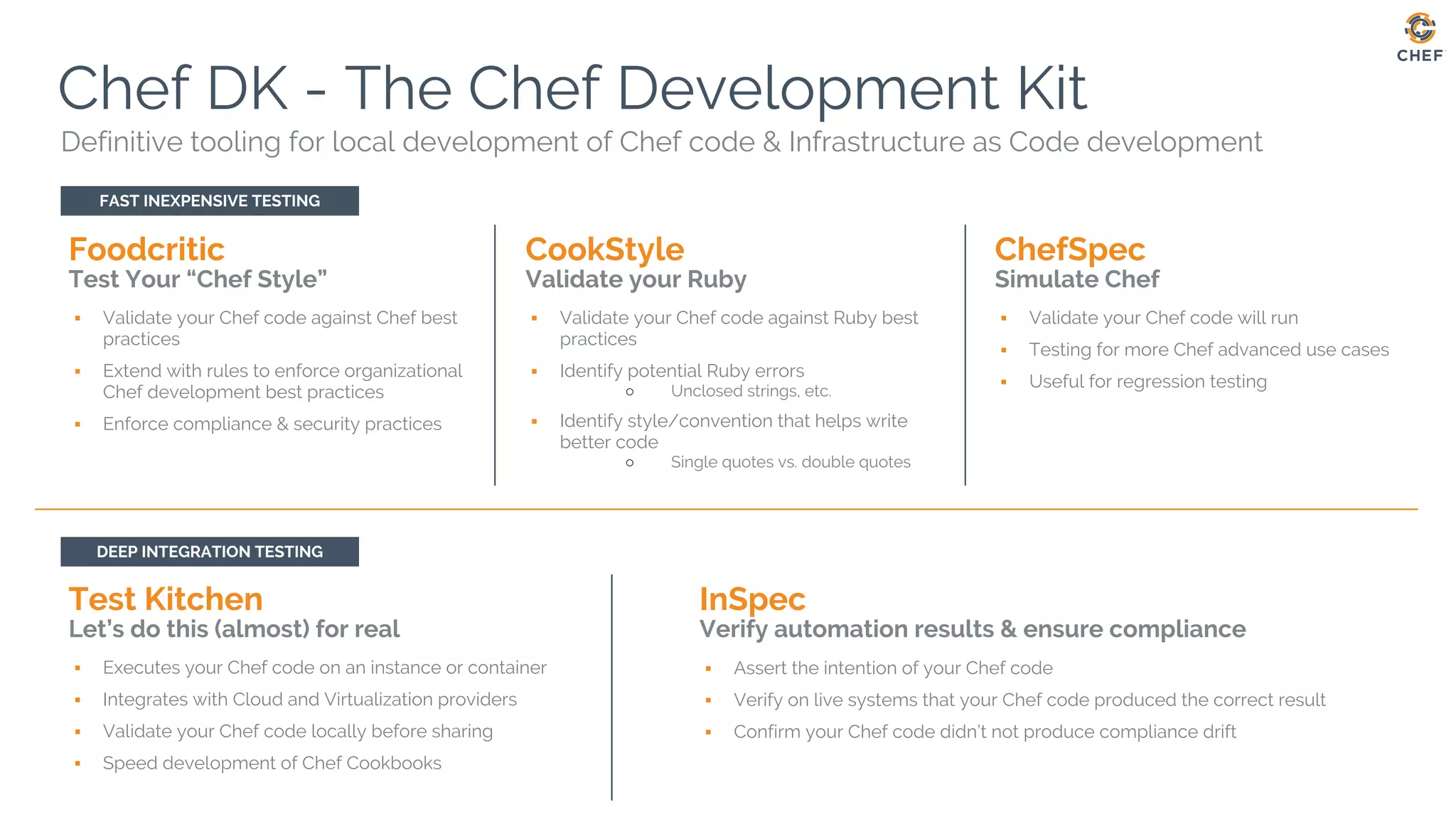
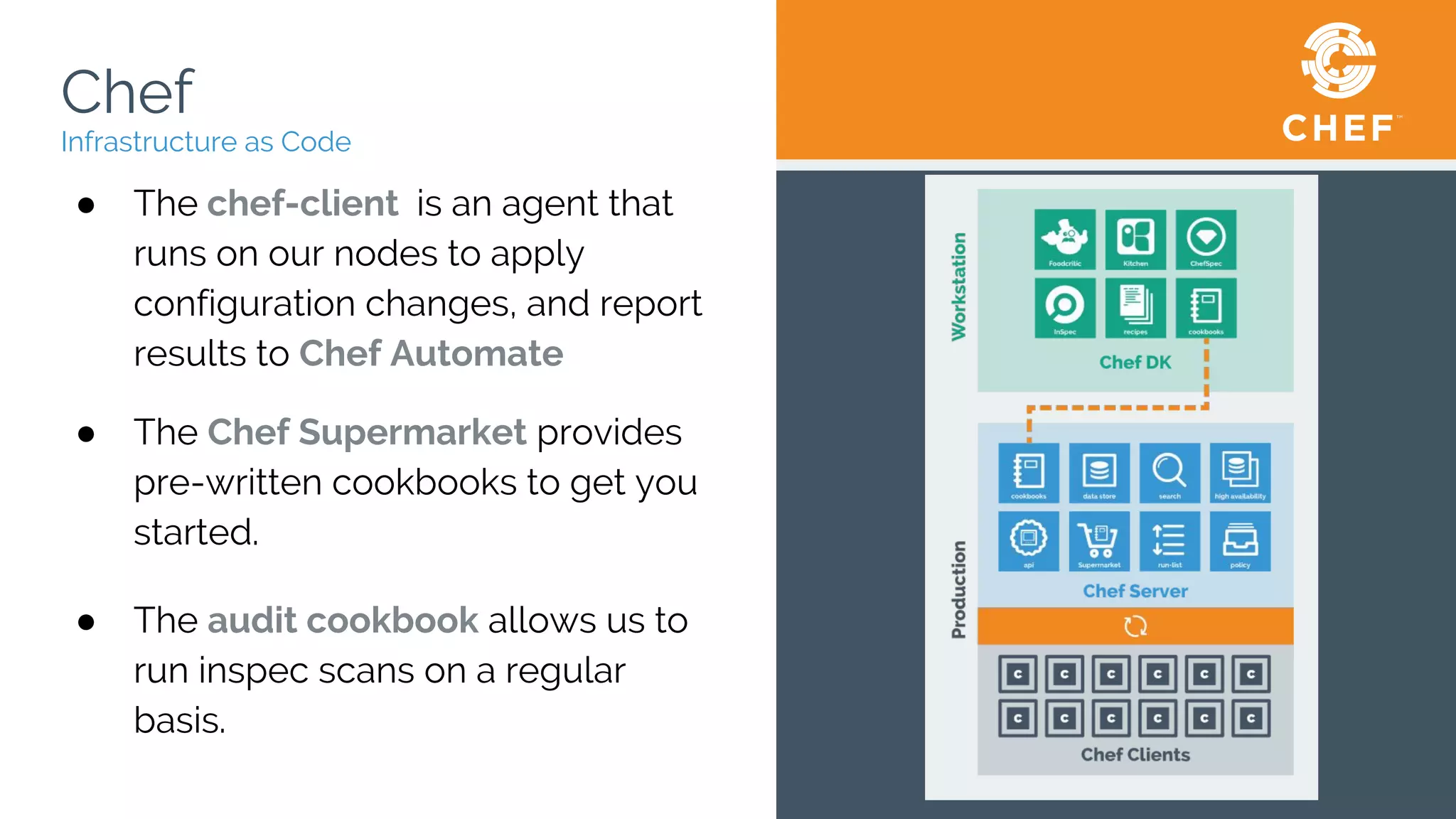
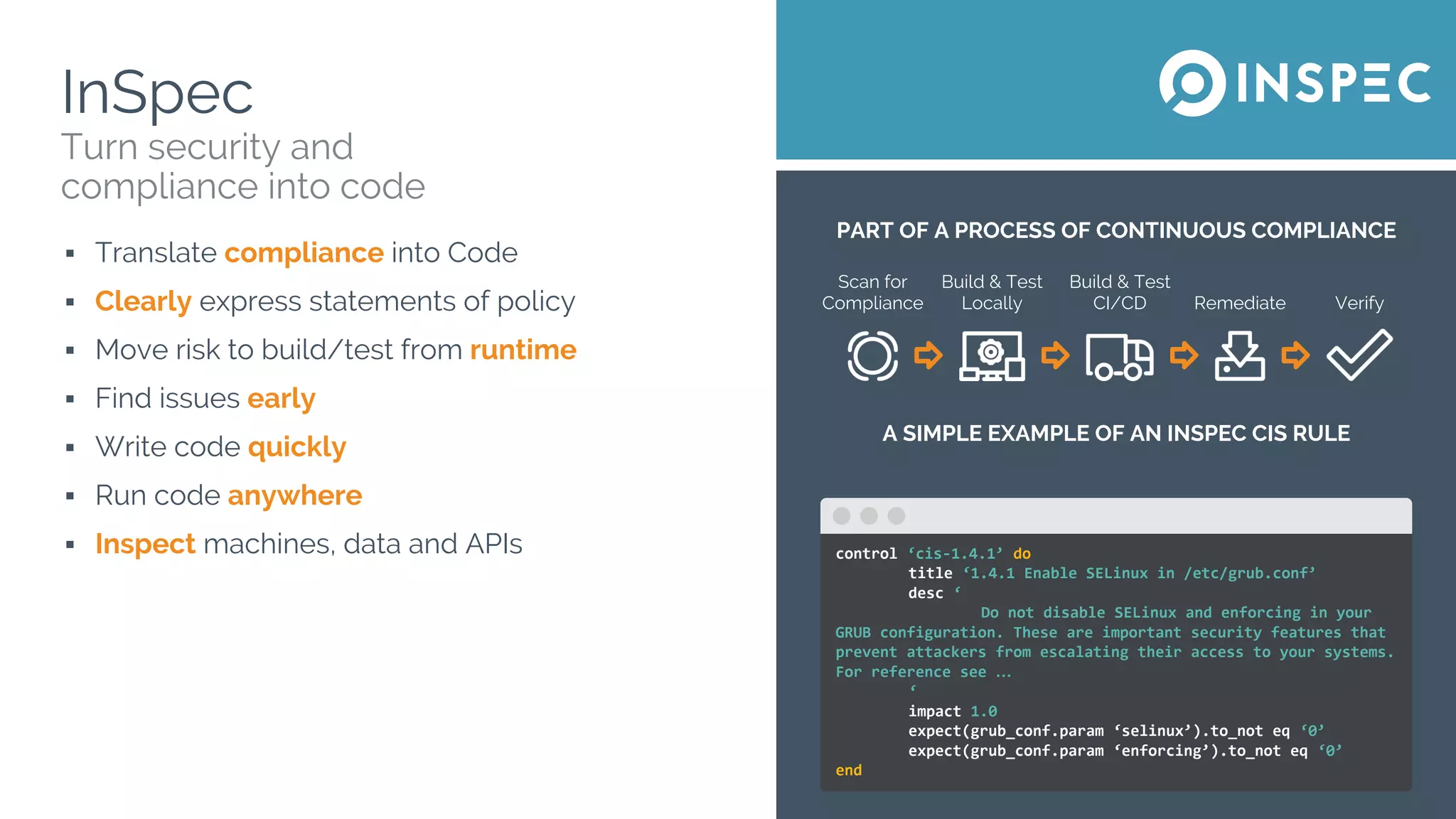
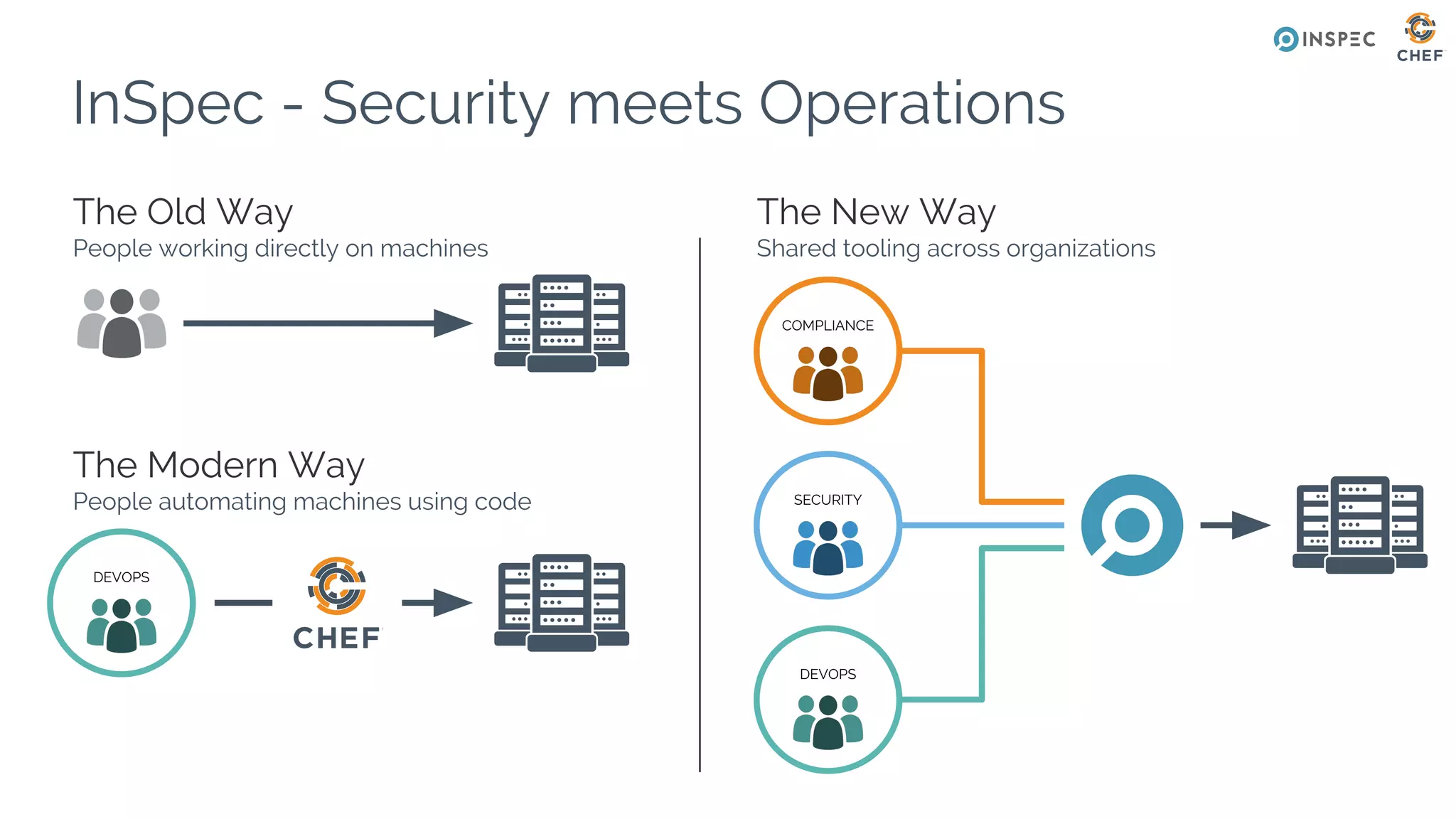
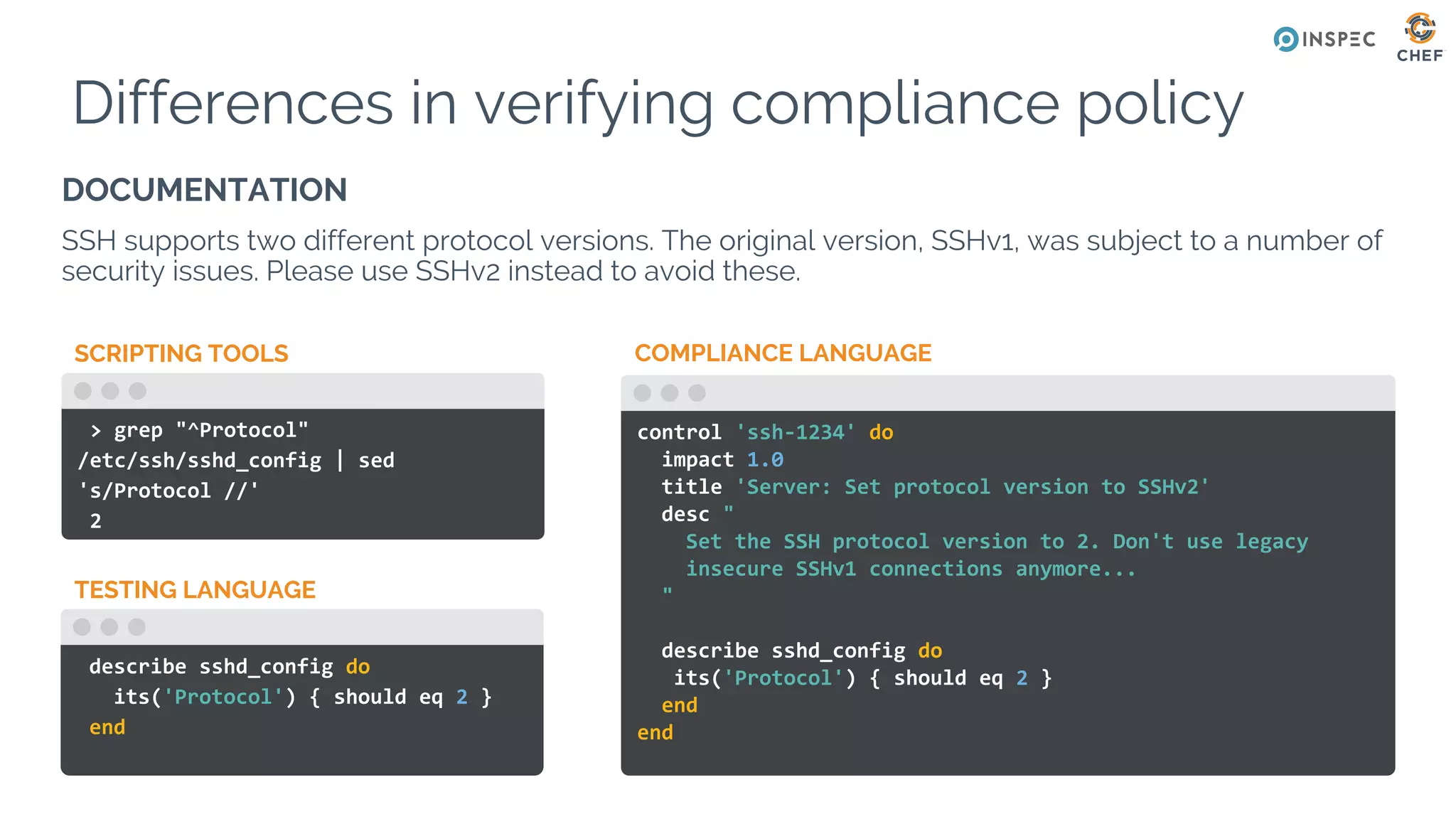
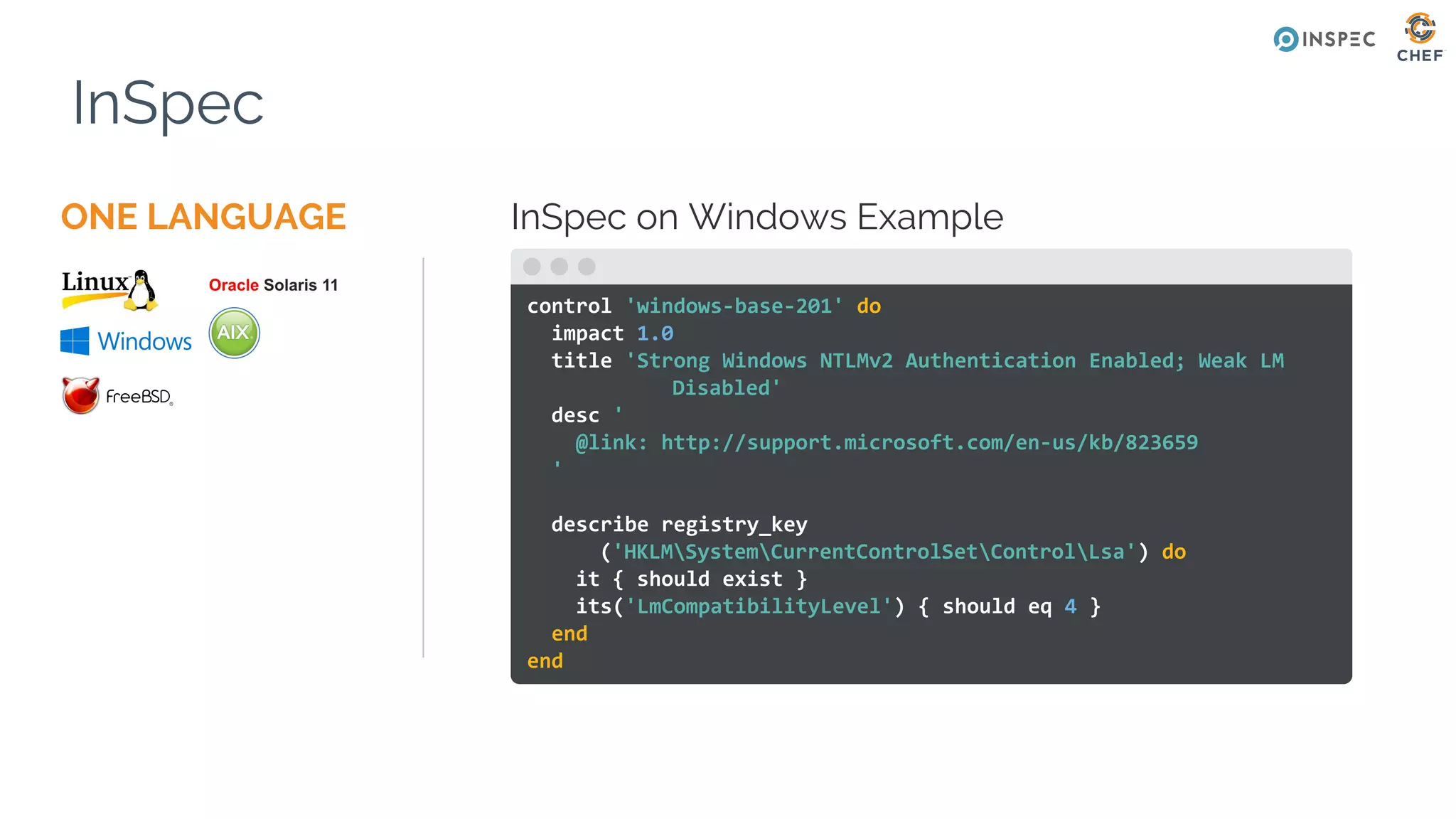
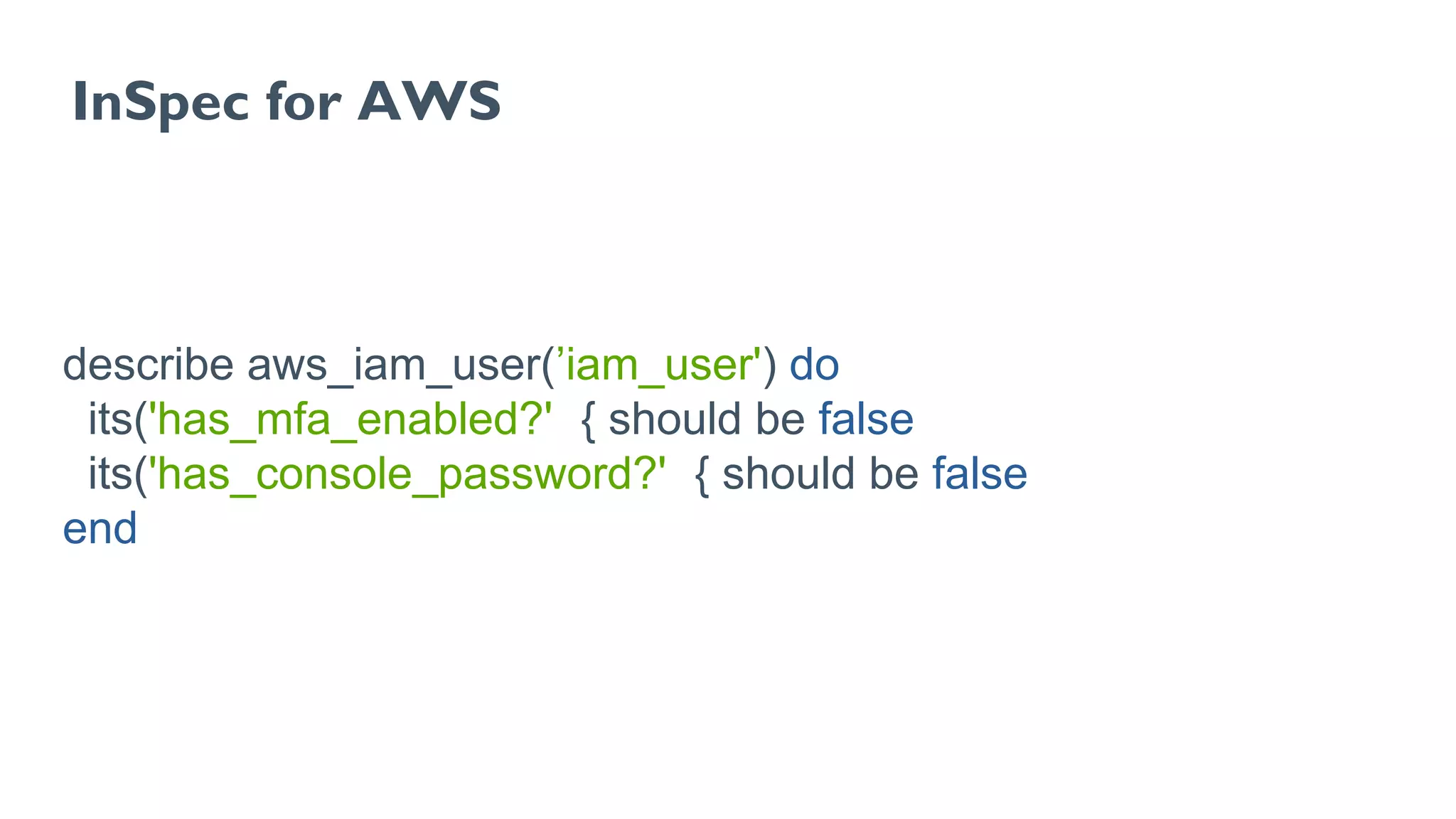
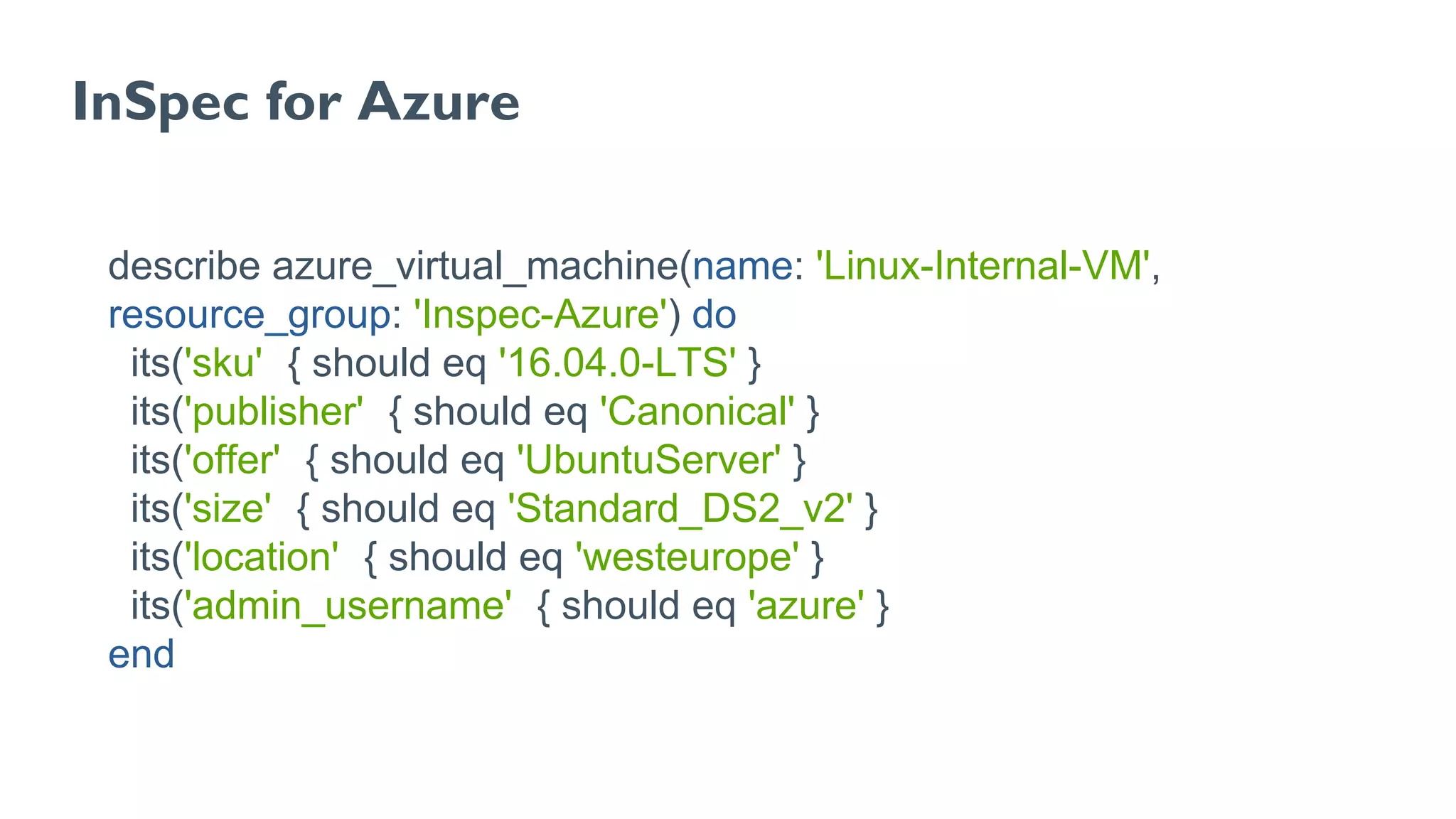
