The document presents an overview of Inspec, an open-source framework for compliance and security testing, highlighting its new features in version 1.0 released on September 26, 2016. It discusses the importance of infrastructure tests as code, showcases various resource examples, and explains Inspec's execution through available commands. The document also mentions community profiles, custom resources, and installation options, emphasizing integration with Chef Automate and the use of Inspec shell for testing.



![What is InSpec and how it works
chef-client inspec
Open Source https://github.com/chef/chef https://github.com/chef/inspec
First Commit March 2008 April 2015
Language Ruby DSL Ruby DSL
Code
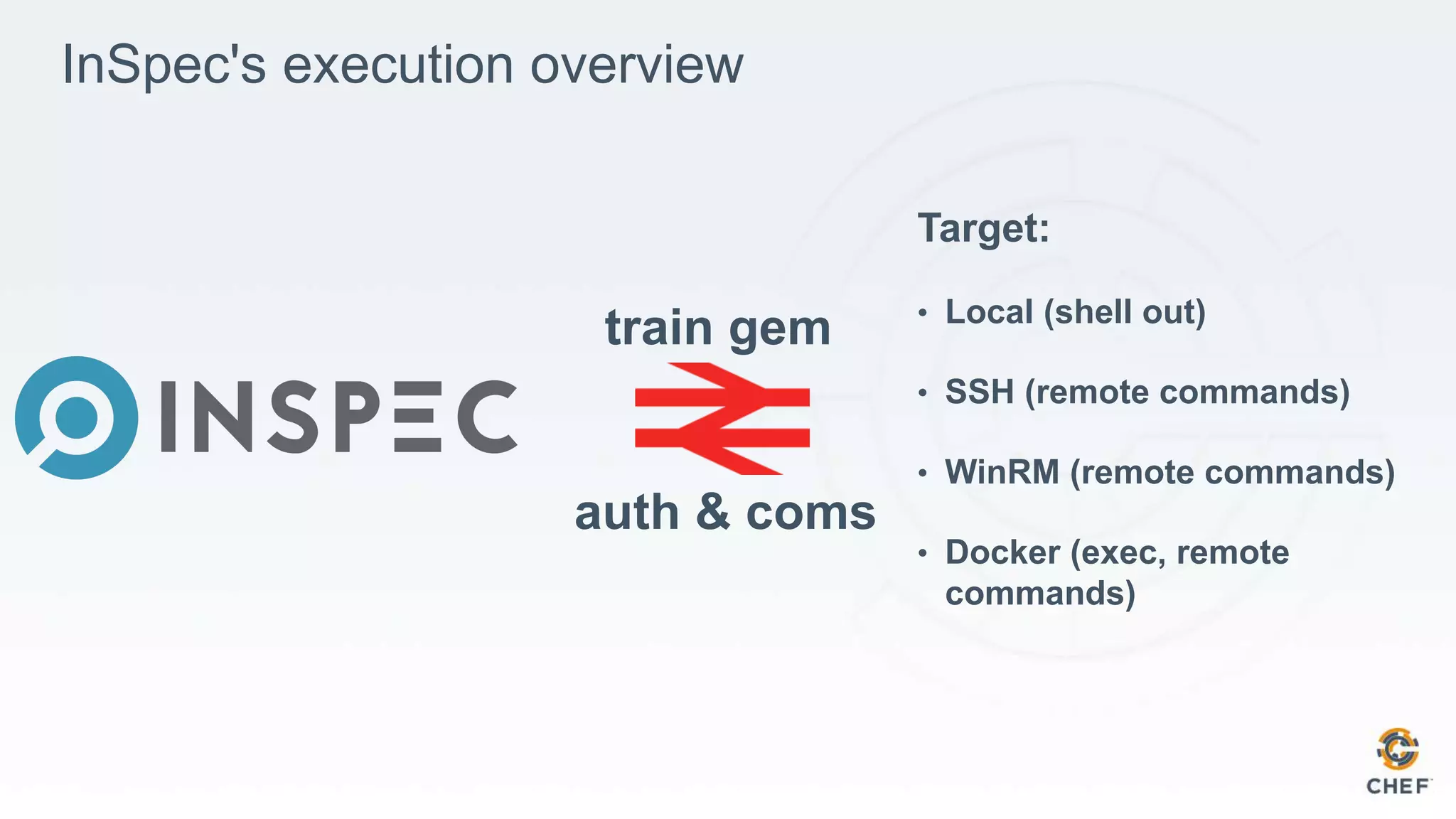
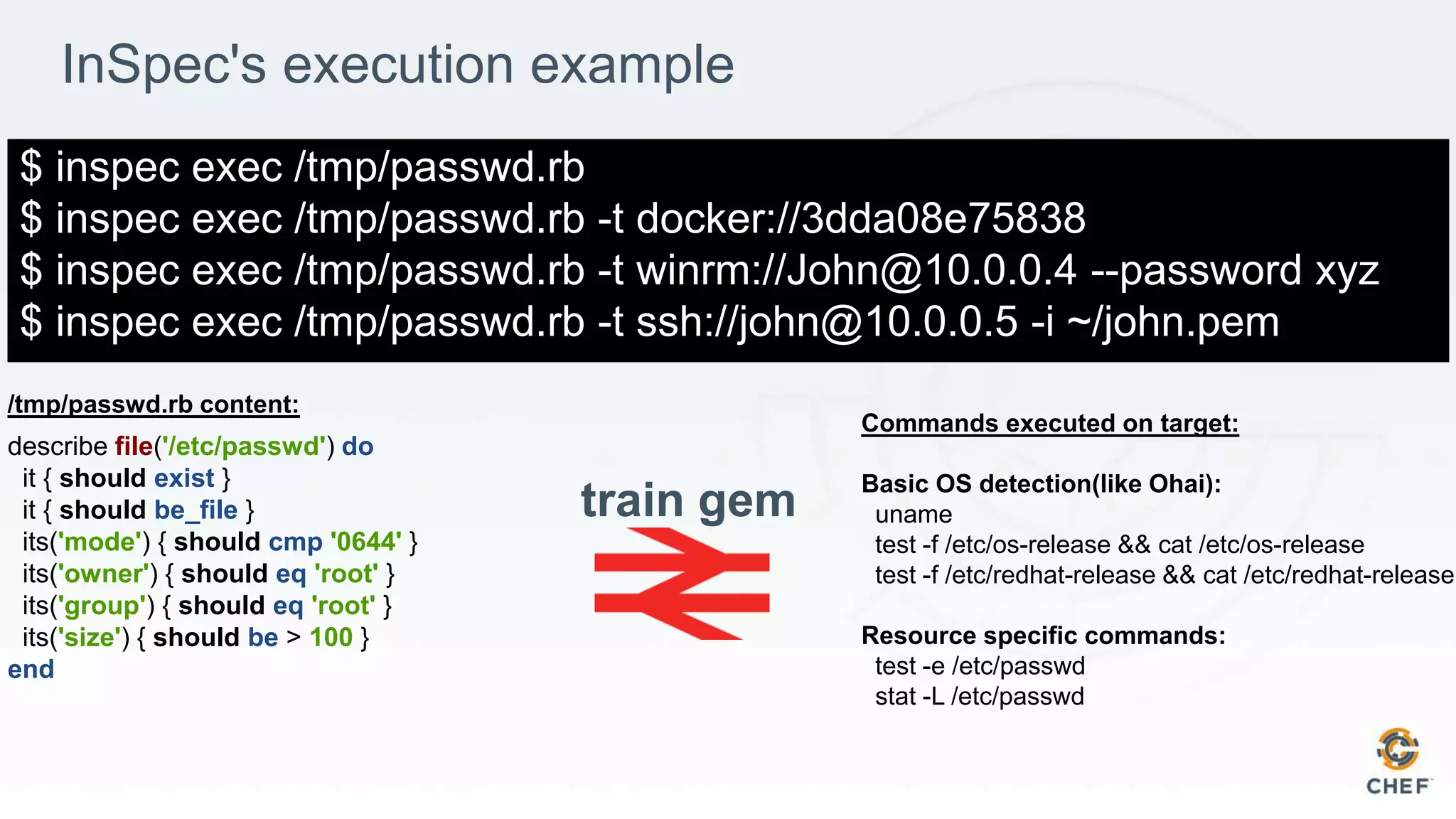
Execution Local Local & Remote (SSH, WinRM, Docker)
Artifacts Cookbooks & Recipes & Resources Profiles & Controls & Resources
Share Artifacts Chef Supermarket, Github, Bitbucket, etc Chef Supermarket, Github, Bitbucket, etc
