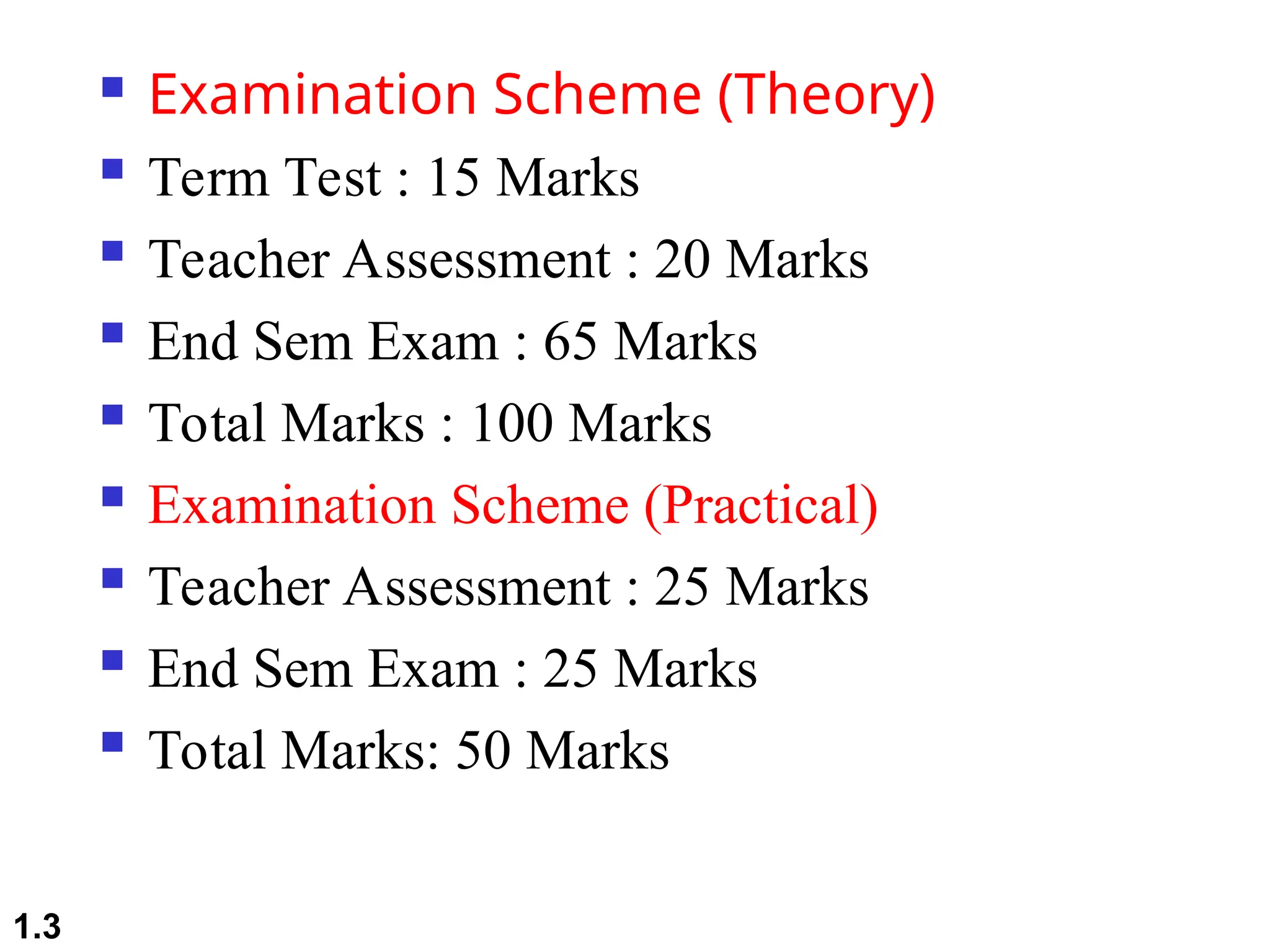
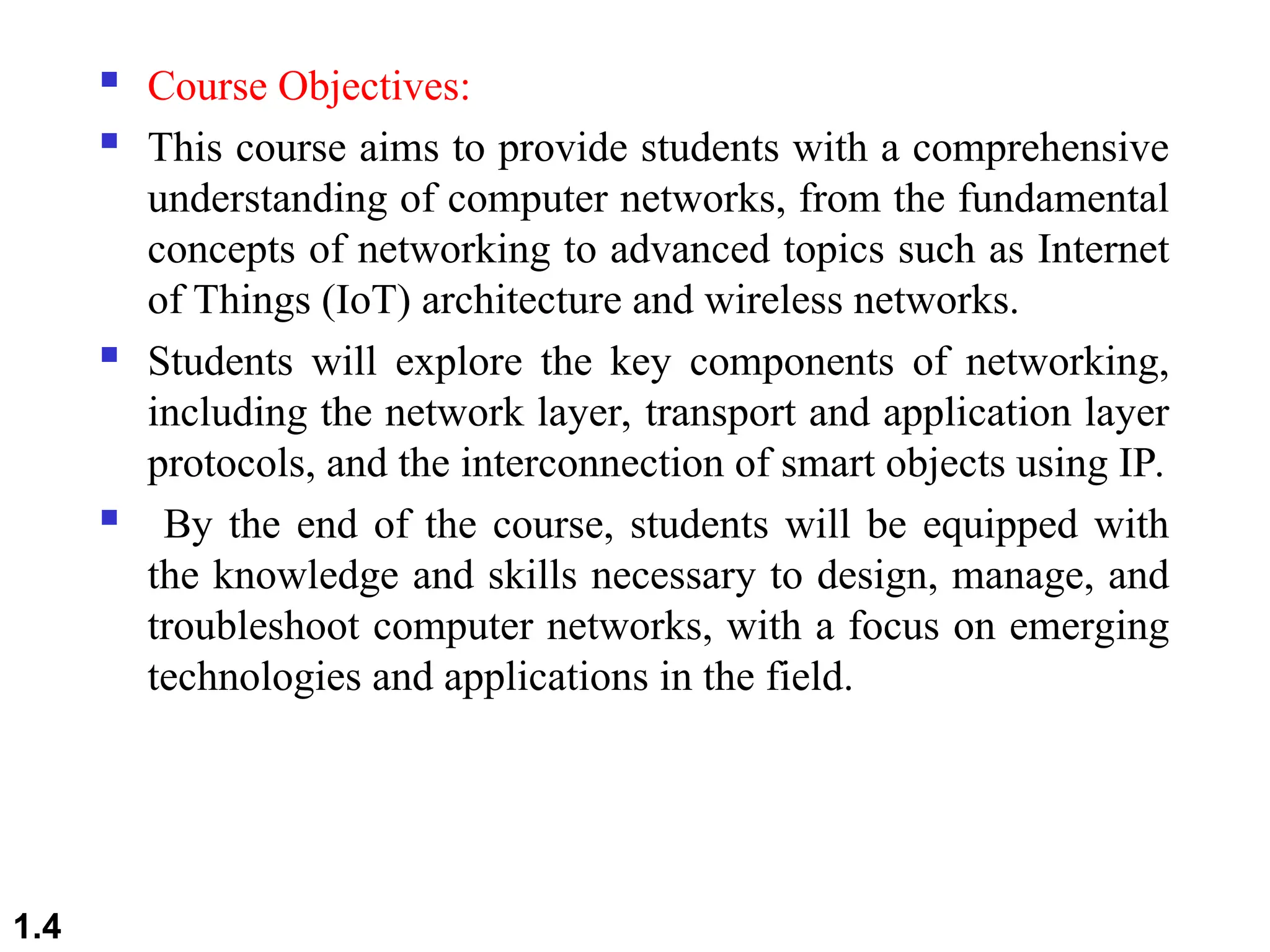
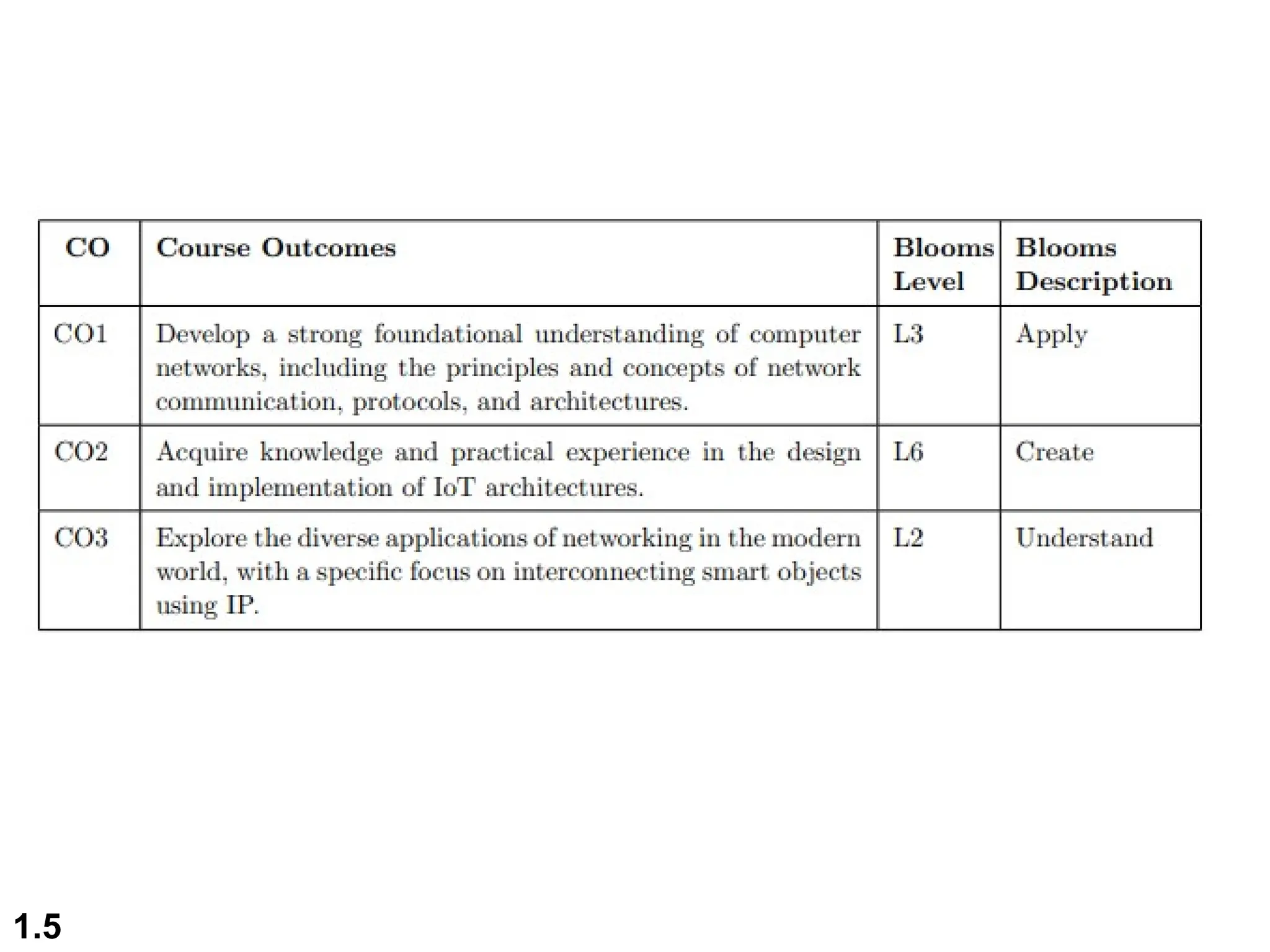
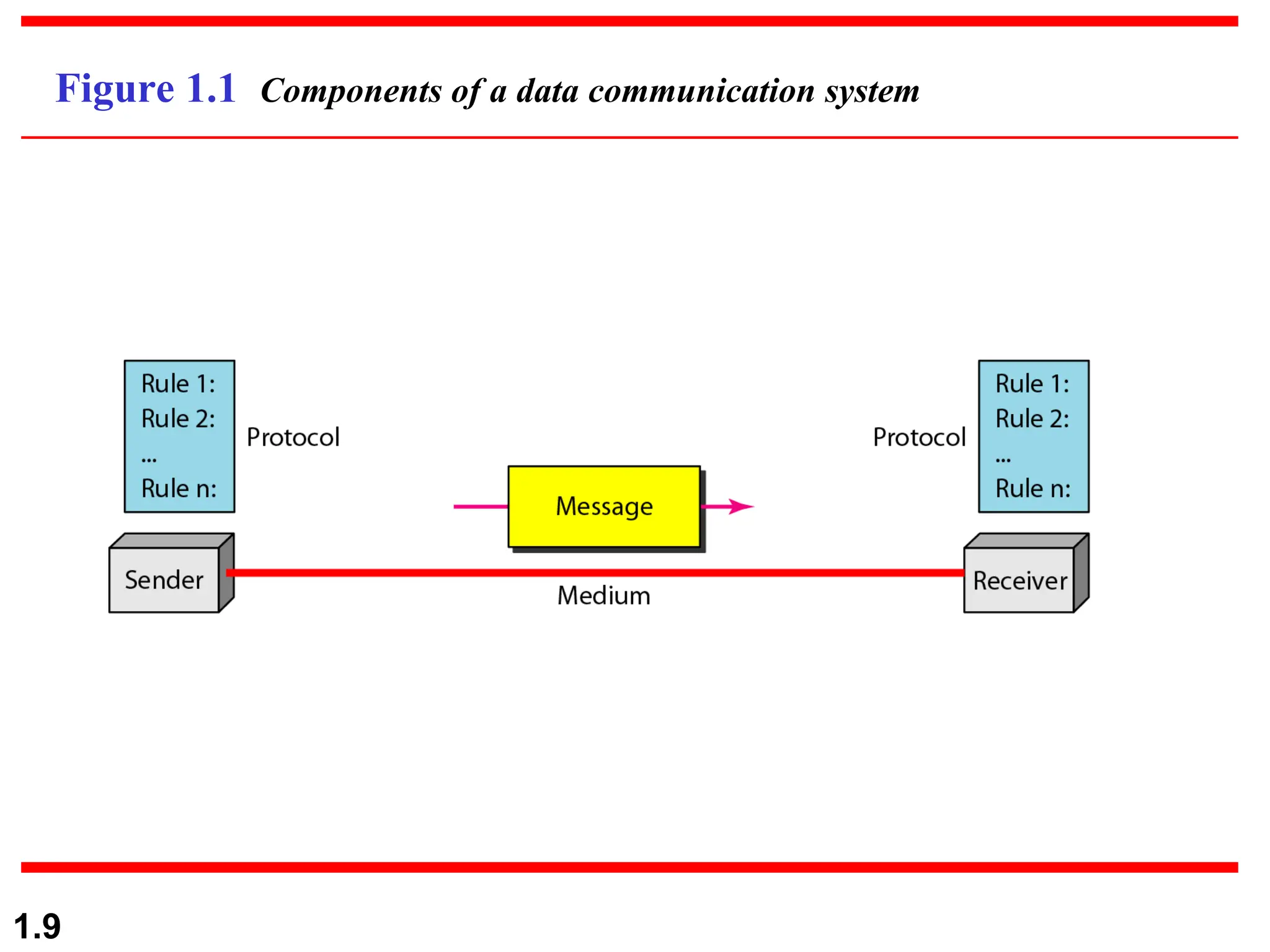
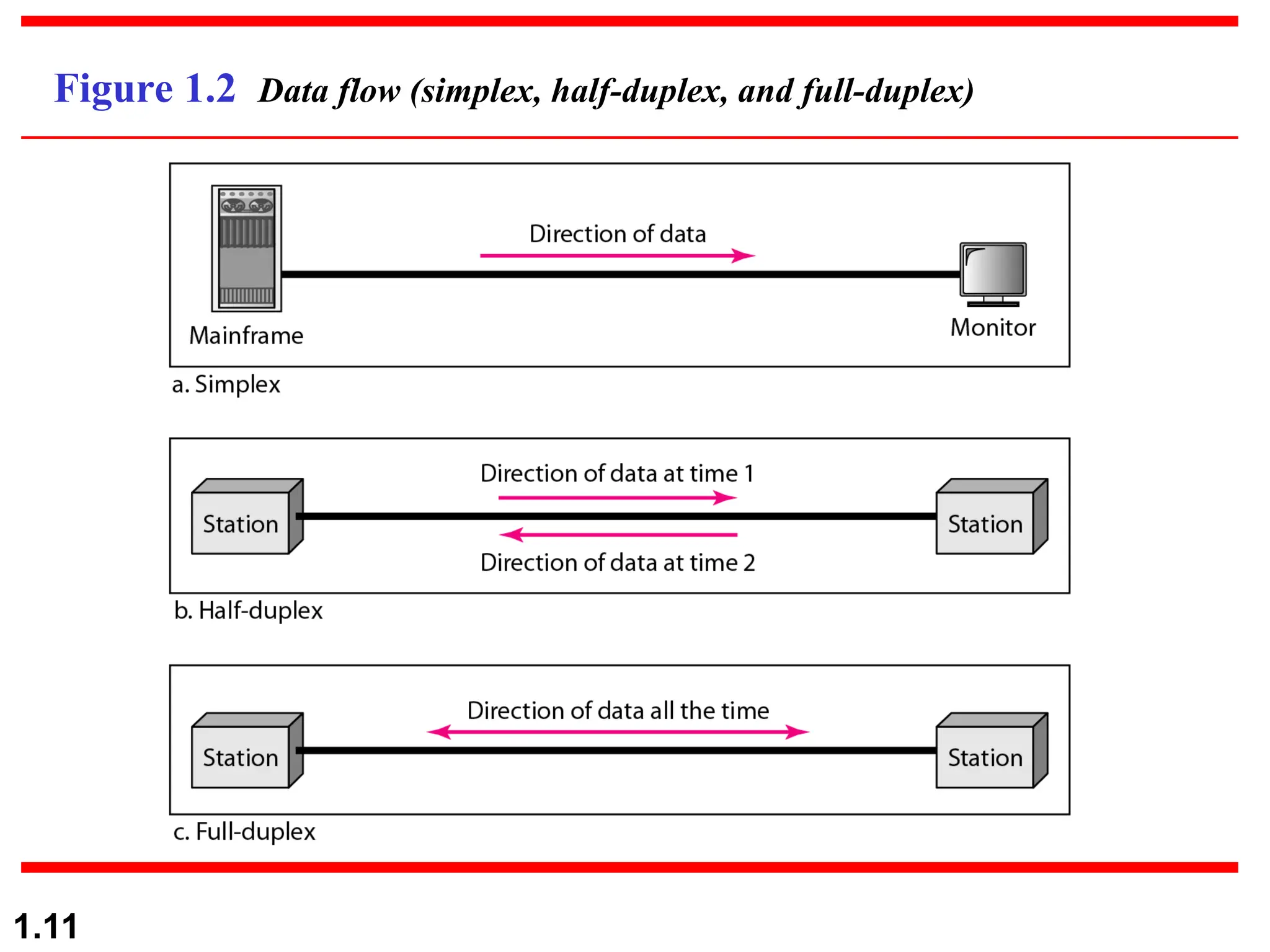
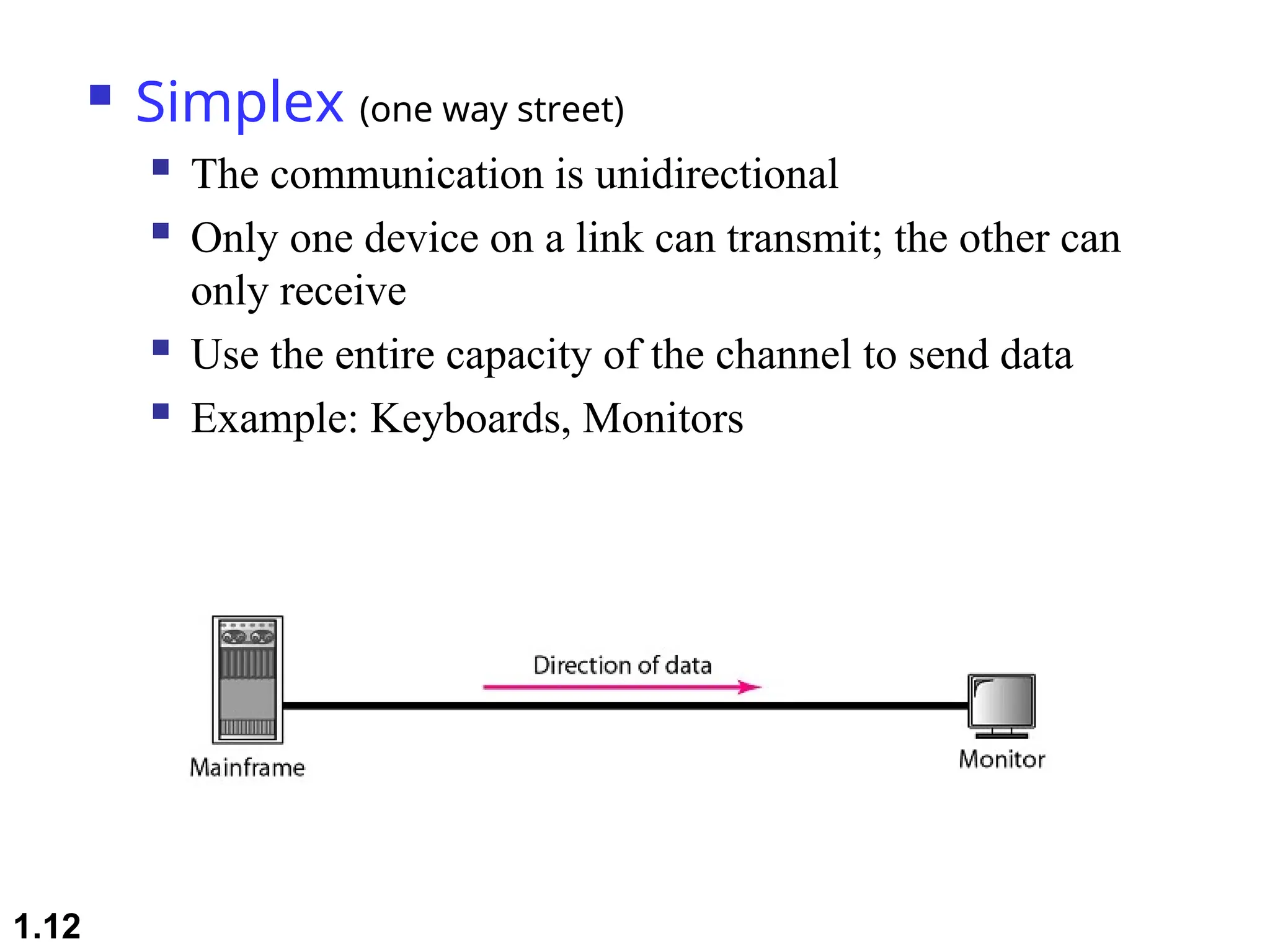
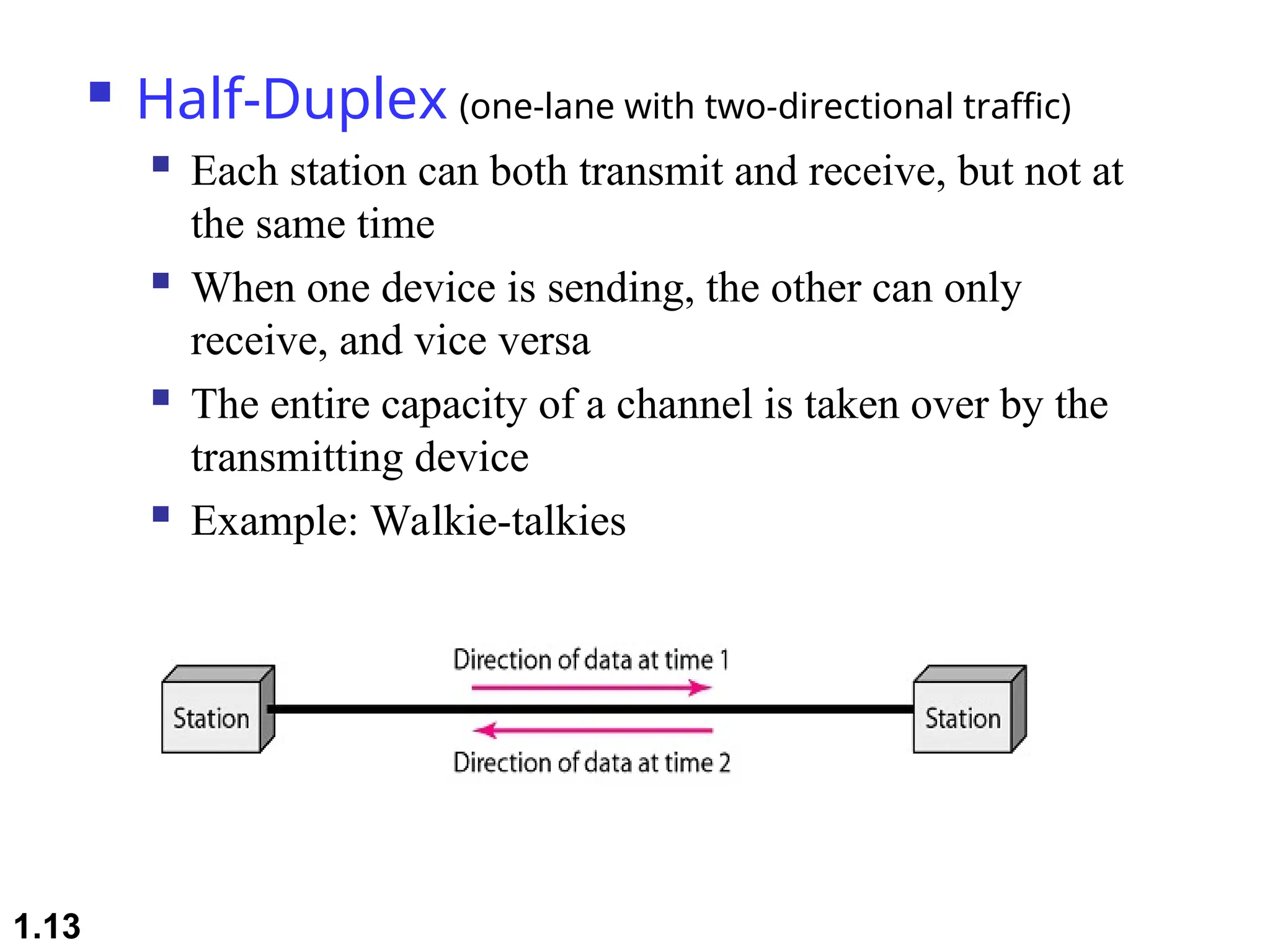
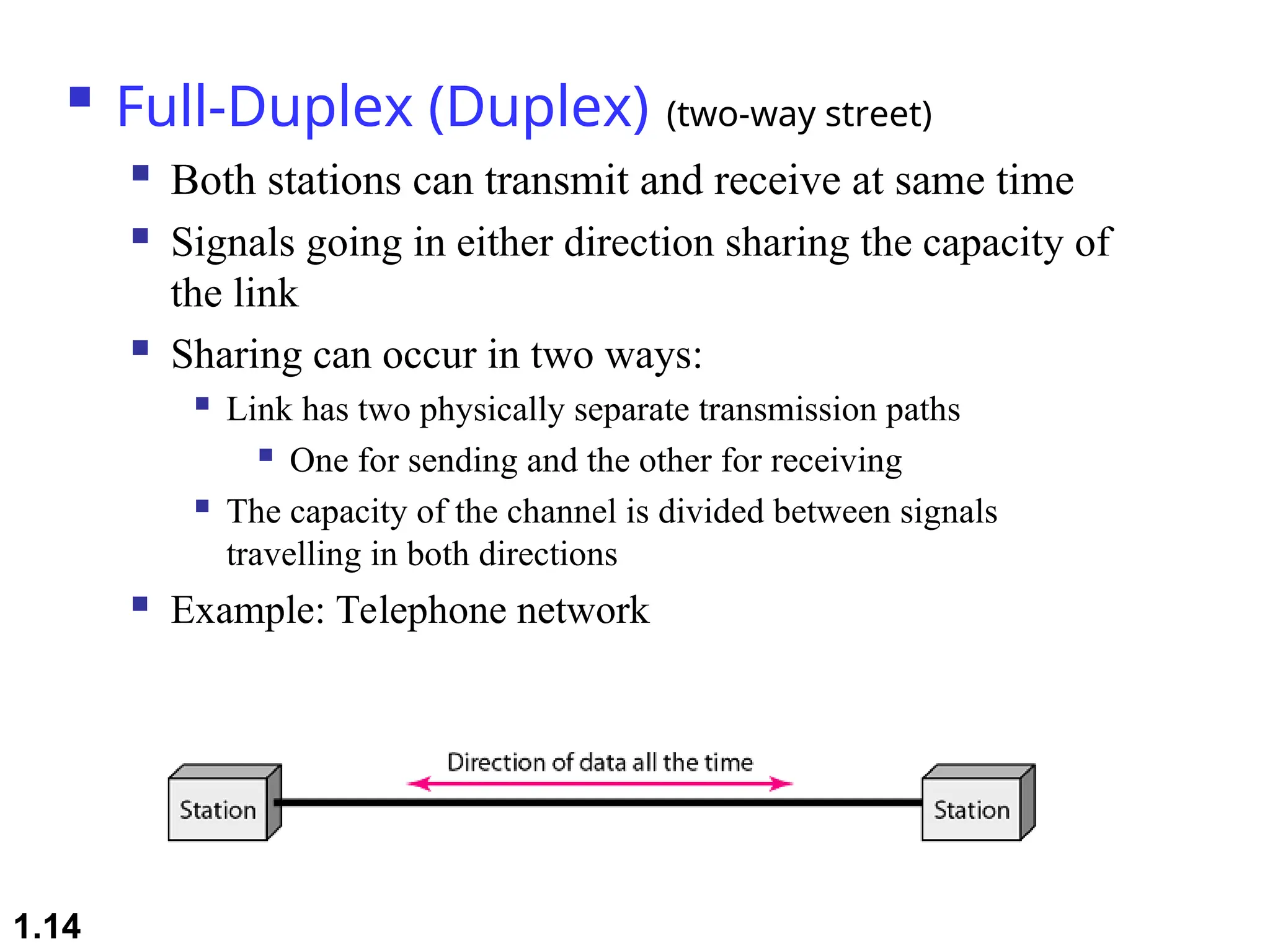
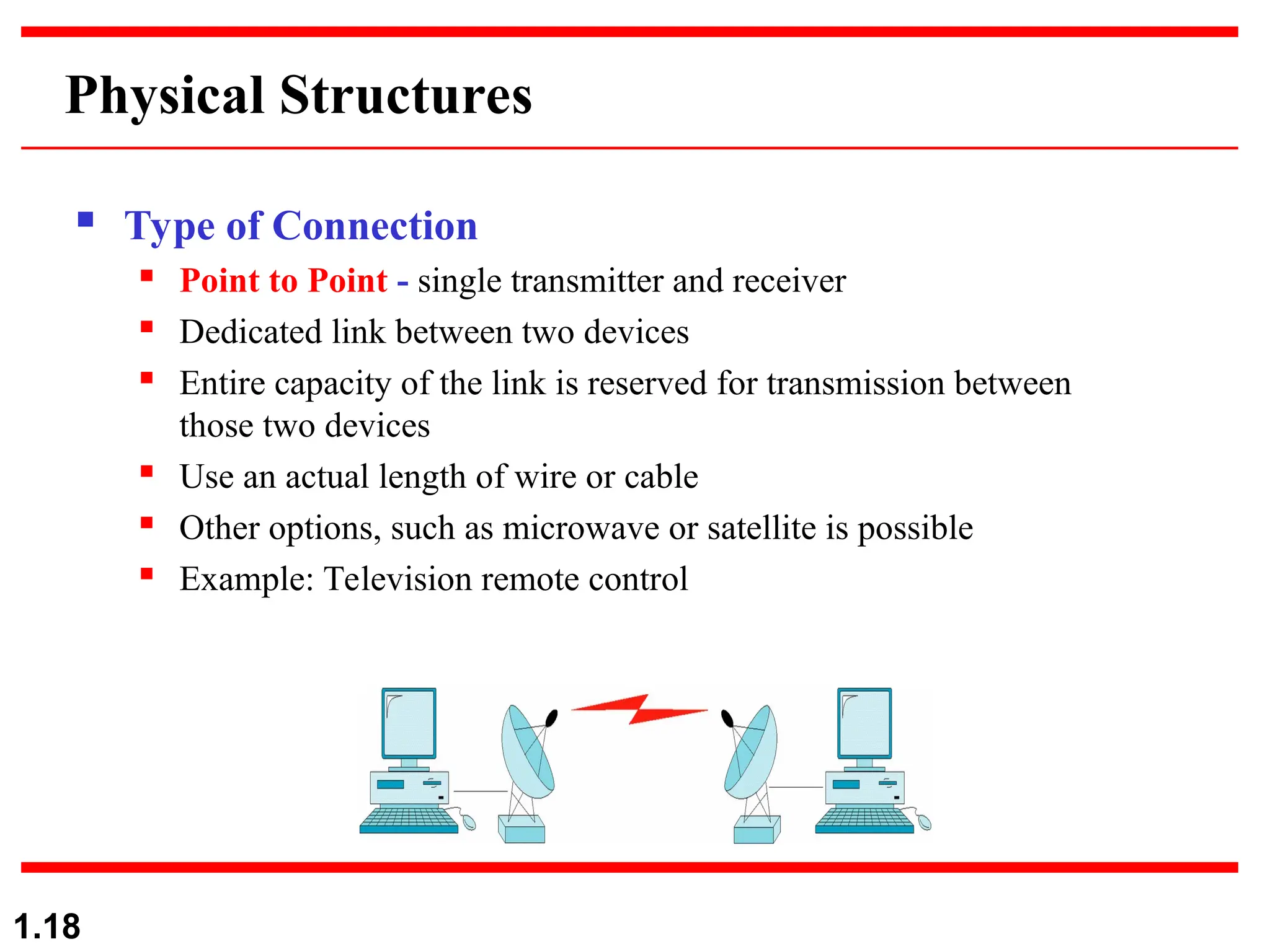
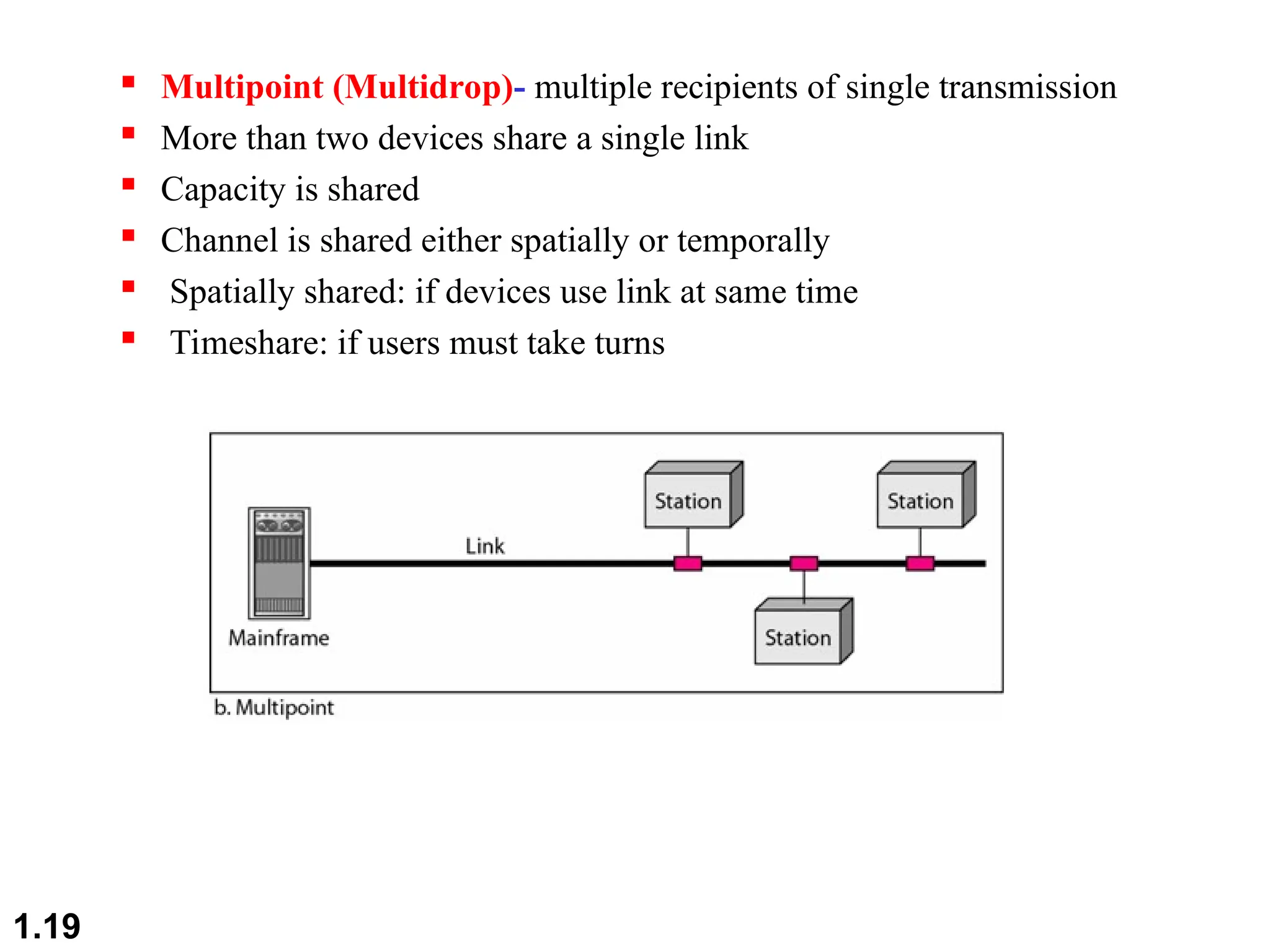
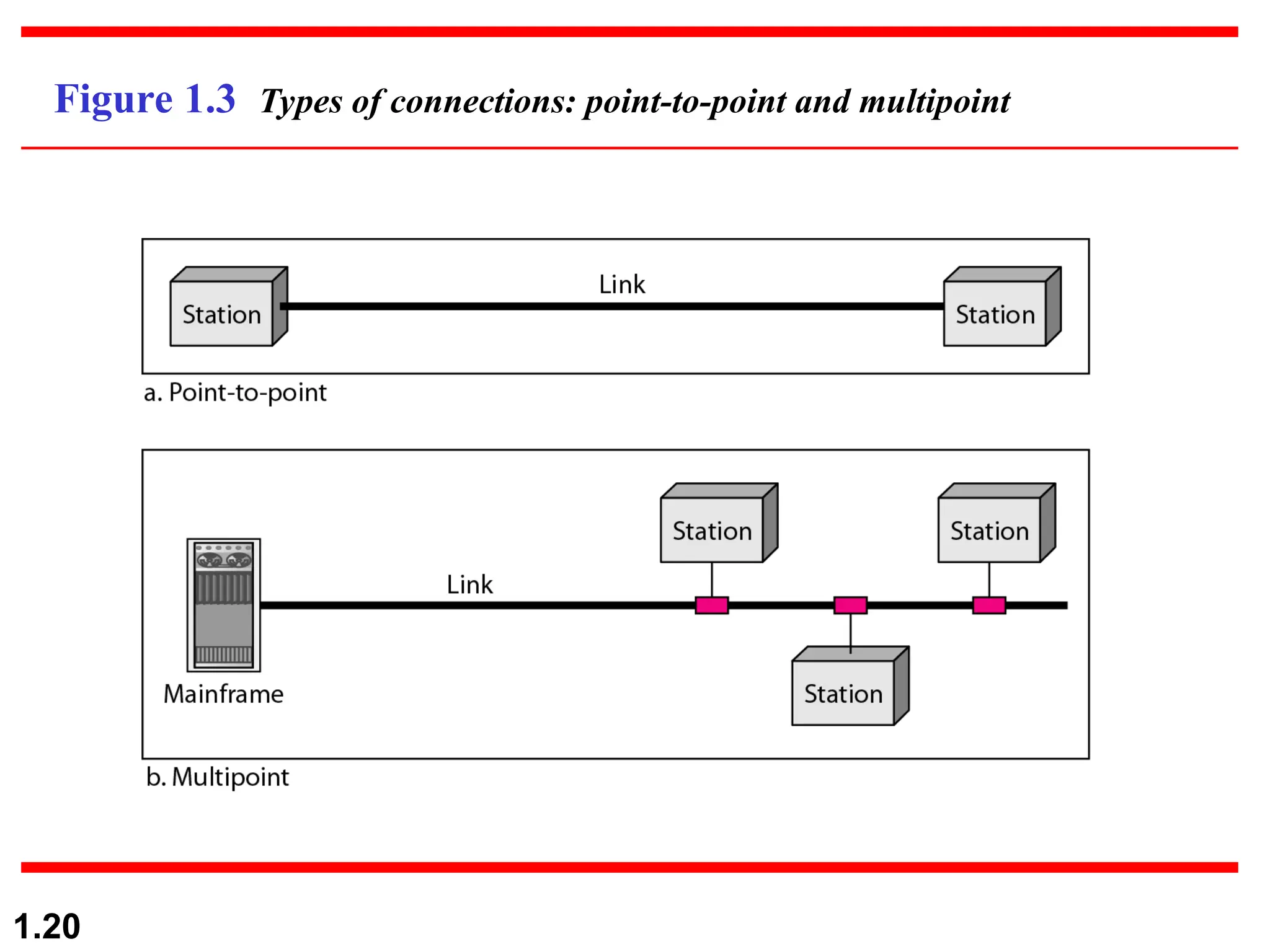
