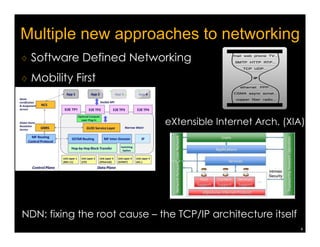
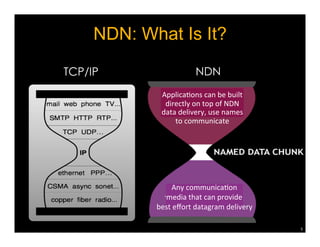
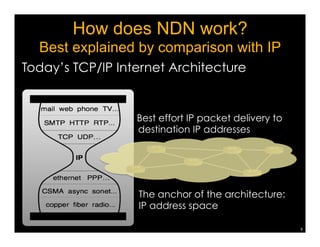
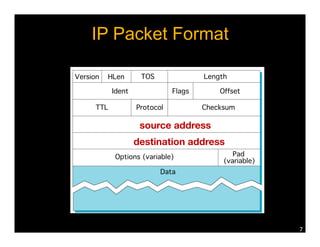
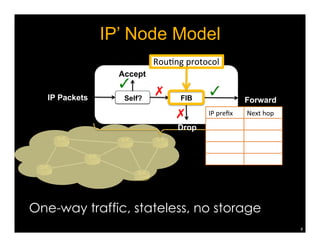
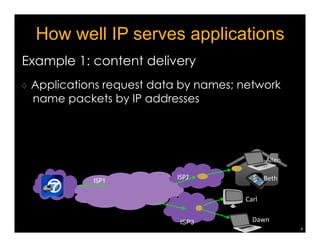
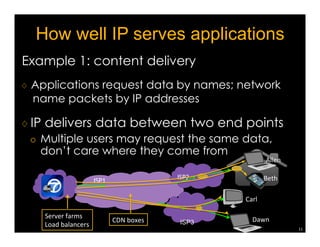
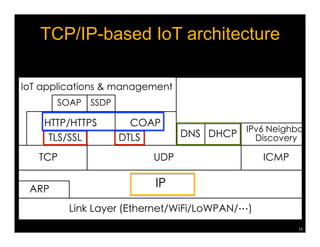
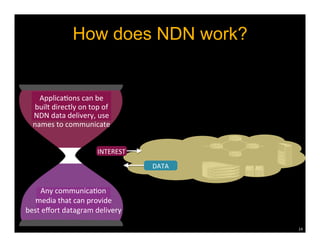
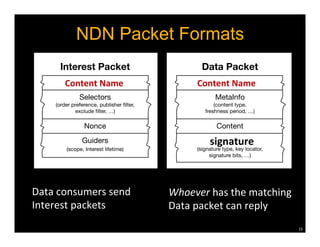
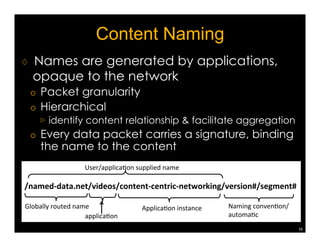
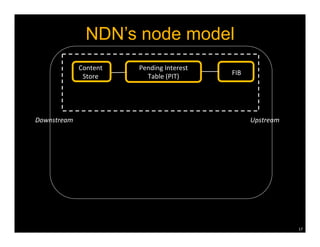
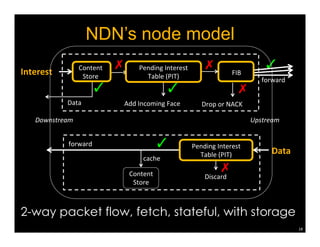
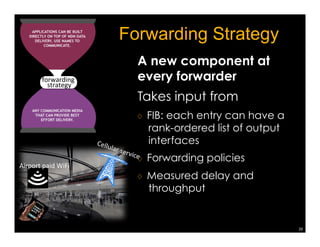
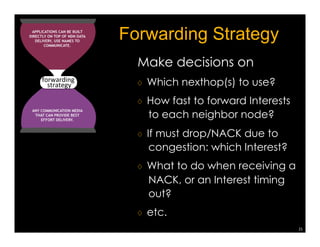
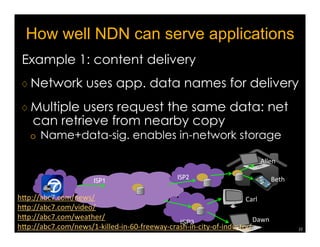
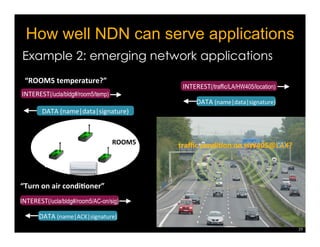
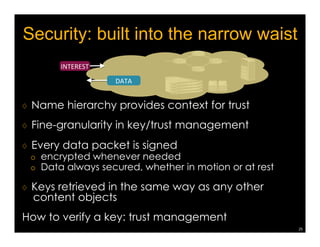
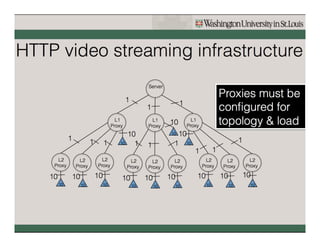
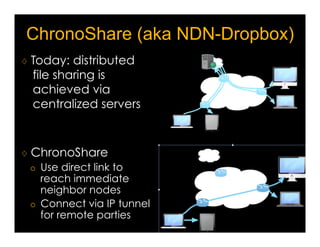
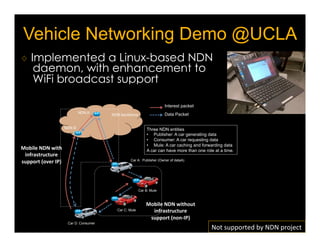
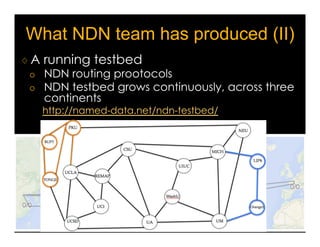
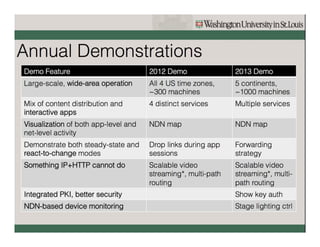
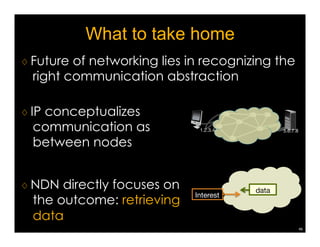
Named Data Networking (NDN) is a new approach to networking that emphasizes data retrieval by names instead of IP addresses, addressing key challenges of scalability, security, and enabling new applications. NDN's architecture allows for efficient data delivery and in-network storage, which can enhance performance for applications like content delivery and the Internet of Things. The document outlines the current status of NDN research, its applications, and the need for further community engagement to drive its development.