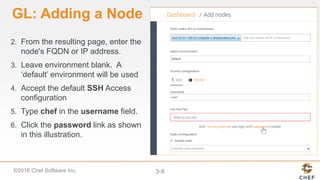
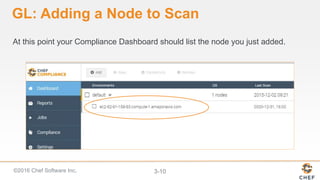
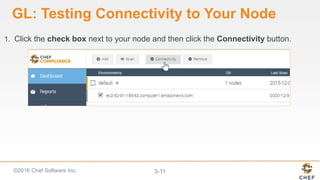
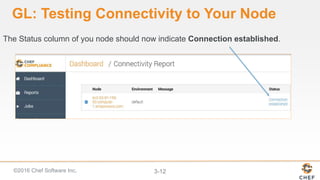
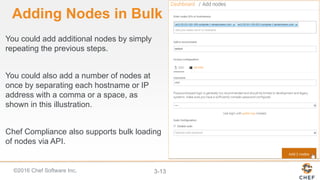
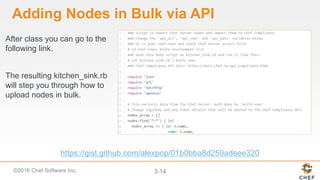
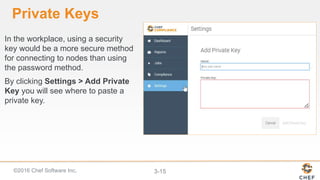
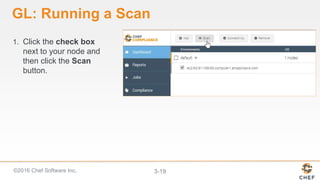
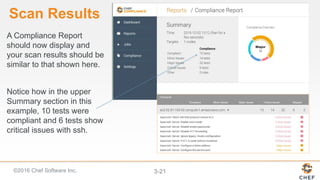
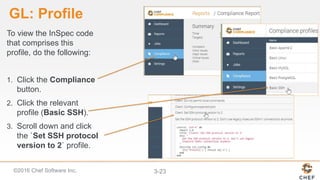
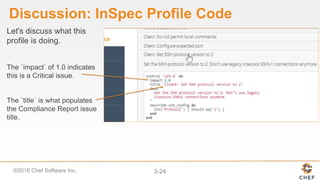
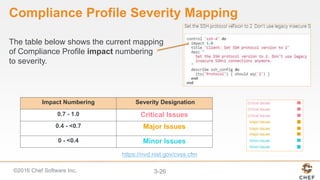
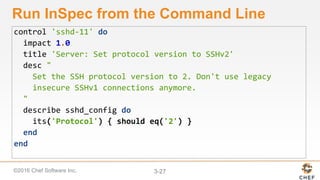
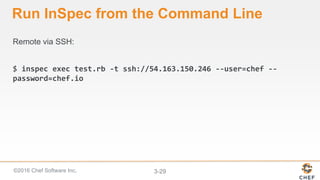
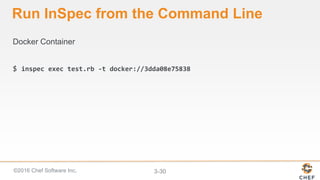
InSpec can be used to automate security and compliance testing by translating compliance policies into code. This allows organizations to find issues early in the development process and continuously test configurations as code is built, tested, and deployed. The document discusses adding nodes to scan from the Chef Compliance dashboard, running compliance scans using built-in profiles, and viewing scan results to identify compliant and non-compliant controls. It also provides instructions for running InSpec tests directly from the command line locally or against remote systems using SSH or Docker.