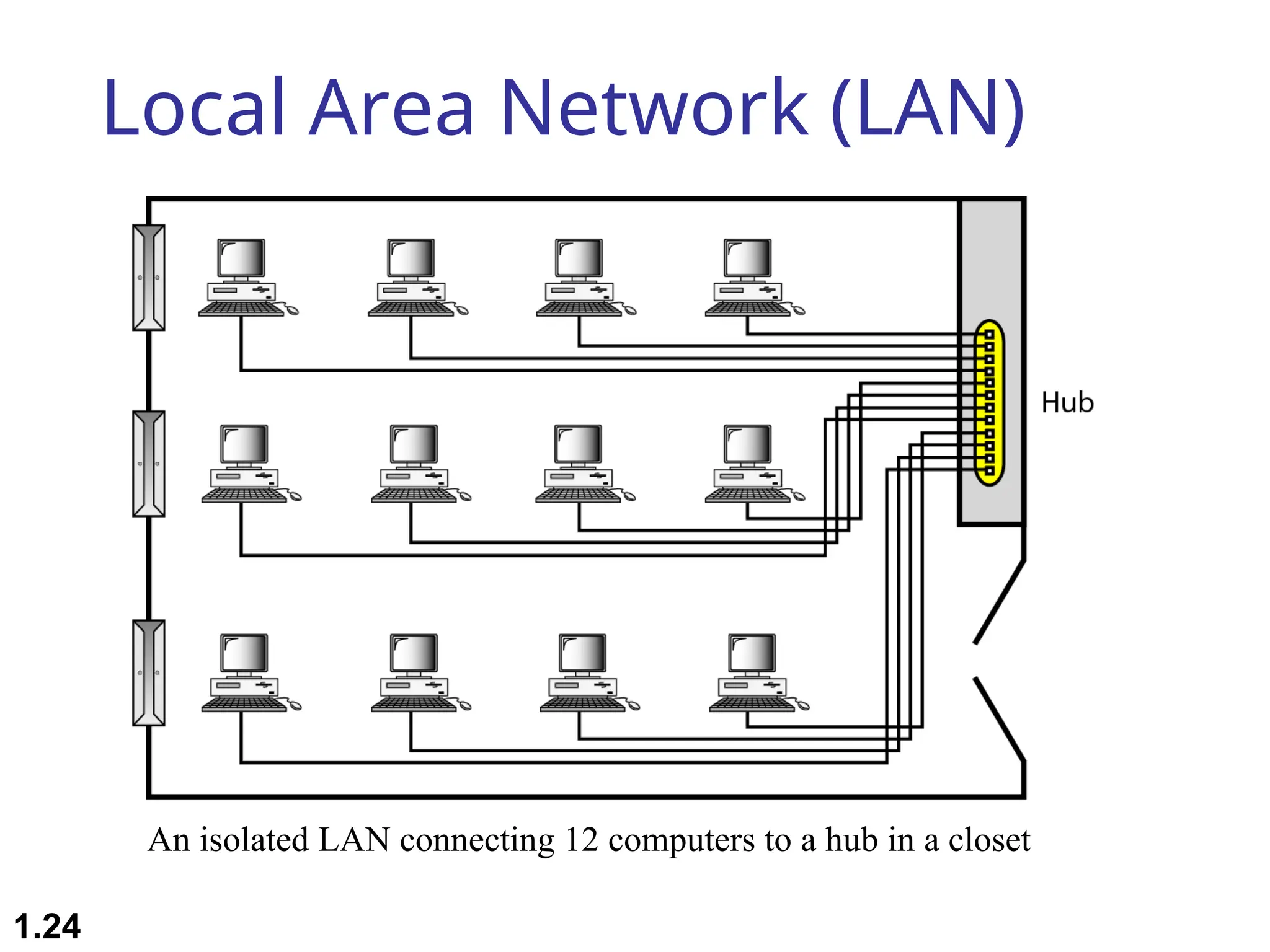
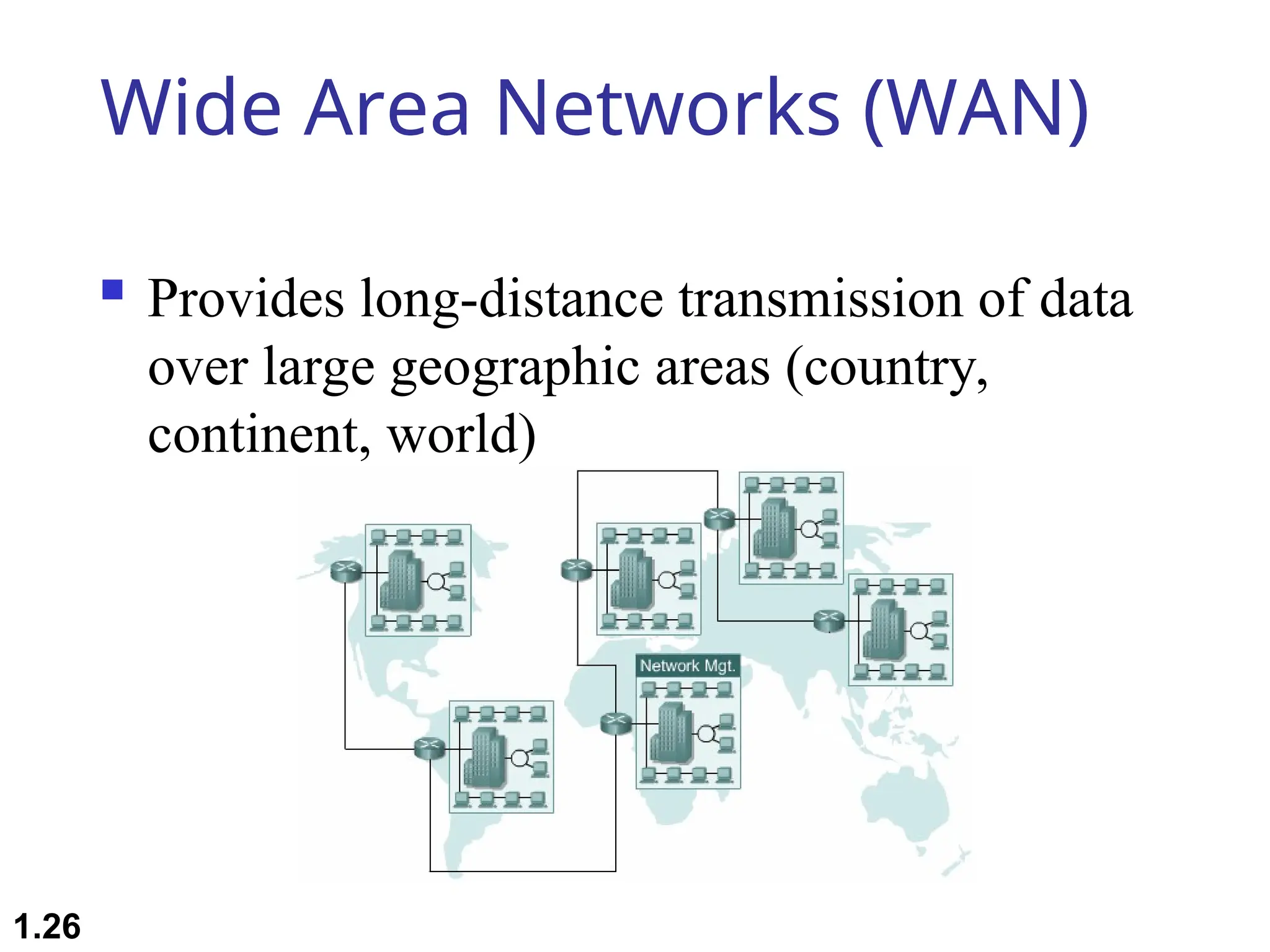
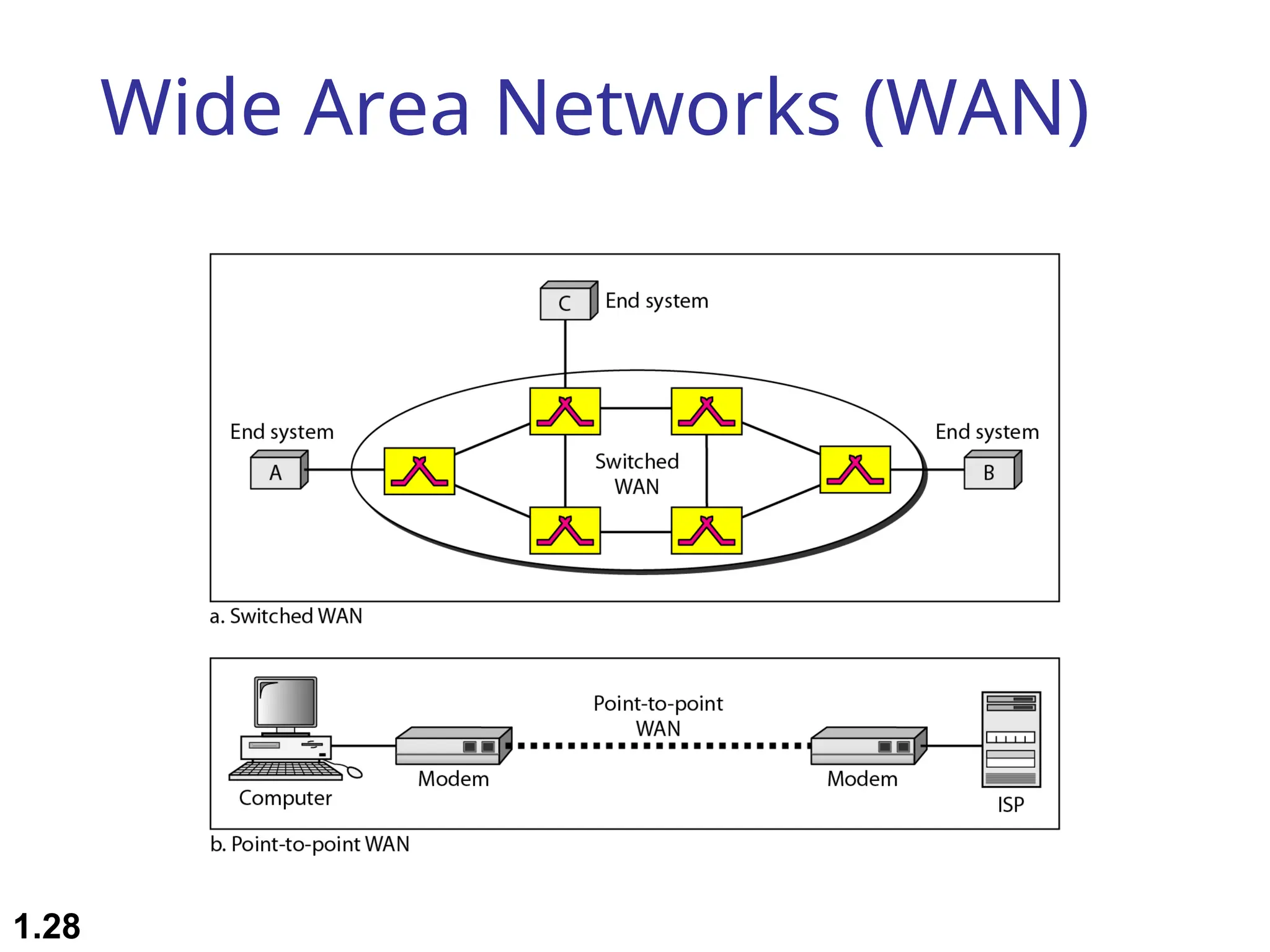
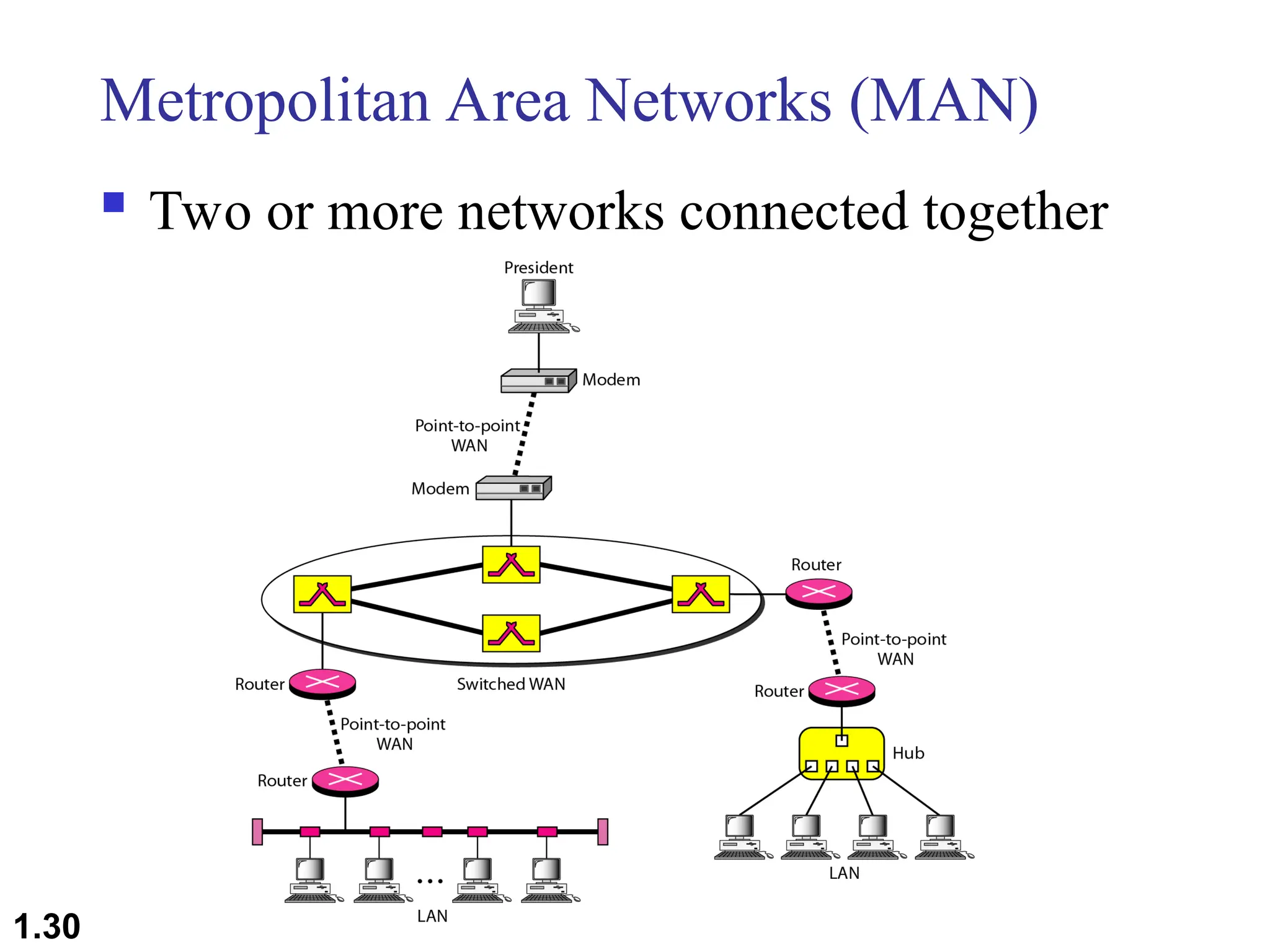
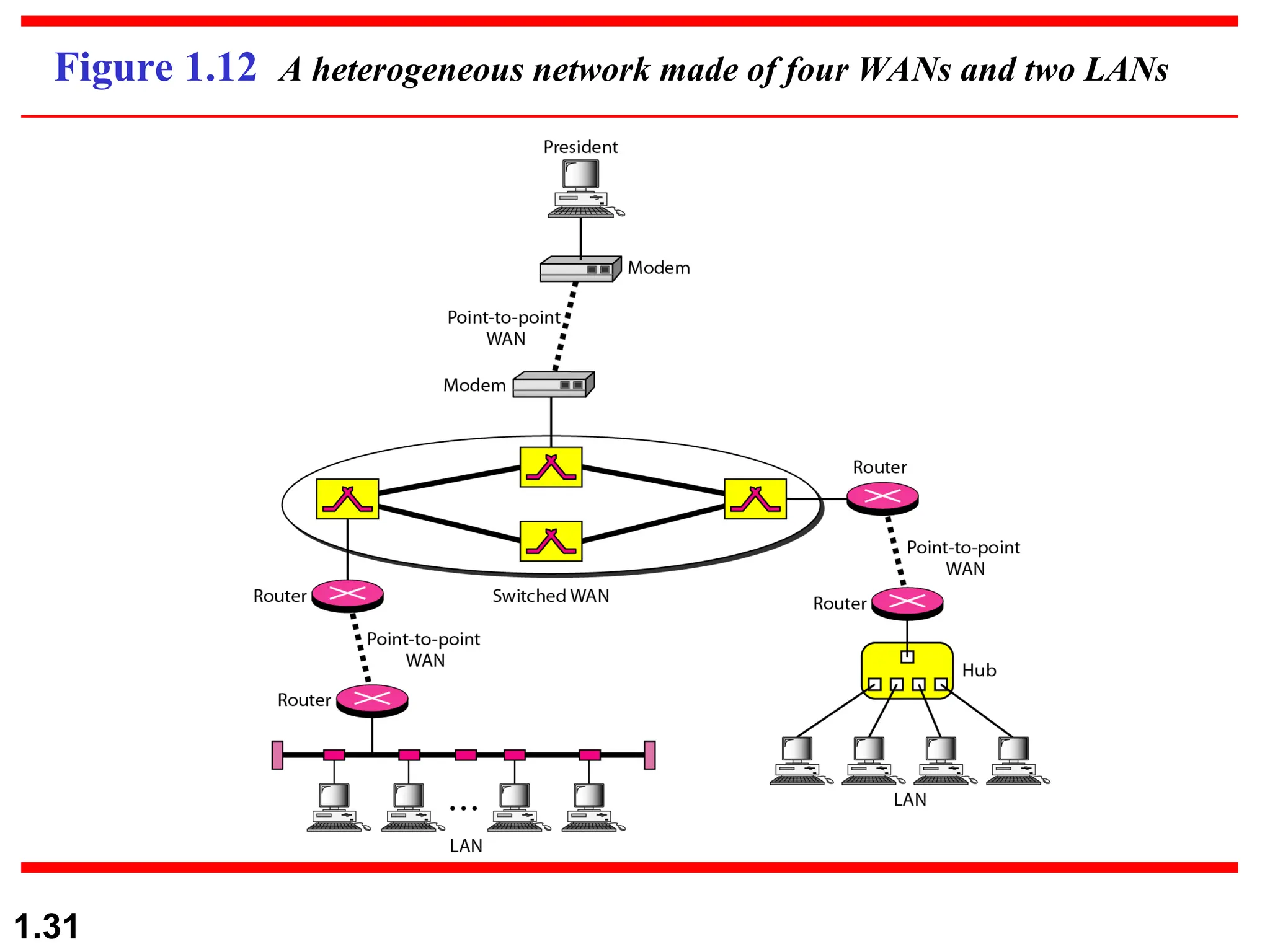
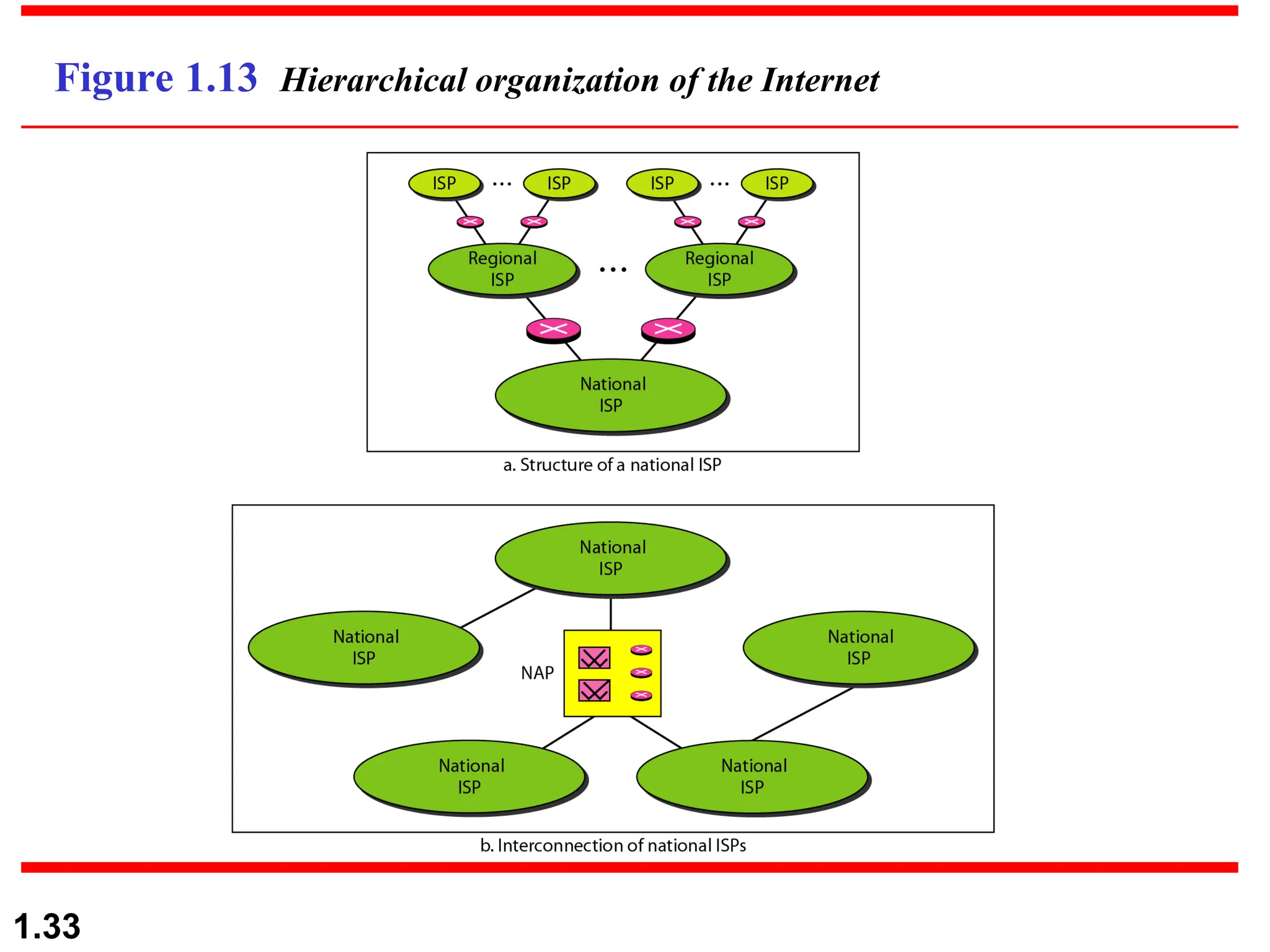
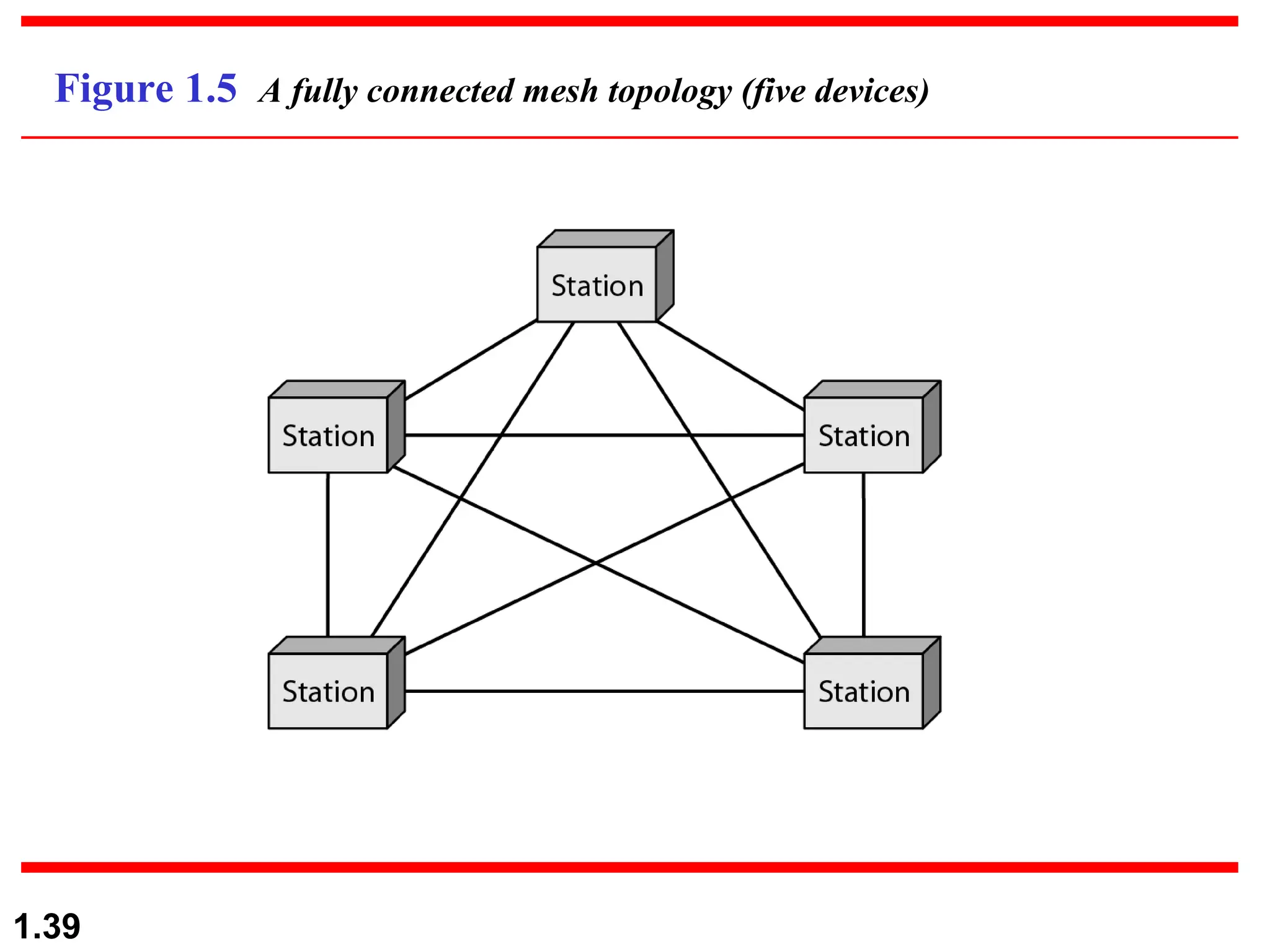
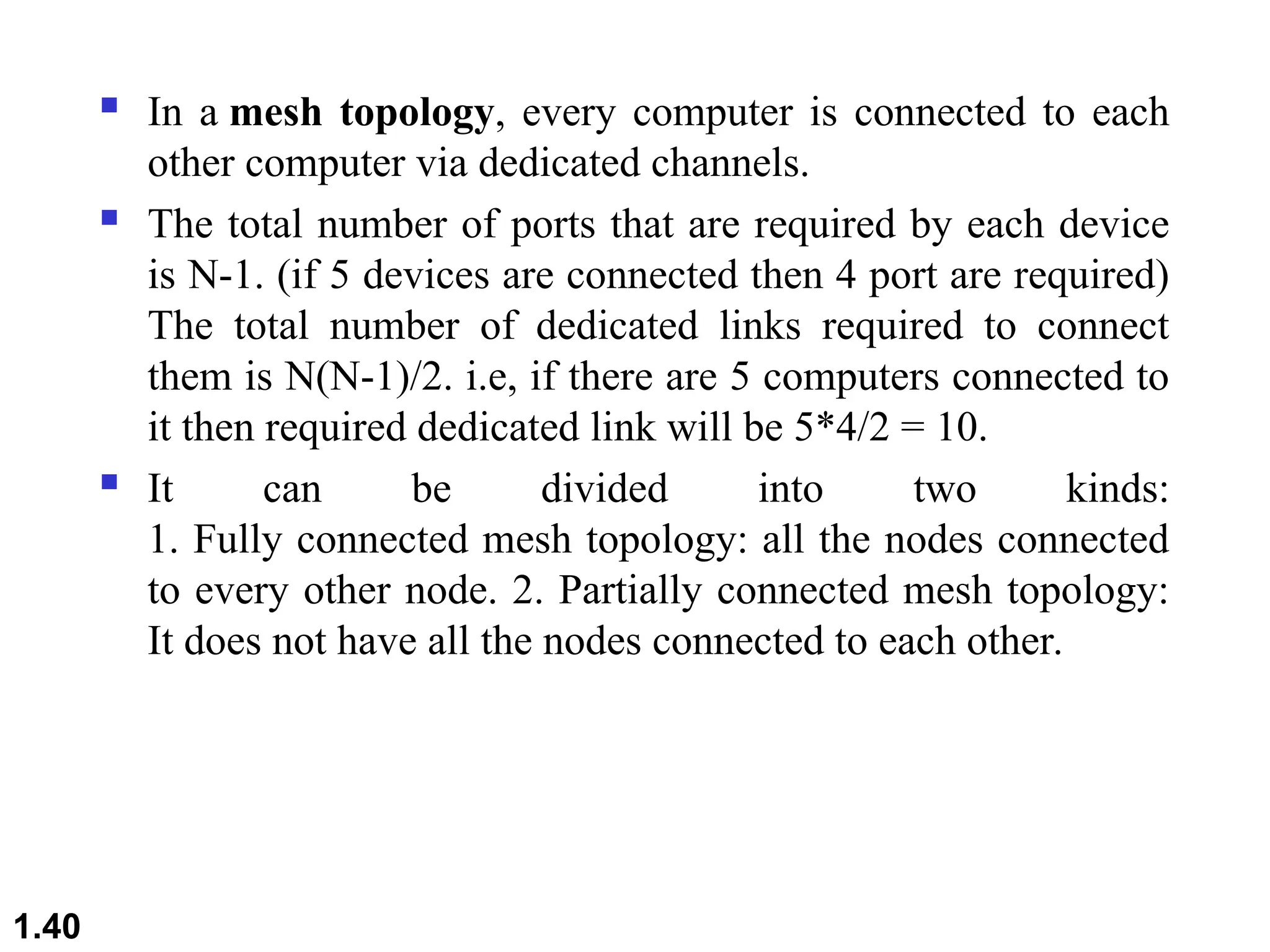
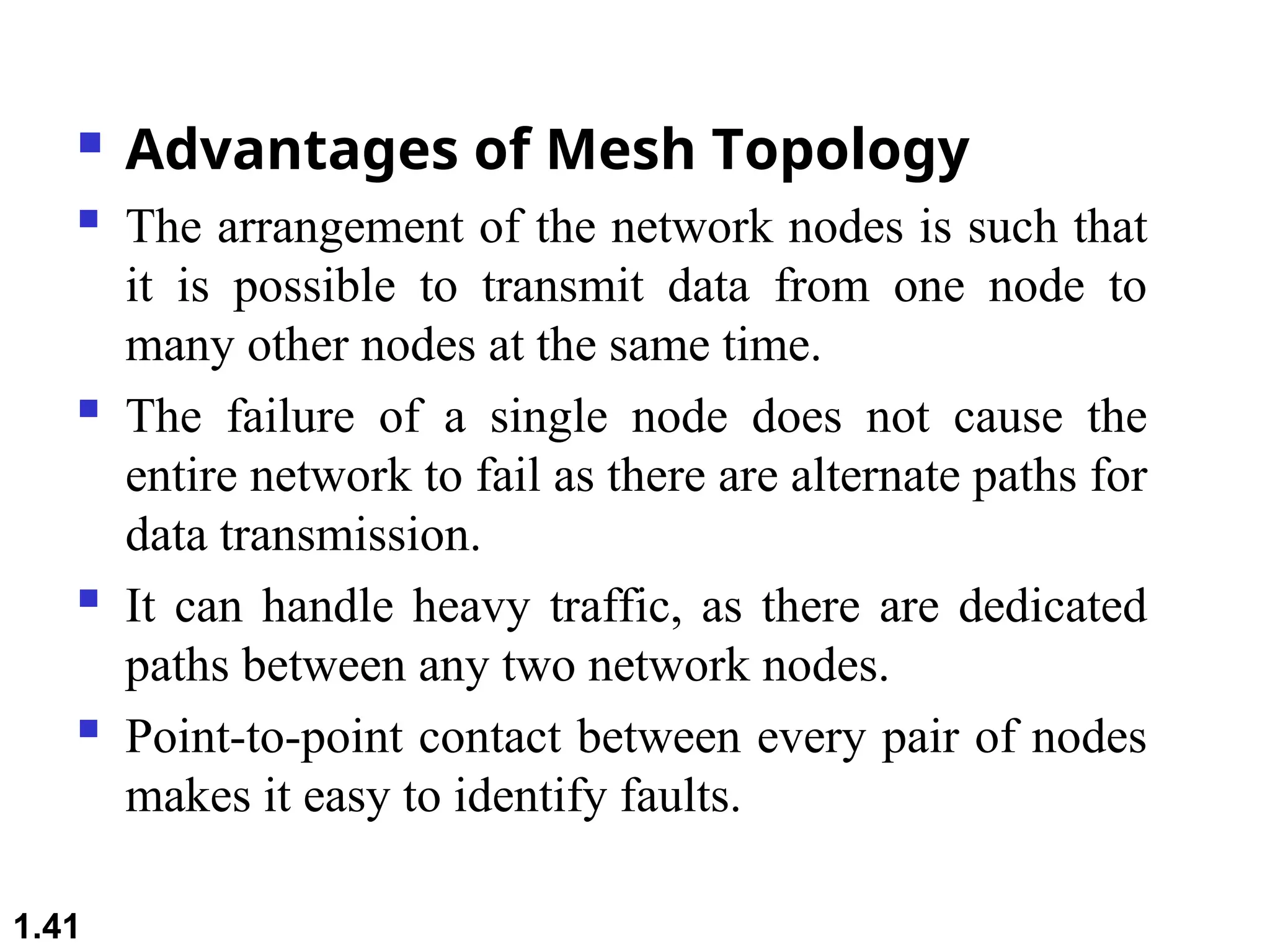
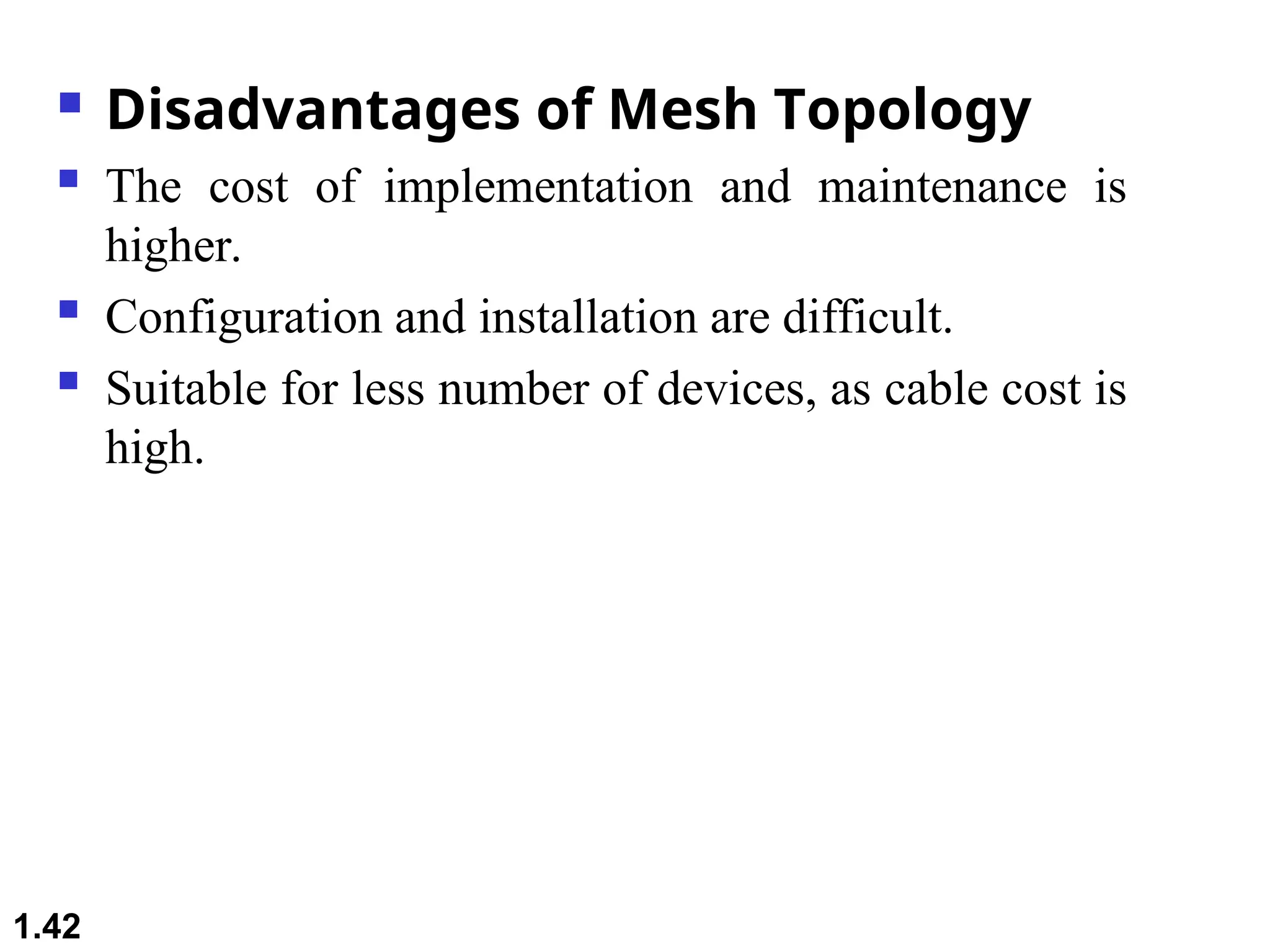
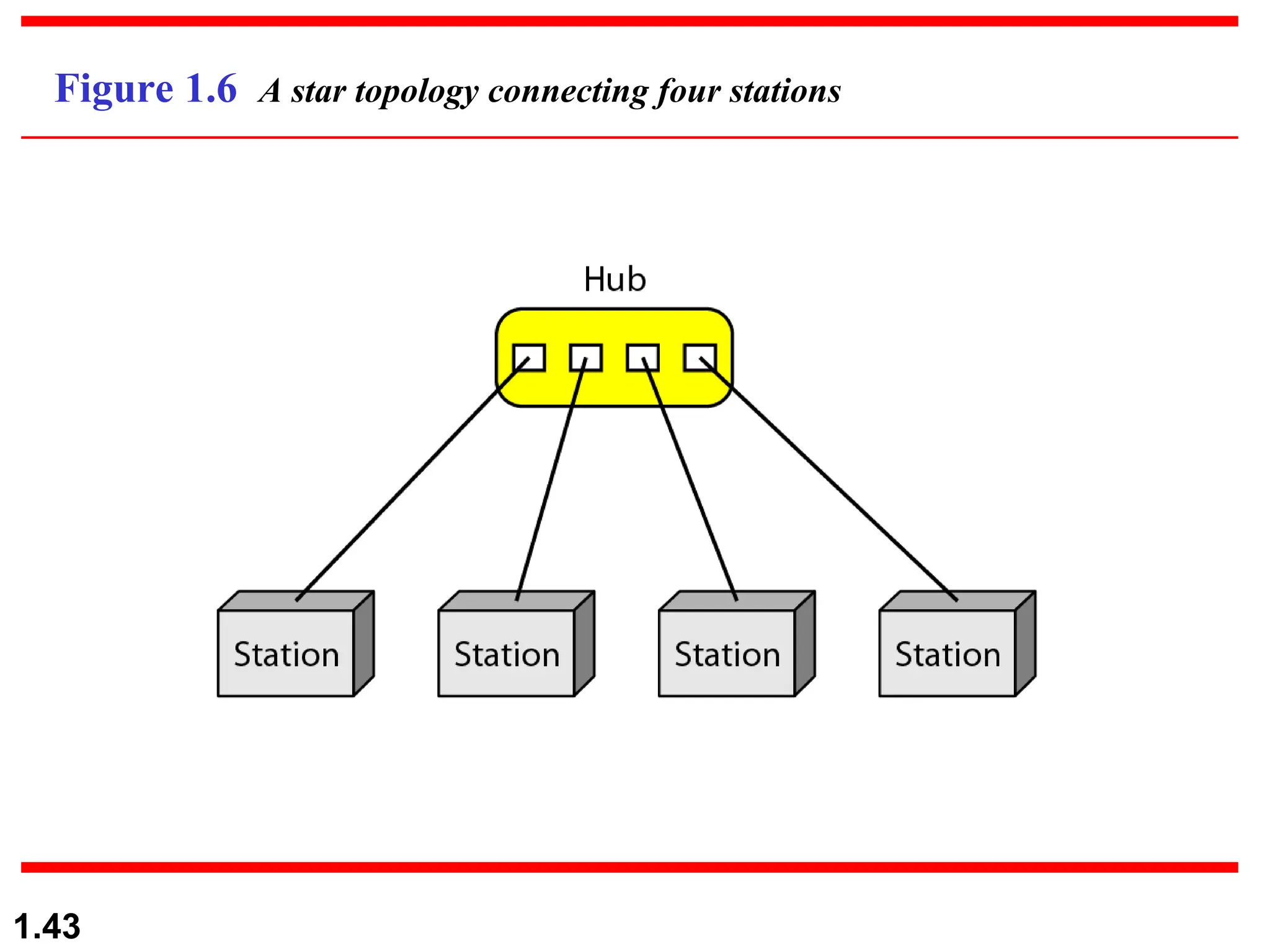
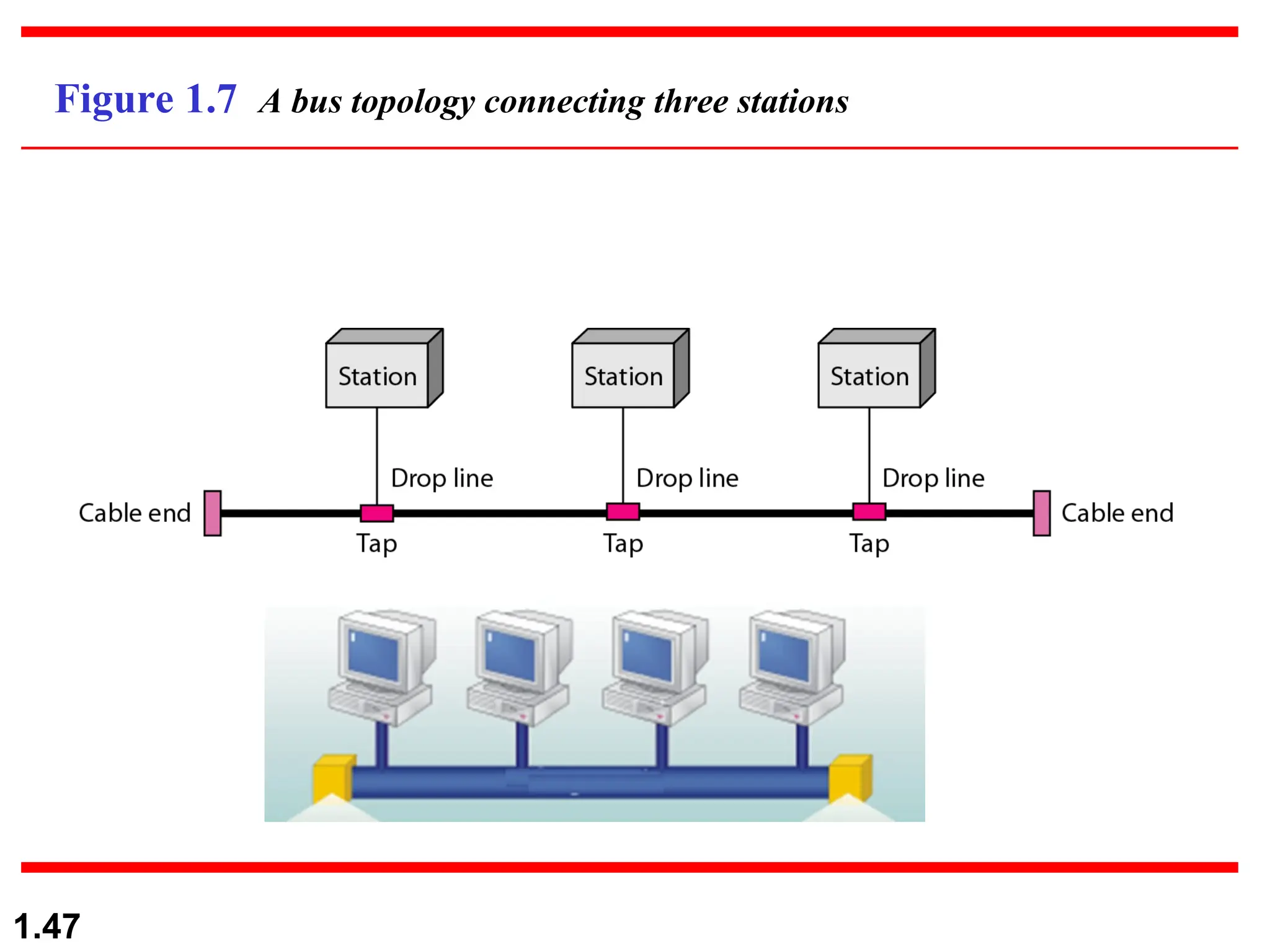