service 'iptables' do
action [ :enable, :start ]
end
describe service('iptables') do
it { should be_enabled }
it { should be_running }
end](https://image.slidesharecdn.com/inspecintro1-160928105804/75/Introduction-to-InSpec-and-1-0-release-update-5-2048.jpg)


![2-
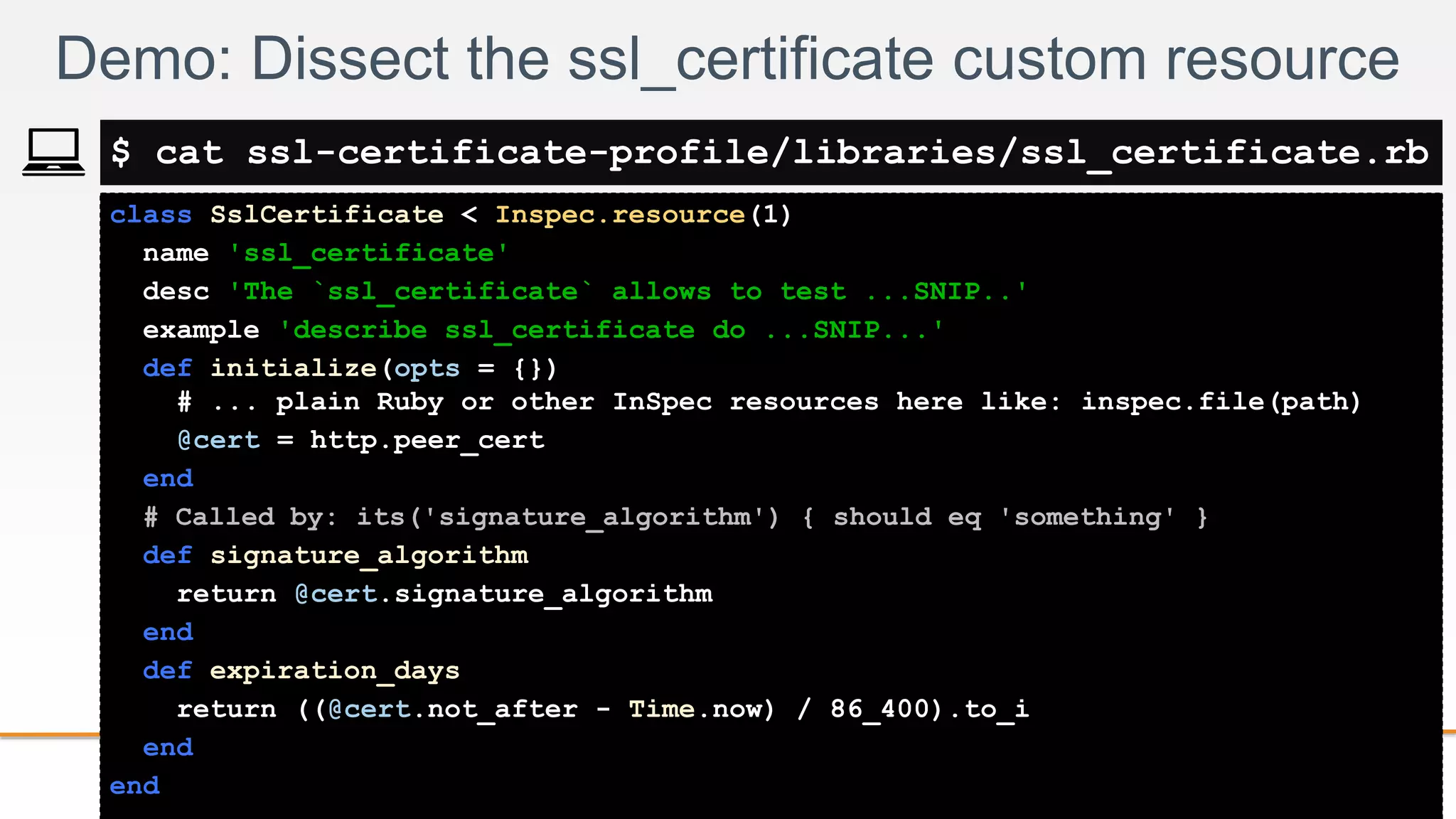
def signature_algorithm
require 'pry'
binding.pry # execution will stop here and give me a pry> shell
return @cert.signature_algorithm
end
def expiration_days
return ((@cert.not_after - Time.now) / 86_400).to_i
