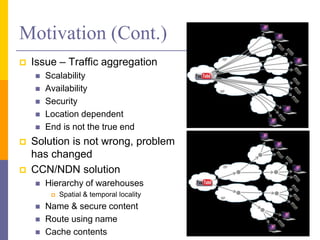
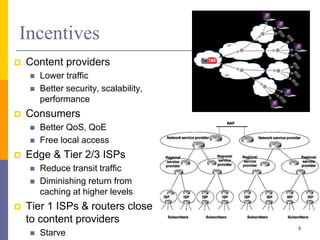
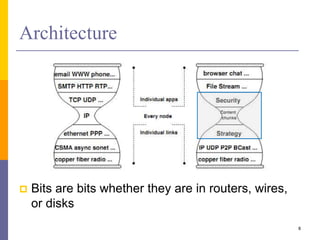
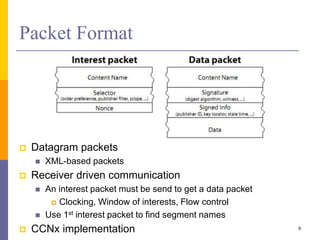
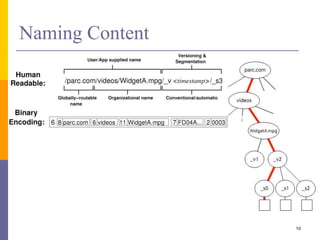
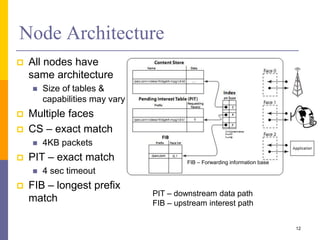
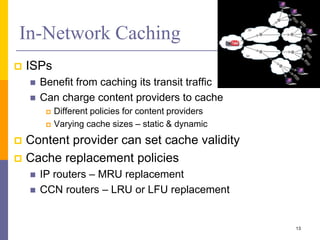
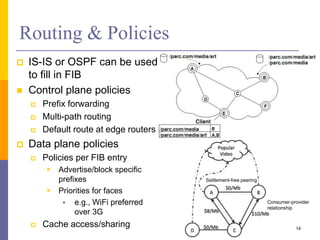
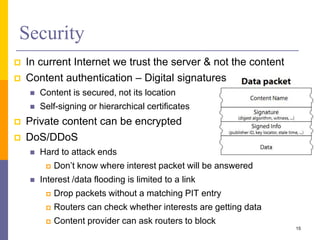
Content-Centric Networking (CCN) is a new approach that moves from addressing end systems to naming content directly. This allows content to be cached within the network close to consumers for improved performance and reduces traffic by satisfying multiple requests from the same cached copy. CCN uses hierarchical content names, in-network caching, and interest and data packet types to enable content retrieval and routing. The architecture has in-network caching, no routing loops, and built-in security features to authenticate content.