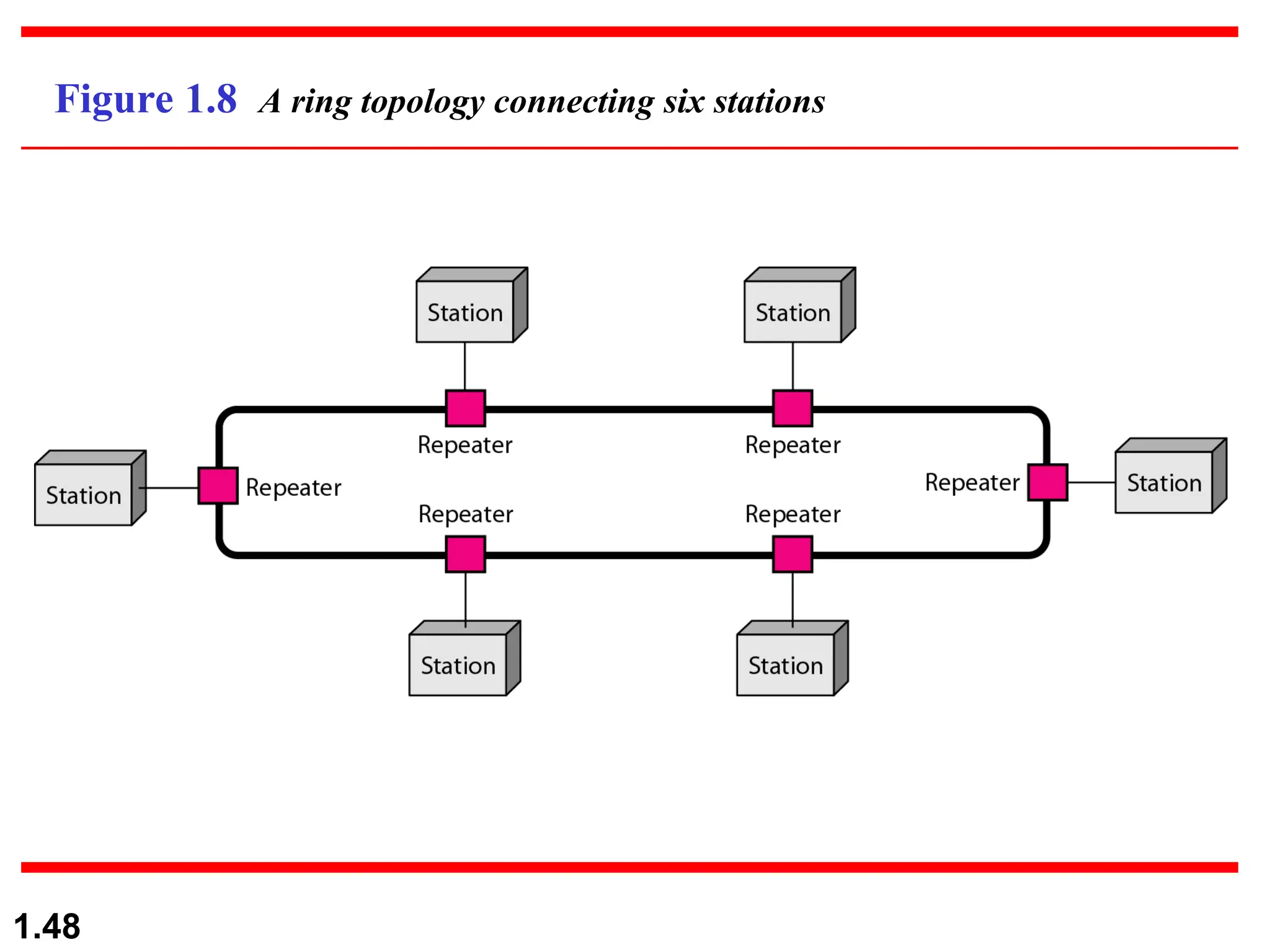
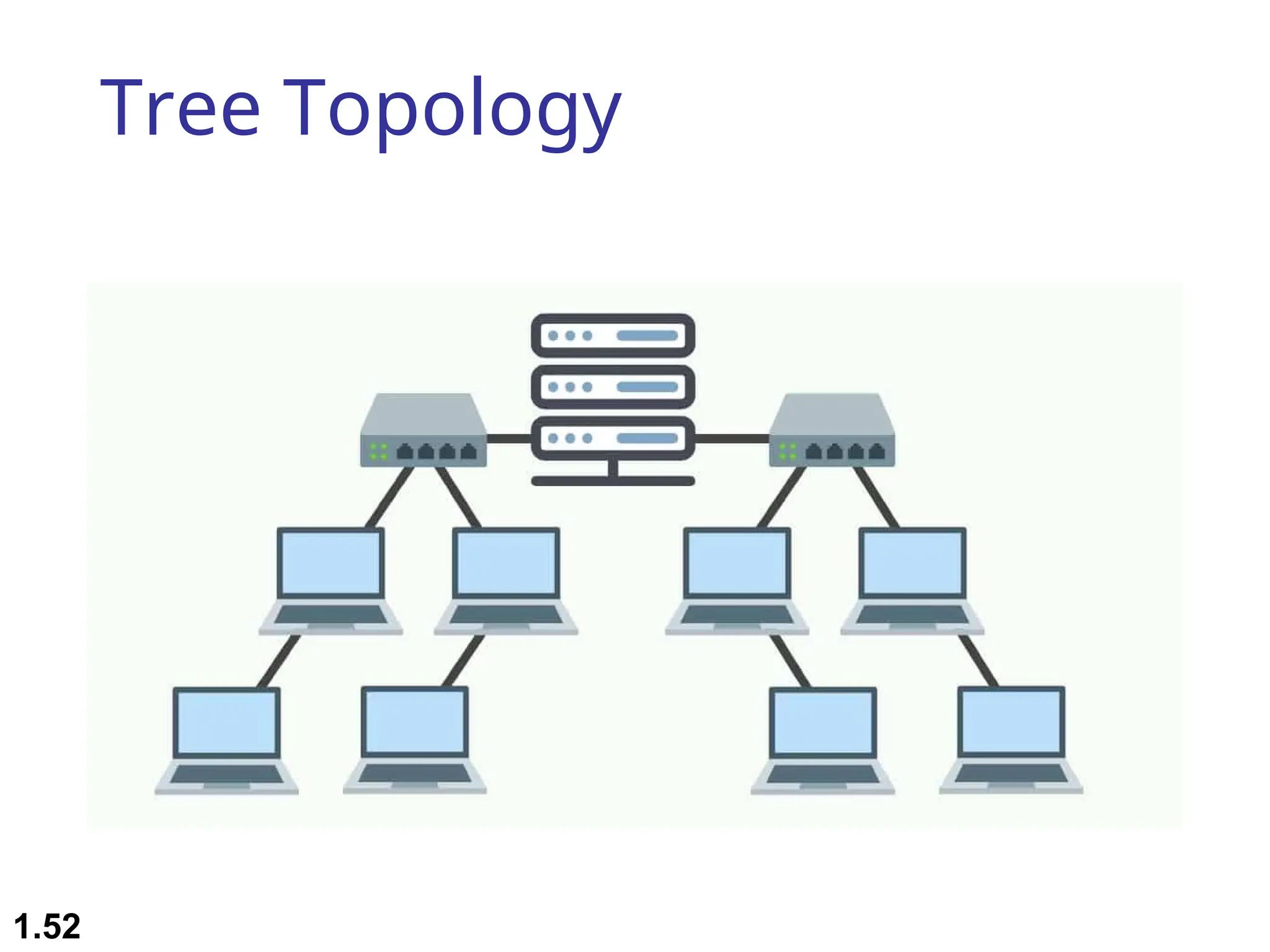
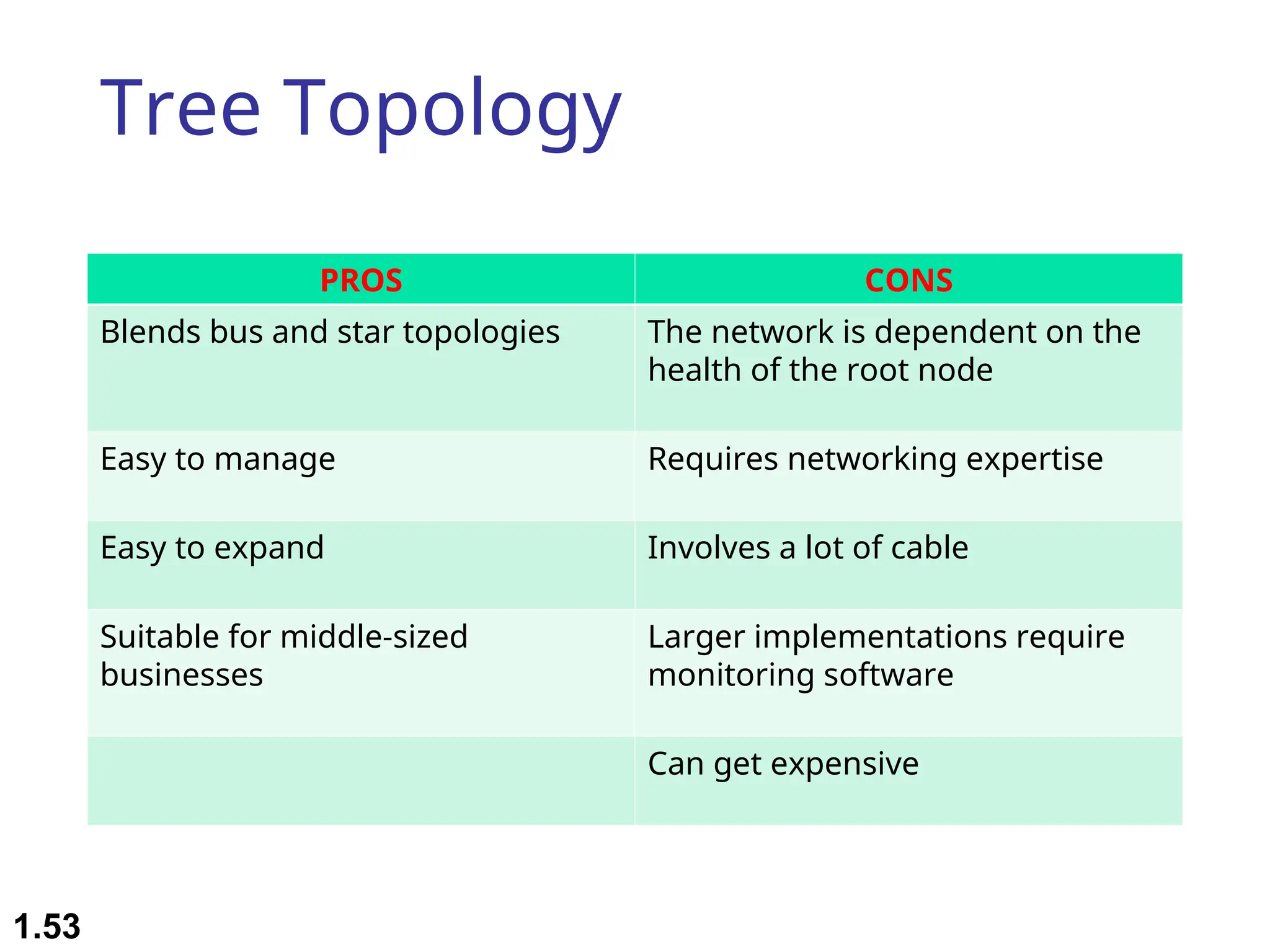
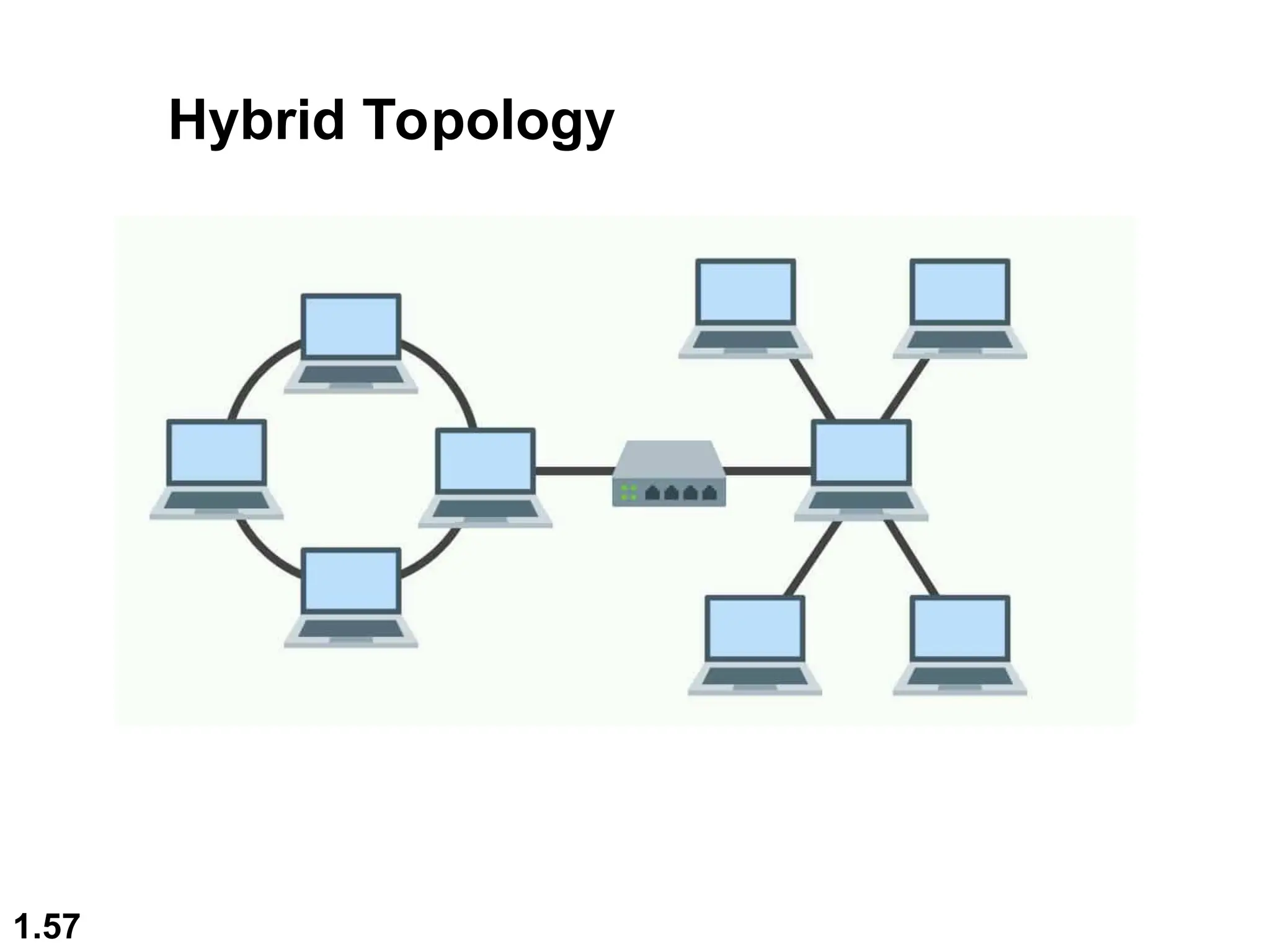
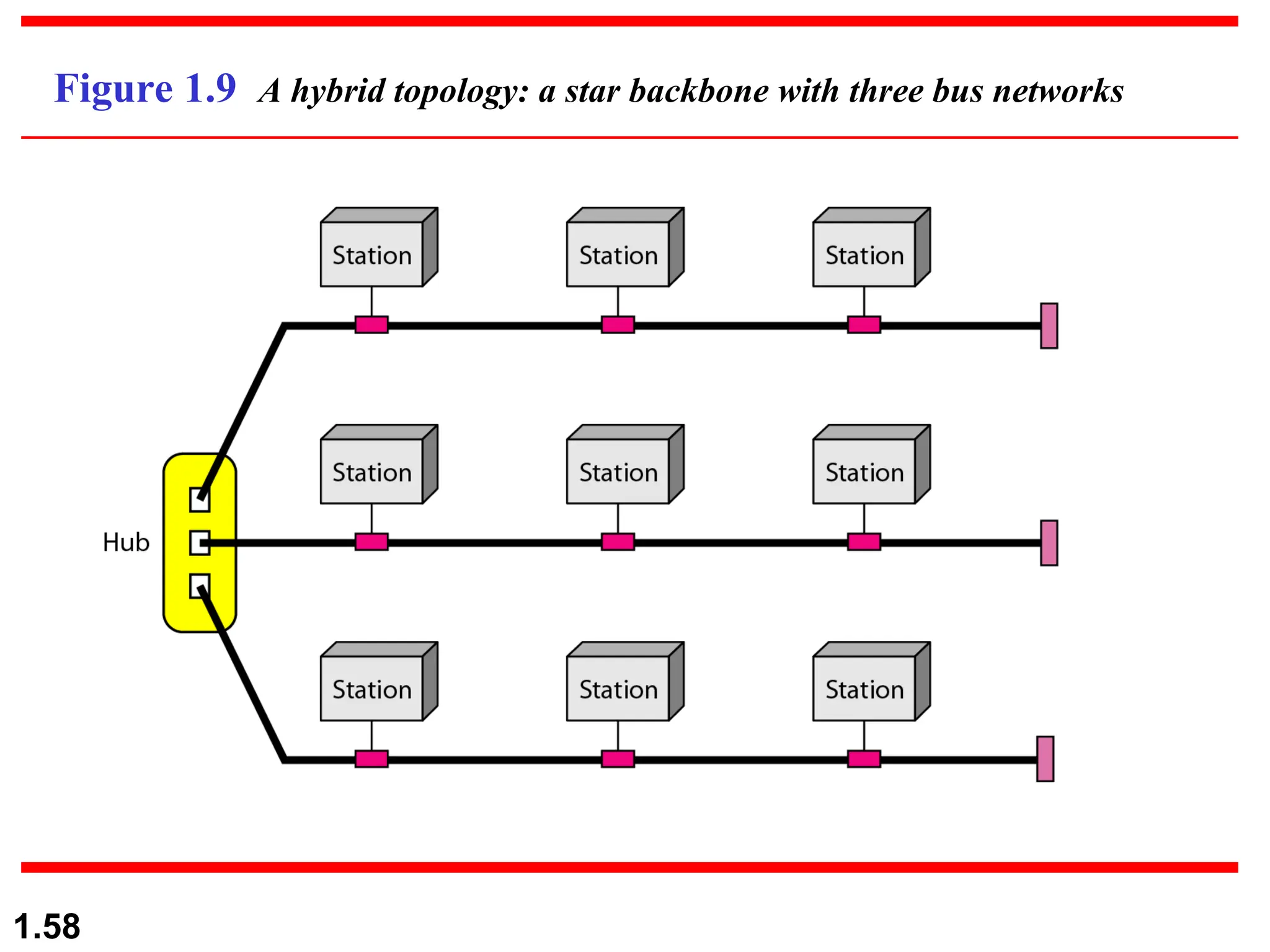
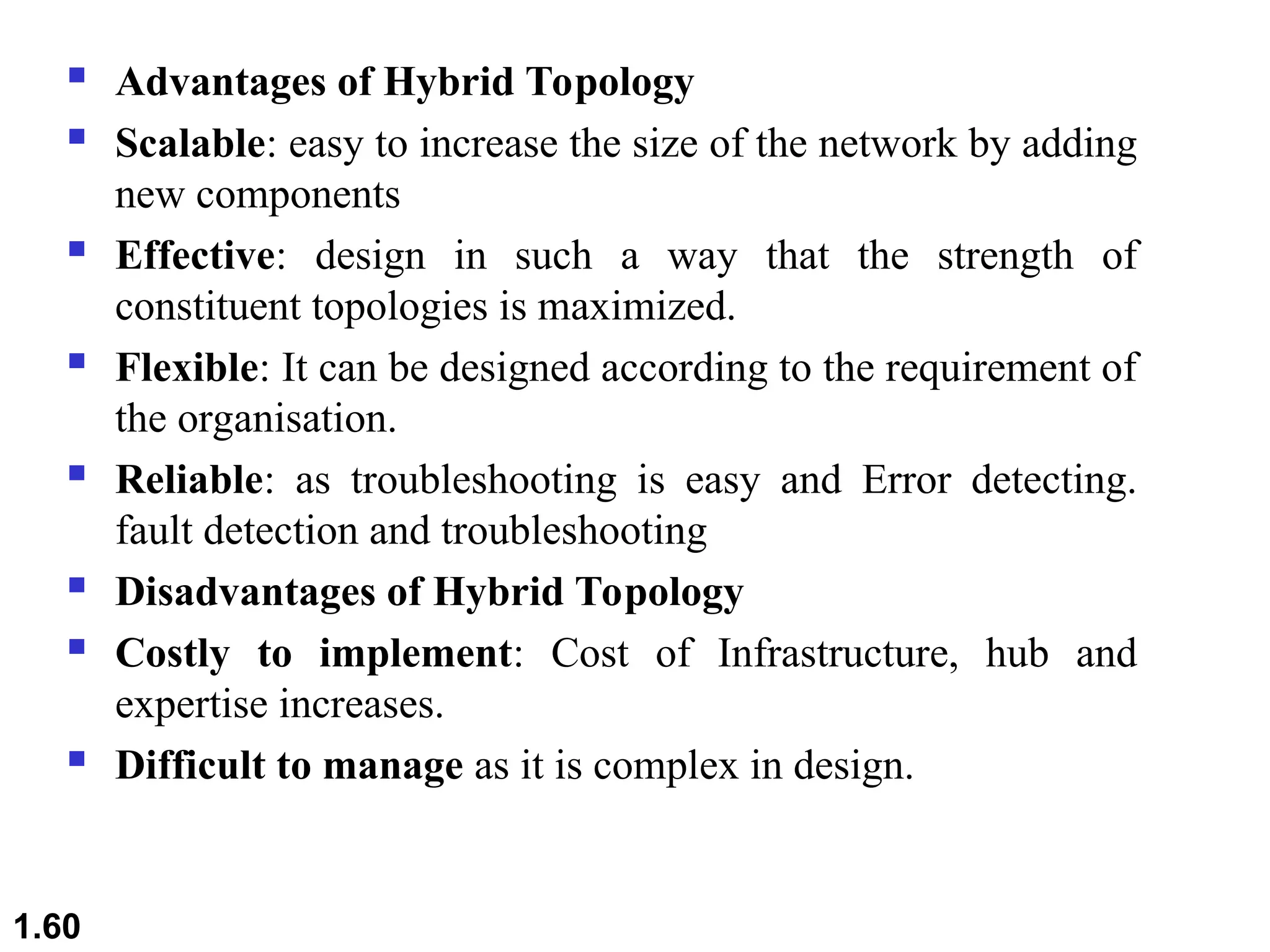
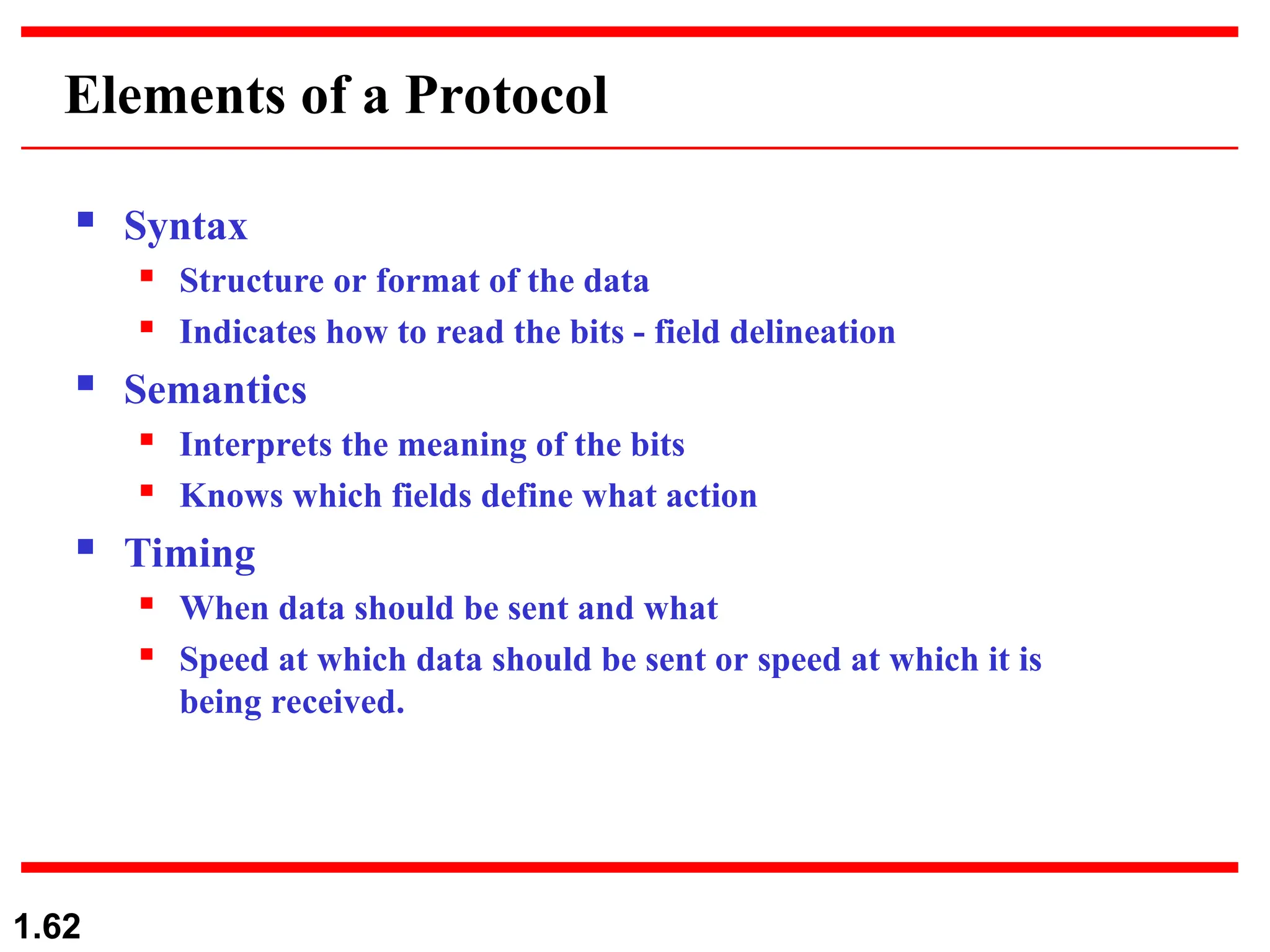
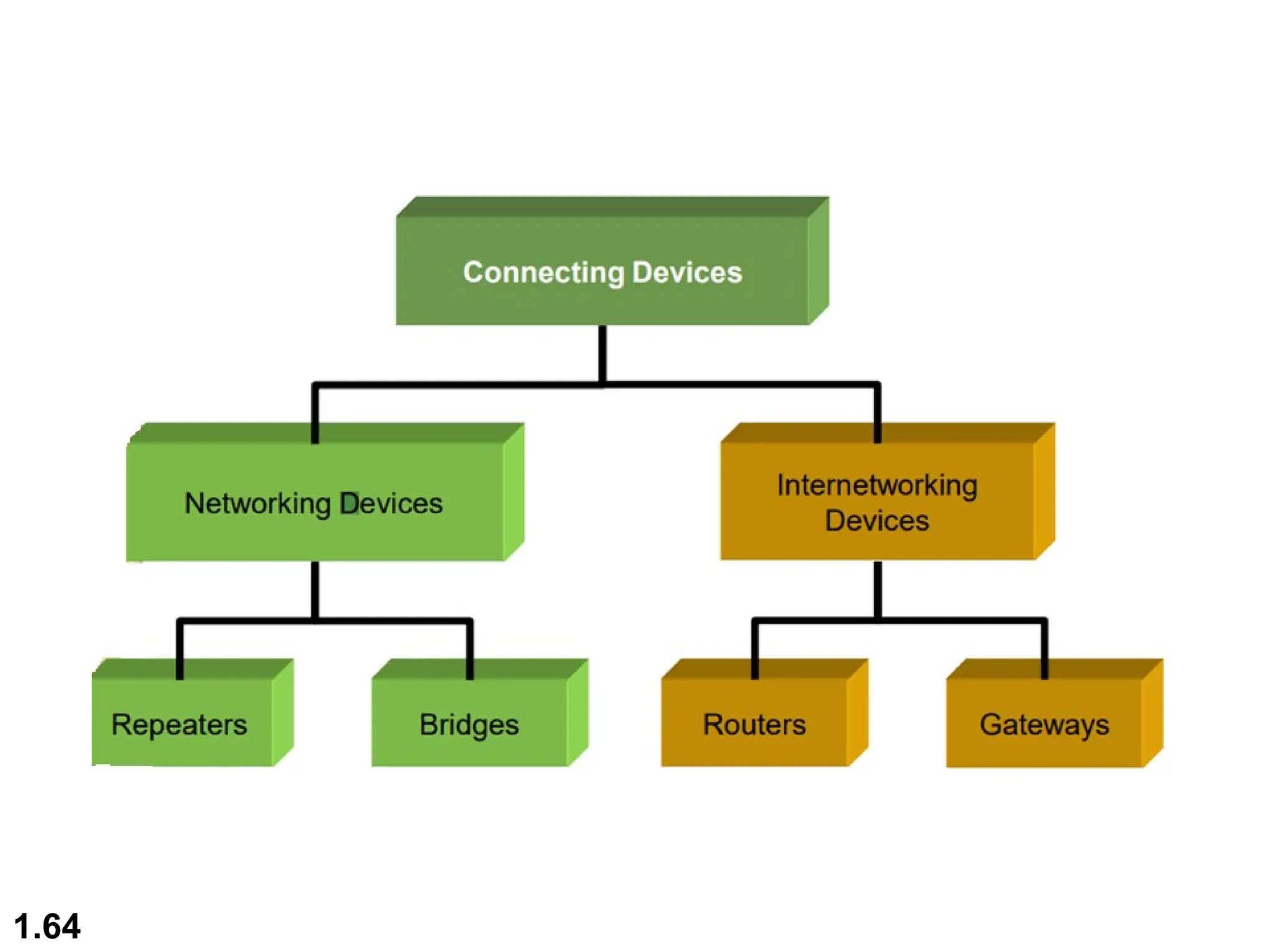
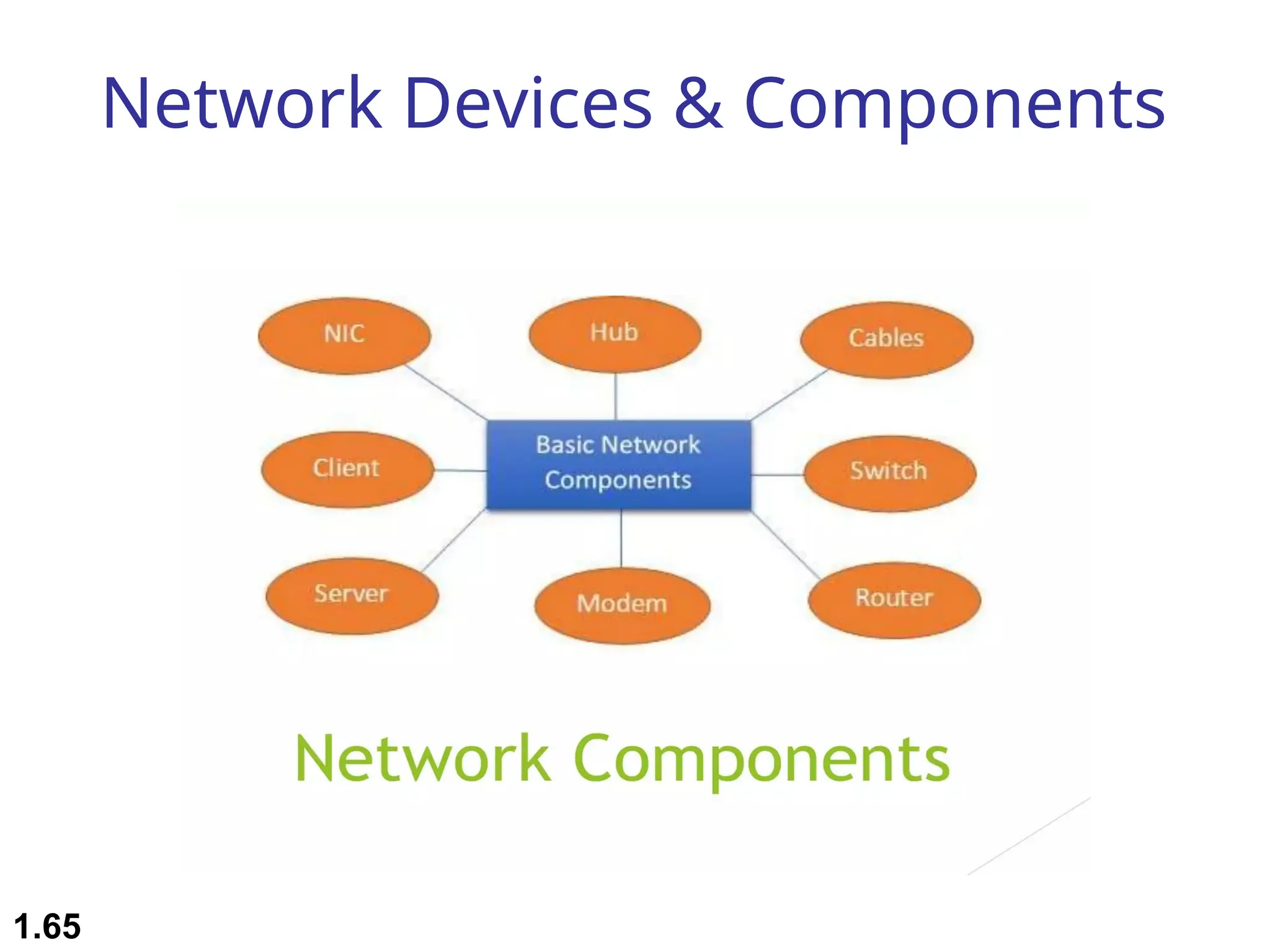
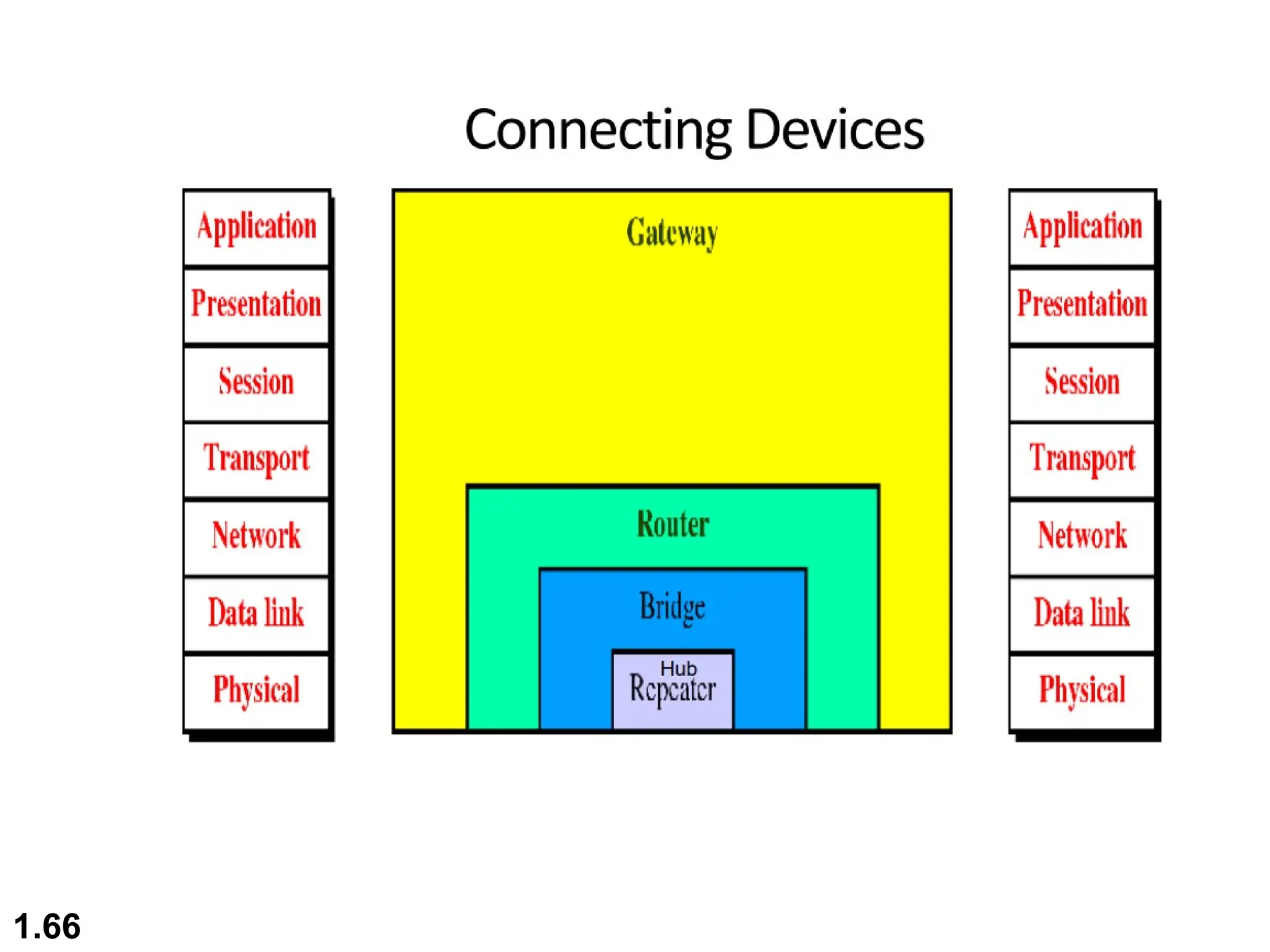
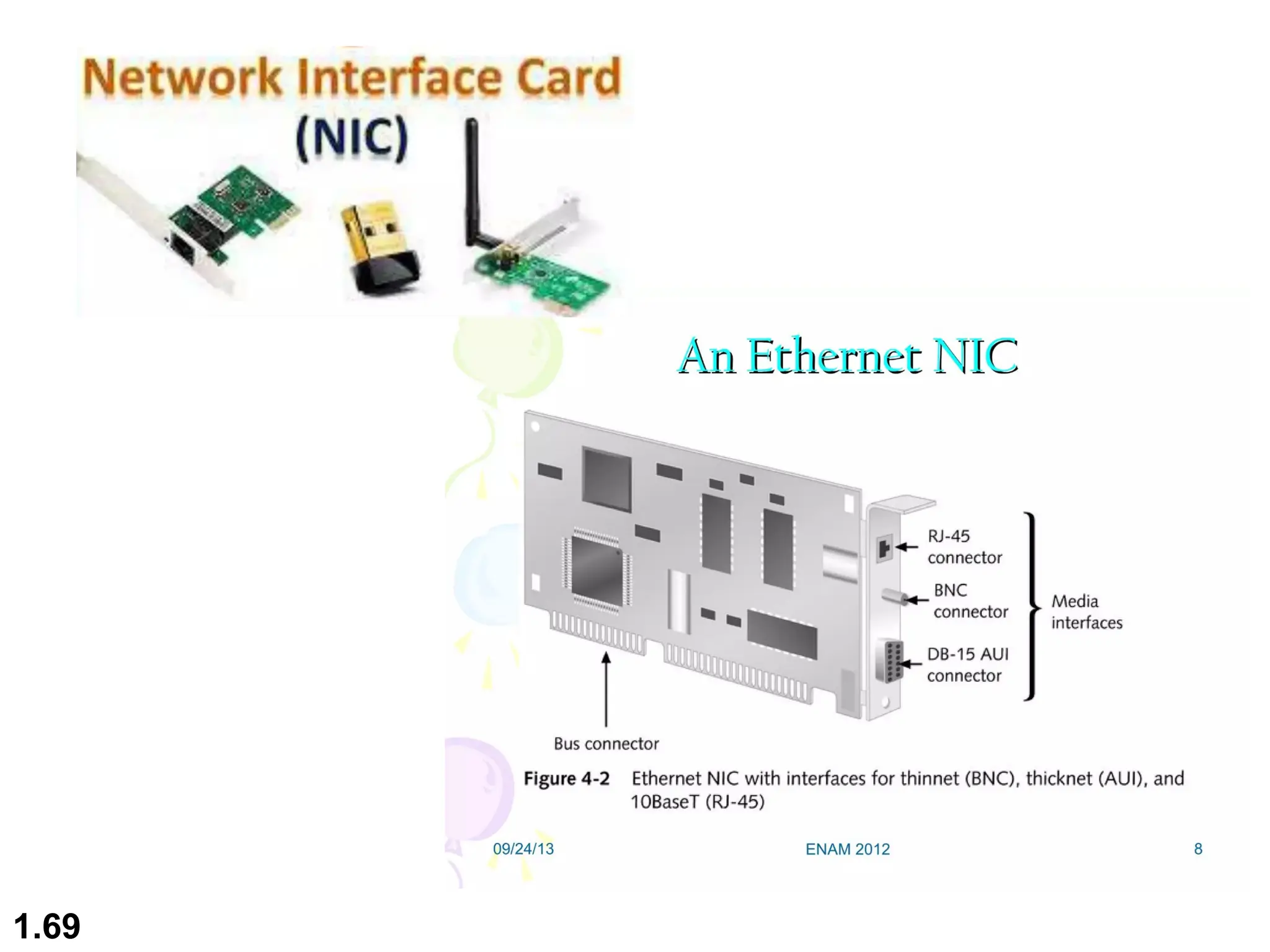