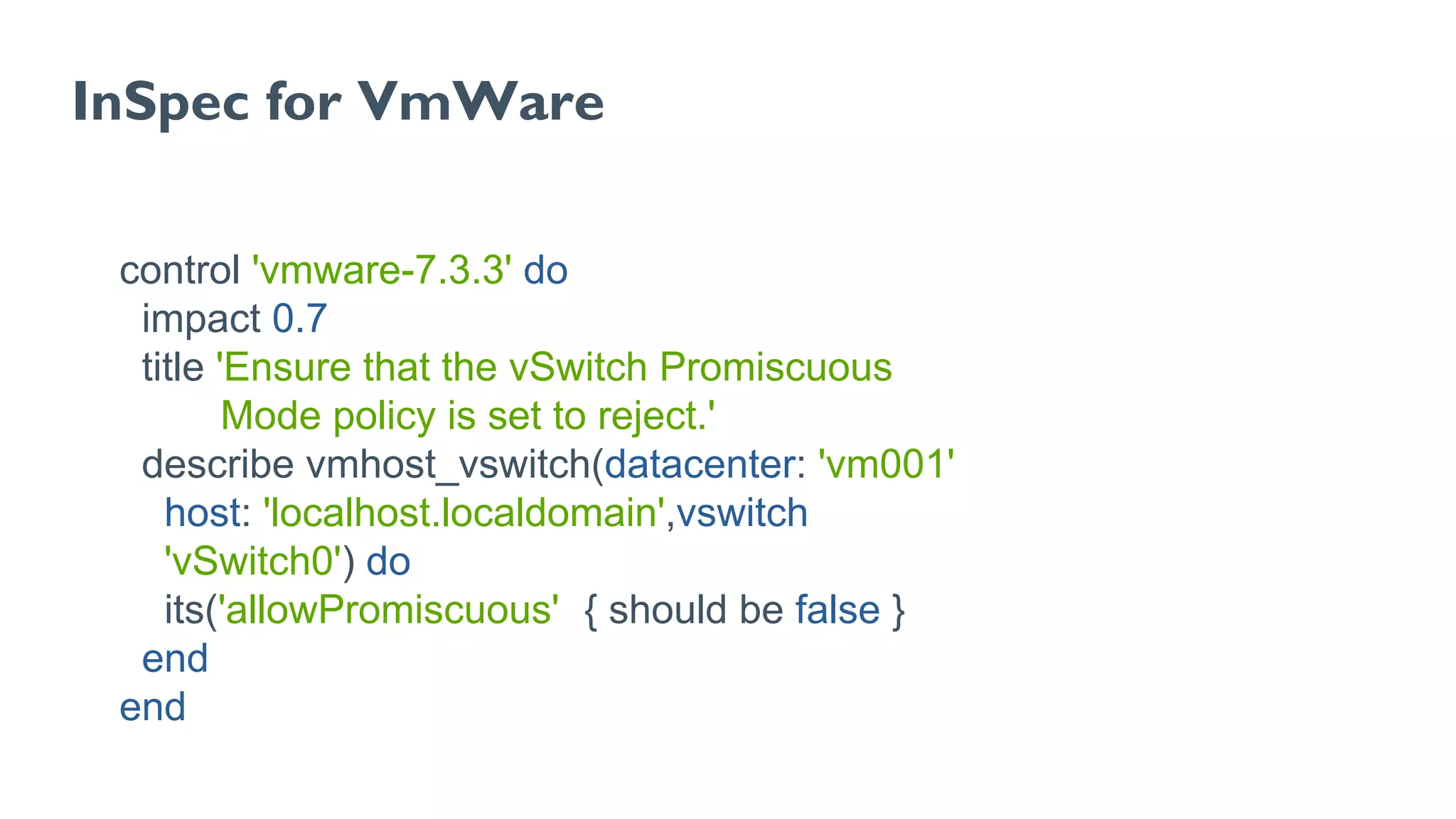
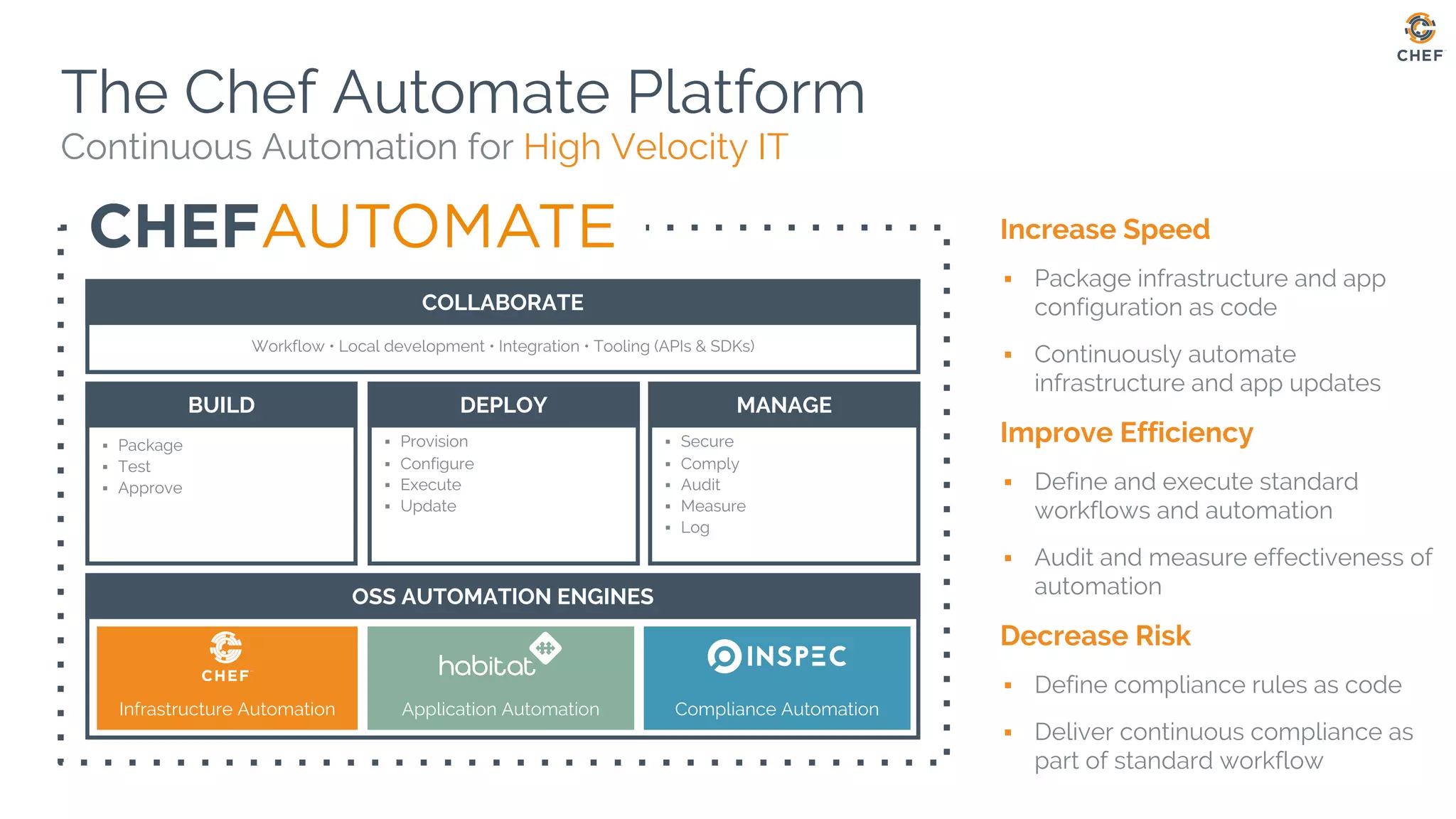
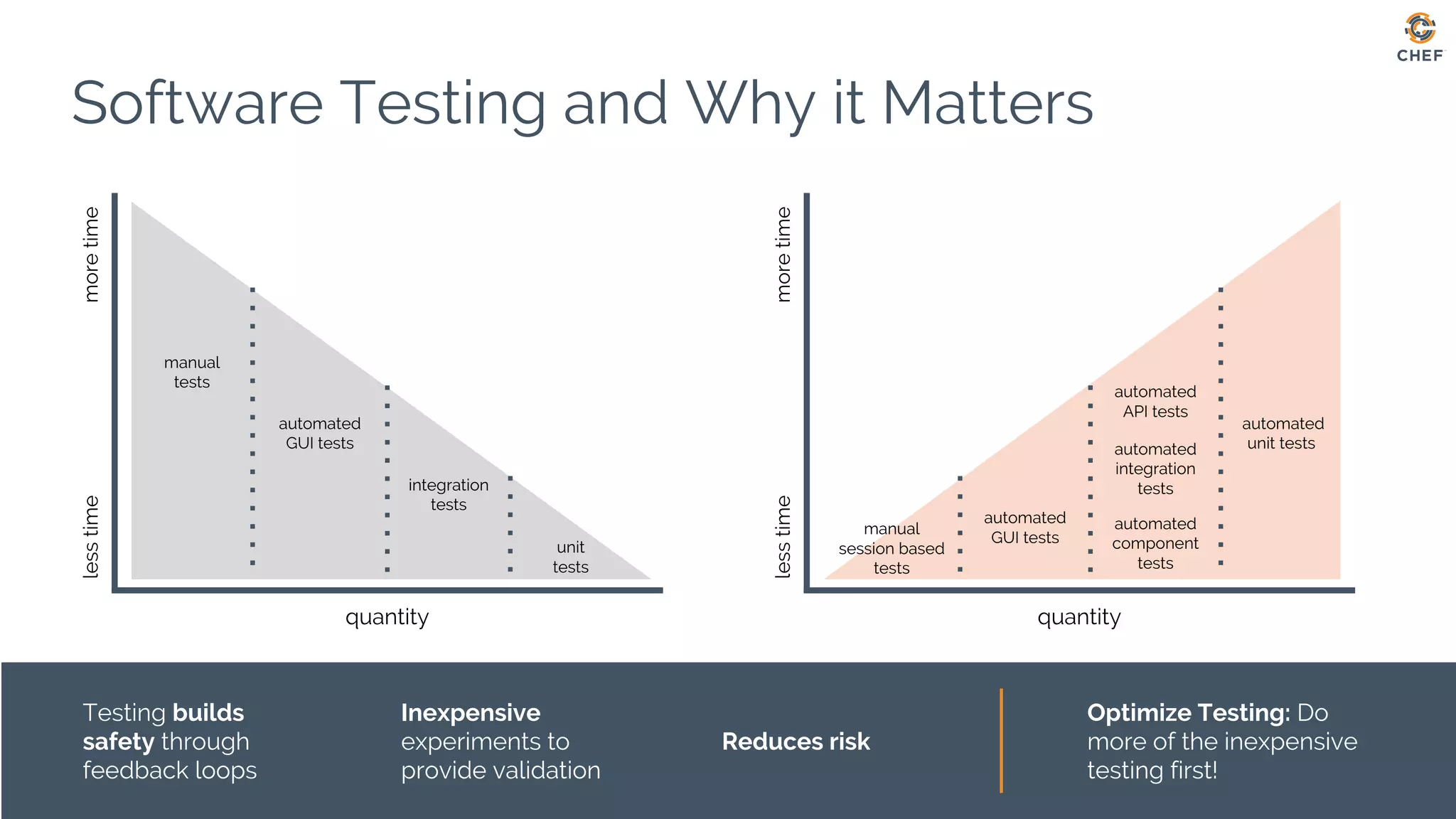
The document discusses Chef, an automation framework for infrastructure as code, emphasizing its tools for testing, managing deployment, and ongoing automation. It highlights the importance of