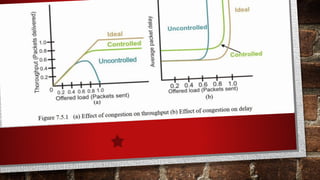
This document discusses computer networks and congestion control techniques. It provides information on routing algorithms, causes of congestion, effects of congestion, and open-loop and closed-loop congestion control methods. Specifically, it describes the leaky bucket algorithm and token bucket algorithm for traffic shaping, and how they regulate data flow rates to prevent network congestion.