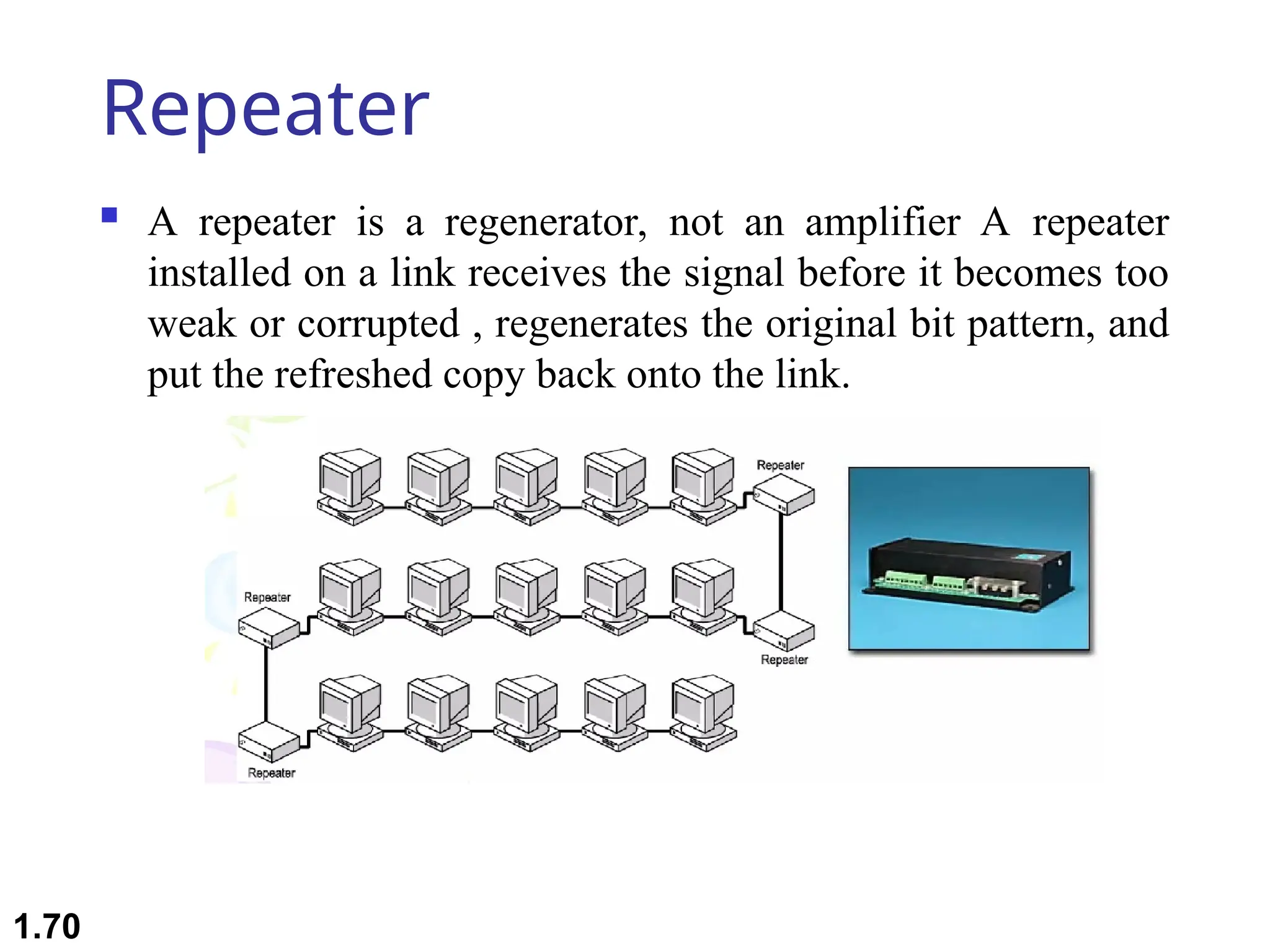
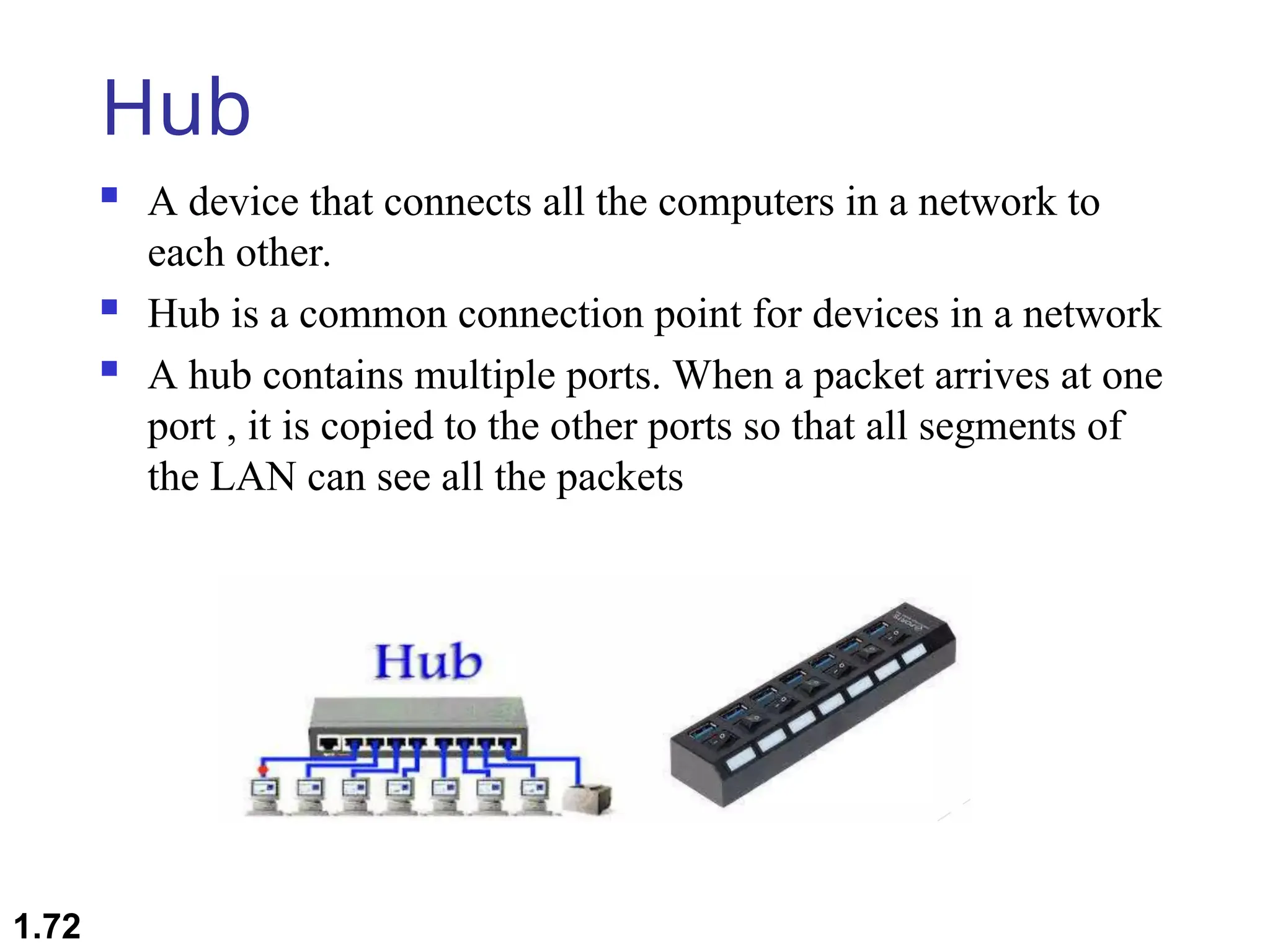
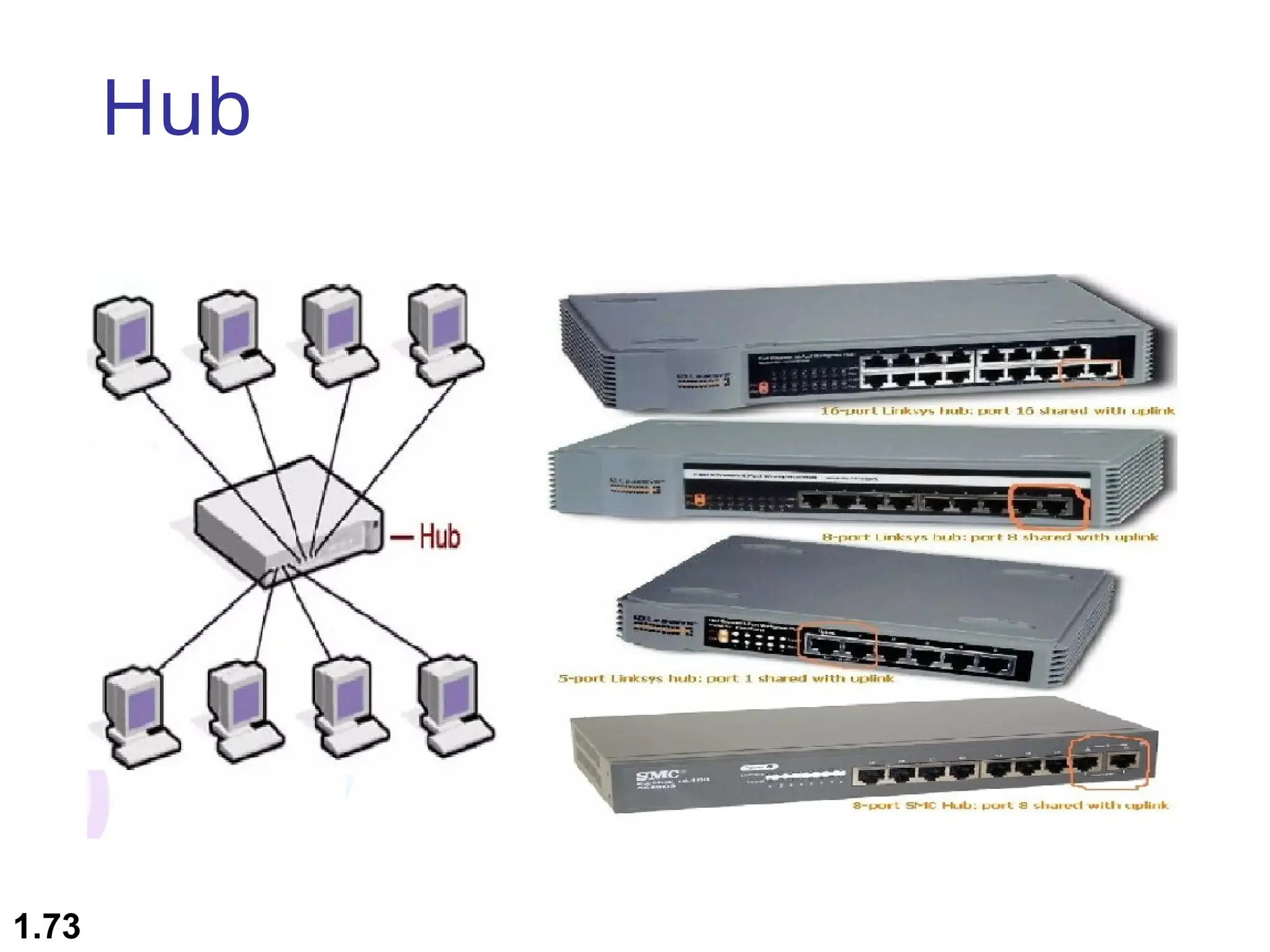
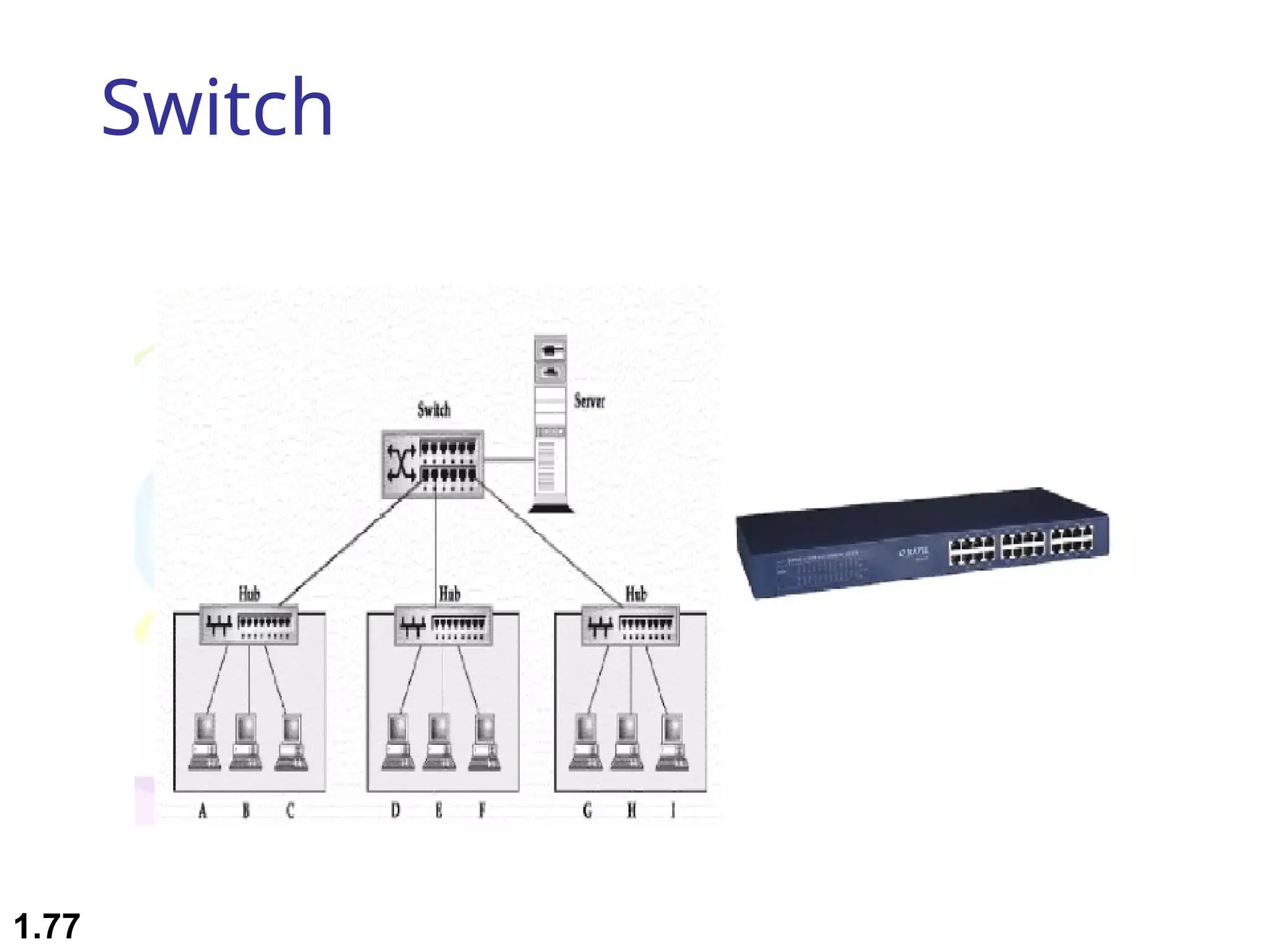
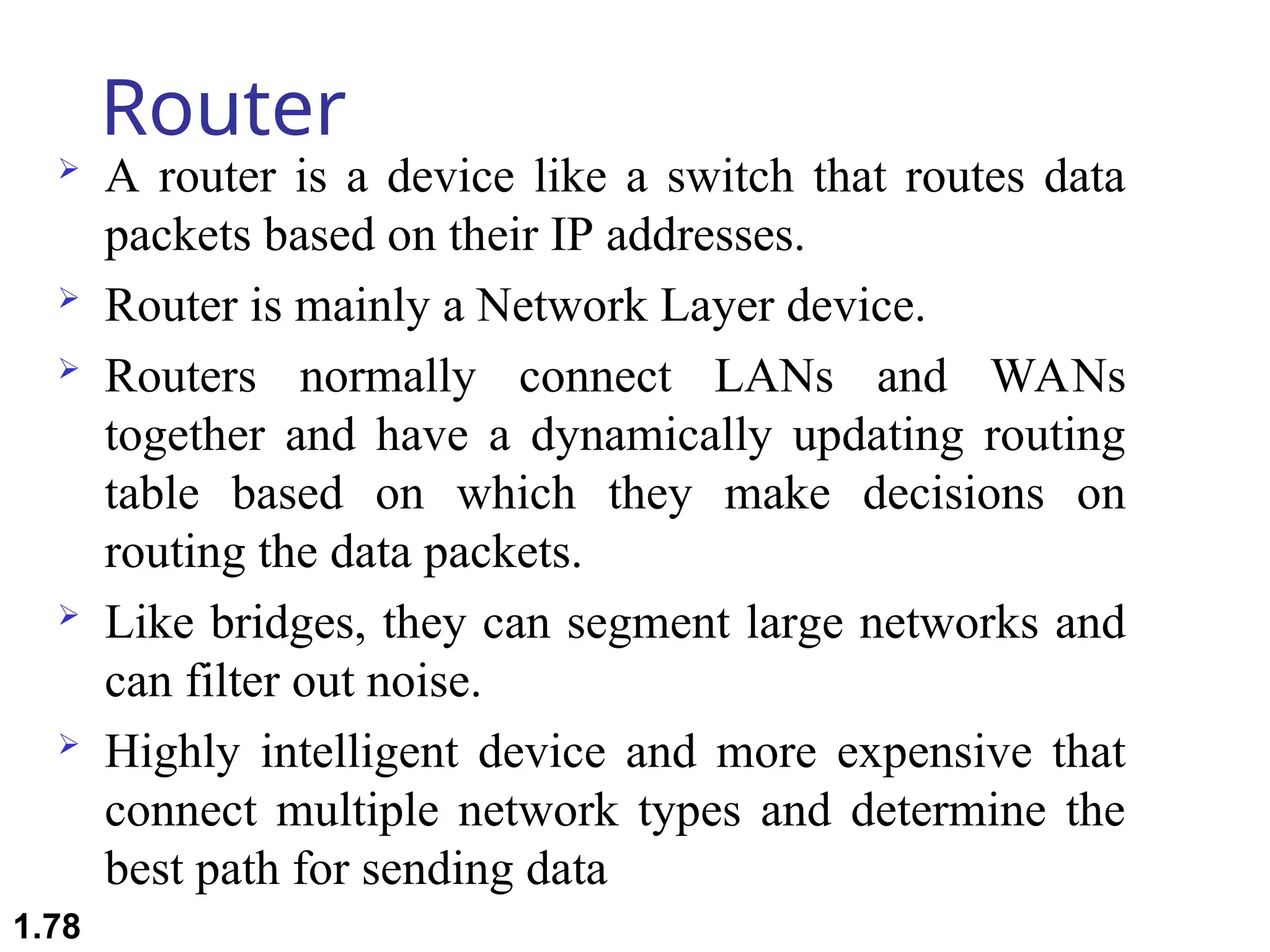
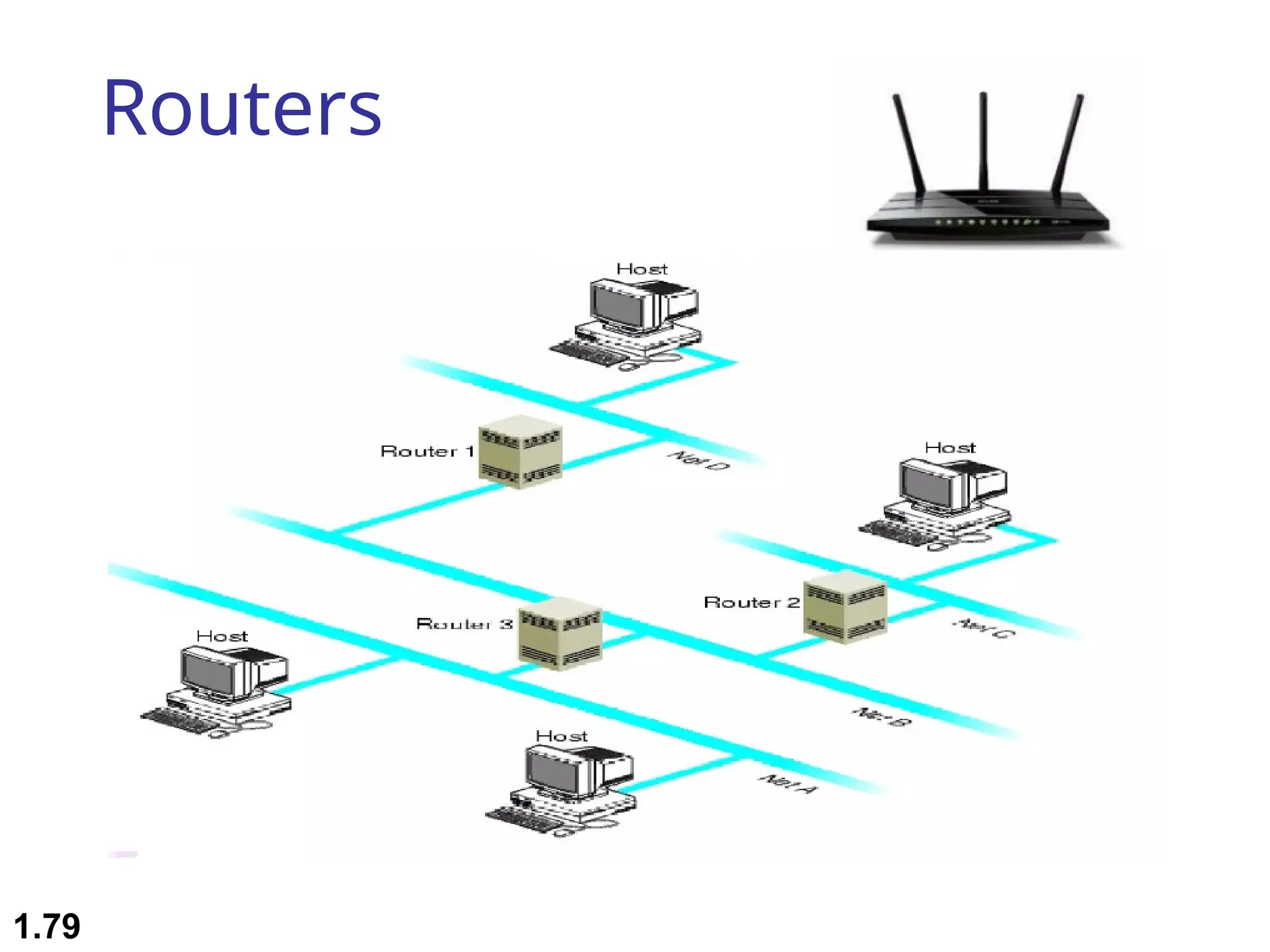
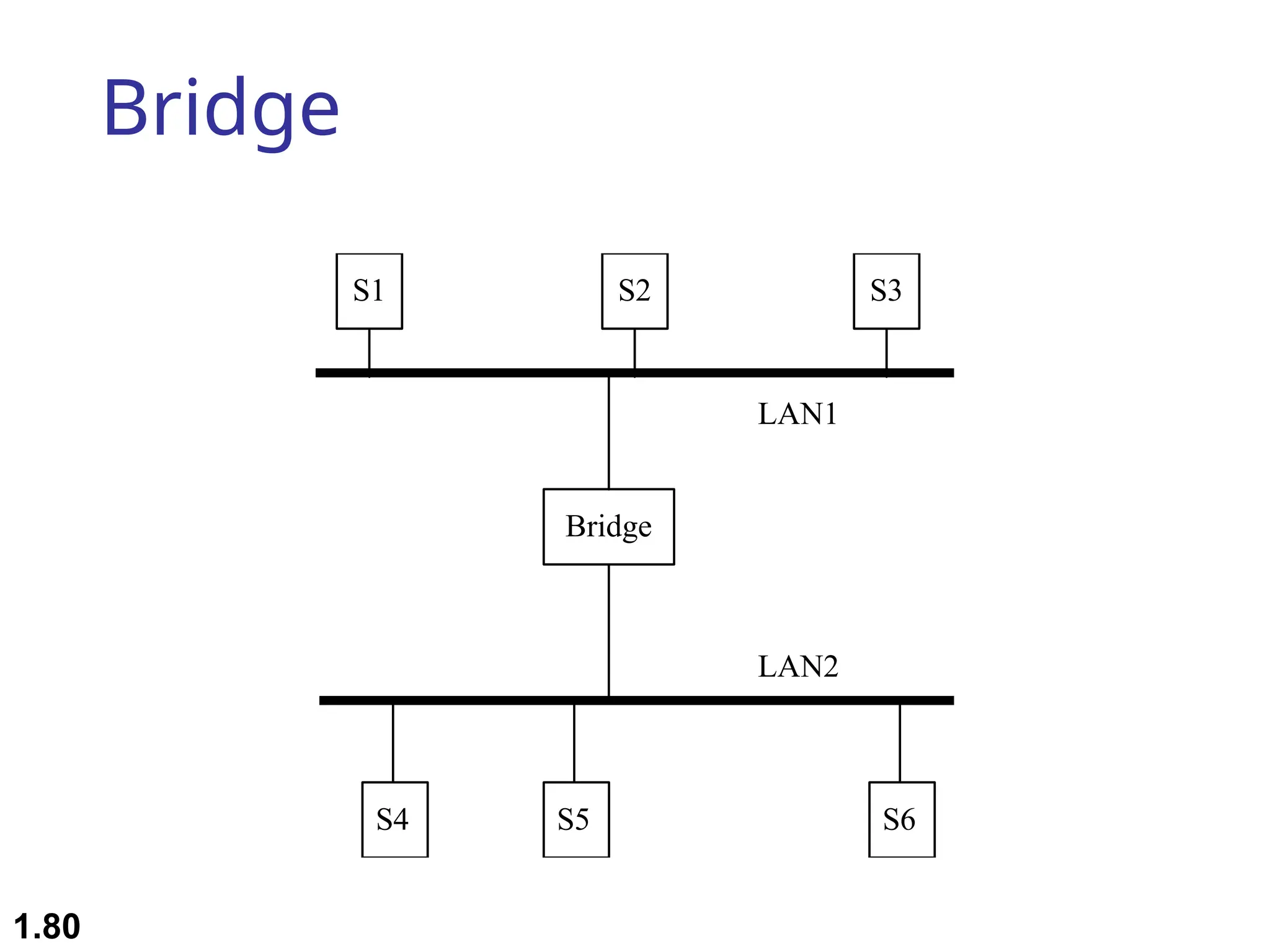
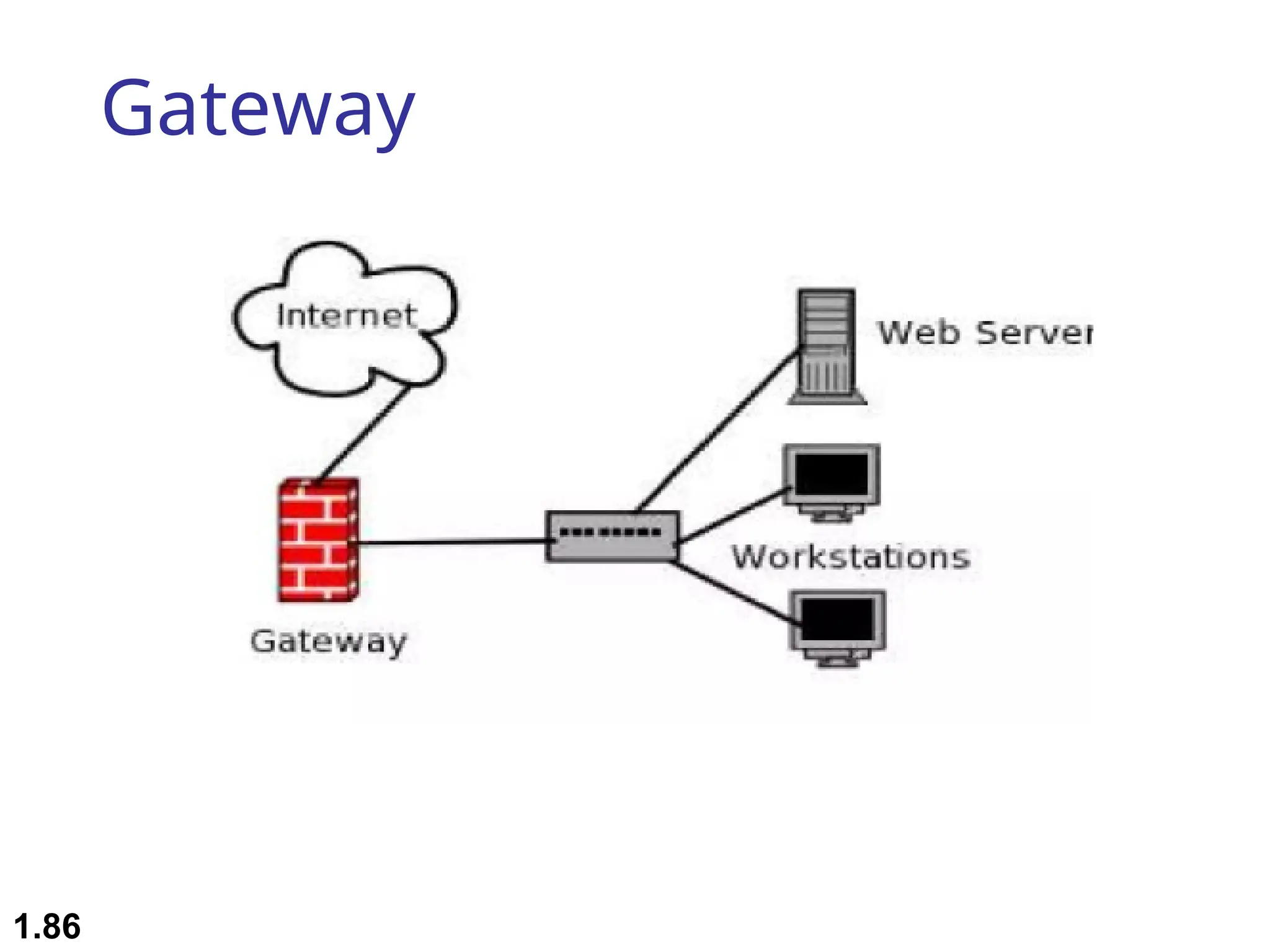
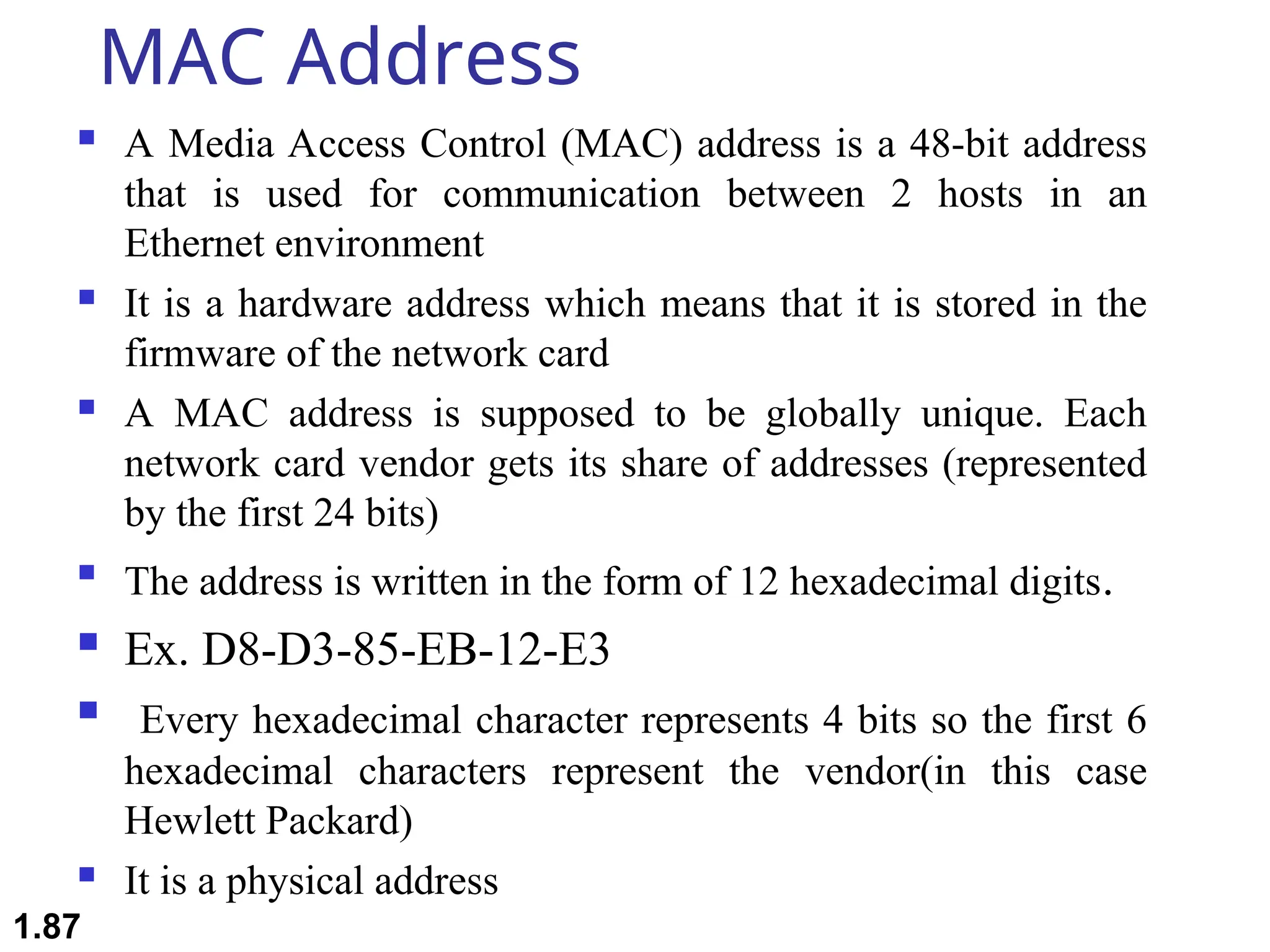
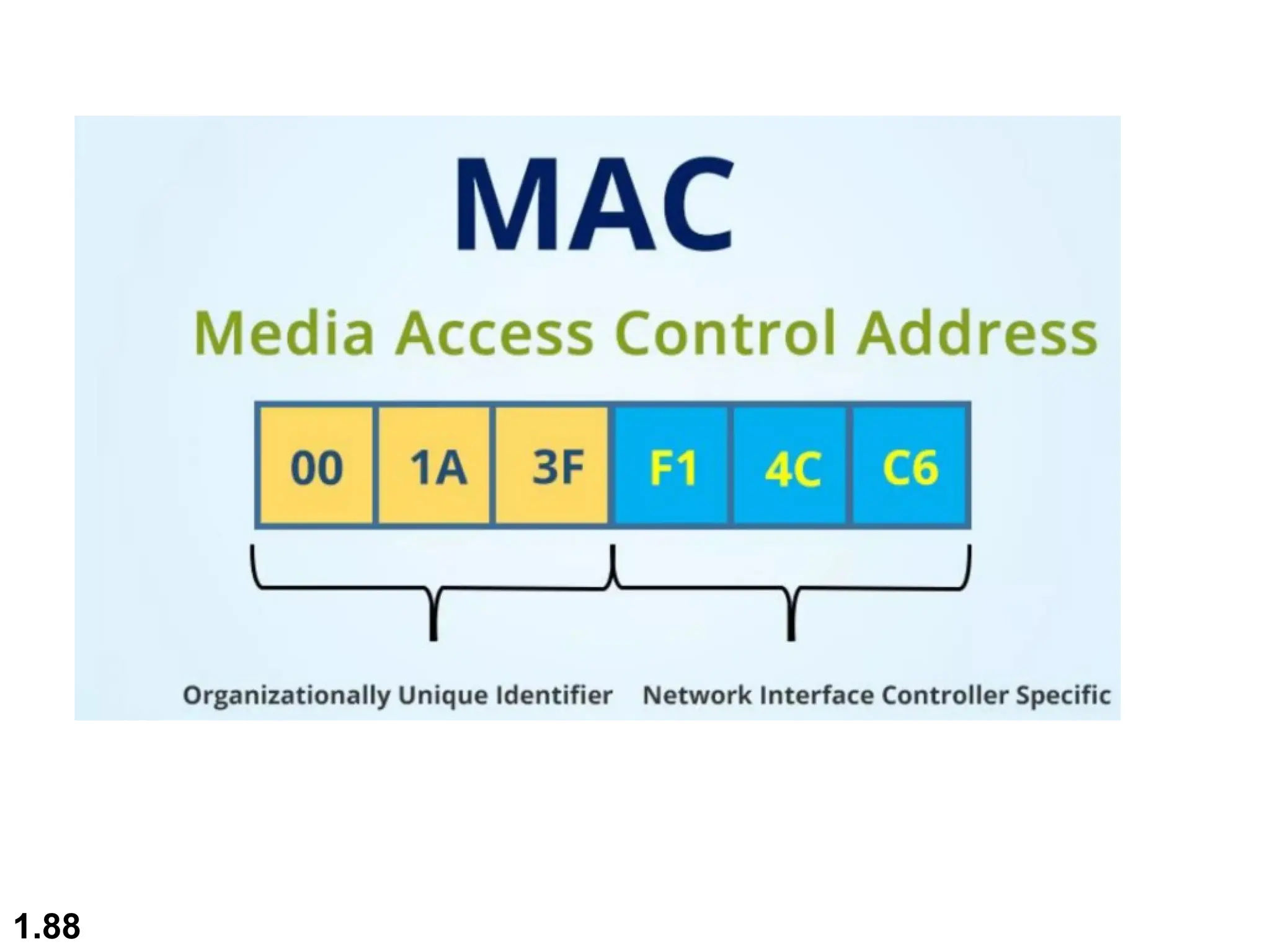
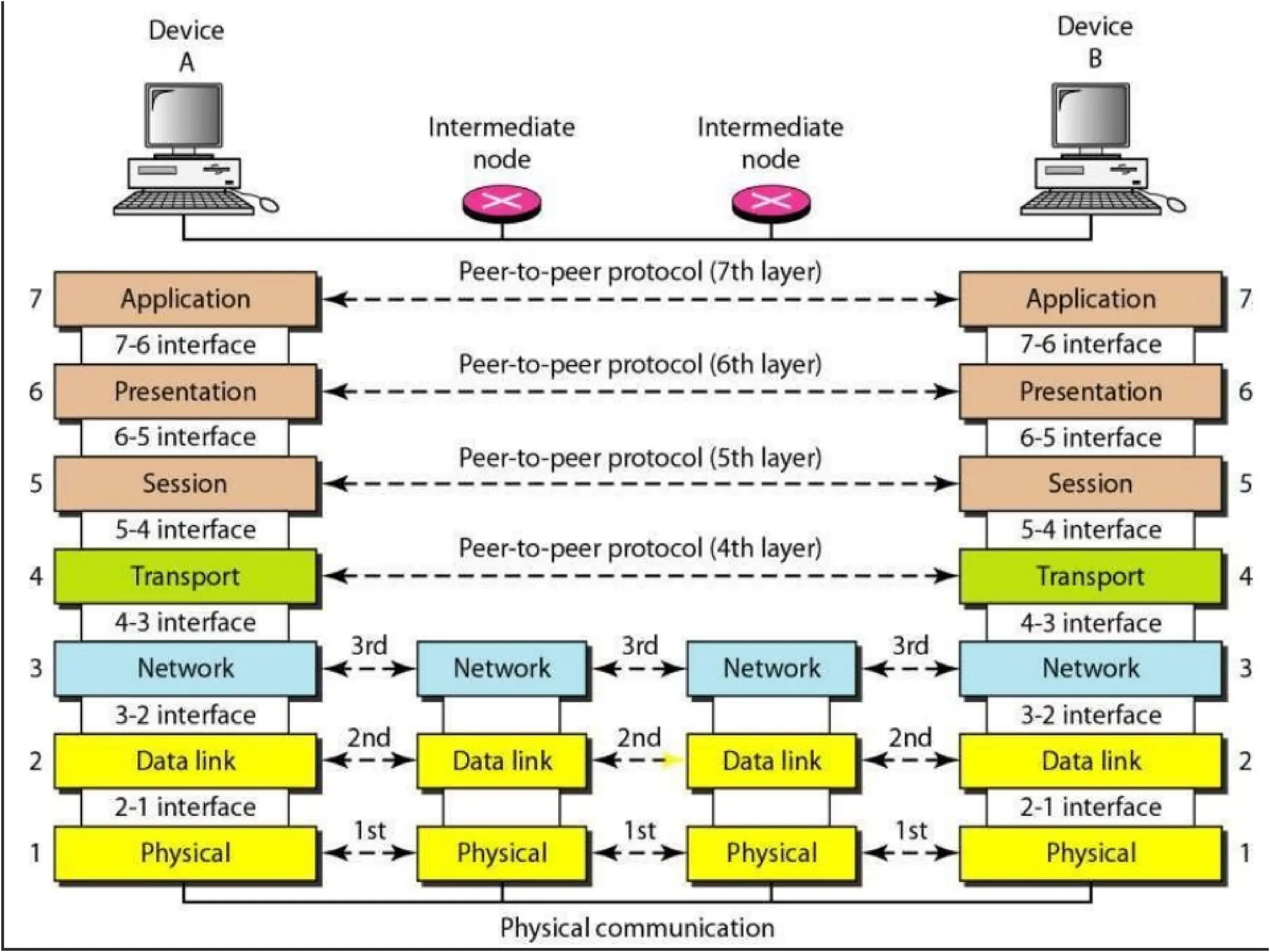
