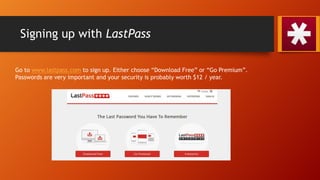
The document discusses the Heartbleed vulnerability and explains how password management tools like LastPass can help improve online security. It describes what the Heartbleed bug is, how it allows theft of sensitive information, and why unique, strong passwords are important to prevent attacks. The bulk of the document demonstrates how to set up a LastPass account and vault, generate secure passwords, organize accounts into folders, and access passwords across devices for a more secure digital life.