,seclists.org/fulldisclosure/2011/Dec/419;
classtype:trojan-activity; sid:2014041; rev:2;)
•# jwalker
•alert udp $HOME_NET any -> $EXTERNAL_NET 53 (msg:"DNS Query to msnsolution.nicaze.net"; content:"msnsolution|06|nicaze|03|net";
offset:12; fast_pattern; reference:md5,89332c92d0360095e2dda8385d400258; sid:10000500; rev:1;)
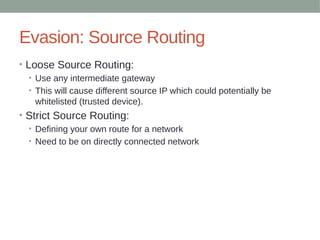
•# jwalker
•alert tcp $EXTERNAL_NET any -> $HOME_NET $HTTP_PORTS (msg:"ET LOIC Javascript DDoS Inbound"; flow:established,to_server;
content:"GET /?id="; nocase; pcre:"/[0-9]{13}/"; content:"&msg="; nocase; detection_filter:track by_src, count 100, seconds 60;
reference:url,isc.sans.org/diary/Javascript+DDoS+Tool+Analysis/12442; reference:url,www.wired.com/threatlevel/2012/01/anons-rickroll-botnet;
classtype:attempted-dos; sid:10000101; rev:1;)
•# jwalker
•alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"ET LOIC Javascript DDoS Outbound"; flow:established,from_client;
content:"GET /?id="; nocase; pcre:"/[0-9]{13}/"; content:"&msg="; nocase; detection_filter:track by_src, count 100, seconds 60;
reference:url,isc.sans.org/diary/Javascript+DDoS+Tool+Analysis/12442; reference:url,www.wired.com/threatlevel/2012/01/anons-rickroll-botnet;
classtype:attempted-dos; sid:10000102; rev:1;)
•# jwalker
•alert udp $EXTERNAL_NET any -> $HOME_NET any (msg:"Combat Arms UDP DDoS"; detection_filter:track by_src, count 10, seconds 30;
dsize:1024<>2048; sid:10000103; rev:1;)
•# jwalker
•alert tcp $EXTERNAL_NET any -> $HOME_NET $HTTP_PORTS (msg:"ET SCAN FHScan core User-Agent Detect"; flow:to_server,established;
content:"FHScan Core 1."; http_header; reference:url,www.tarasco.org/security/FHScan_Fast_HTTP_Vulnerability_Scanner/index.html;
classtype:attempted-recon; sid:2014541; rev:4;)
•# jwalker
•alert tcp $HOME_NET any -> $EXTERNAL_NET 443 (msg:"ET TROJAN Possible Variant.Kazy.53640 Malformed Client Hello SSL 3.0
(Session_Id length greater than Client_Hello Length)"; flow:to_server,established; content:"|16 03 00|"; depth:3; content:"|01 00 00 33 03 00|";
distance:2; within:6; byte_test:1,>,51,32,relative; reference:md5,a01d75158cf4618677f494f9626b1c4c; classtype:trojan-activity; sid:2014634;
rev:3;)](https://image.slidesharecdn.com/coporateespionage-180129071725/85/Coporate-Espionage-44-320.jpg)















![Tunnels and Logging
• Automation example (not tested. The grep –b4 would probably need to be
more dynamic):
• max_ms=250
• hosts=( $(nmap -PN -sV -p$port $host | grep -b4 $service | egrep -o '[[:digit:]]{1,3}.[[:digit:]]
{1,3}.[[:digit:]]{1,3}.[[:digit:]]{1,3}') )
• for ip in "${hosts[@]}"
• do
• # want to make sure ping response time is within our specified $max_ms
• time=$(ping -c1 $ip | egrep -o 'time=[0-9]{1,5}' | sed -e 's/time=//g' | tr -d 'n')
• if [[ "${time:-1000}" -ge $max_ms ]]
• then
• echo "$ip $time too slow, ignoring"
• else
• echo "$ip $time OK.. attempting to connect"
• # do stuff here with discovered device...
• fi
• done](https://image.slidesharecdn.com/coporateespionage-180129071725/85/Coporate-Espionage-61-320.jpg)