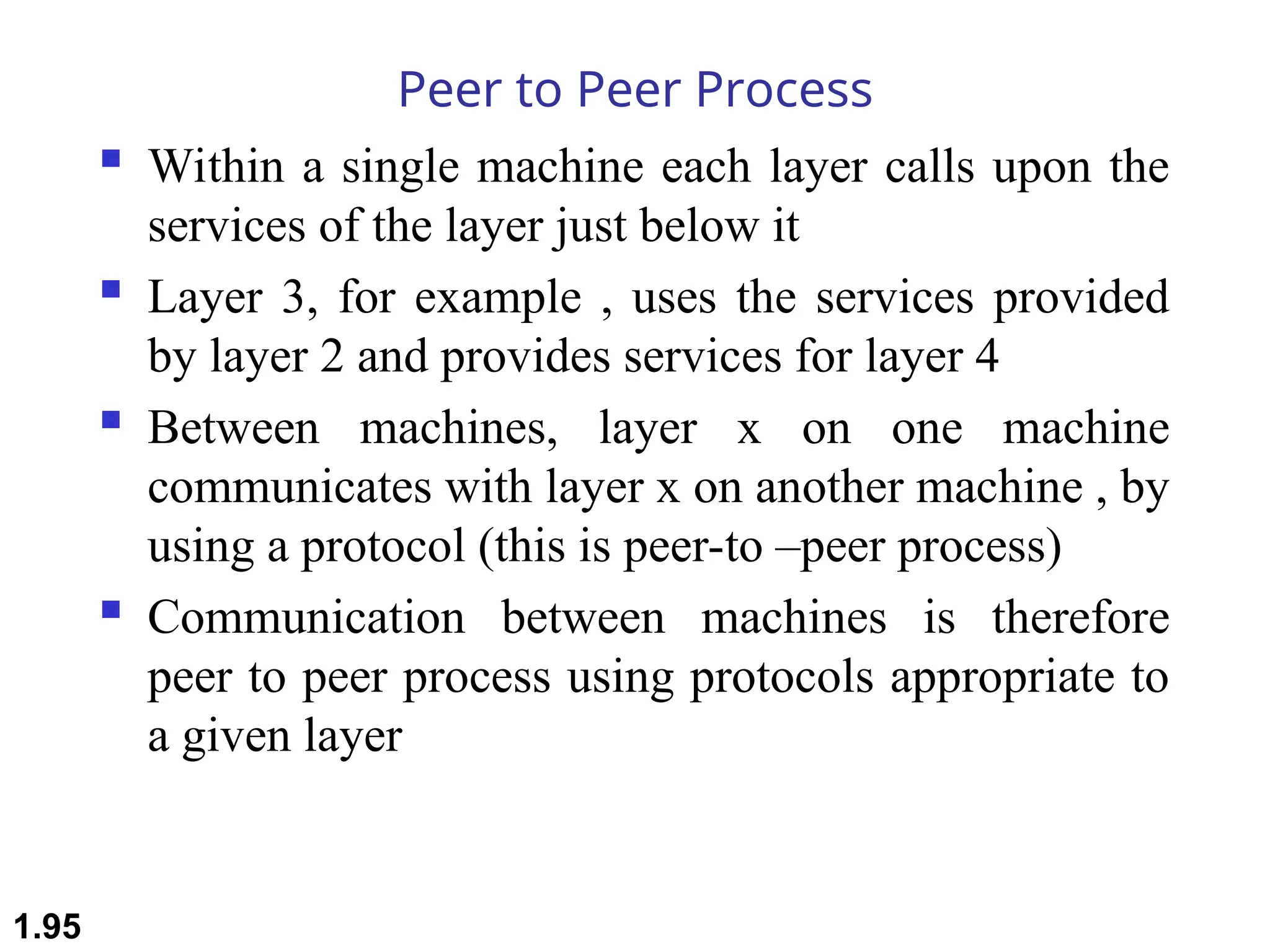
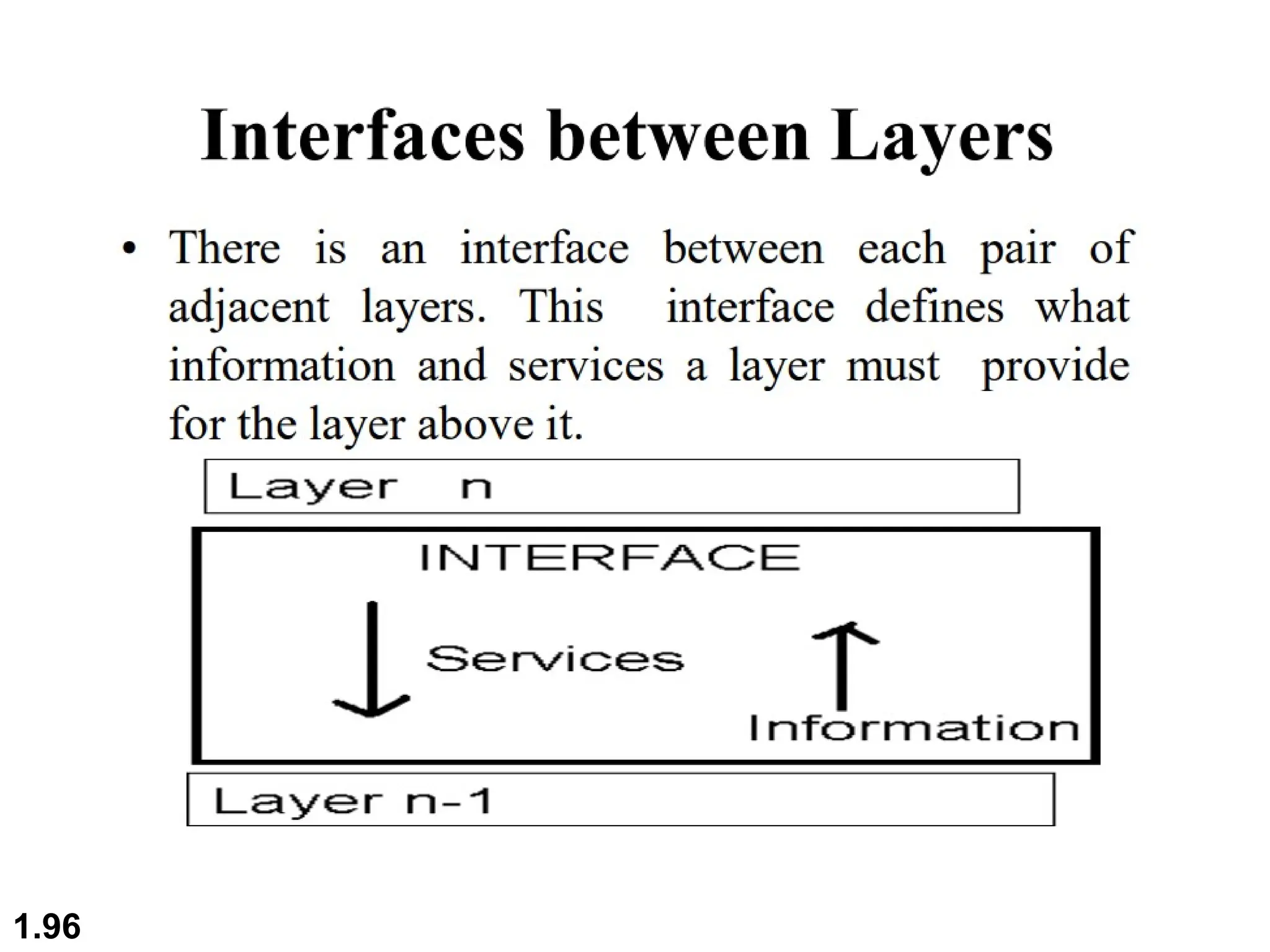
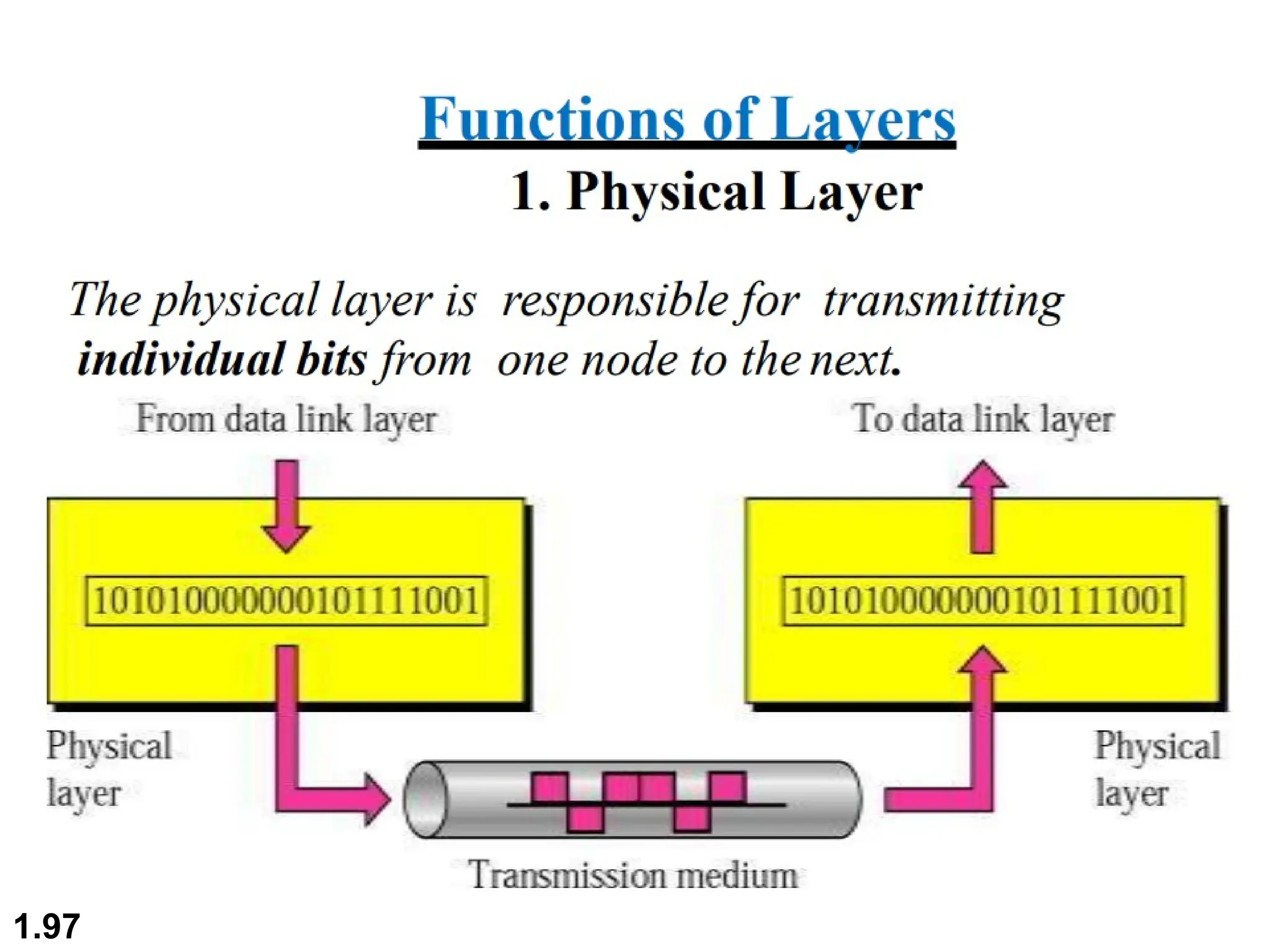
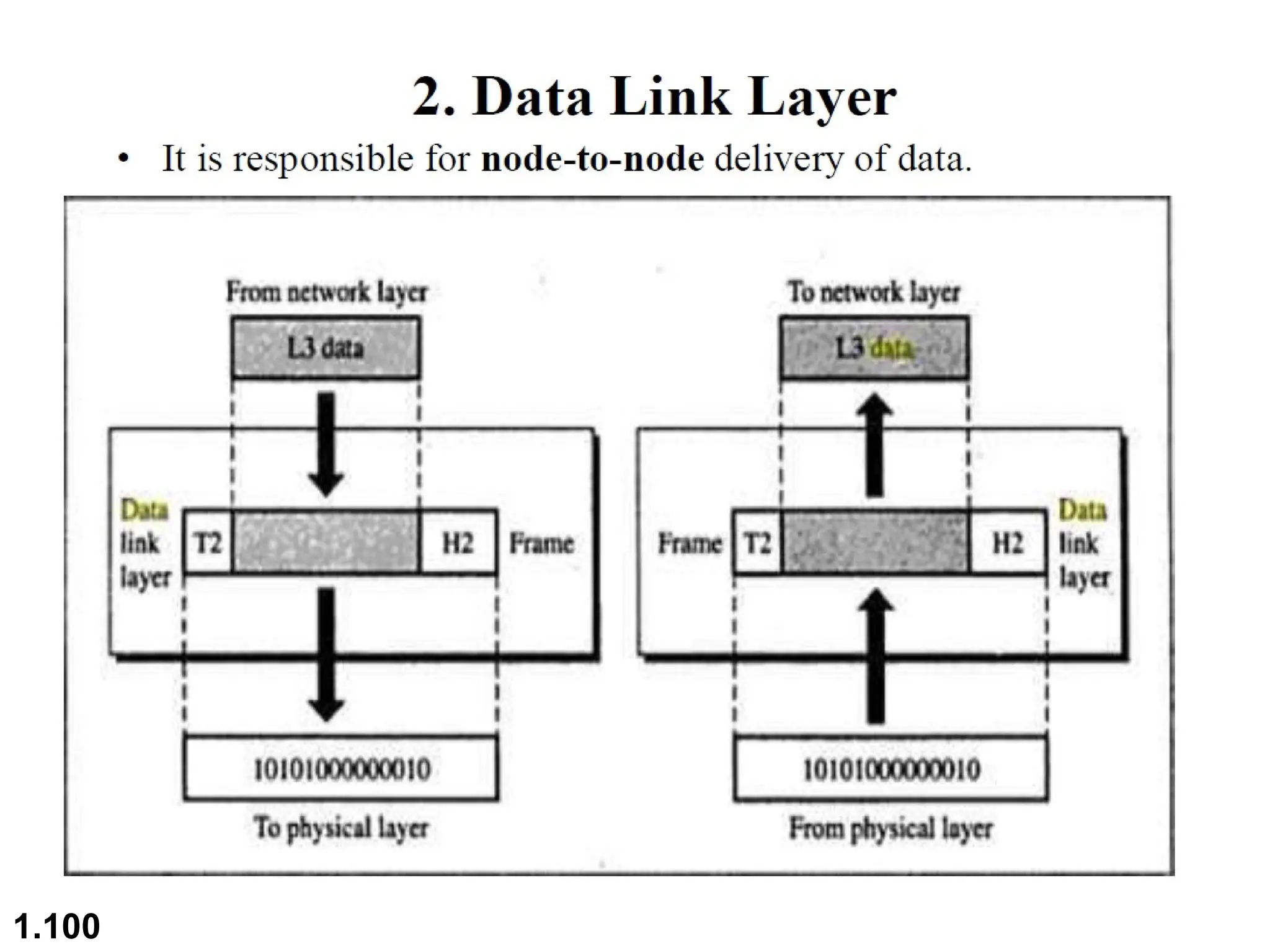
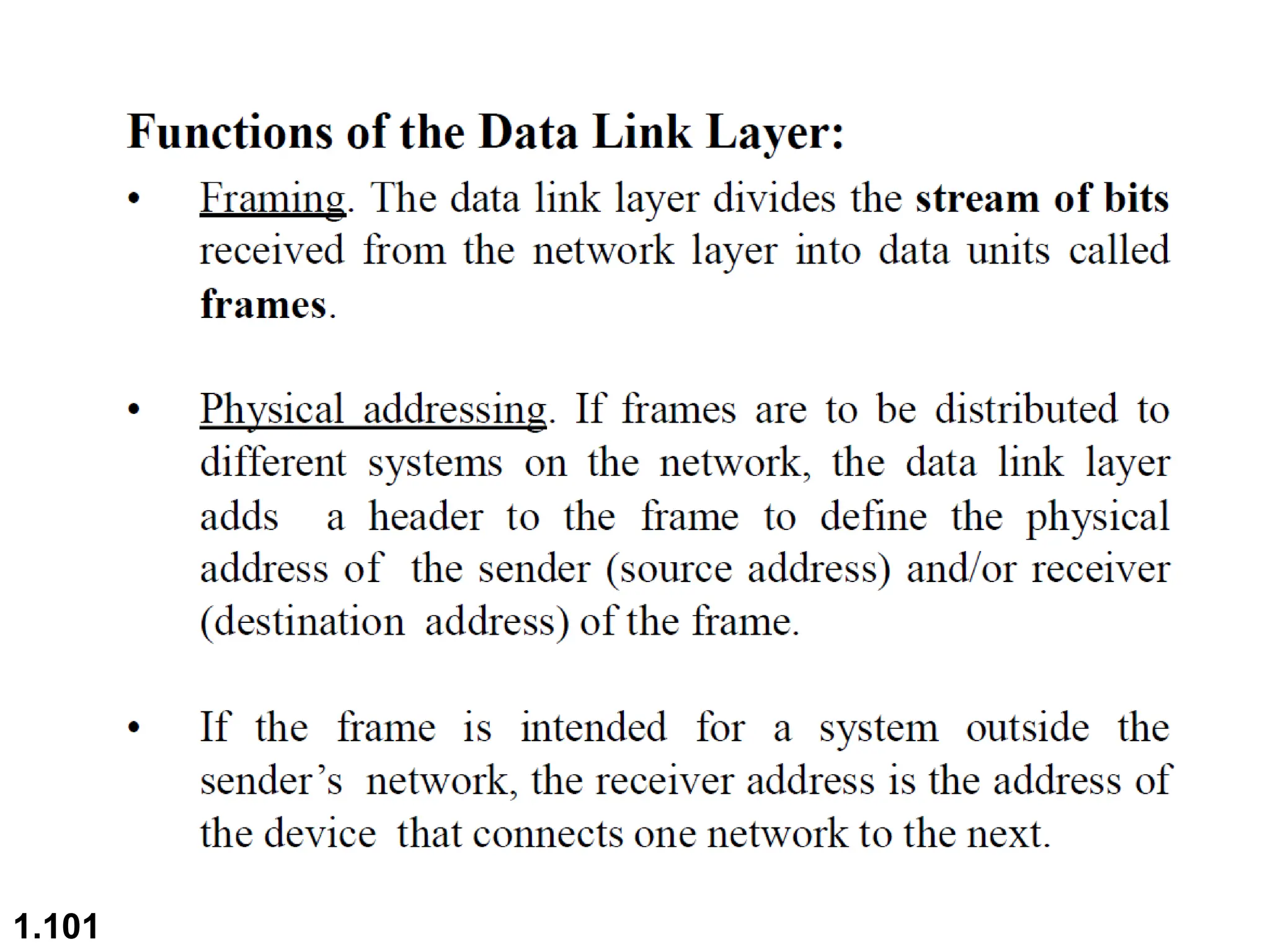
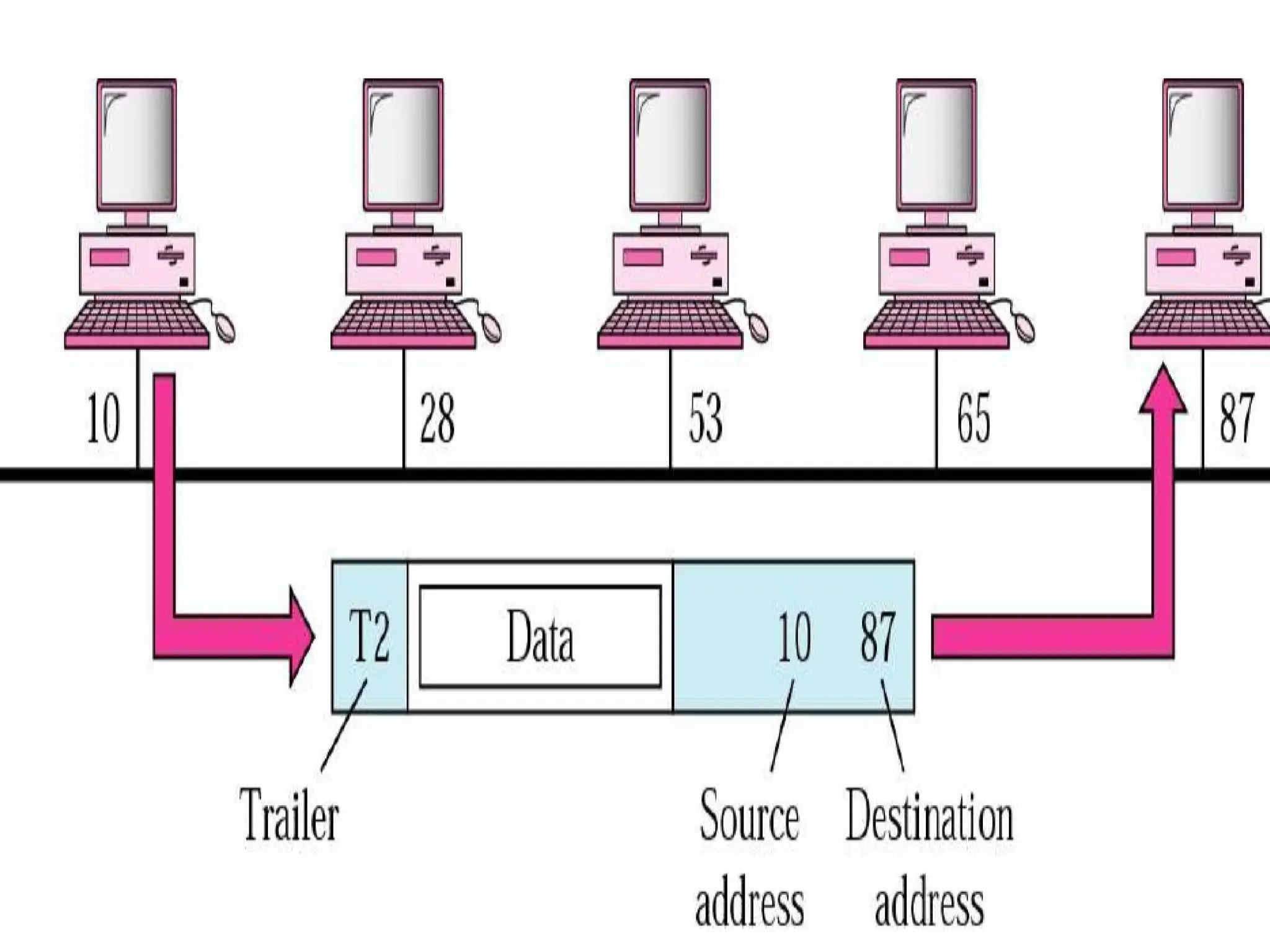
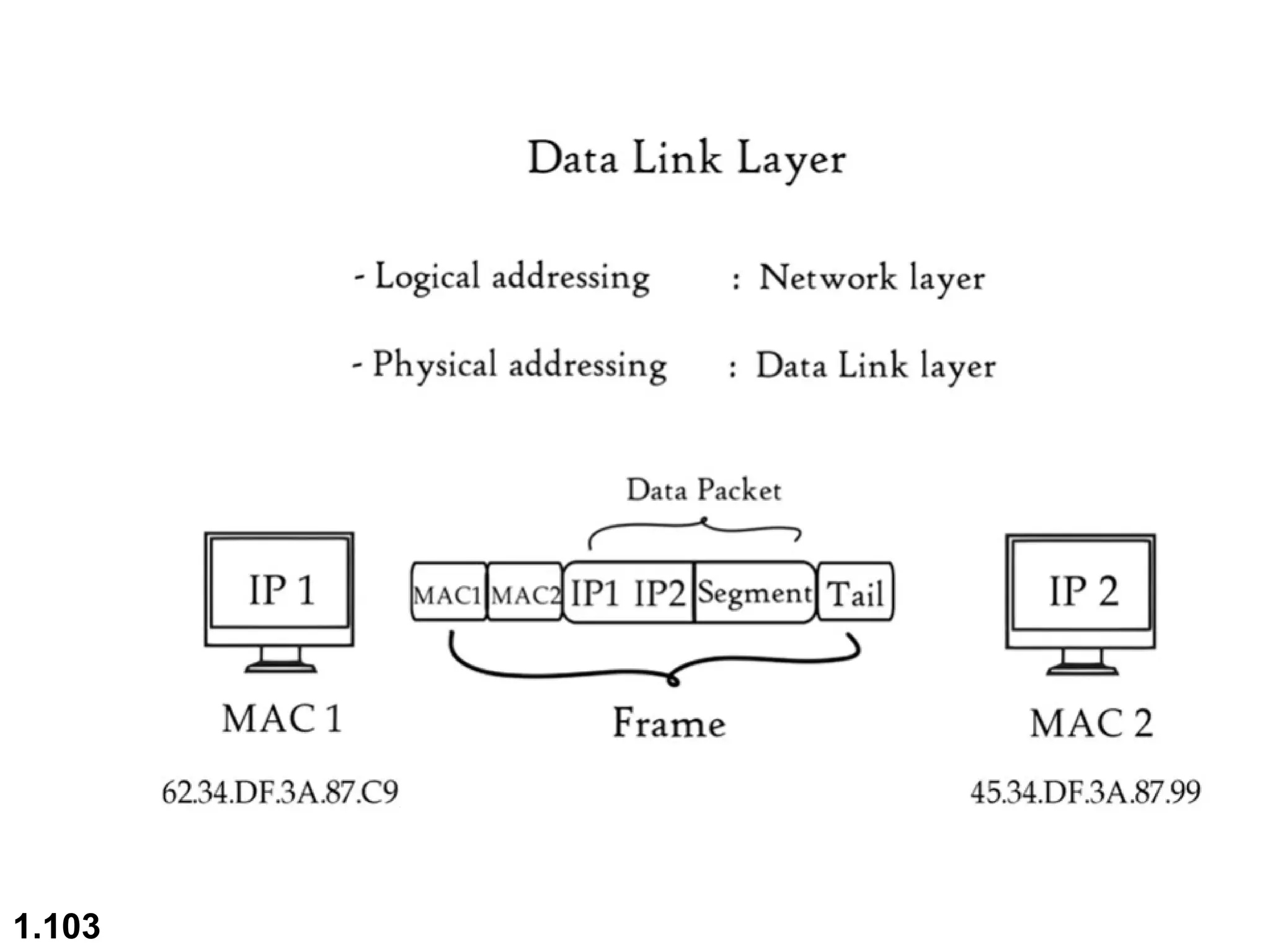
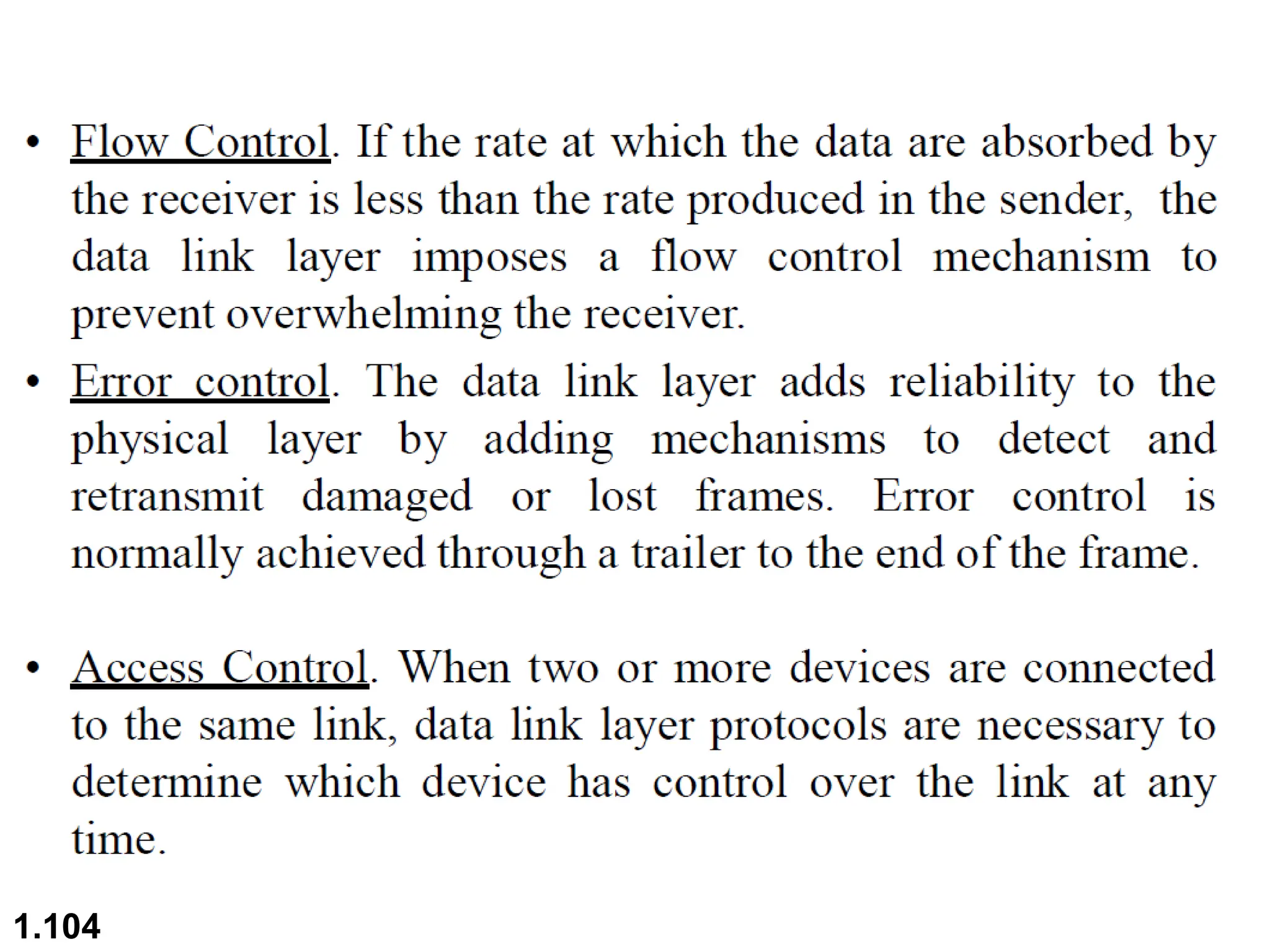
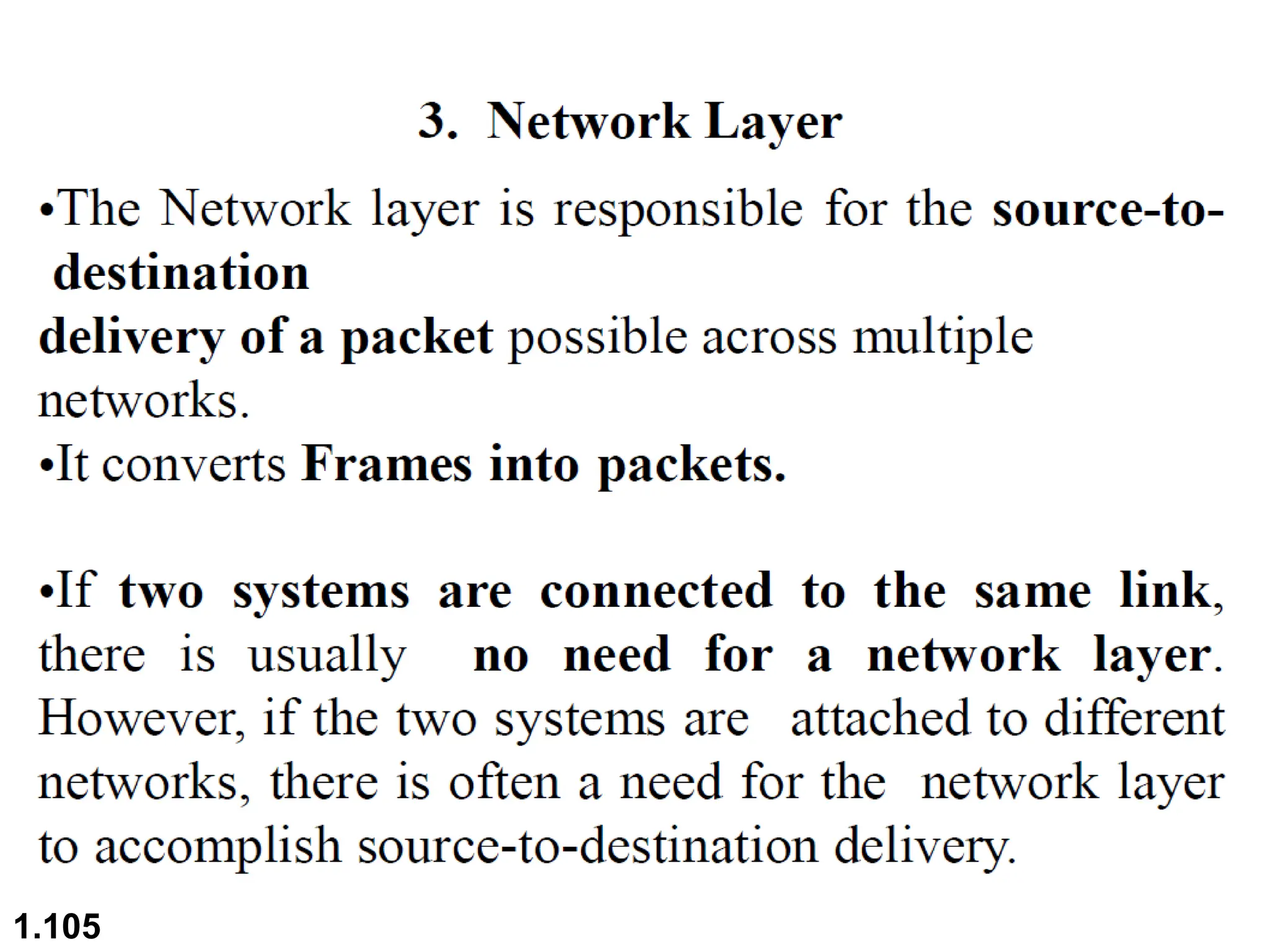
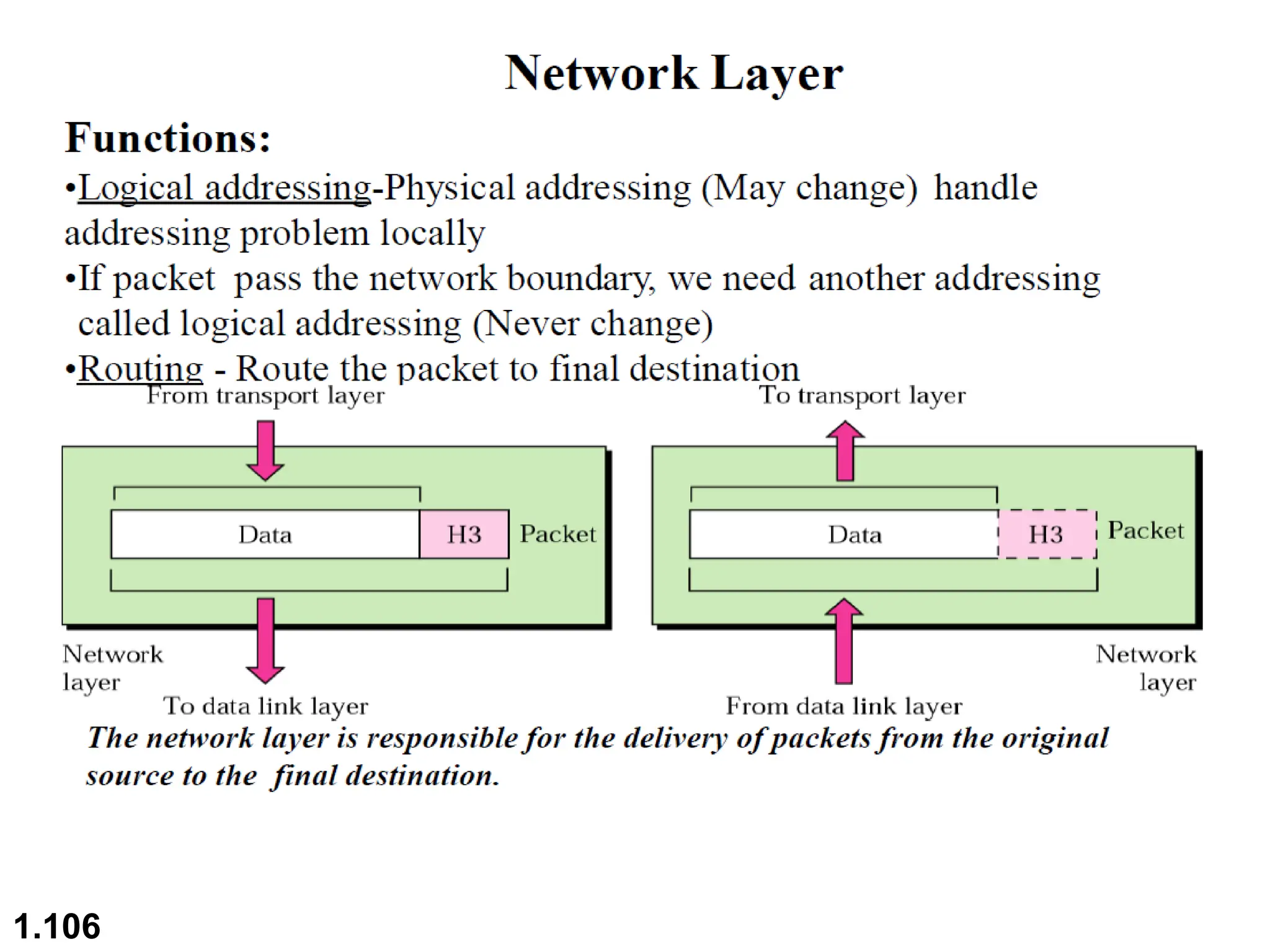
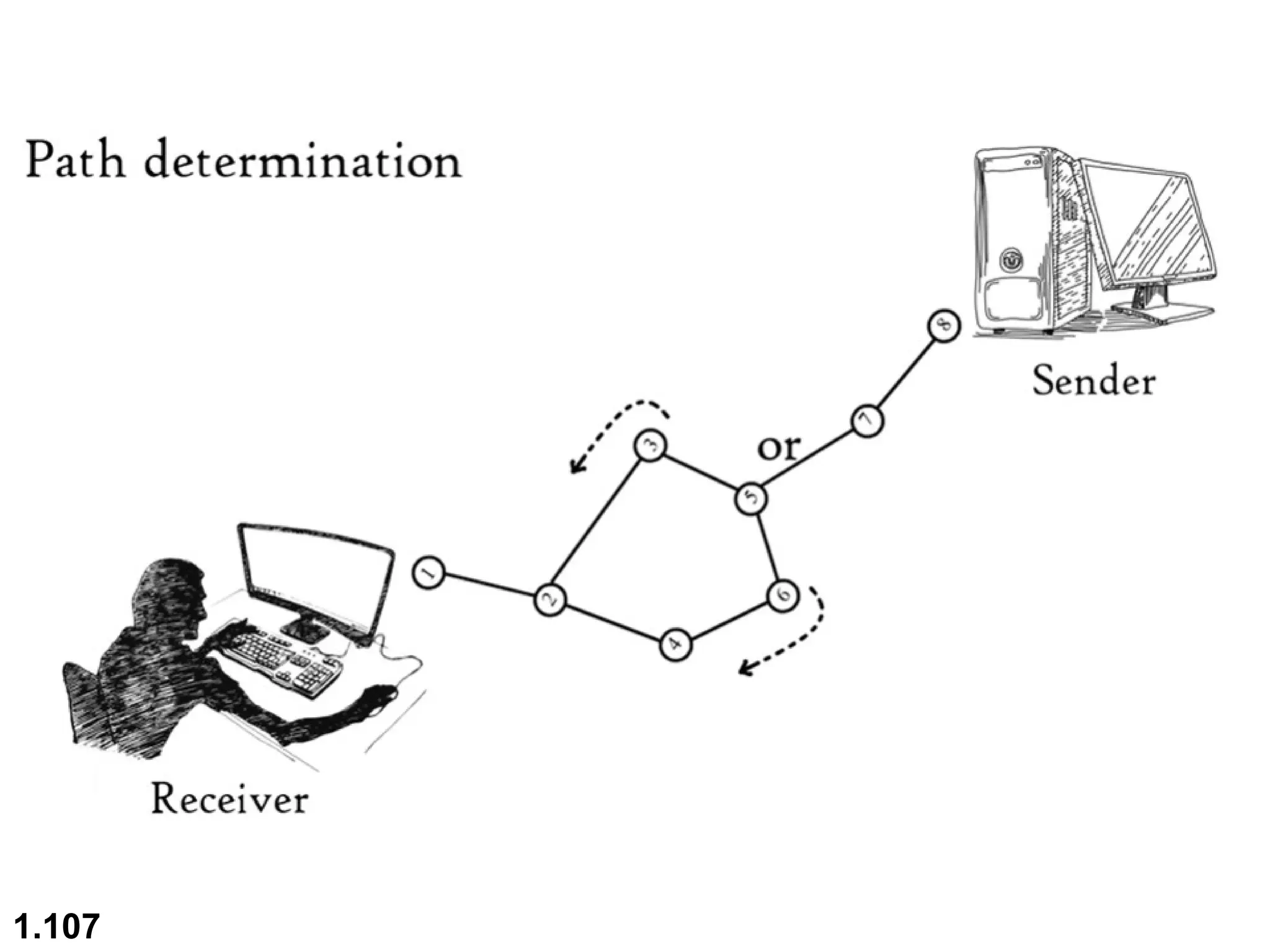