compliance and security checks through the InSpec tool, transforming compliance into code to identify issues early in the development process. Additionally, it details the structure of Chef, including resources, recipes, and cookbooks, along with the significance of automated testing in the software development lifecycle.


![● Write some code
● Write and run some unit tests
● Go to pre-production
● Run some integration/acceptance tests
● Go to production
● Lowered chance of production failure
Test Driven Development
Add a test
Run the tests
Make a little change
Run the tests
pass
[development
continues]fail
fail
pass
pass
[development
stops]](https://image.slidesharecdn.com/phillysecurityshellmeetup-180119214133/75/Philly-security-shell-meetup-12-2048.jpg)



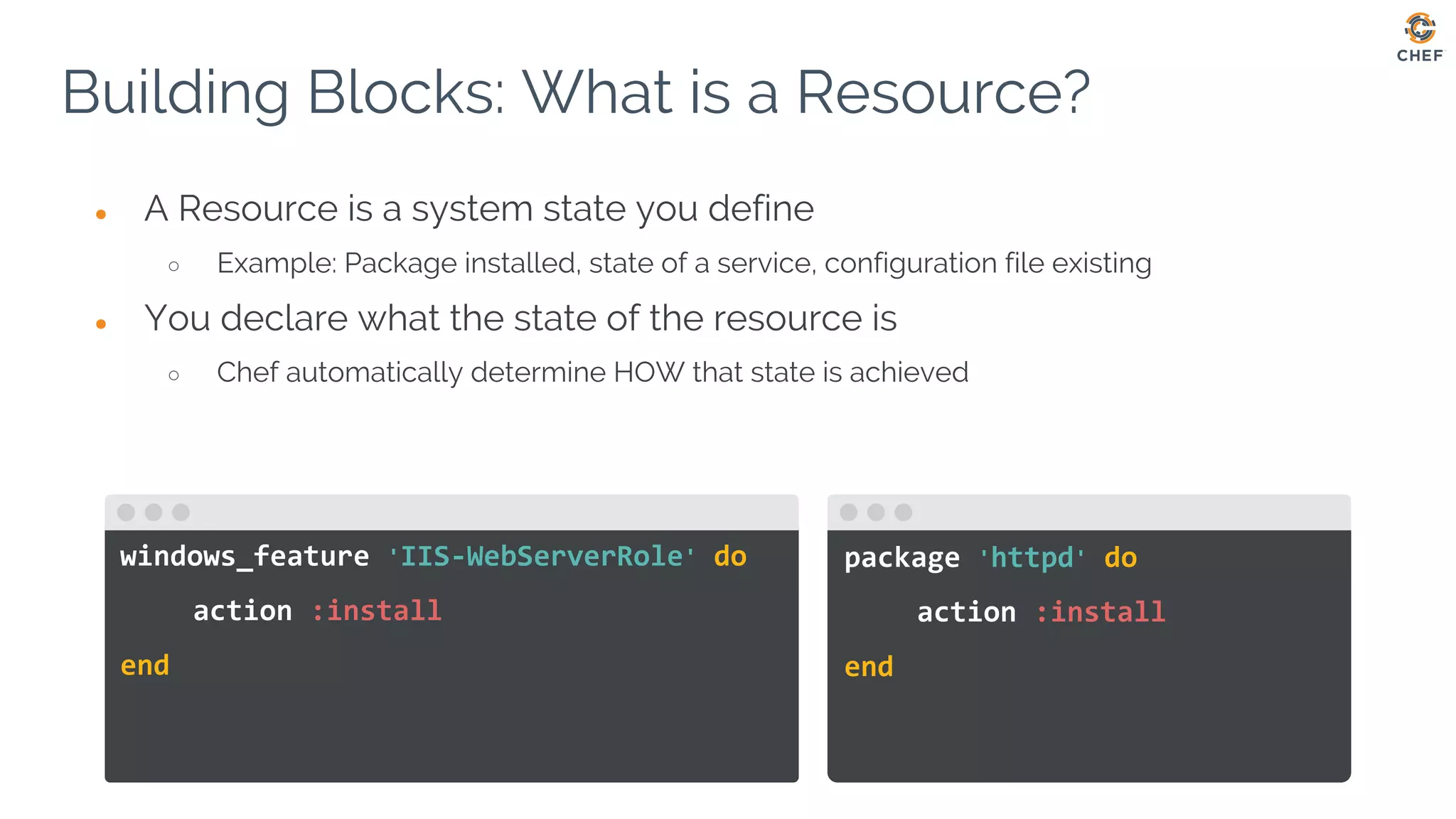
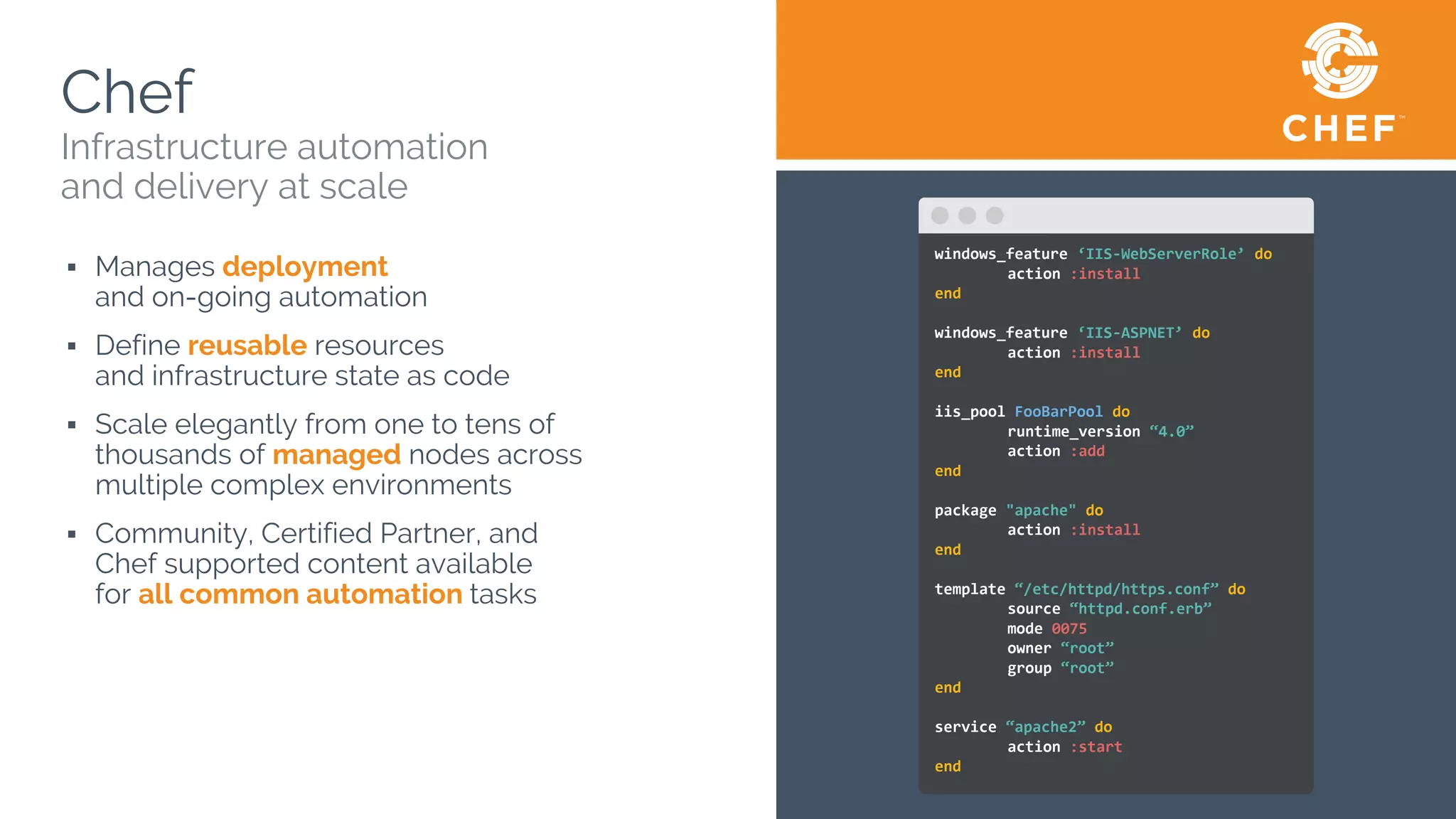
![● A recipe is a collection of Resources
● Resources are executed in the order they are listed
Building Blocks: What is a Recipe?
On Linux based OSes:
windows_feature 'IIS-WebServerRole' do
action :install
end
template 'c:inetpubwwwrootDefault.htm' do
source 'Default.htm.erb'
rights :read, 'Everyone'
end
service 'w3svc' do
action [ :enable, :start ]
end
package 'httpd' do
action :install
end
template '/var/www/index.html' do
source 'index.html.erb'
mode '0644'
end
service 'httpd' do
action [ :enable, :start ]
end](https://image.slidesharecdn.com/phillysecurityshellmeetup-180119214133/75/Philly-security-shell-meetup-24-2048.jpg)


![● Write some code
● Write and run some unit tests
● Go to pre-production
● Run some integration/acceptance tests
● Go to production
● Lowered chance of production failure
Test Driven Development
Add a test
Run the tests
Make a little change
Run the tests
pass
[development
continues]fail
fail
pass
pass
[development
stops]](https://image.slidesharecdn.com/phillysecurityshellmeetup-180119214133/75/Philly-security-shell-meetup-29-2048.jpg)