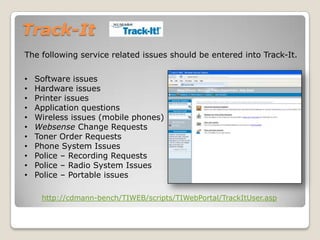
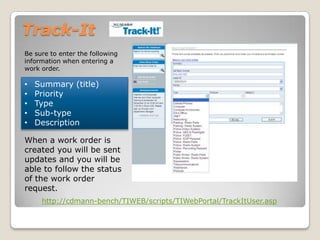
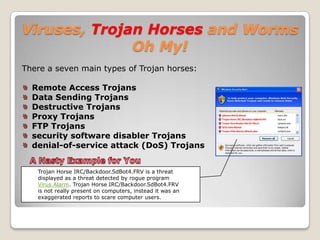
This document provides an agenda and information for an IT training session on security. The agenda includes covering Track-It, a tech blog, passwords, viruses, Trojan horses, worms, and spam. Details are given on properly using Track-It to log issues. Network security is discussed, including creating strong passwords and types of malware like viruses, Trojan horses, and worms. The training recommends keeping anti-virus software up-to-date and cautions against opening suspicious email attachments.