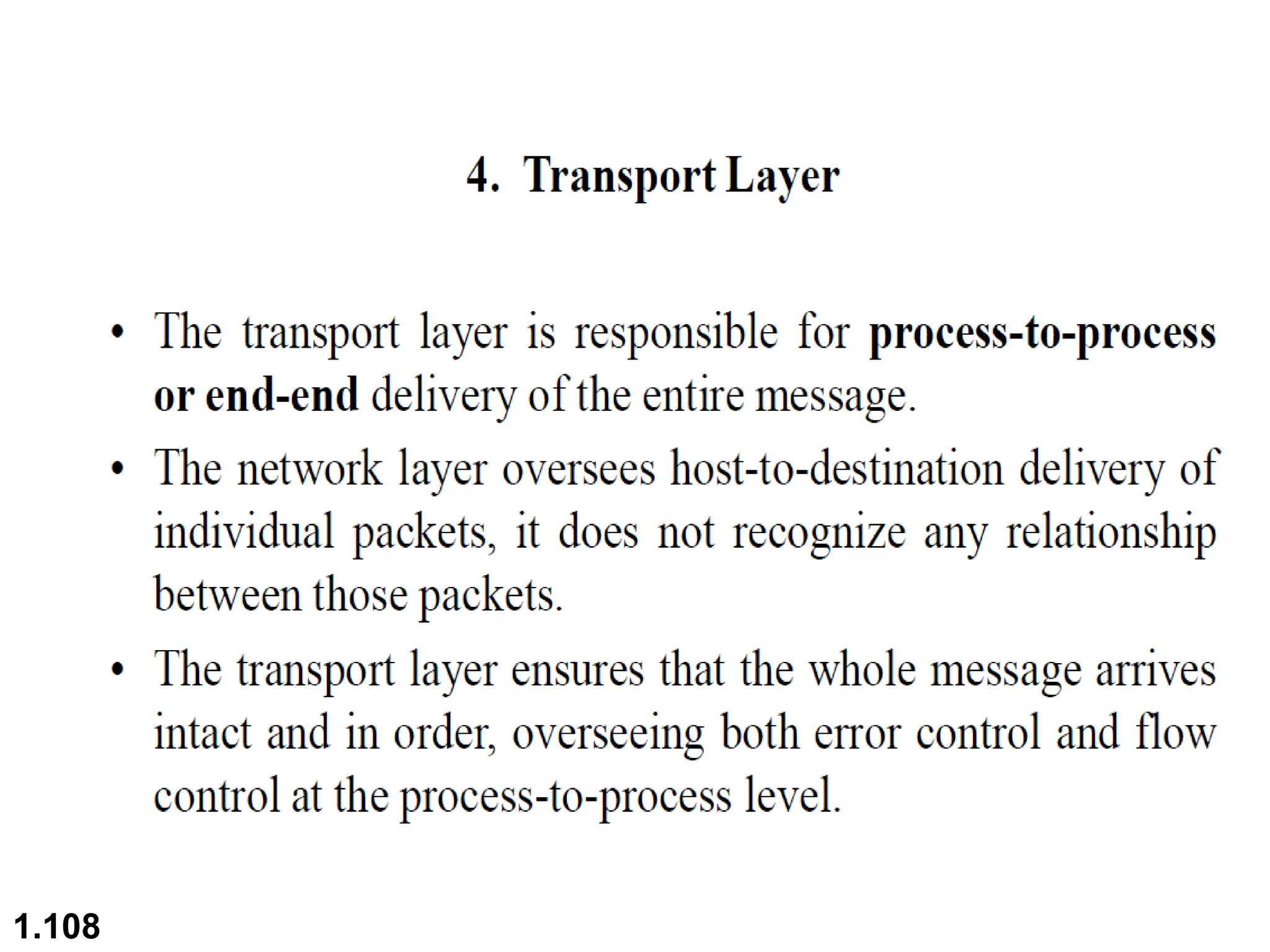
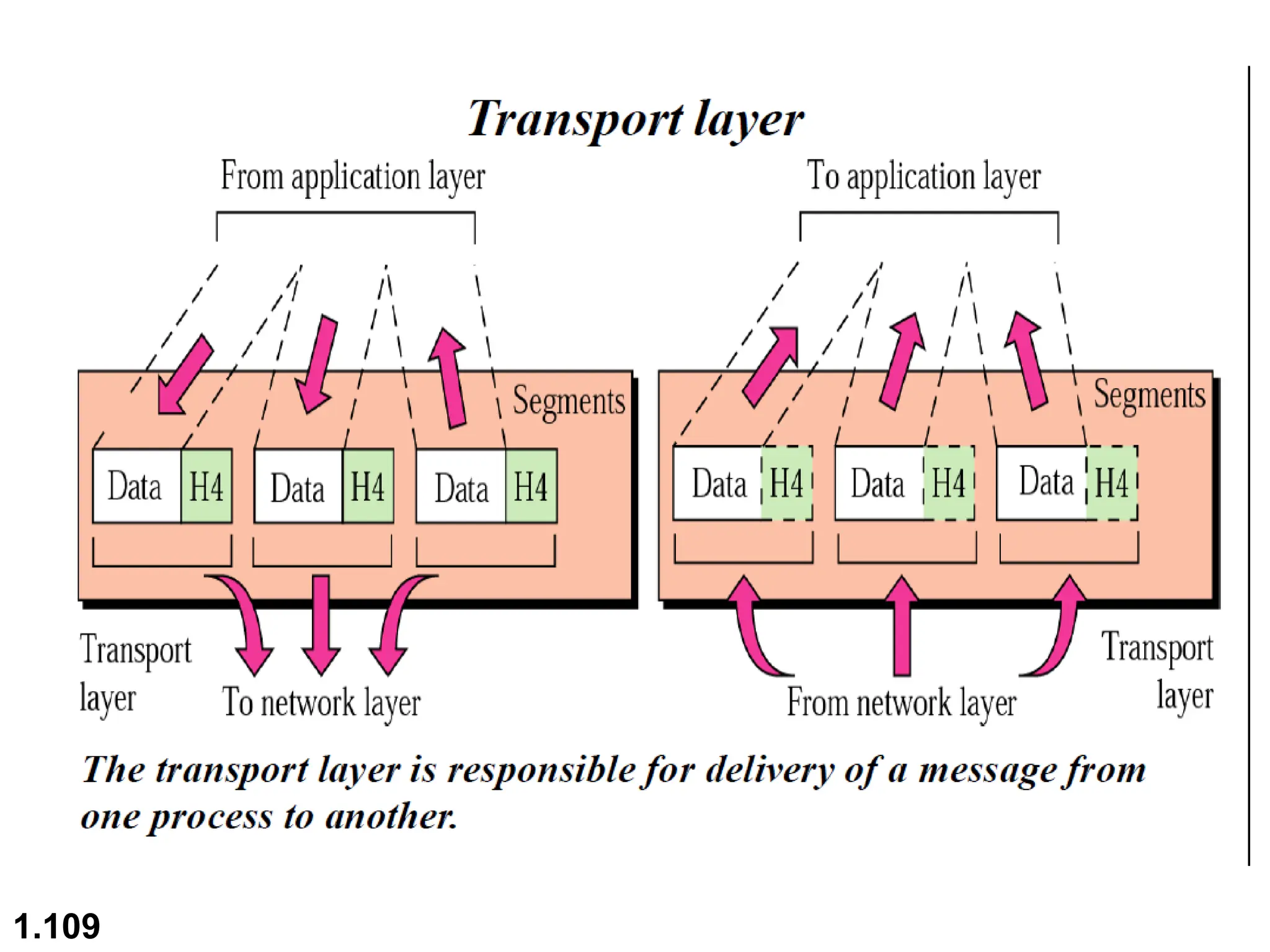
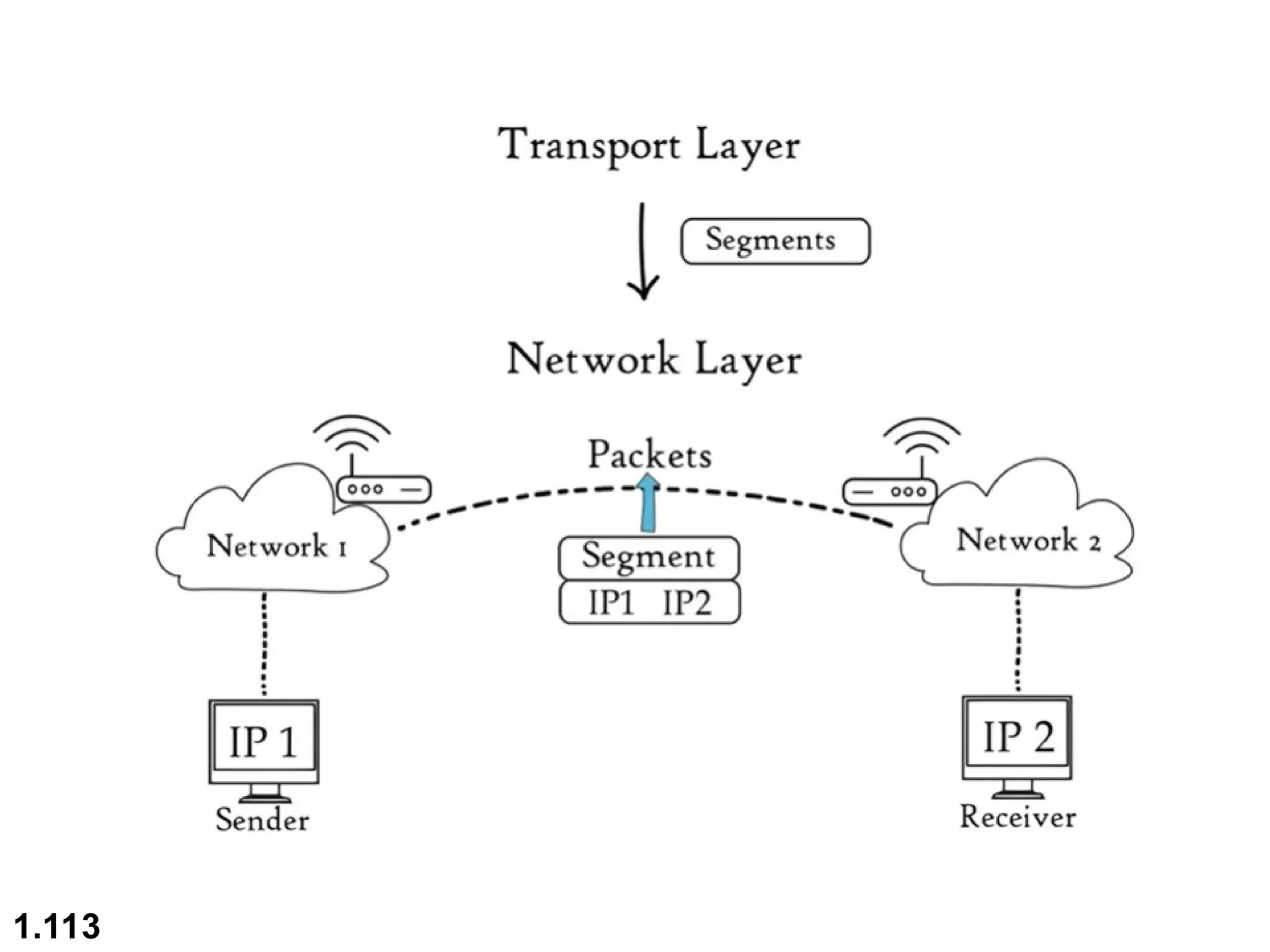
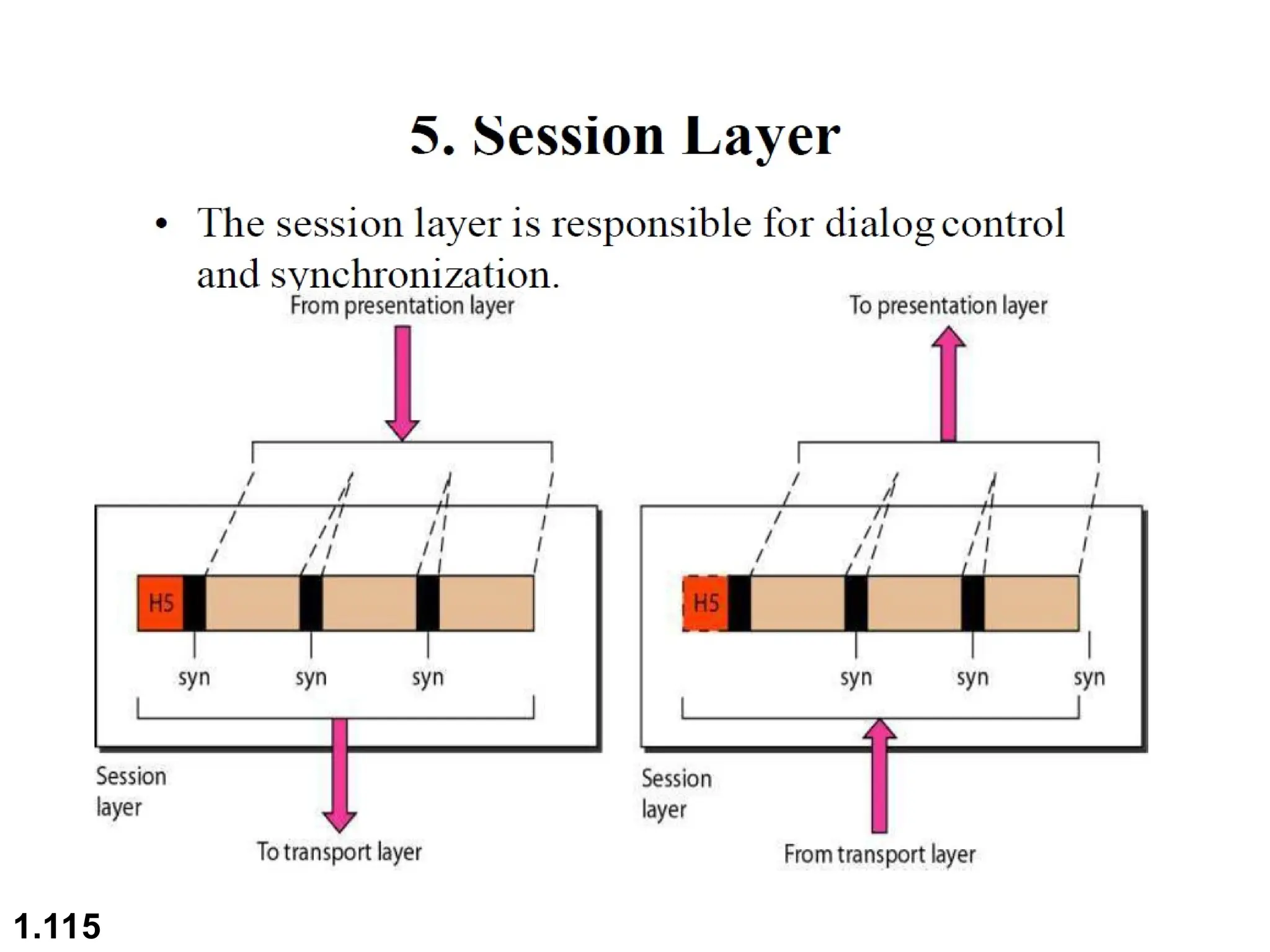
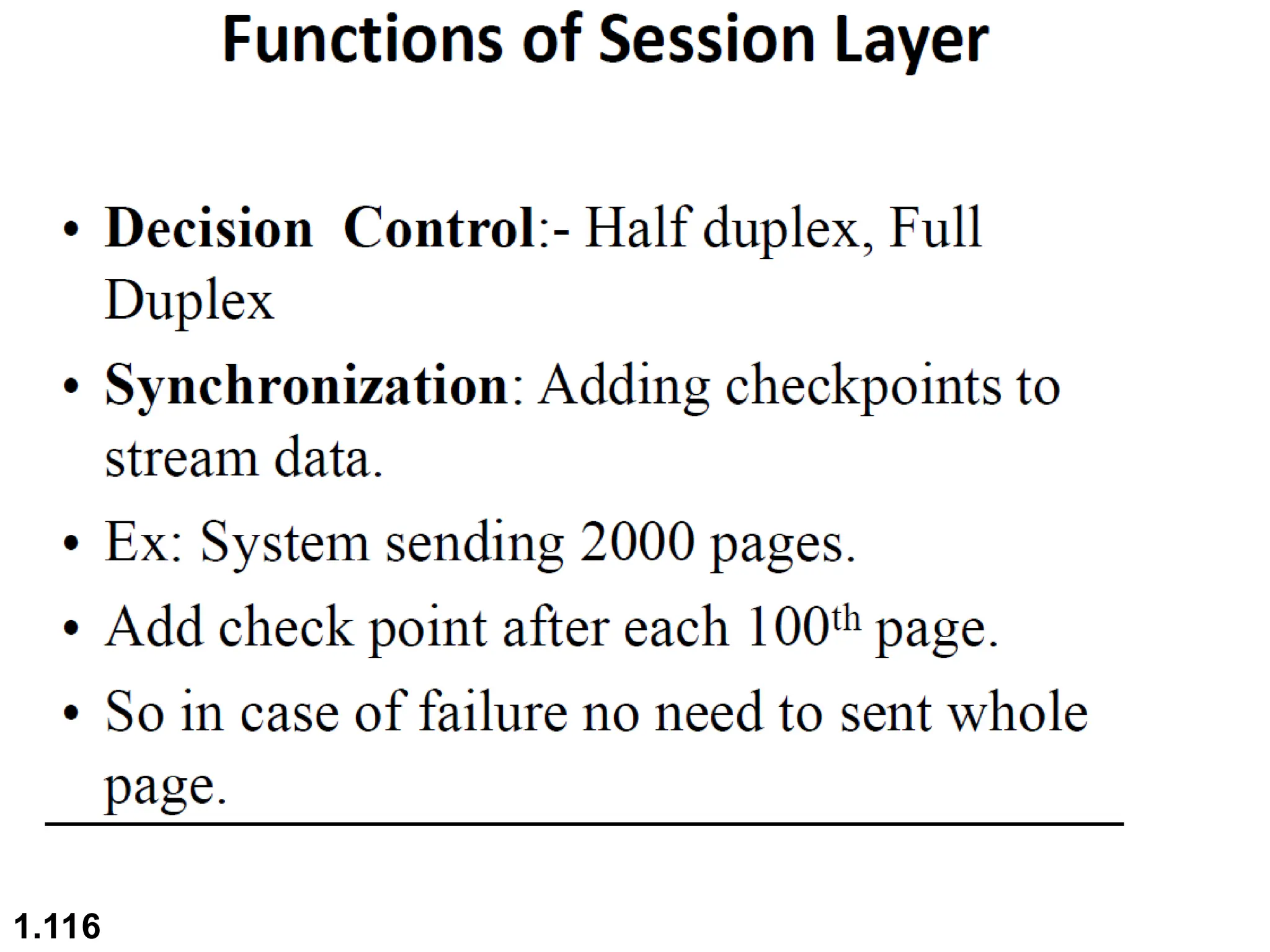
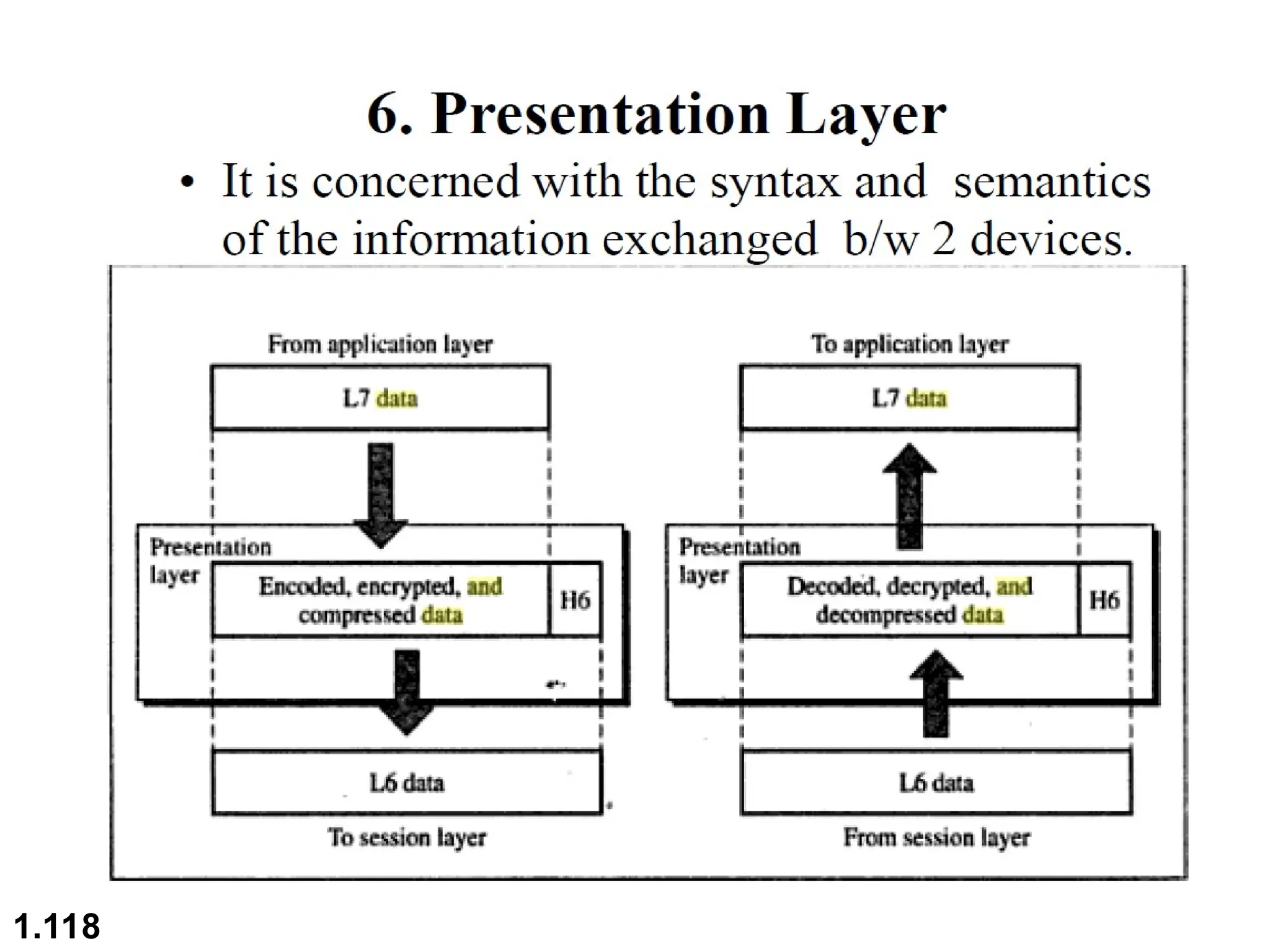
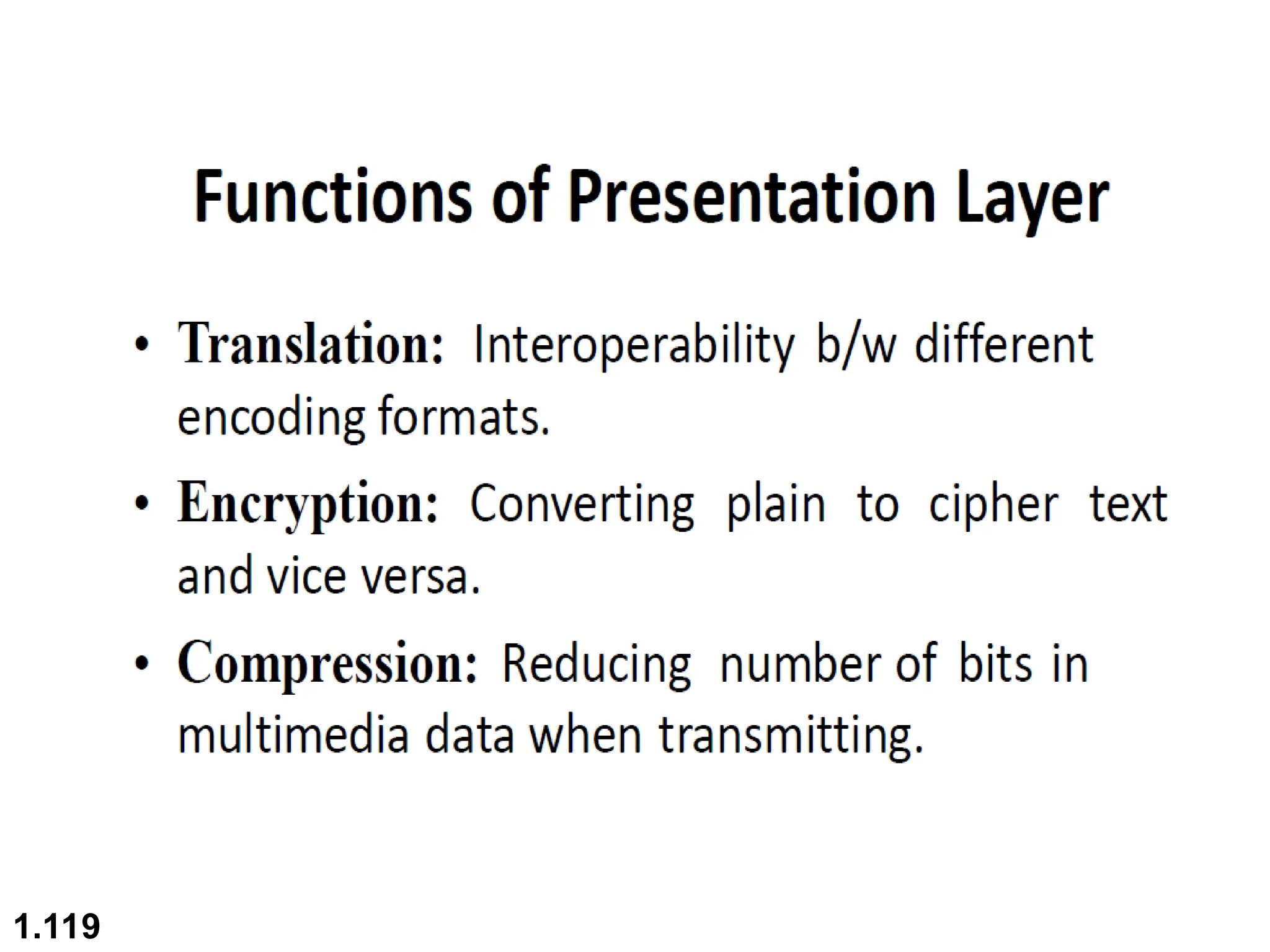
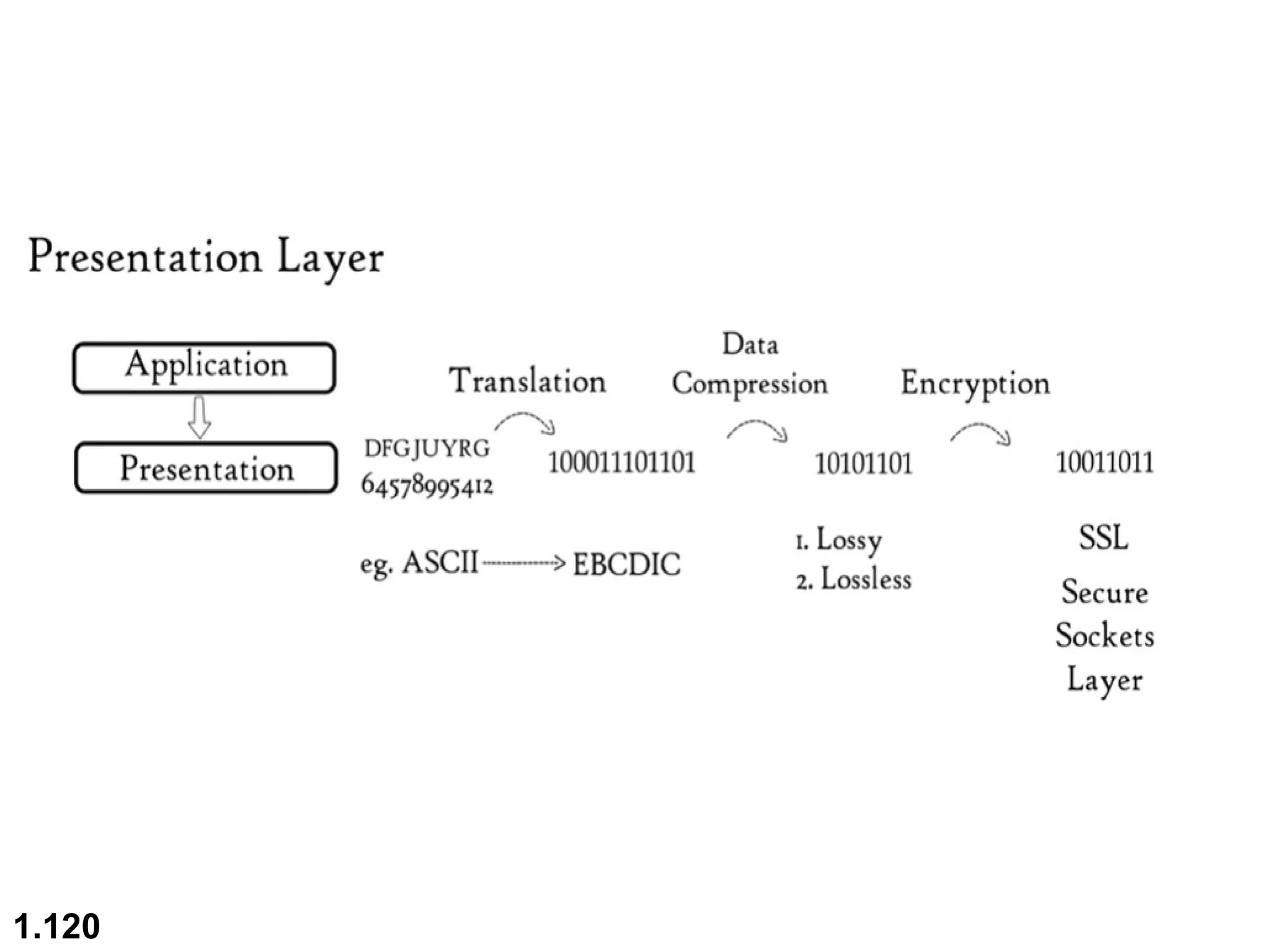
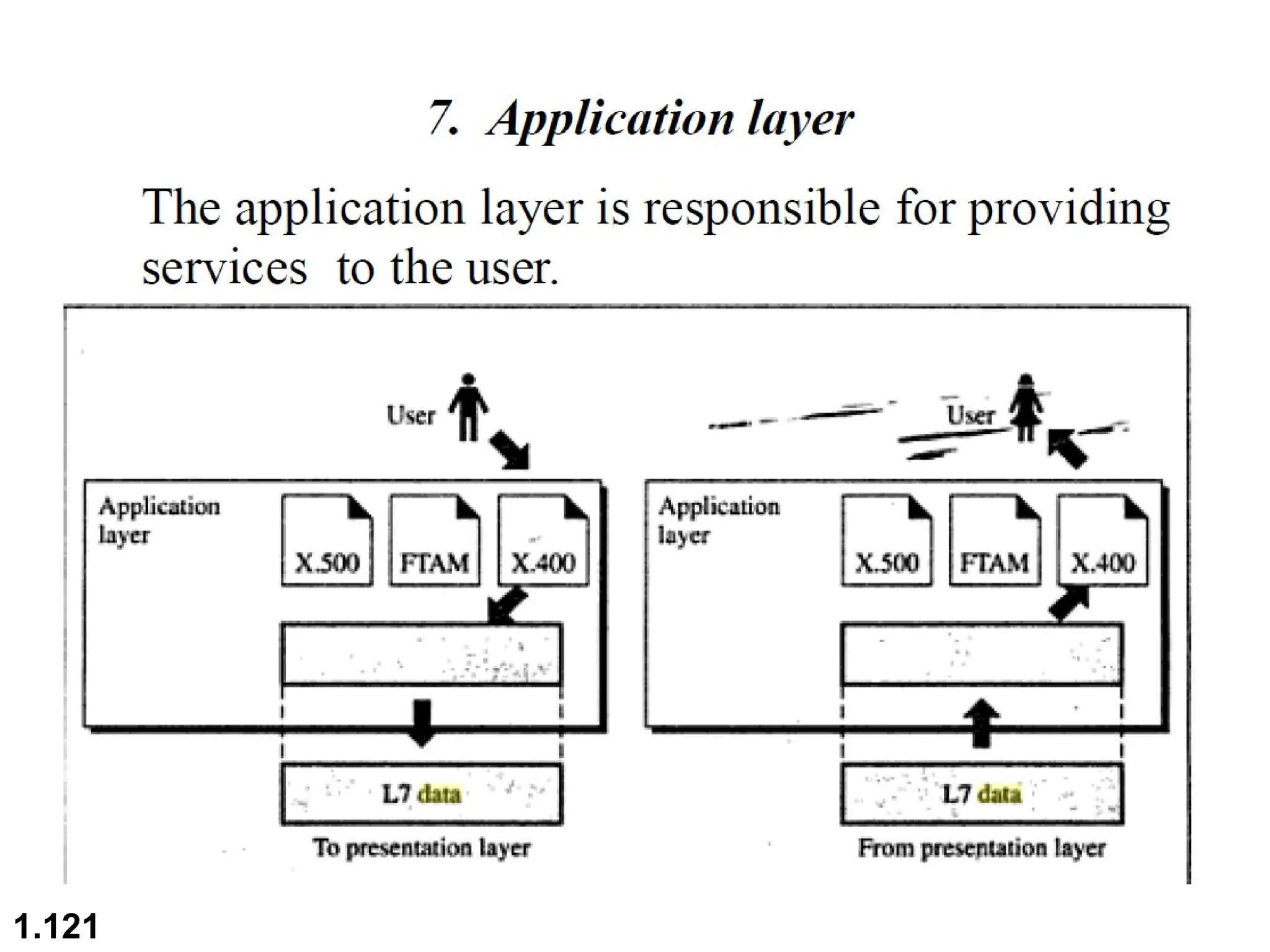
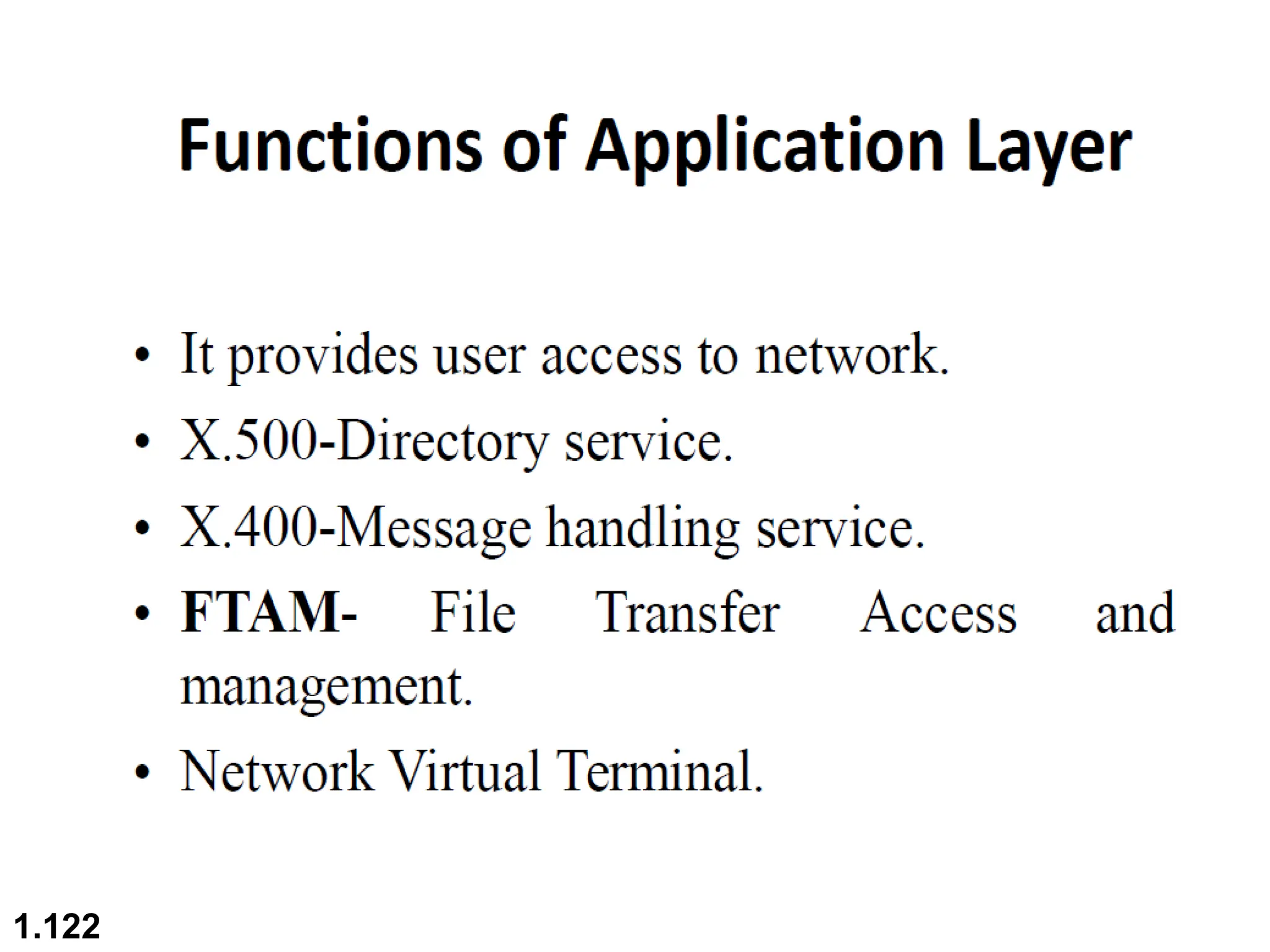
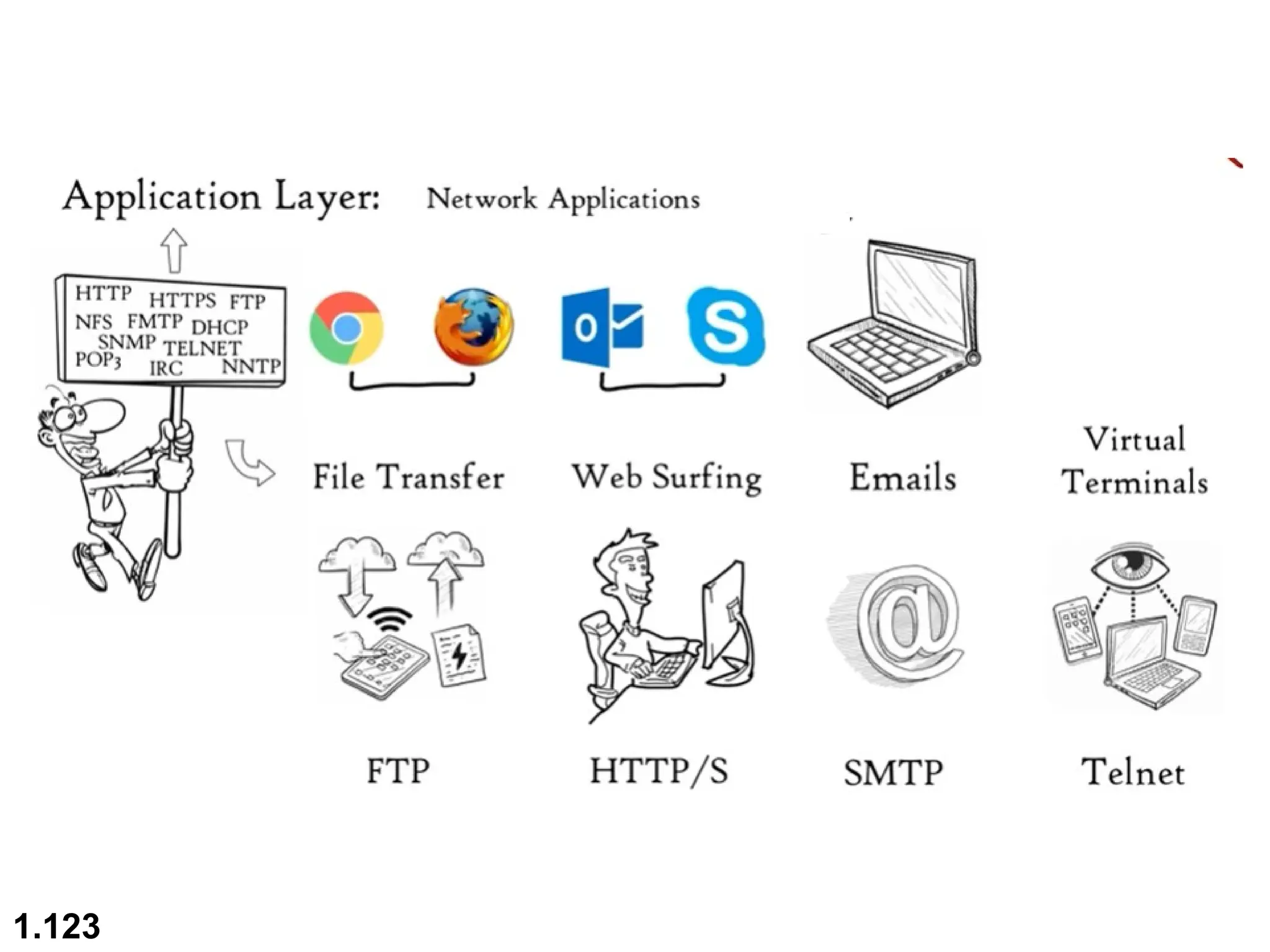
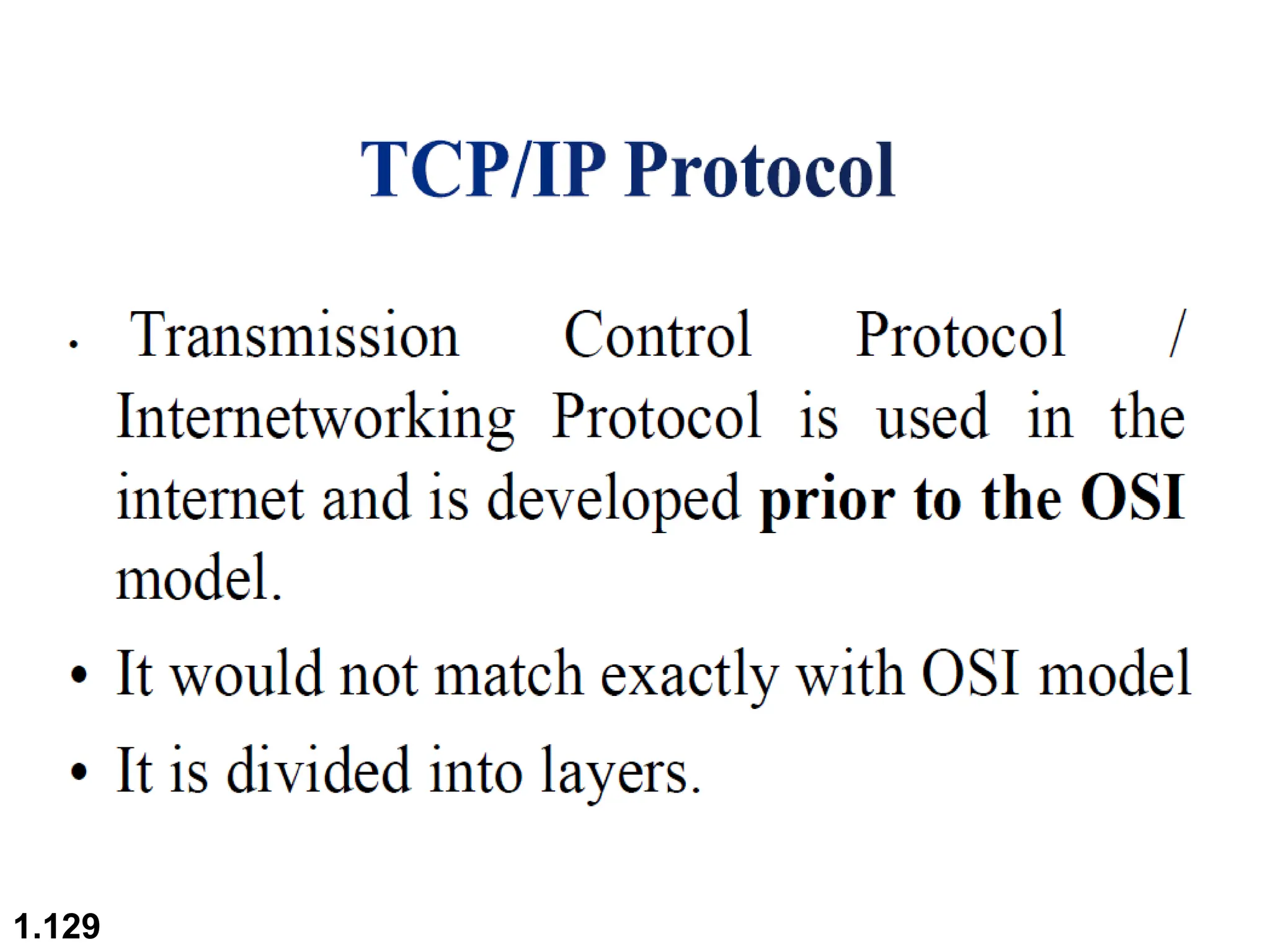
