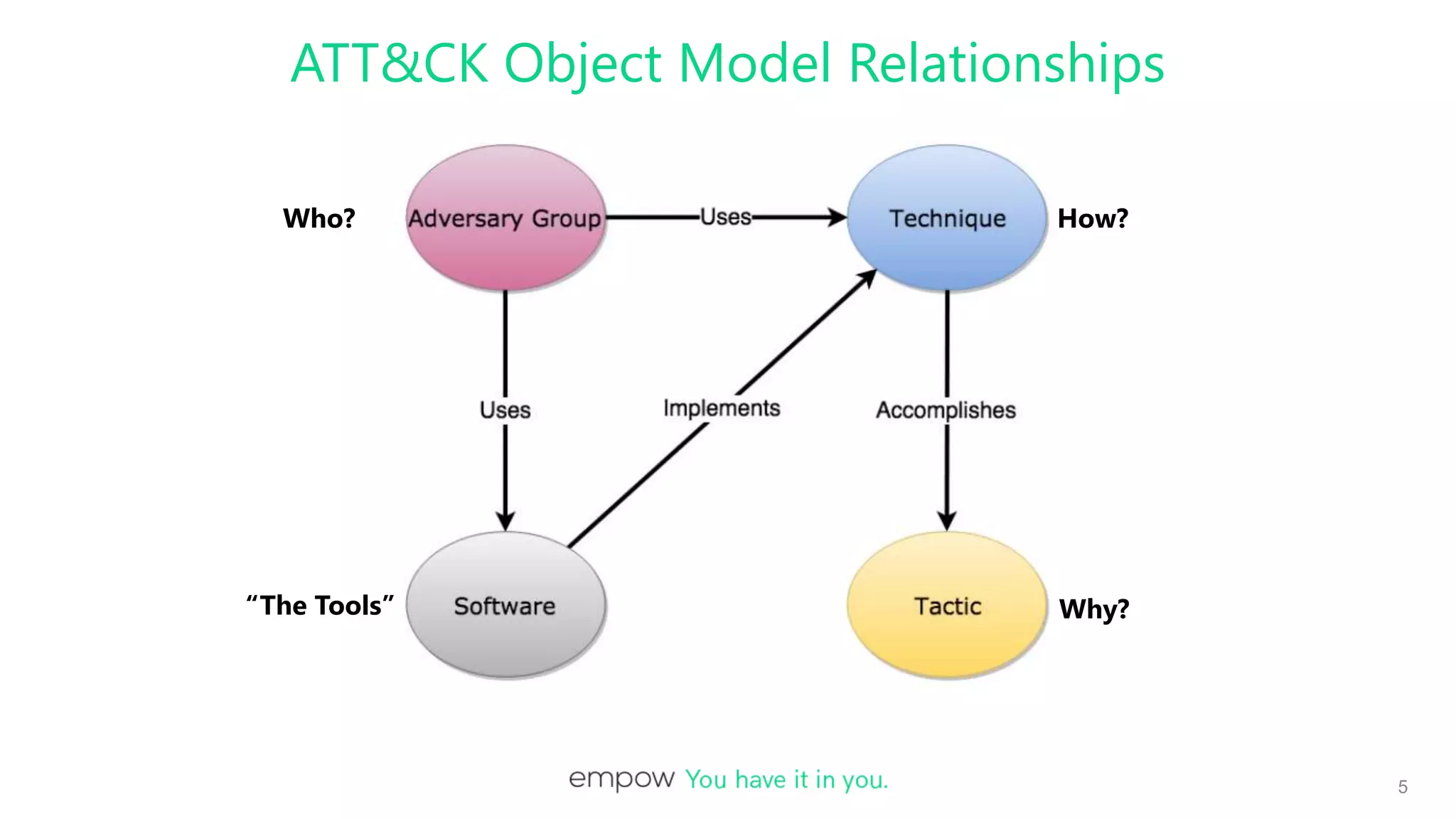
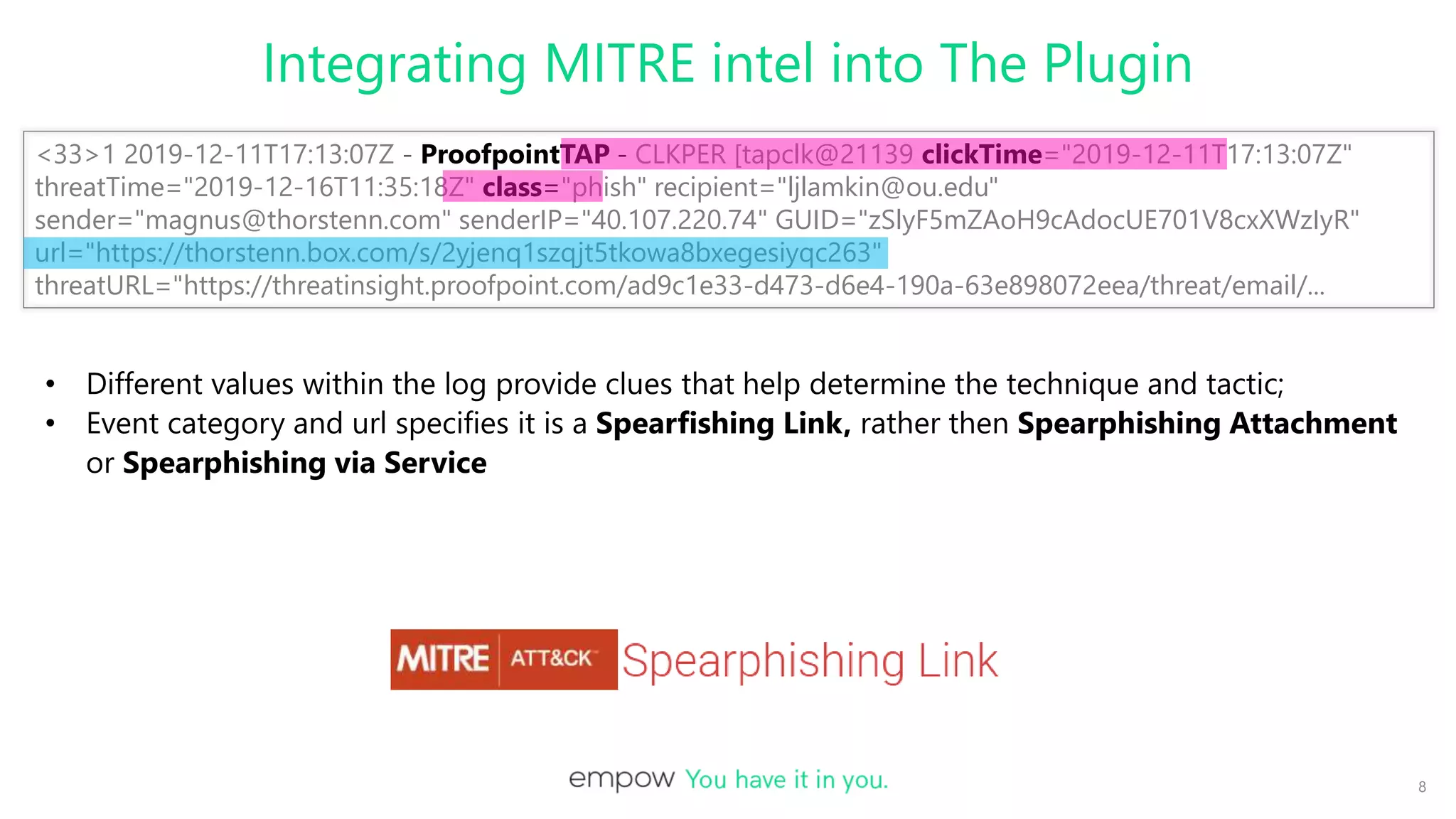
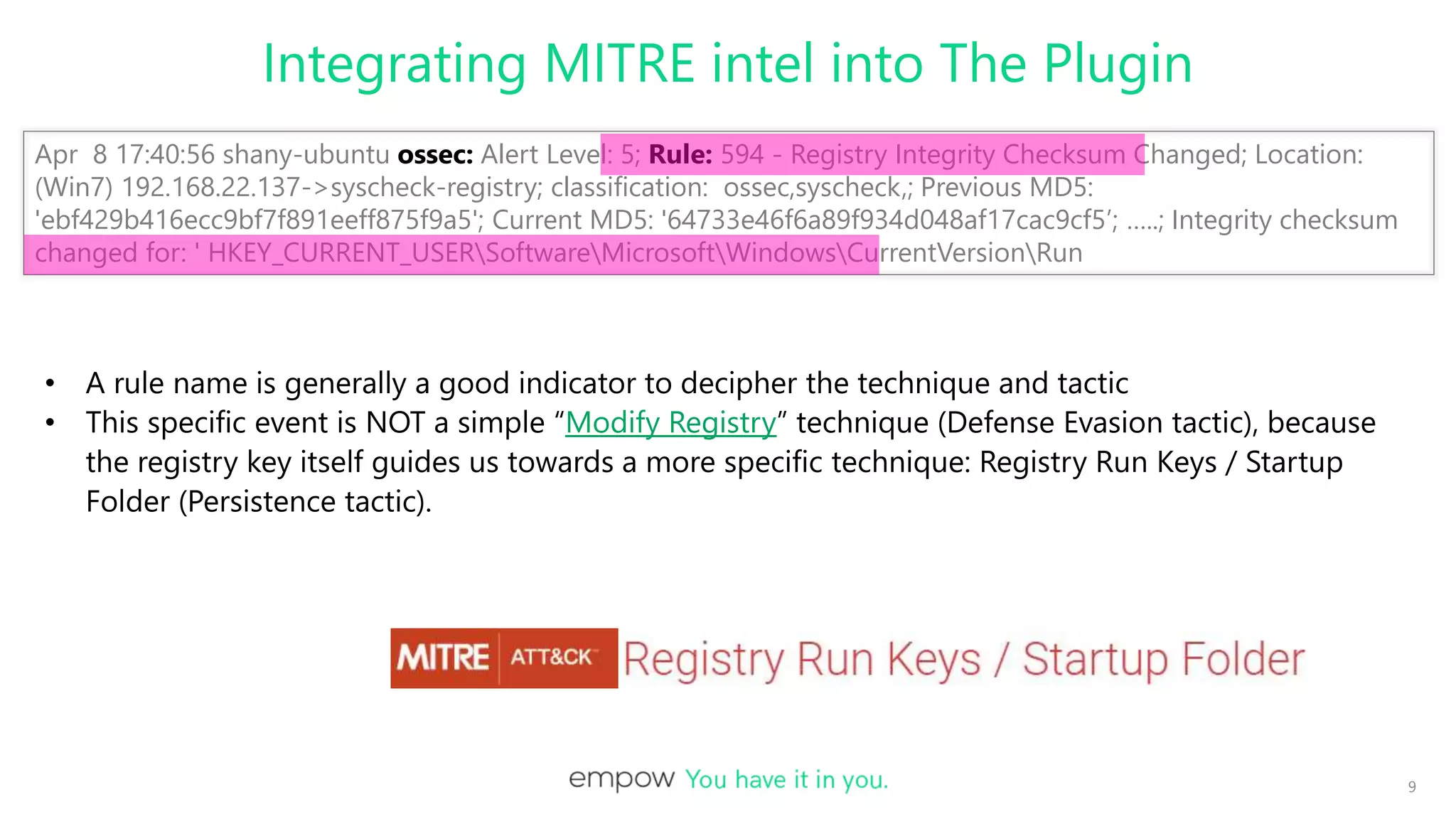
This document discusses integrating MITRE ATT&CK intelligence into Logstash plugins to provide security analysts with more context about threats. It covers writing plugins to extract relevant data from logs and map detections to MITRE tactics and techniques. When data is missing, the plugin uses other intelligence sources to infer classifications. The document demonstrates connecting Logstash pipelines to leverage parsing and enrichment, and shows tools for viewing and debugging pipeline configurations.




