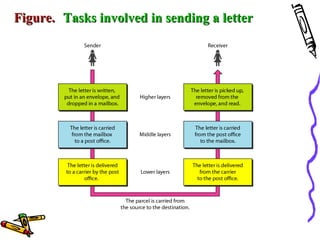
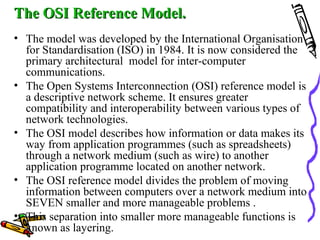
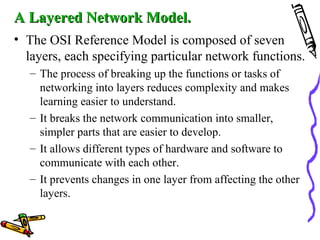
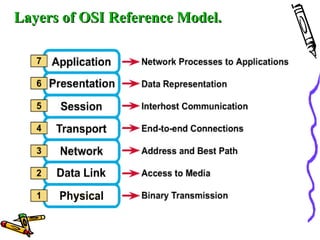
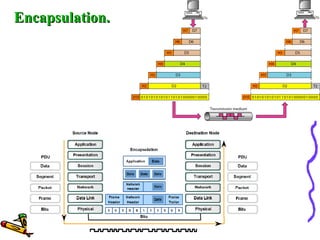
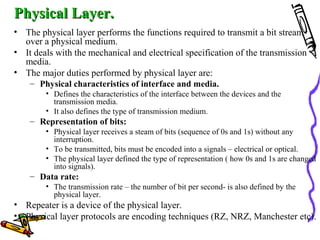
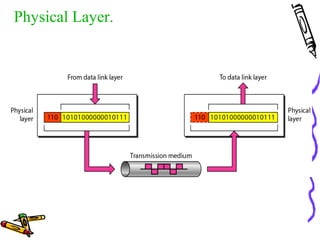
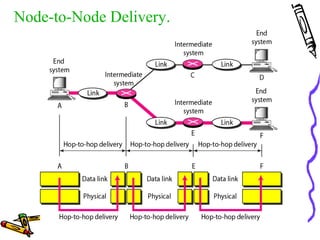
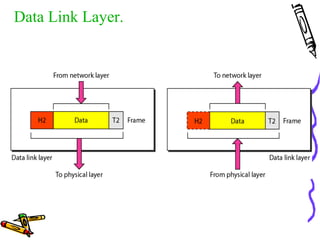
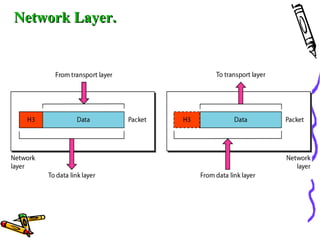
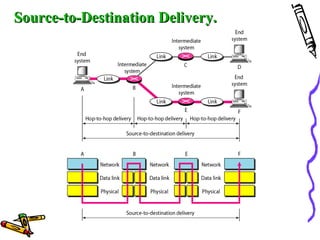
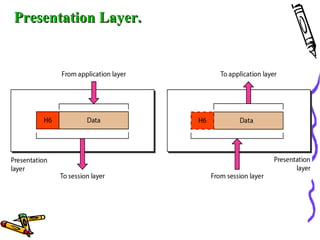
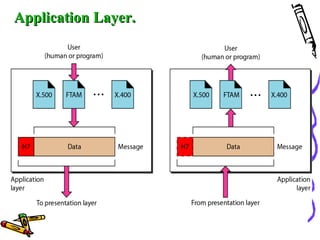
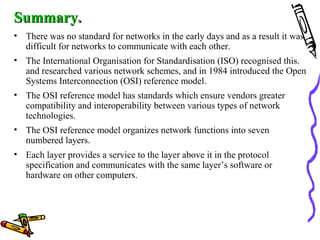
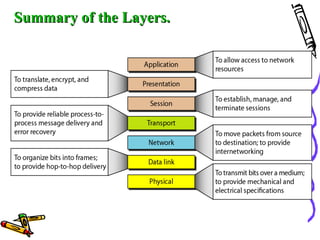
The document discusses the OSI Reference Model, which divides networking functions into 7 layers - physical, data link, network, transport, session, presentation, and application layer. Each layer has distinct responsibilities and provides services to the layer above it. The model was developed by ISO to standardize network communication and ensure compatibility between different systems.