end
end
[1] pry> @cert.signature_algorithm
=> "sha256WithRSAEncryption"
[2] pry> ls @cert
OpenSSL::X509::Certificate#methods:
add_extension extensions= not_before public_key serial= subject
to_pem verify check_private_key inspect not_after not_before
Pry breakpoints (in profiles, resources, recipes etc)
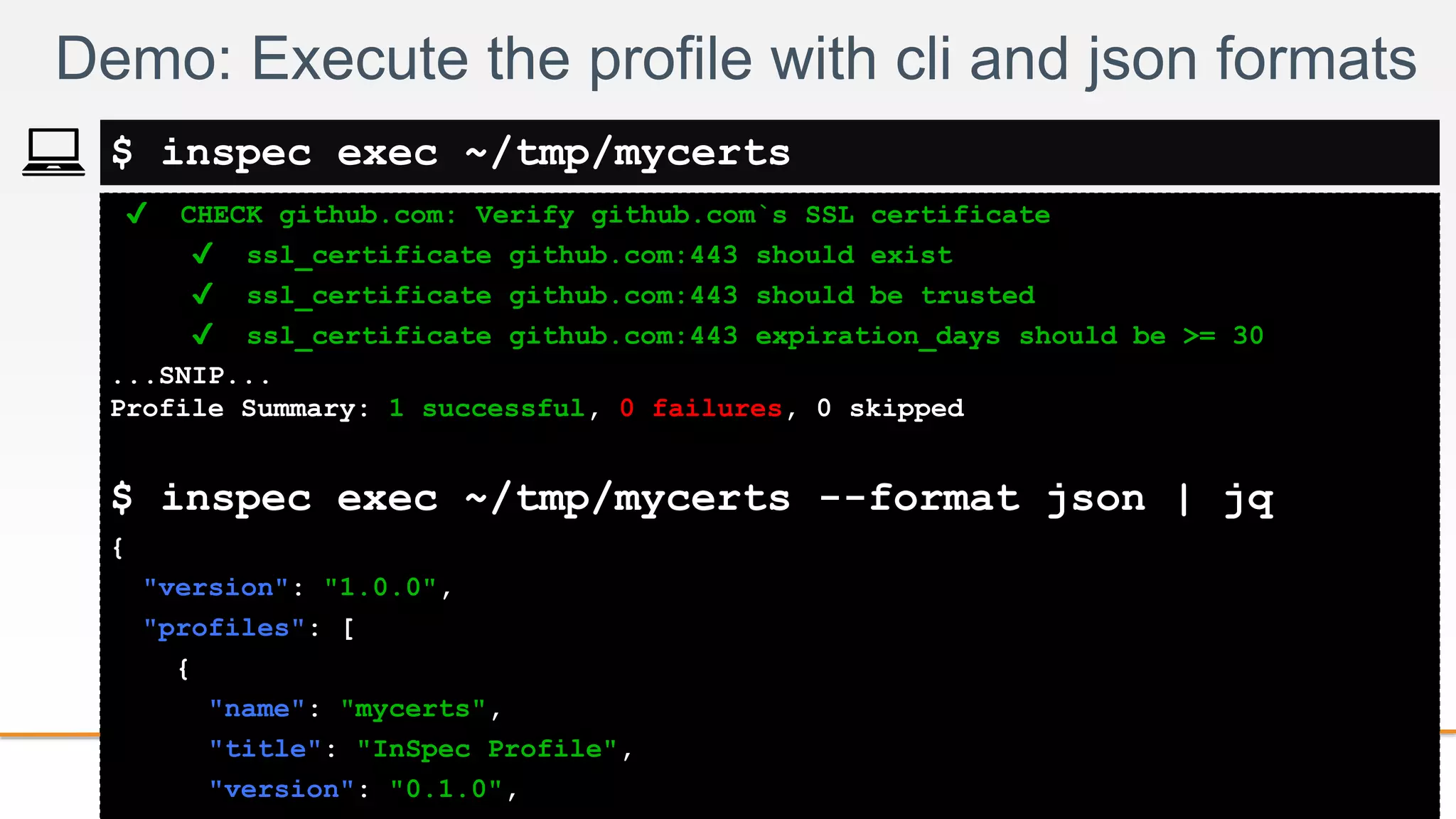
$ inspec exec ~/tmp/mycerts](https://image.slidesharecdn.com/inspecintro1-160928105804/75/Introduction-to-InSpec-and-1-0-release-update-25-2048.jpg)