![10
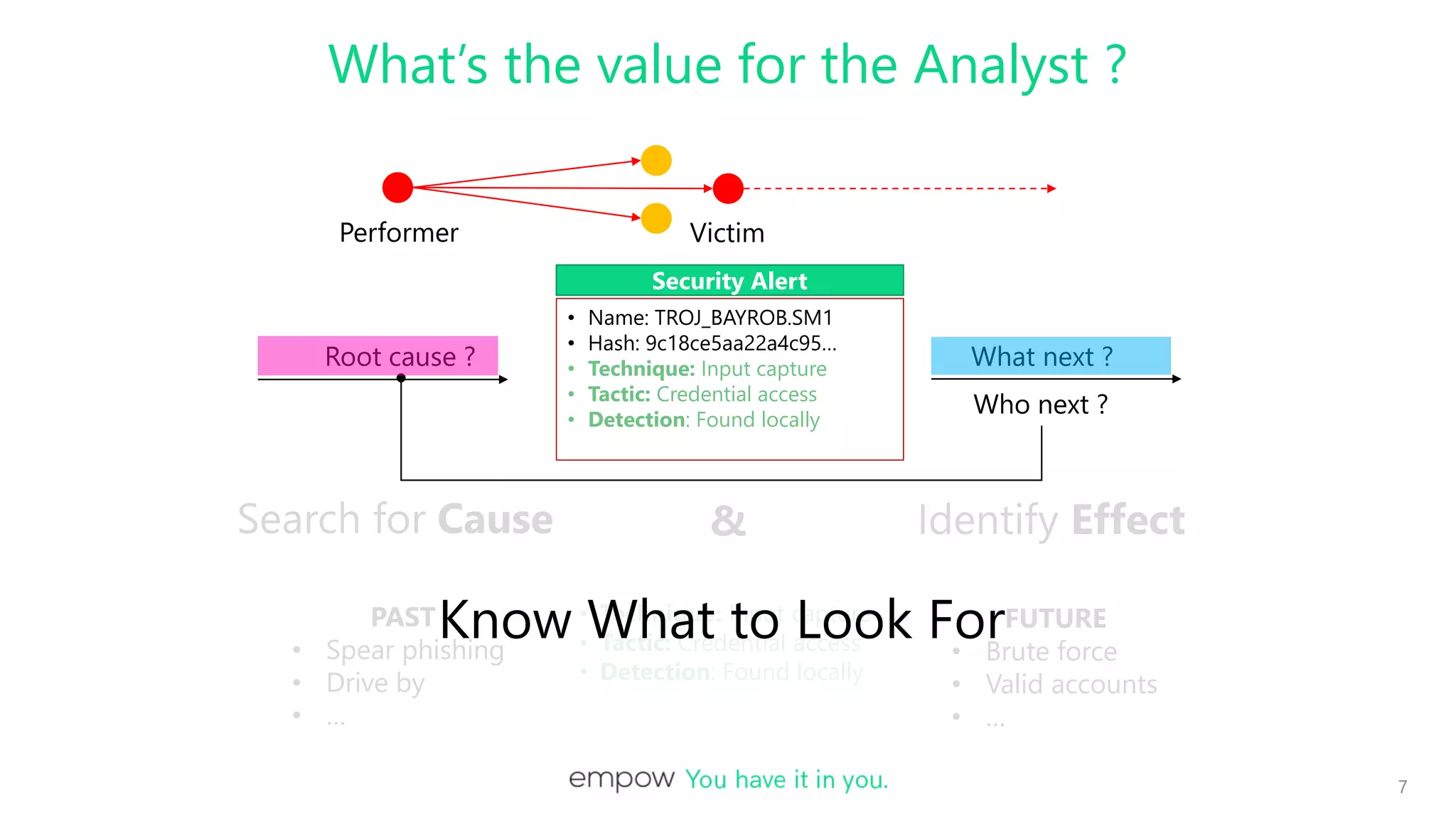
• Name: TROJ_BAYROB.SM1
• Hash: 9c18ce5aa22a4c95…
• Description: Malware/Trojan !
Malware Alert Log (Trend Micro)
• Name: TROJ_BAYROB.SM1
• Hash: 9c18ce5aa22a4c95…
• Technique: Input capture
• Tactic: Credential access
• Detection: Found locally
Advanced Enrichment
ECS
NLP Classification
What if there is NO Data For MITRE Classification ?
Microsoft threat description:
This threat can steal your user-names and passwords.
It can arrive on your PC as a malicious spam email attachment.
Checkpoint threat description:
Trojan which gathers passwords and system information or settings…
Some versions of this malware collect keystrokes…and spreads via
spam mail attachments or malicious websites.
Input
capture
• Name: TROJ_BAYROB.SM1
• Hash: 9c18ce5aa22a4c95…
• Technique: ???
• Tactic: ???
• Detection: Found locally
Threat Intelligence Feeds
[Name: TROJ_BAYROB.SM1 ; Hash: 9c18ce5aa22a4c95…]
Future effects
Past cause](https://image.slidesharecdn.com/injectingattackinteltols-rev7-201002162912/75/EmPOW-Integrating-Attack-Behavior-Intelligence-into-Logstash-Plugins-10-2048.jpg)