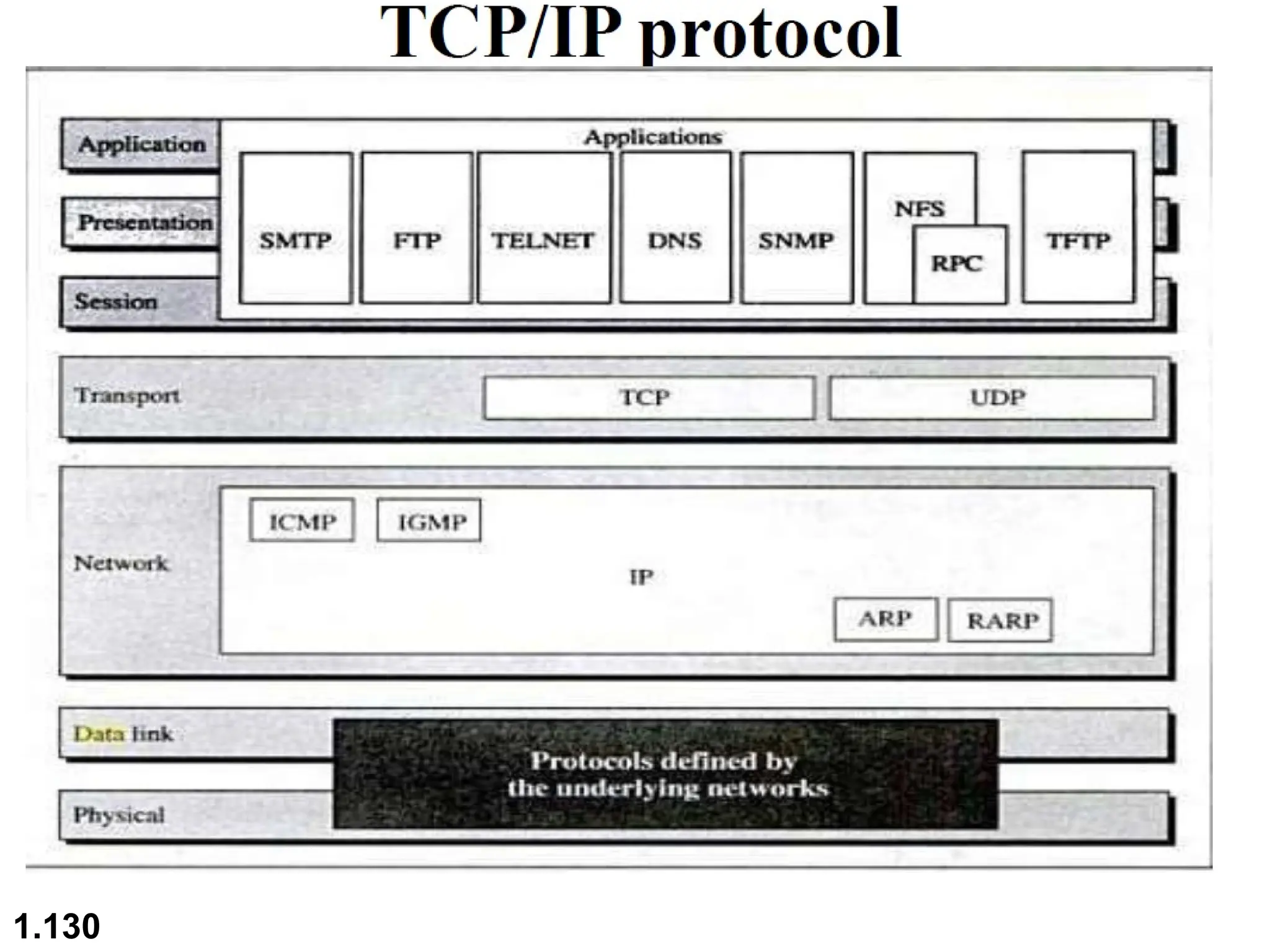
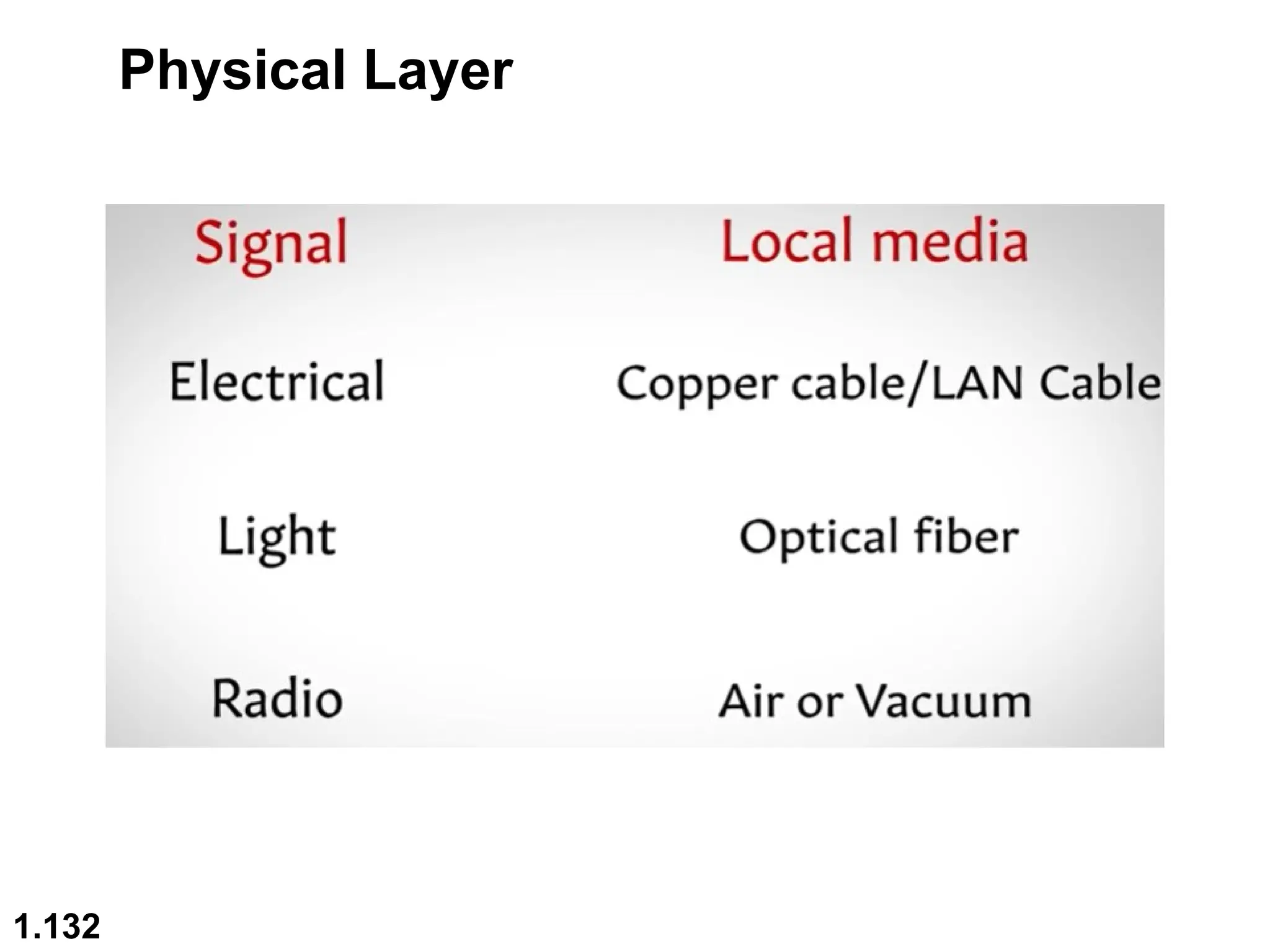
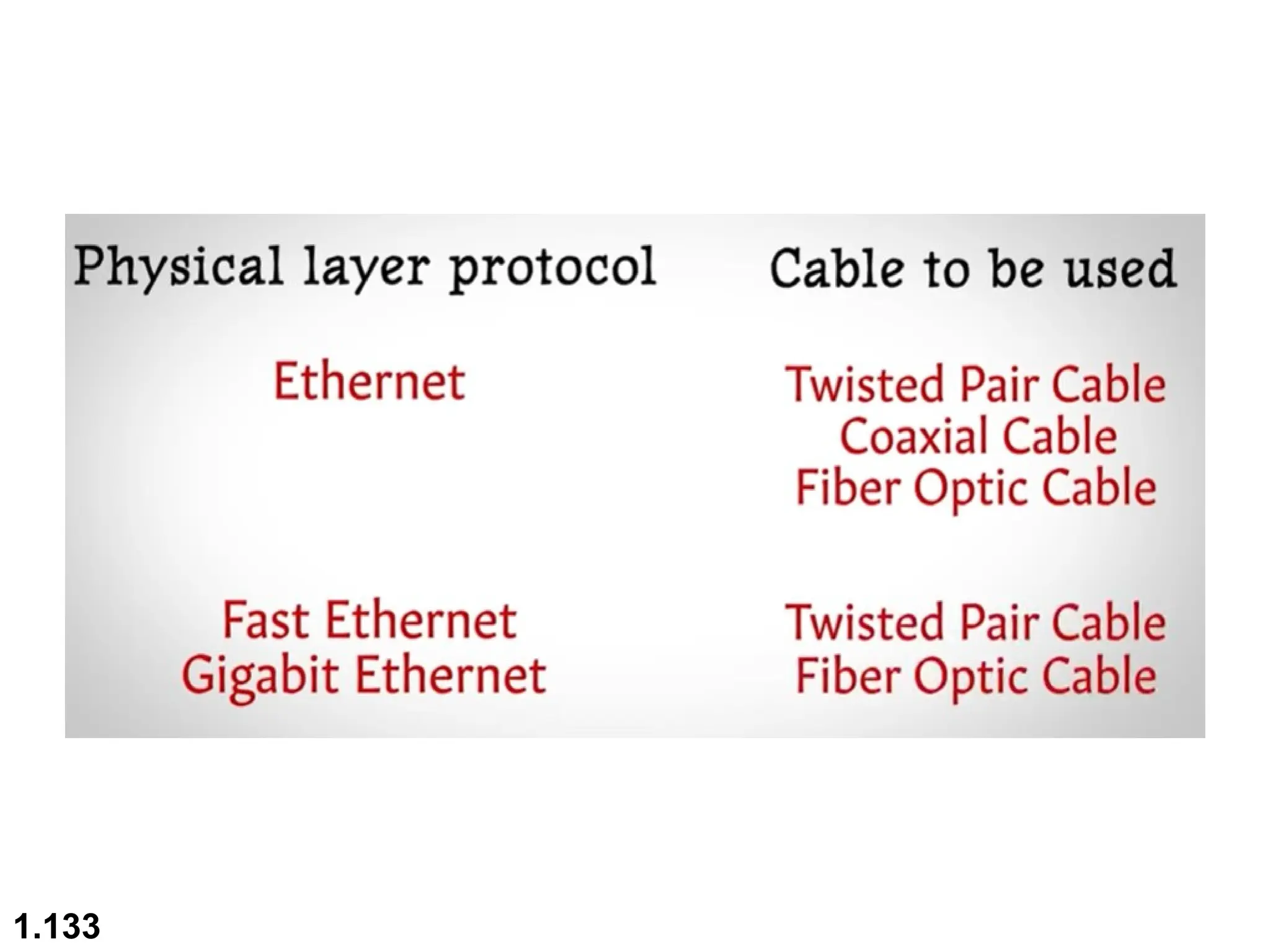
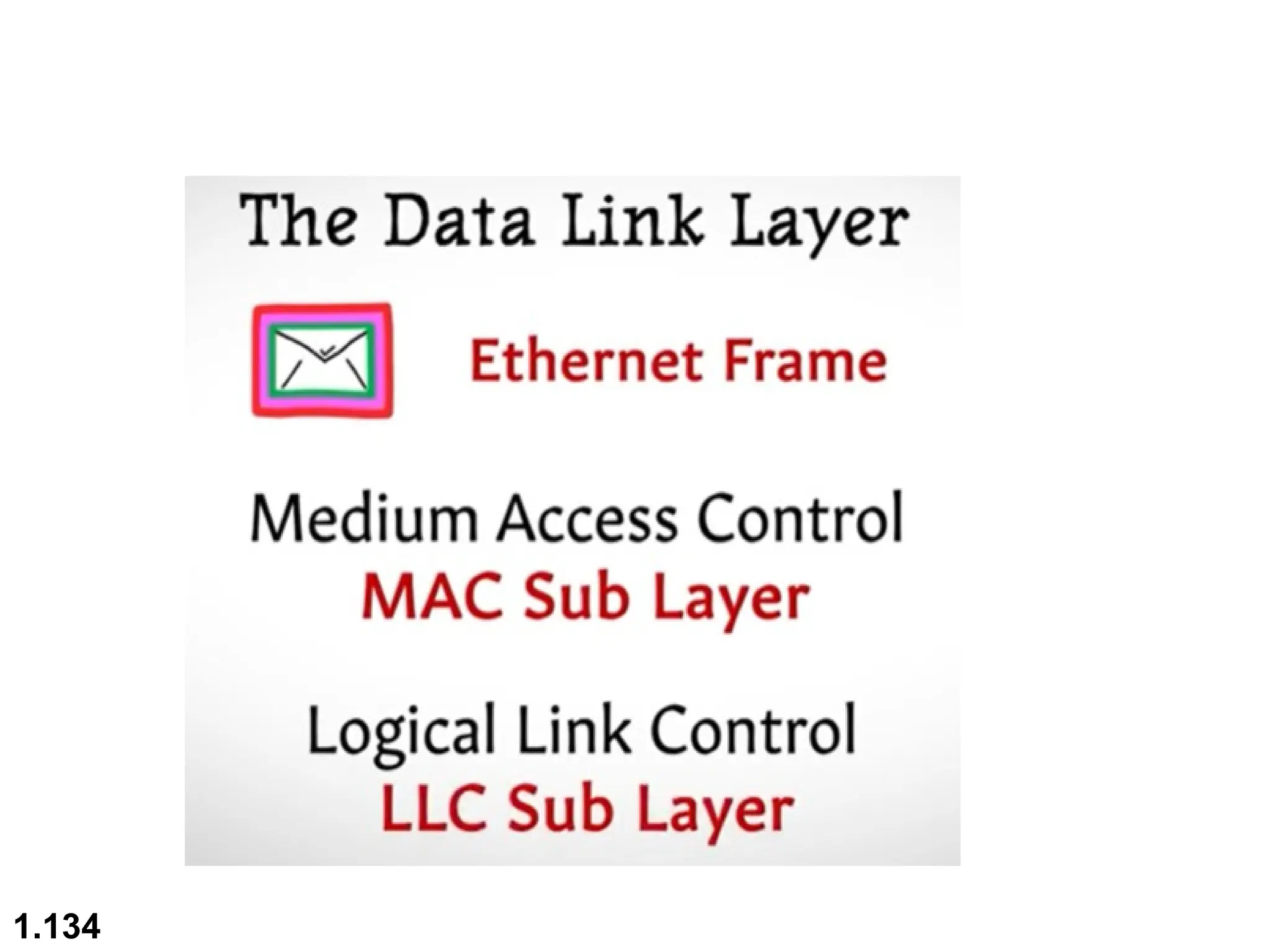
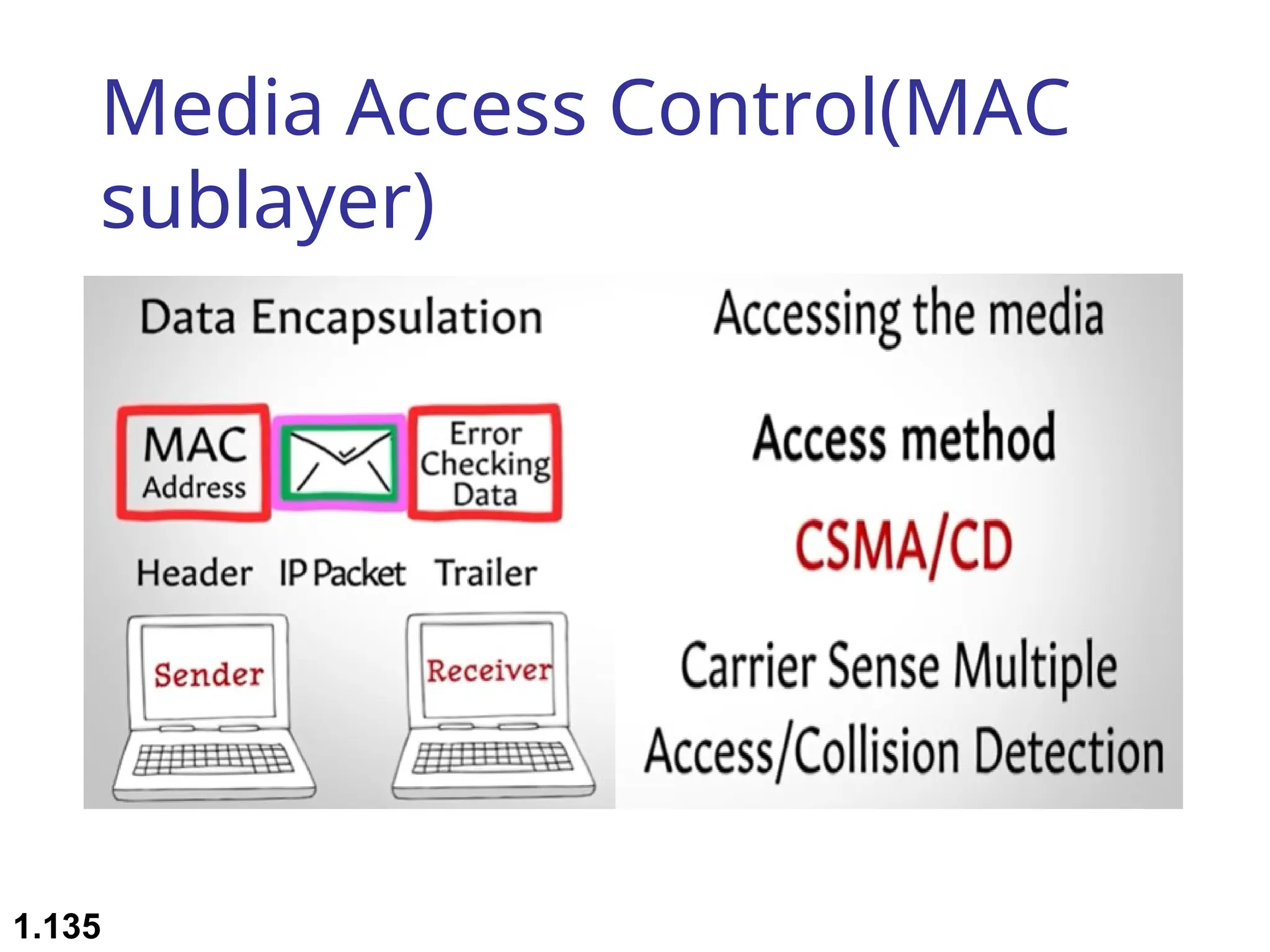
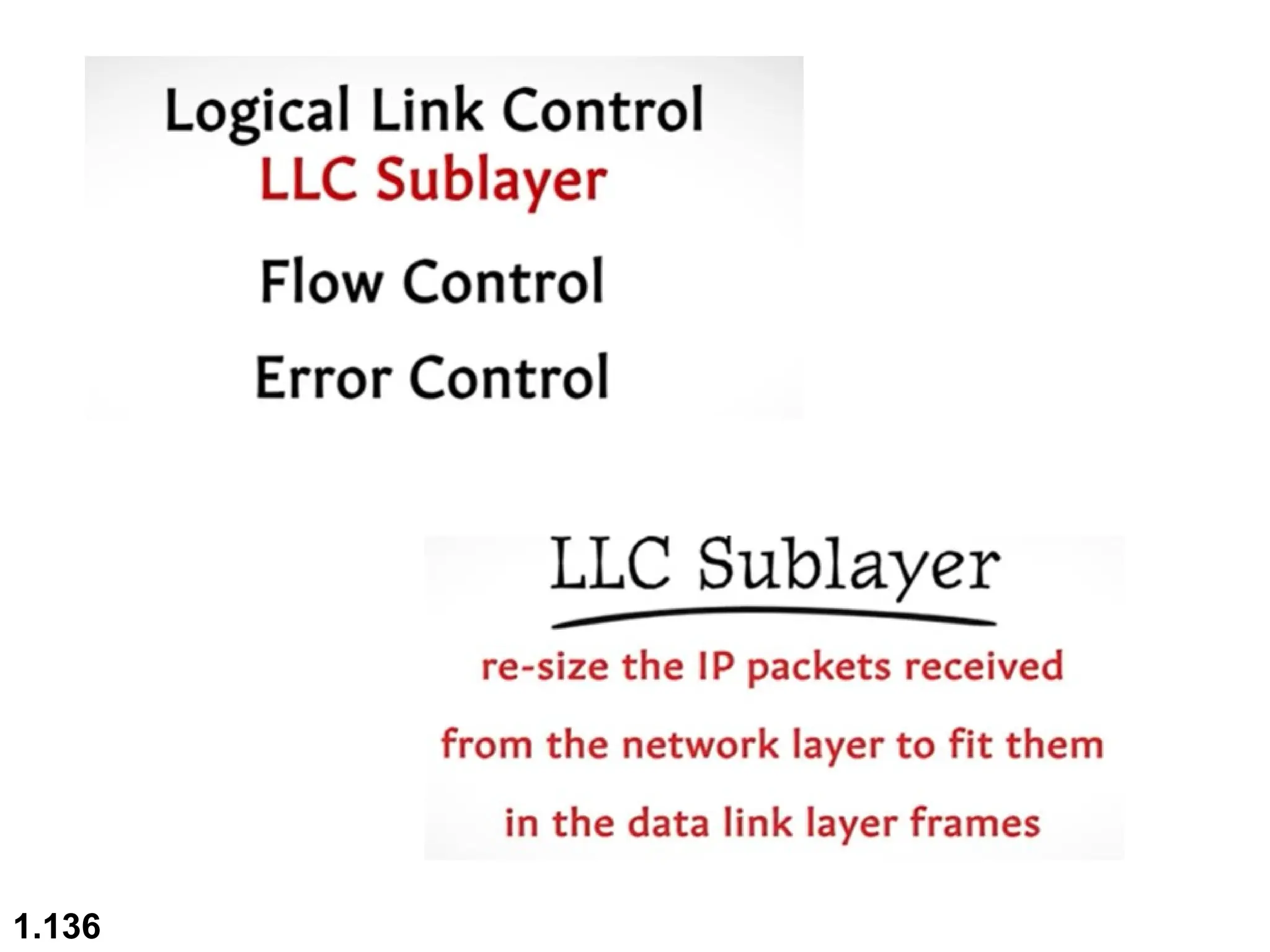
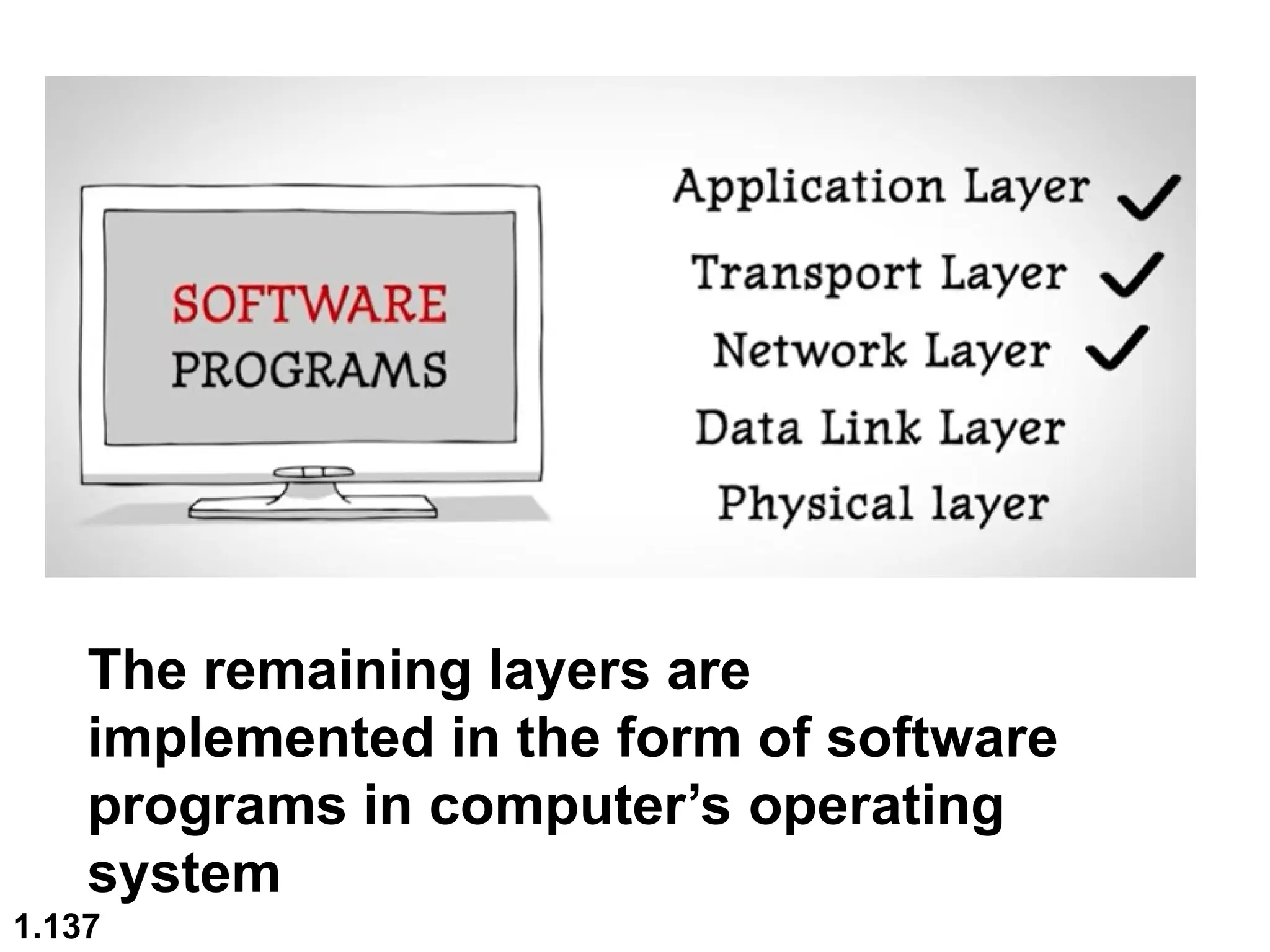
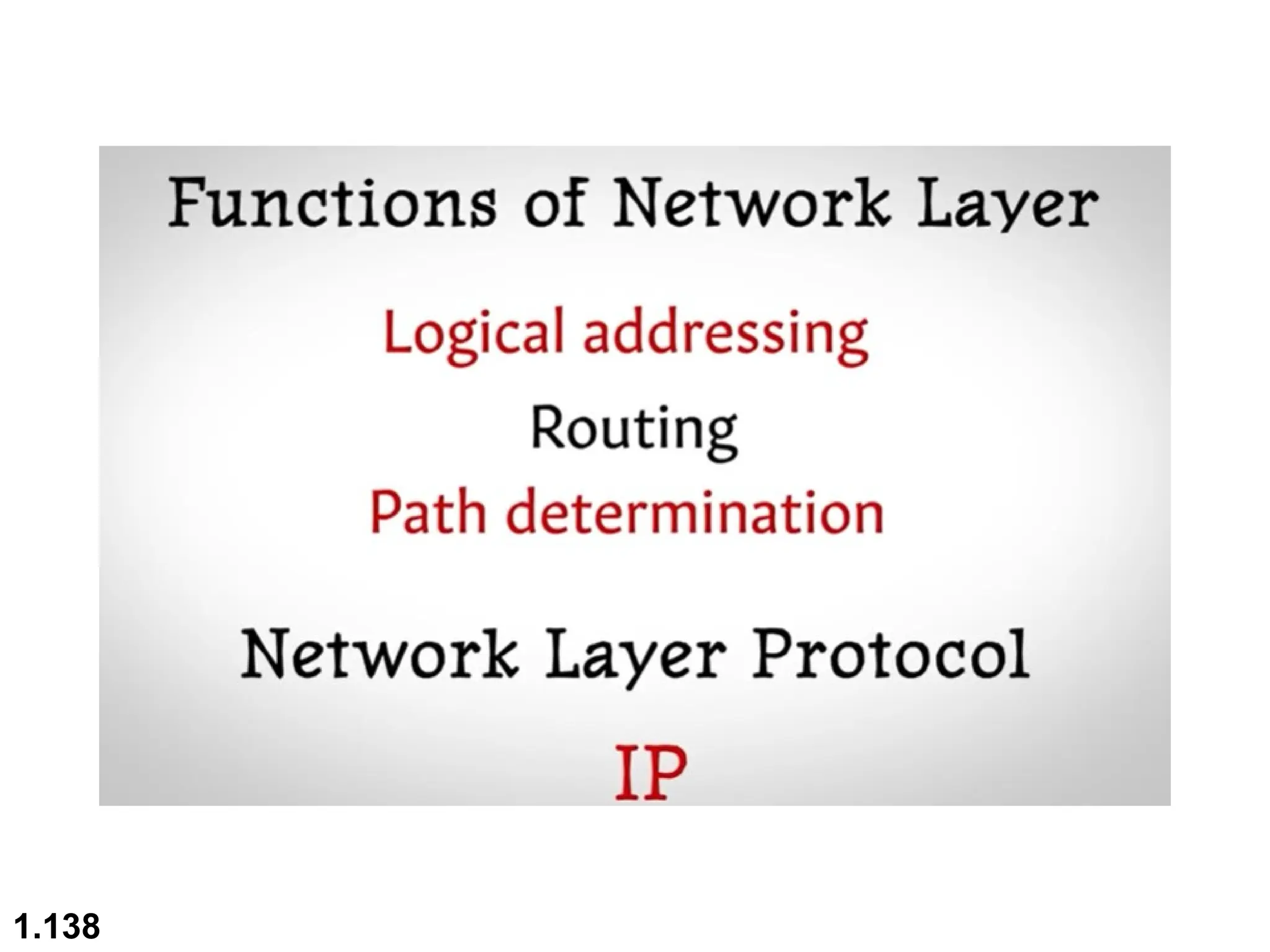
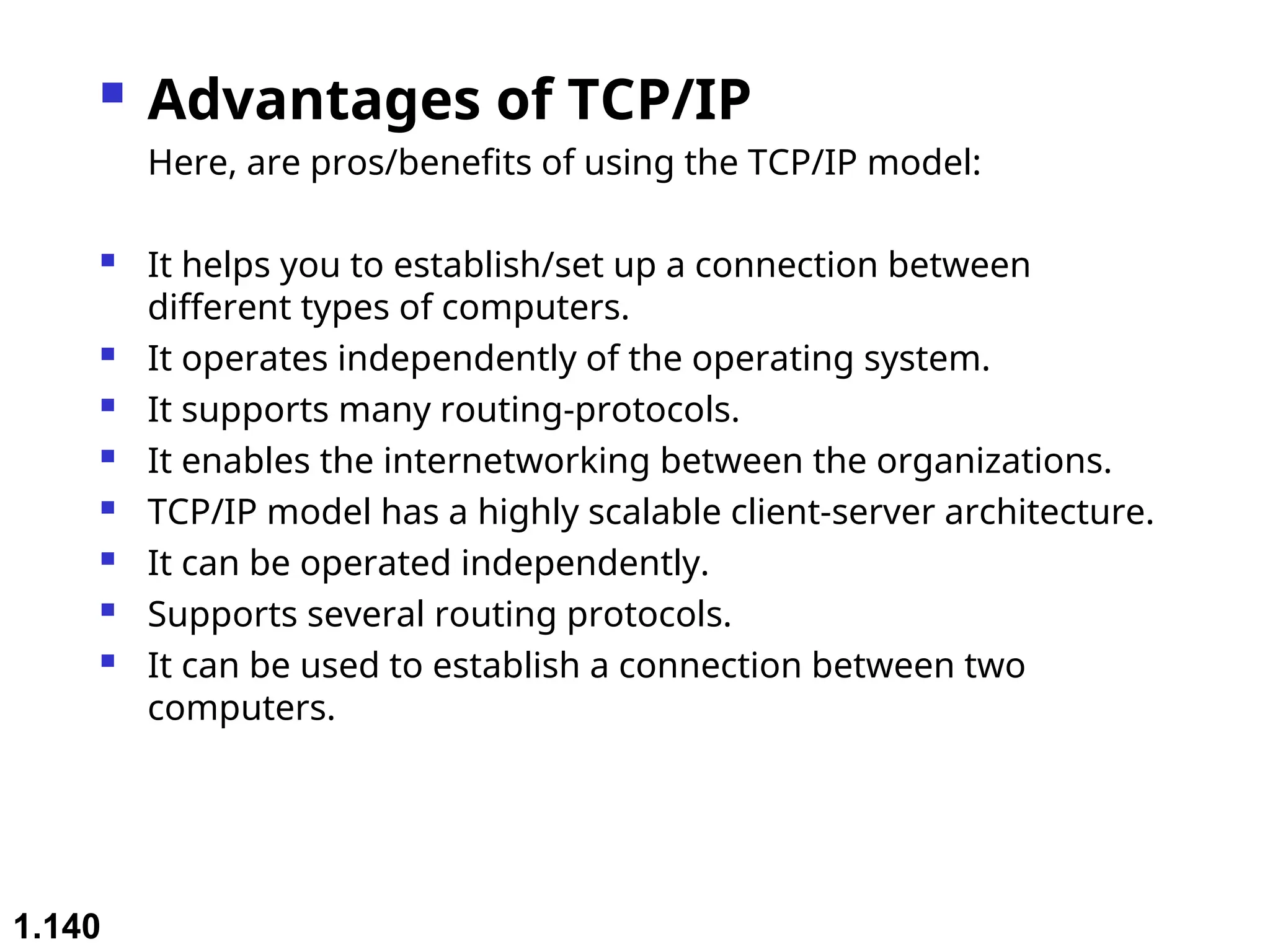
The document outlines the course objectives and examination schemes for a computer networking course, covering both theoretical and practical assessments. It introduces key concepts such as data communications, network components, and various network topologies (mesh, star, bus, ring, tree, hybrid), detailing their functionalities, advantages, and disadvantages. Additionally, the document discusses types of networks including LANs, WANs, and MANs, along with the internet's structure and the importance of protocols in data communication.